What is Azure Active Directory? (Microsoft Entra ID) – A Comprehensive Guide

Azure Active Directory (AD) is Microsoft’s cloud-based identity and access management (IAM) cloud service. Azure AD is generally seen as a move from on-premises IAM to the cloud. Learn more about Azure AD here.
What is Azure Active Directory (Microsoft Entra ID)?
Microsoft Azure Active Directory (Azure AD, AAD, Entra ID, etc.) is a cloud IAM (Identity Access Management) service that allows administrators to manage end-user accounts, identities, and devices, among other entities. Several main services make up the core service – access management, directory, and access identity protection.
Identity management in the cloud
Azure AD is generally described as ‘Active Directory in the cloud’. Each company has its own tenant to administer users and resources. Resources and employees are automatically protected from outside attacks via default security settings. If this is your focus, I plan to write another article solely based on Azure AD security. Watch for it.
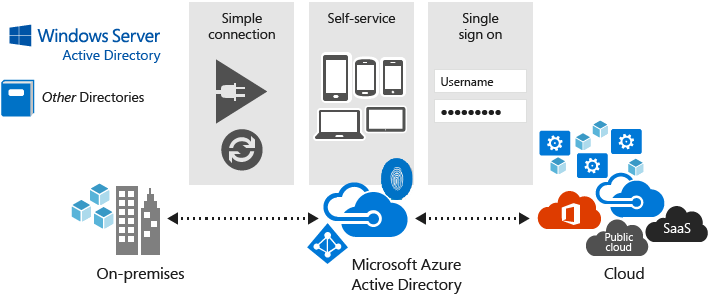
Security has been one of the main focuses of Azure AD over the past ten years or so. Microsoft announced and released several security measures including secure sign-in, and multifactor authentication (MFA) to protect your users.
Who uses Azure AD?
Every customer of Microsoft 365 uses Azure AD inherently. It is the backbone of all identity and authentication services across the M365 stack of applications and services.
One important aspect of Azure AD is its ‘Platform as a Service’ (PaaS) benefits. Microsoft handles all the infrastructure instead of that responsibility being on you as a business owner or IT Pro. I’ll cover more on this subject next.
What are the differences between Azure AD and Active Directory?
The biggest difference between the two is that Windows Server Active Directory requires you to build and support servers to host the Active Directory Domain Services (AD DS) role. IT Pros need to manage the security, patching, lifecycle of software and hardware, etc. Azure AD, being a cloud-based service, runs on its own. Microsoft takes much of the responsibility for management and security.
Although the two services handle similar functions – managing users, authentication, and application management – the underlying technologies are rather disparate. They use completely different protocols and code bases.
Here are the key differences:
- Active Directory supports NTLM and Kerberos for authentication, but Azure AD uses SAML and OAuth 2.0.
- Azure AD includes Azure Policy whereas Active Directory uses Group Policy to manage end-user devices and their environment
- Whereas Active Directory includes Organizational Units (OUs) and forests/domains, Azure AD is a flat directory structure
- Azure AD is designed for many web-based services. It supports services that use Representational State Transfer (REST) APIs for Office 365 online apps, for example
- Azure AD supports Single Sign-On (SSO) and Multifactor Authentication (MFA), whereas Active Directory does not
Does Azure AD have an equivalent to Active Directory Certificate Services (ADCS)?
If you’re interested in the possibility of ‘upgrading’ from Windows Server AD to AAD, there are many reasons this is not feasible.
The Active Directory Certificate Services (ADCS) role in Windows Server does not have a counterpart service in Azure AD. However, if your company uses client authentication certificates to access, for example, corporate WiFi, you can look into other options. For instance, if you use Cisco ISE, you can use that to directly integrate with MS Intune to handle the enrollment and compliance processes.
Always working to make transitions easier for their customers, Microsoft has recently announced a few related services in public preview. For example, certificate-based authentication (CBA) is an authentication method that allows users to log in directly with X.509 certificates against their Microsoft Entra ID (Azure AD) identities.
In addition, Microsoft Intune has certificate services in preview form. This enables users to authenticate and secure access to VPN, WiFi, or other email profiles using certificates.
