What Is IAM? A Guide to Identity and Access Management

Identity and Access Management (IAM), is a crucial cybersecurity framework that governs and secures digital access to resources. It plays a pivotal role in helping organizations control and secure their digital resources such as apps, files, user identities, permissions, and all other organizational data. IAM also helps ensure the confidentiality and integrity of sensitive information.
What is IAM?
IAM, at its core, is a comprehensive framework consisting of policies and business processes paired with technology to manage and secure organizational digital identities. It involves defining the access privileges for systems and individuals in an organizational ecosystem to safeguard sensitive and critical data and resources.
IAM policies and processes are usually established and configured by organizational security administrators or professionals. Their role is to enforce necessary security policies and to help mitigate the risks associated with data breaches or unauthorized access.
IAM policies not only help enhance data and resource security but also aid in streamlining business operations and in adherence to regulatory compliances like the General Data Protection Regulation (GDPR) or HIPAA.
How does IAM work?
Identity and Access Management works by regulating and orchestrating access to digital resources and data based on the identity and access of users and systems. The core of IAM involves authentication and authorization to help secure digital resources. IAM performs user or system authentication using passwords or biometrics like fingerprints. And subsequently checks for their authorization to determine access.

What is an example of IAM?
IAM works by centralizing the management of user identities, their authentication, and access permissions. All these access criteria are defined in IAM policies. An IAM Policy is a set of rules that defines and explains the permissions and access controls for individuals, groups of individuals, or systems within an organization. These policies list what’s permissible to access and under what conditions, and when. These conditions could also be time-bound and can include temporary restrictions to ensure the safety and security of digital resources and access.
Below is a simple IAM Policy that grants a user with basic read and write access to an S3 bucket.
{
"Version": "2023-12-09",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": “arn:aws:s3:::example-S3-bucket/*"
}
]
}What are the main components of an IAM solution?
While a modern IAM solution could include multiple components, below are the 10 crucial IAM components that collectively form its foundation to use identity to secure access and safeguard digital resources.
| Component | Description |
| Users | Individuals or entities within an organization require access to digital resources. |
| Groups | Collections of users based on similar roles or responsibilities meant to simplify access management. |
| Roles | These are sets of permissions that are not tied to any specific user or group but are assumed by users or groups as needed. |
| Policies | Policies are rules that define actions (allow or deny) on specific resources, attached to users, groups, or roles. |
| Authentication | The process of verifying a user’s identity using methods like passwords, biometrics, or multifactor authentication. |
| Authorization | The process of determining access permissions based on policies and defined rules. |
| Access Control Lists (ACLs) | These are the lists defined by the organization to specify resource permissions and to control who can access the resource and what actions are allowed. |
| Single Sign-On (SSO) | An authentication mechanism enabling users to access multiple systems with a single set of login credentials. |
| Audit and Monitoring | Tools and processes for tracking and logging user activities, providing insights into resource access that can help in preventing and projecting access misuses. |
| Directory Services | Centralized systems that store and manage information about users, groups, and digital resources within an organization. |

What are the benefits of implementing an IAM solution?
Implementing Identify and Access Management (IAM) offers several benefits for organizations in terms of security, compliance, resource protection, and more. Here are some of the top benefits:
Access control
With IAM, you can build a granular access control model defining the resource access to every user and system within an organization.
Security
IAM allows you to build a robust framework to manage and control access to sensitive resources and data within your organization. It also reduces the risk of unauthorized user or system access, data breaches, or security threats.
Improved productivity
IAM greatly reduces the administrative overhead of individual access management and simplifies the user and resource onboarding/offboarding process to enhance productivity and operational excellence.
Single sign-on (SSO)
SSO capabilities of an IAM solution enable users to access multiple systems within an organization using a single username and password. This reduces the need to handle multiple credentials and the overhead of maintaining them.
Centralized user management
IAM solutions allow you to easily group users and resources based on their roles and responsibilities, access requirements, and more. This makes it extremely easy to map the current and upcoming users while ensuring safe and secure access policies.
Regulatory compliance
IAM enables companies to adhere to regulatory and compliance requirements by implementing and enforcing security policies, access management, audits and logging, and more.
Logging and monitoring
IAM solutions offer robust logging and monitoring features that enable organizations to track user access. Detailed reporting helps in securing and adhering to regulatory compliance.
Cost savings
IAM solutions reduce the likelihood of security incidents like data breaches and data leaks saving a lot of costs for organizations.
What are the risks associated with IAM?
While IAM solutions offer many benefits in fortifying digital security and access rights, they do come with a few challenges. Organizations must understand and acknowledge the potential risks associated with Identity and Access Management.
Here are the top 3 potential risks that you need to watch out for:
1. Misconfigurations
Humans are prone to making mistakes and even the slightest misconfiguration in IAM policies could result in a severe impact to organizational security. To prevent misconfigurations in IAM, you need to conduct regular audits and reviews of role access controls and permissions.
2. Insider threats
Like with any security framework or solution, malicious or inadvertent actions by malicious actors within an organization pose a serious security risk. Implementing the principle of least privilege, conducting employee training, and employee behavior analytics could be a great defensive mechanism to safeguard against insider threats.

3. Insufficient monitoring and logging
Inadequate logging and monitoring may lead to delayed or no detection of unauthorized activities within the organization, which could increase security incidents. Implementing a robust monitoring system, defining clear logging policies, and automating the alerting mechanism are crucial to deal with this issue.
What is the difference between cloud vs on-premises IAM?
While both cloud-based and on-premises IAM solutions offer robust security features, choosing the right solution for your organizational needs could be tricky. Here are the major differences between these two types of IAM solution so you can make an informed decision.
| Feature | Cloud IAM | On-Premises IAM |
| Deployment | Hosted on cloud servers. | Installed and managed within an organization’s physical infrastructure. |
| Scalability | On-demand scalability and offers flexibility | Scaling may require additional hardware and resources. |
| Accessibility | Accessible from any location with internet connectivity. | Typically limited to the organization’s internal network. |
| Cost Structure | Often operates on a subscription-based, pay-as-you-go model. | Upfront capital investment, with ongoing maintenance costs. |
| Maintenance | Managed and updated by the service provider. | Requires in-house IT staff for maintenance, updates, and security patches. |
| Integration | Could easily integrate with other cloud services and applications. | May require complex integrations with on-premise systems. |
| Security | Auto-managed security by service providers and provides regular security updates. | Direct control over security, but responsibility for implementation and updates rests on the organization. |
| Customization | Limited customization options based on the provider’s offerings. | A higher degree of customization to meet specific organizational needs. |
| Deployment Speed | Rapid deployment and quick access to new features. | Deployment timelines may be longer, especially for large-scale implementations. |
| Compliance | Service providers often adhere to industry-specific compliance standards. | Organizations have direct control over compliance measures and auditing. |
What should I include in a robust IAM implementation strategy?
To build a robust IAM policy, you should include the key components and practices mentioned below. Along with all the critical components of an IAM solution mentioned above.
User provisioning and de-provisioning
As an organization, it’s very crucial to set up and have processes in place to create and delete user accounts as employees onboard or offboard from the organization.
Robust access control policies
Having robust access policies that are based and built on the principle of least privilege are crucial for better security and control. IAM solutions allow you to implement role-based access control (RBAC), attribute-based access control, rule-based access control, or time/policy based access controls.
Secure single sign-on
Implementing SSO can not only help users in managing their credentials but can also help organizations by reducing the overhead associated with employee credential management and partially eliminates the need of credential rotations.
Data encryption
Using data encryption to protect sensitive and confident organizational data is crucial. Ensure you implement strong data encryption for data at rest as well as in transit.
Identity federation
Enabling identity federation can help establish secure communication and access controls across different systems and organizations.
Incident response plan
Having a strong incident response plan could help you efficiently address any access or security mishaps and can help you mitigate them.
What are some of the common IAM solutions available today?
Choosing the right IAM solution hinges on factors such as organizational needs, scalability, integration capabilities, and security and compliance requirements. Here are some of the top readily available IAM solutions that you can pick for your organization.
Microsoft Entra ID (formerly Azure Active Directory)
Microsoft Entra ID is the company’s leading cloud-based Identity and Access Management service that helps organizations secure their user identities and resources. Some of the top advantages of Microsoft Entra ID are its direct integration with Microsoft Azure cloud services and the Microsoft ecosystem.
Entra ID also offers robust security features including MFA, conditional access policies, identity protection, and more. However, there could be a bit of a learning curve associated with mastering the Entra ID.
Windows Server Active Directory
Windows Server AD is an on-premises Identity and Access Management service from Microsoft. It provides a centralized directory service for managing and authenticating users, computers, and other devices within a networked environment. It also plays a crucial role in controlling access to resources and enforcing security policies for organizational security.
Active Directory (AD) is a mature and established solution that offers robust security solutions and seamless integration with the Microsoft ecosystem, just like the Entra ID. However, it does come with on-premises dependency and could involve considerable up-front costs.
AWS IAM
AWS Identity and Access Management (IAM) is Amazon’s comprehensive web service that enables users to securely control access to AWS resources. AWS IAM enables organizations to be able to seamlessly manage users, groups, roles, and permissions to enhance organizational security. It provides a flexible and scalable solution for identity management within the AWS cloud and it offers granular access control but comes with complex security policy syntaxes.
OKTA
Okta IAM is a cloud-based IAM solution that provides Single Sign-On (SSO), multi-factor authentication (MFA), and other identity services. Okta’s platform is designed to securely connect and manage user identities across various applications, whether they are on-premises or in the cloud. It is a scalable solution that offers several features such as a universal directory, adaptive authentication, easy policy lifecycle management, and more.
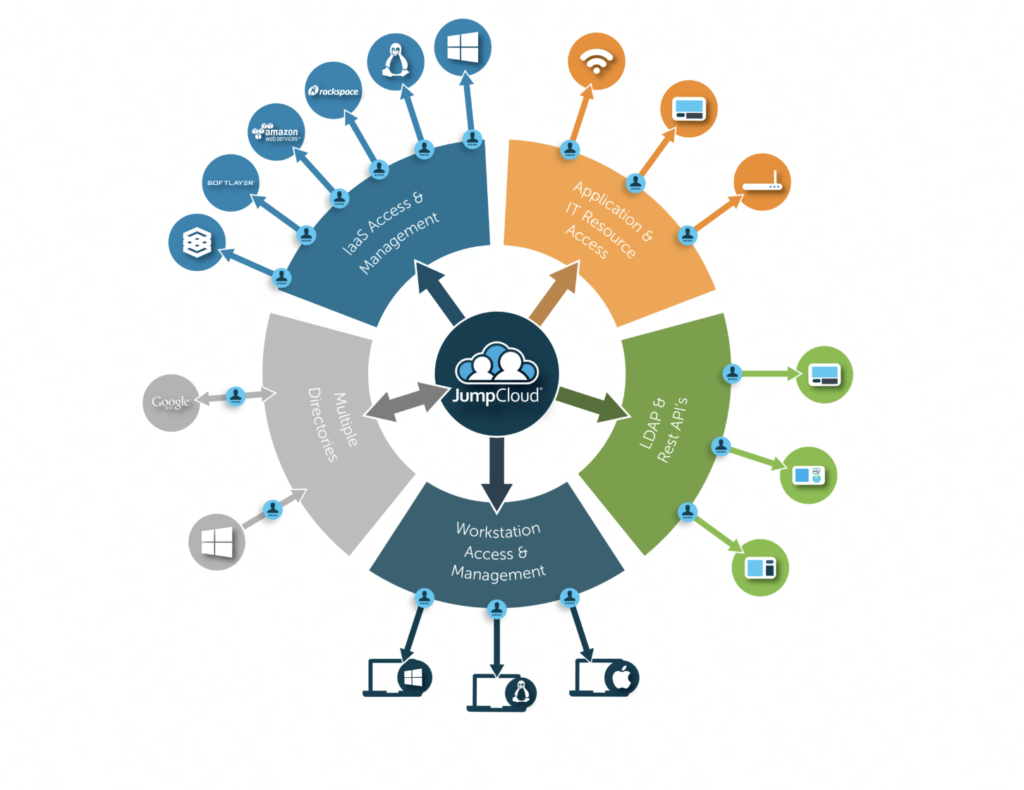
JumpCloud
JumpCloud is an IAM service provider that offers a cloud-based Directory-as-a-Service (DaaS) that serves as a central source of truth for user identities. This eliminates the need for traditional on-premises directory services making it scalable and easy to manage.
JumpCloud supports multiple authentication protocols and it is cross-platform. However, having some security features such as password manager and patch management may cost extra depending on your package.
Conclusion
Identity and Access Management (IAM) is a crucial cybersecurity framework that ensures secure access to organizational digital resources. IAM encompasses policies, processes, and technology for efficient identity management.
Organizations need to weigh the benefits against the potential risks of IAM platforms before they choose one. Choosing the right IAM solution should be factored in on deployment preferences, scalability, integration capabilities, and organizational needs.
Table of contents
- What is IAM?
- How does IAM work?
- What is an example of IAM?
- What are the main components of an IAM solution?
- What are the benefits of implementing an IAM solution?
- What are the risks associated with IAM?
- What is the difference between cloud vs on-premises IAM?
- What should I include in a robust IAM implementation strategy?
- What are some of the common IAM solutions available today?
- Conclusion



