What Is Multifactor Authentication and How Does It Work?

Multifactor authentication adds an extra layer of security, or authentication factor, to your online accounts and it should be enabled in your organization, period. This guide will walk you through all the technology behind it and give examples of how to protect your organization from phishing attacks and security breaches.
What is multifactor authentication?
Multifactor authentication (MFA) is a service that requires a user to use two or more authentication methods to authorize themselves to an application, service, online account, or virtual private network (VPN). Traditionally, users used a ‘single factor’ – a password. This was the baseline and was so for many decades of computing.
MFA, sometimes referred to as two-factor authentication, is a robust security method that enhances the protection of all of your online accounts, including Microsoft 365 and Microsoft Entra ID. Let’s move on to why it is so vital today.
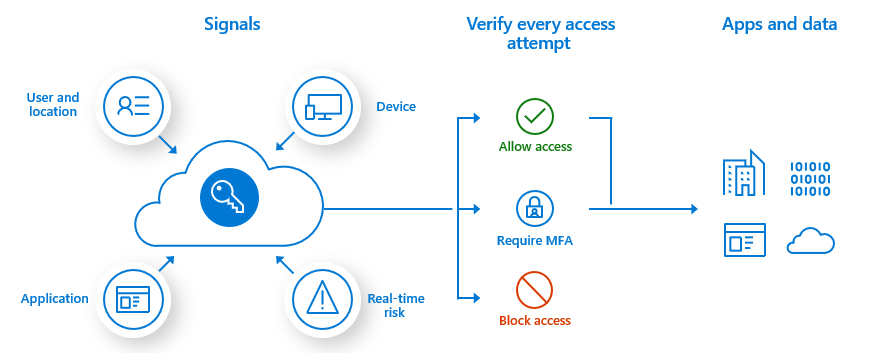
Why should I use multifactor authentication?
Over the last two decades or so, hackers and threat actors have been able to compromise users’ online identities by guessing passwords or using brute-force attacks. Cybersecurity has exploded in value. Phishing attacks have also been very prevalent. Once they have your identity, attackers have varying amounts of liberty, and time to infiltrate that user’s information, and spread it to other parts of that user’s identity or organization.
Additional verification methods and strategies needed to be created to protect users’ identities. This is why you should use MFA. Even if a hacker uses brute-force to compromise a user’s password, they would be blocked from gaining access without the user’s other authentication methods, such as a push notification to the Microsoft Authenticator app on a smartphone.
I highly recommend that organizations enable or enhance identity and access management infrastructure with MFA. This should be a requirement or standard today. The process and journey to continually keep your users and company information safe is ongoing. Already, in early 2024, additional authentication methods are gaining traction, awareness, and acceptance – including passkeys (more a bit later…).
How does multifactor authentication work?

Let me explain how multifactor authentication works in Microsoft 365 and Microsoft Entra ID.
- A user browses to https://office.com/ to log in to their Microsoft 365 work account.
- They enter their email address/login name and password.
- The website then sends an MFA request for an additional factor of authentication to their mobile device.
- This could include a push notification to their Microsoft Authenticator app or a security key on their laptop.
- The website could also send an SMS message to the user’s smartphone or a phone call.
- The user approves or denies the request through the app, enters the 6-digit code sent to them via SMS, or answers the phone call and presses a key when prompted to approve.
- The user also has potential options to respond with biometrics: fingerprint, Windows Hello face recognition, etc.
- The system then verifies and grants access appropriately.
What are one-time passwords (OTPs)?
A one-time password (OTP), or one-time PIN (personal identification numbers), is a password that is valid for only one login authentication session. Once used, it is invalid. Because it is a ‘one-off’, there is a minimal timeframe of risk to hackers or outside threats.
Here are some devices or apps that can generate OTPs:
- Mobile Apps
- The MS Authenticator app can produce OTPs for users.
- Hardware Tokens
- Hardware security tokens or fobs can generate OTPs
- Server-Side Generation
- OTPs are generated from the server and sent to a user via SMS or verified email addresses.
The main multifactor authentication methods
For completeness, let me go over each of the most popular multifactor authentication methods, and how they relate to MFA.
Password or PIN
Passwords go back many decades of course. Just think that there was a time when people logged into computers and systems with a username alone! Anyway, passwords (or credentials) are linked to a single user account. For systems that support it, you can also use a PIN. For example, you can set up Windows 11 to let you sign in to your Microsoft Account (MSA) with a PIN. This is more secure than a password because that PIN only allows access to that single device.
Device / smartphone
There are several methods of authentication you can use on an iOS or Android smartphone/tablet. You can receive a voice call or an SMS text message to reply by pressing a number after answering the call or a 4-8 digit code (SMS).
You can also install an authenticator app like Microsoft Authenticator, Google Authenticator, etc. These apps offer various ways to reply to an MFA prompt including a push notification. These apps also offer OTPS (one-time password codes). These change every 30 seconds. Instead of a push, a user can enter these 6-digit always-changing codes to verify authenticity.
Biometrics
As we progress down this list, we are increasing the inherent strength of each method. Authenticating with your fingerprint or facial recognition is multiple times more robust than a password or PIN. Windows 11 offers these surrounding Windows Hello and Windows Hello for Business. You can even configure Microsoft Edge to allow users to log in to specific web pages with their fingerprint or face.
Microsoft 365 / Microsoft Entra ID
Microsoft has been at the forefront of getting on the bandwagon of enhancing security for their customers. Multifactor authentication has slowly been rolled out and required in specific scenarios since 2019.
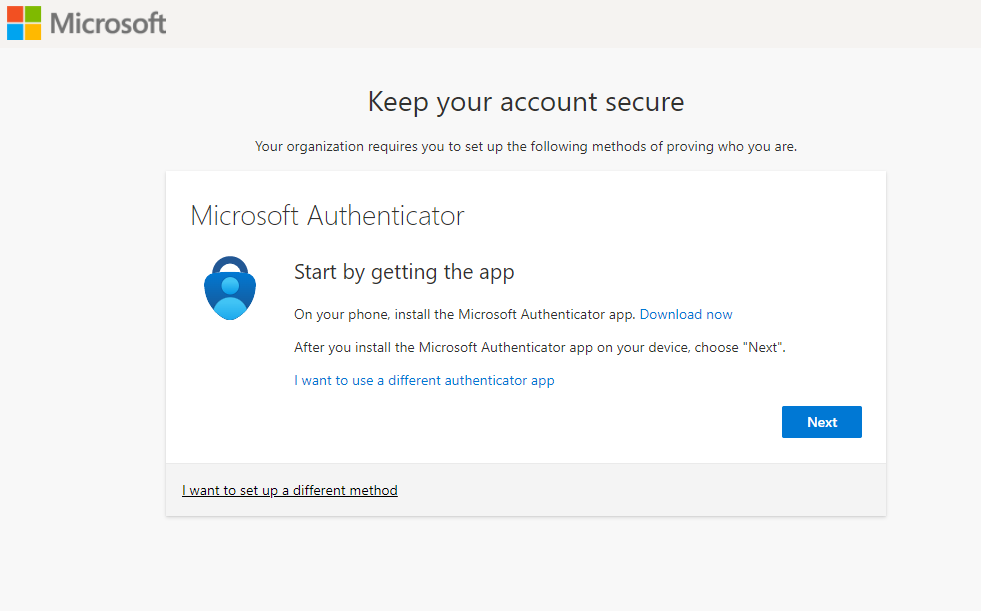
They have made continual improvements to the service over the past few years. Besides my recommendation to, at a bare minimum, enable MFA, I also highly recommend incorporating what’s called Conditional Access Policies in your tenant(s). Let me explain further.
Conditional Access Policies
In the Microsoft Entra ID portal, under Security, the first feature under the ‘Protect’ category is ‘Conditional Access.’ Conditional Access considers several configurable criteria of a user’s login attempt to ‘condition’ their attack vector. If a user is trying to log in from a geographically diverse location, Entra ID may prompt the user for additional verification. Conversely, if a group of users are connecting from a trusted location or public IP Address/range, they won’t be prompted for MFA, to ease user experience concerns.
Conditional access policies ensure the right controls are applied to a user’s login based on location, time of day, device type, risk detection, and other configurable criteria.
Multifactor authentication vs passwordless
Looking to more modern times and the future of this space, we explore what’s called passwordless authentication. This removes a password from a user account and puts in its place either unique login links sent via email, SMS, or biometrics. Passwordless logins do NOT rely on knowledge-based credentials, the single largest security risk – the human factor.
Here are the most common methods of using this technology with Microsoft Entra ID.
- Windows Hello for Business
- This marries biometric factors directly to the user’s PC.
- Supports SSO
- FIDO2 Security Fobs/Keys
- Fast Identity Online (FIDO0 standard for strong authentication.
- Microsoft Authenticator
- This enables passwordless sign-in to any Entra account.
- Users log in with a PIN or biometric method (fingerprint, face, etc.)
- Certificate-Based Authentication
- Certificates are tied to the user’s account.
- Uses digital certificates for authentication purposes.
What are passkeys?
What is the hottest example of passwordless authentication today? Passkeys. I imagine we’ll see a noticeable adoption of passkeys in 2024. A passkey is a security method that replaces passwords (passwordless authentication) with a robust foundational technology base.
Passwords are knowledge-based. Passkeys, on the other hand, combine public-key encryption with other factors. These factors can include biometrics or a PIN. When you set up a passkey, it’s tied to a specific device, such as a user’s phone. If you need to sign in on another device, you can scan a QR code from your phone to use the same security.
Passkeys are essentially phishing-resistant because they don’t involve any typing or a user needing to remember anything at all. You can’t unwillingly enter your personal information on a phishing site when using passkeys – very nice.
Conclusion
Multifactor Authentication (MFA) is a robust security method that enhances protection for your users’ logins. It requires users to provide two or more verification factors during login, such as:
- something they know (like a password)
- something they have (such as a smartphone or secure USB key)
- or something they are (like biometric data).
MFA significantly reduces the risk of unauthorized breaches into your organization or your user’s devices and data. I highly recommend you enable MFA wherever possible to safeguard your online presence.