Because these features are at the ‘public preview’ stage, it is a very good sign that Microsoft is trying to close the ‘feature gap’ between all things Windows Server AD and AAD.
Does Azure AD have an equivalent to Active Directory Federation Services (ADFS)?
This one is a little more nuanced. Active Directory Federation Services (ADFS) offers single sign-on services in your on-premises environment. But it solely works inside your network (LAN). Azure AD handles similar functions in the cloud.
Let me mention a few features in Azure AD that replace some functionality in ADFS:
- Azure Active Directory Connect: This tool synchronizes users and groups between your on-premises Active Directory and Azure AD, enabling federation. I’ll touch on this later.
- Azure Active Directory B2C: This service provides identity and access management for external users, such as customers or partners, who don’t have an Azure AD account. I will also delve into this feature later on.
- Azure Active Directory B2B: collaboration between your users and trusted business guests from outside organizations, while keeping control of your corporate data.
- Azure Application Proxy: This service allows you to publish on-premises applications to the cloud and enable access through Azure AD.
Does Azure AD support Kerberos authentication?
No, Azure AD doesn’t natively support Kerberos authentication. However, you do have a clear option – Azure Active Directory Domain Services (Azure AD DS).
- Azure Active Directory Domain Services (Azure AD DS)
- This is an example of a ‘Platform as a Service (PaaS)’ that provides Active Directory Domain Services in the cloud.
- When you deploy Azure AD DS, you can then join your Azure virtual machines (VMs) to it and use Kerberos authentication to access resources within your domain.
- Azure AD Kerberos for Azure Files
- This is a recent feature from Microsoft that allows Azure AD to utilize and issue Kerberos tickets for accessing Azure Files shares (from your on-premises network).
- Kerberos Constrained Delegation (KCD)
- A feature in Windows Server that can be used with single sign-on to your on-premises applications published through Application Proxy that requires Kerberos authentication.
How does Azure Active Directory Work?
So how does this web-based cloud service tick? Let’s find out. I’ll go into greater detail here on the most important features and services it offers.
Users and groups
In terms of Azure AD’s identity and access management (IAM) features, it is a secure online store for users and groups. When one of your users logs into Office 365 via office.com, Azure AD provides the authorization and authentication engineering behind that interaction.
Azure AD Groups offer similar functionality to AD Groups – security-based application access and distribution list-based email delivery.
Note – you can synchronize your users and groups from AD to Azure AD using Azure AD Connect or Azure AD Connect cloud sync. I’ll show you more details later.
Cloud authentication
As I just mentioned, Azure AD offers authentication and authorization to allow your users to access Platform as a Service (PaaS) examples like Word Online, Excel Online, Sharepoint Online, etc. Through SSO, Conditional Access Policies, and multifactor authentication, your users can securely and safely log into your tenant to avail themselves of all your tenant’s vast resources of gold and fortune.
Self-service password resets
This is a feature that allows your users to reset their Azure AD passwords themselves. Through a series of ‘checks and balances’, users verify who they are via security methods that are initially set up before the feature is enabled.
This service provides a range of benefits including a reduction of help desk calls and loss of productivity when your users are locked out.
Federated authentication
Once you taste how wonderful this is after initial testing, you’ll never go back. Your users are blessed with the ability to use a single set of credentials to log into on-premises AD and Azure AD / Office 365 apps and services. When you utilize Azure AD Connect, their AD password ‘passes through’ to their Azure AD user account, automatically. When they change their on-premises password, it is also updated (kept in sync) in Azure AD.
Hybrid Active Directory deployments
Interestingly, this article does a very good job of describing what a hybrid Active Directory deployment is. Let me offer you some bullet points that help explain the ‘hybrid’ aspect of this scenario.
- Azure AD Connect (and cloud sync)
- This software tool allows you to synchronize your on-premises AD users and groups to Azure AD. This is a classic example of a hybrid environment. You utilize on-premises and cloud-based IAM tools.
- Single Sign-On
- Users in a hybrid AD deployment can benefit from SSO. This allows them to manage one set of credentials when logging into their devices, accessing on-premises resources, and logging into Office 365 (Azure AD).
- Group Policy
- GPOs (Group Policy Objects) from on-premises AD can be synced and applied to Azure AD-joined devices, helping the migration path from GPOs to Microsoft Intune-based policies.
Multifactor authentication
This is vital. Every organization should have this enabled, including yours. This is not hyperbole. If a threat actor or hacker retains one of your user’s login credentials, they have free reign to hack into the account. Often, passwords are not created as securely as you would hope.
This is where multifactor authentication comes in. This offers a second factor users use to sign into Azure AD and Office 365 services. Users can use push notifications to the Microsoft Authenticator app on their mobile devices, and receive a phone call or text to their mobile devices, among other authentication methods. This should be one of the first things you implement when setting up a new Azure AD tenant.
Password protection
This is also at the top of my ‘you need to use this feature’ list. Instead of allowing almost any password for your users, you can use Password Protection’s feature list to secure your user’s login events.
- Password Policies
- Admins can create policies that force users to use specific criteria for their passwords – length, special characters, prevention of common dictionary words, etc.
- Banned Passwords
- When utilized, a globally managed list by Microsoft of commonly hacked passwords is automatically prevented from being used when users create or change their passwords.
- Real-Time Feedback
- Users will receive feedback when they are resetting their password to verify they are utilizing the most secure aspects of their password.
- Customization
- Detailed logging and reporting are available to offer insights into password-related events and potential security incidents in your network.
Passwordless authentication
Azure AD offers passwordless authentication, a feature that allows your users to use other forms of authentication like biometrics, security keys, or mobile devices.
You can utilize these features to achieve passwordless authentication.
- Windows Hello for Business
- Microsoft Authenticator (mobile app)
- FIDO2-compliant security keys
- Certificate-based authentication
Security and usage reporting
Azure AD offers a robust and efficient module for reporting on security and usage from your users. Activity Logs, Sign-In Logs, and Audit Logs all offer a ‘paper trail’ for all of your users’ activity online in Azure AD and Office 365.
The Usage and Insights report provides an application-centric view of your sign-in data and includes a report on authentication methods. With this data, you can find answers to questions like: What are your top applications used in your org? What users have the most failed sign-ins? What applications haven’t had a successful log-in for 30 days or more? These can all be answered quickly and securely to assist your IT Pros with managing the lifecycle of applications and onboarding/offboarding efforts.
What is Azure AD Join?
Azure AD Join is ‘essentially’ the counterpart to joining a computer to an Active Directory domain. When you join a device to Azure AD, you gain the following benefits:
- Device Registration – a record of the device is added to Azure AD. The details of the device including operating system, name, etc. are included.
- Authentication – Users sign in to their devices using their Azure AD (Office 365) credentials.
- Authorization – Azure AD determines what resources the user is authorized to access based on roles and permissions.
- Access – Cloud apps, Azure Files, and other cloud services are offered based on their access levels and permissions.
- and access to Azure AD Enterprise State Roaming.
Another similar method to ‘joining’ a device to Azure AD is what’s called ‘Azure AD Registration.’ This process registers a device in Azure AD and sets it up for ‘light management.’ Azure AD Join is typically designed for corporate-owned devices and Azure AD Register is for Bring Your Own Device (BYOD)-type device and does not offer all the management features in Azure AD/Intune.
What is Azure AD Domain Services?
I mentioned this briefly earlier. Azure AD Domain Services provides a fully managed domain built on Active Directory Domain Services (AD DS). This offers organizations the ability to use Active Directory in a trial or robust environment in the cloud.
Azure AD DS seamlessly integrates with Azure AD, allowing enterprises to leverage their existing Azure AD identities and passwords. Group Policy support is included. LDAP and Kerberos authentication are also offered.
The biggest perk is offering organizations applications or services that depend on Active Directory without needing to build and support an on-premises AD environment. You can let Microsoft manage all of your domain controllers, DNS servers, etc.
What is Azure AD B2B?
