In this Ask the Admin, I’ll show you how to set up Windows Hello for Business using Microsoft Intune.
Previously known as Microsoft Passport for Work, Windows Hello for Business replaces passwords with two-factor authentication: one factor being a key or certificate that’s bound to the device, and the second a gesture, such as a PIN or biometric authentication stored locally on the device. For more information on Windows Hello for Business, see Introduction to Windows Hello for Business on the Petri IT Knowledgebase.
Convenience PINs vs. Windows Hello for Business
Windows Hello for Business provisions keys or certificates for users, effectively replacing their domain passwords. By default, Windows Hello credentials are based on an asymmetrical key pair that’s bound to the device and mapped to the user’s AD account during the registration process. Windows Hello for Business also supports certificate-based credentials for organizations that have a Public Key Infrastructure (PKI) in place.
But it’s possible to log in to Windows with a domain account using a convenience PIN if enabled in policy. It’s important to note that convenience PINs provide an encrypted wrapper for domain passwords that is cached on the local device when users sign in.
Configure an MDM Policy in Intune
In the following example, I have user accounts in Azure Active Directory (AD) and Microsoft Intune is used for managing devices. Before you can complete the instructions, you’ll need both an Intune account and Azure Active Directory (Premium) subscription. You’ll also need a Windows 10 device that is already enrolled with your Intune tenant.
For more information on enrolling Windows 10 with Intune, see Microsoft Intune: Windows 10 Device Enrollment on the Petri IT Knowledgebase. Windows Hello for Business policy can also be configured using Active Directory Group Policy instead of an MDM solution.
- Log in to the Intune management portal here in Internet Explorer. The portal isn’t currently compatible with Microsoft Edge.
- In the list of options on the left of the Intune portal, click ADMIN.
- Under Administration, expand Mobile Device Management > Windows and click Windows Hello for Business.
- Check Enable Windows Hello for Business on enrolled devices.
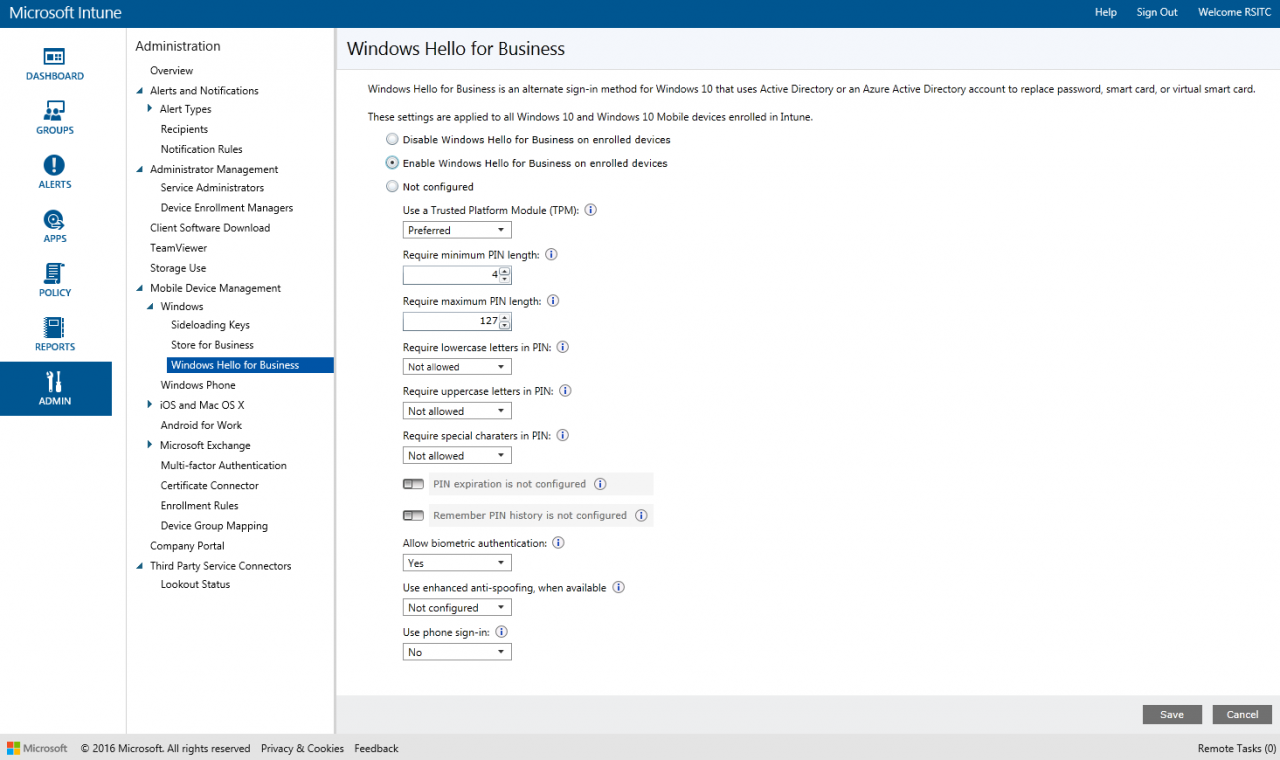
For the purposes of this lab, I’ll accept all the default settings. But as you can see, Windows Hello for Business settings can be configured. For instance, you can modify the minimum and maximum required PIN length, and enable or disable biometric authentication. Accept the default settings by clicking Save at the bottom of the portal windows.