Azure AD Business to Business allows your organization to securely and efficiently communicate with external parties and guests. Applications and resources can be shared through intricate and granular controls to allow for more flexible communications between your users and guests.
One idea I want to get across here – Azure AD B2B is not a replacement or a transition from AD FS or other federation technologies from on-premises to the cloud. This is a secure method of bridging your users with approved and trusted guests, and external parties, to communicate seamlessly amongst your user groups.
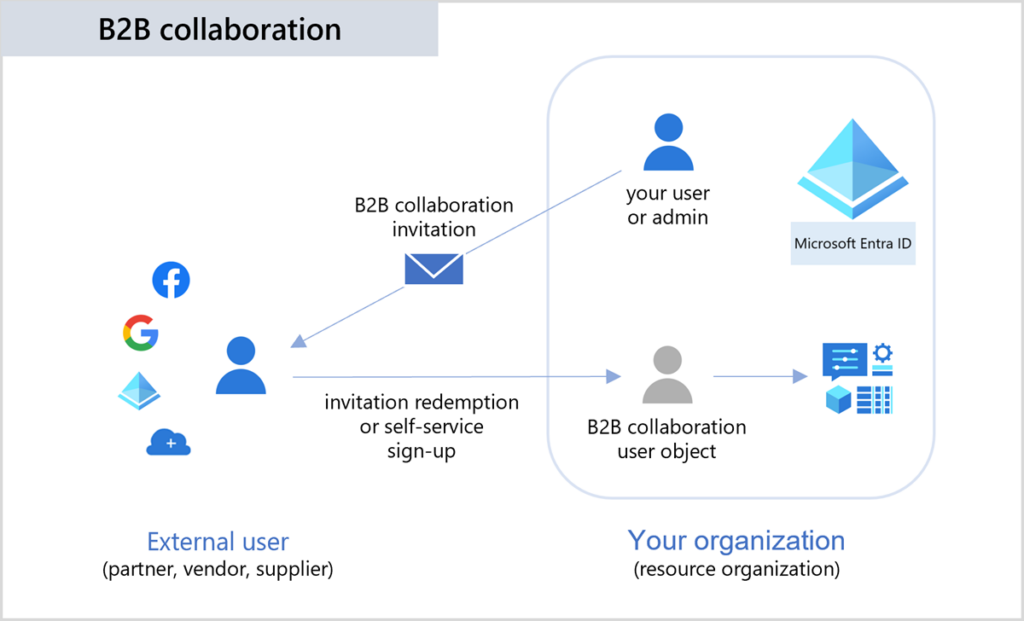
Azure AD B2B simplifies collaboration and shared resource access by allowing external users to log in with their credentials. In addition, external guests can use single sign-on to access their native resources and your organization’s shared resources.
Azure AD licensing
There are four pricing tiers related to Azure AD. Free, Basic, Premium P1, and Premium P2. Here are some high-level details of each.
| Pricing Level | Features | Pricing |
|---|---|---|
| Free | Up to 50,000 user accounts, Single sign-on (SSO) for up to 10 apps, user provisioning, and basic reports. Ideal for SMBs and very small companies. MFA and Azure AD Connect are available. | Free |
| Basic | SSO for unlimited apps, self-service password reset, and group access management. B2B collaboration. | $1 per user per month |
| Premium P1 | All Basic features, conditional access, identity protection, and advanced reports | $6 per user per month |
| Premium P2 | All Premium P1 features, Azure AD Identity Protection, and Privileged Identity Management | $9 per user per month |
Please note – this is a high-level summary and the pricing will vary due to the nature of your company’s agreement with Microsoft.
Conclusion
In conclusion, Azure AD, transitioning to Microsoft Entra ID in name only, is a comprehensive and secure cloud-based identity and access management service provided by Microsoft Azure. Azure AD facilitates secure authentication, seamless single sign-on experiences, and efficient management of user identities across a variety of applications and services.
There are many features and corresponding services that help assist you in your overall path from on-premises Active Directory to Azure AD. Azure AD Connect cloud sync is a perfect example that helps to securely provide an easier end-user experience to get their jobs done.
Please feel free to leave a comment or question below. Thank you for reading!