Add a PIN
Once the Windows Hello for Business MDM policy is configured in Intune, users already working with enrolled devices will be prompted to set up a PIN via the automatic provisioning process. Users logging into VMs via Remote Desktop Services won’t be prompted automatically and need to set up a PIN manually:
- Log in to a Windows 10 device that’s already enrolled with Intune.
- Click the Settings icon on the Start menu.
- In the Settings app, click Accounts.
- Click Sign-in options on the left.
- Click Add under PIN on the right.
- Verify your password when prompted.
- Type a new pin, and once more to confirm it, then click OK.
If you haven’t already confirmed your identity on the device, you’ll be prompted to do so using one of several methods. In the instructions that follow, I’ll confirm my identity using an SMS sent to my mobile.
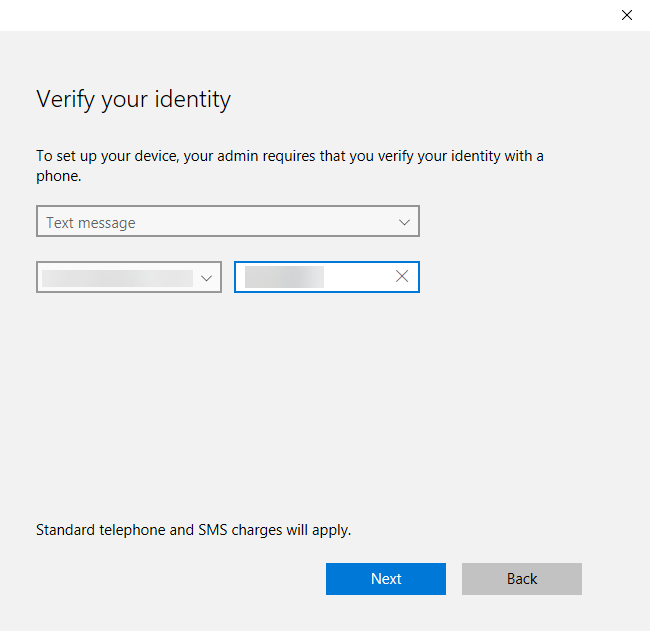
- You’ll then see the Set up a PIN dialog box stating that this device belongs to your organization. Click Set up PIN.
- On the Help us protect your account screen, you’ll be asked to set up your account for extra security. Click Set it up now.
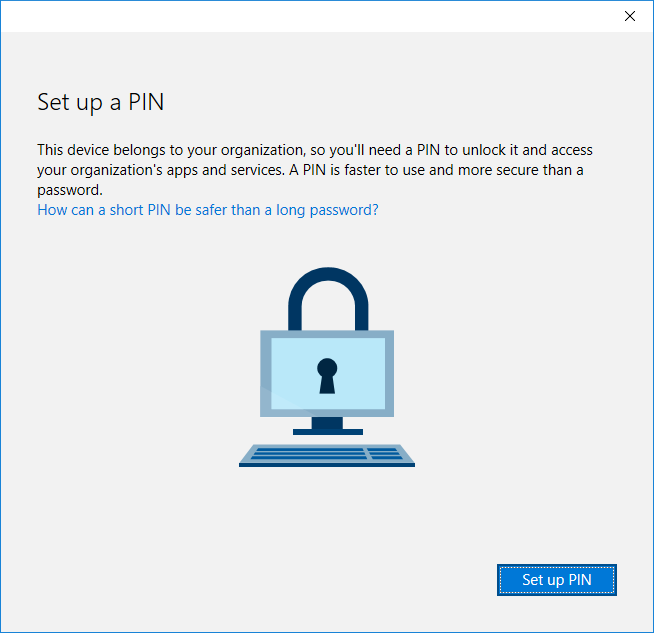
- On the Verify your identity screen, select an identification method from the drop-down menu and then enter the necessary details. I’ve chosen Text message and entered a mobile phone number. Click Next.
- Enter the code you receive and click Next.
- Click OK and wait for the PIN to be set up.
In this article, I showed you how to set up Windows Hello for Business using Microsoft Intune.
Related Article:



