Mitigating Identity-Related Risks With Windows Hello for Business and Seamless Single Sign-On (SSO)

These days, document theft and data siphoning are common for most ransomware gangs. Because digital theft is different from analog theft, digital security should be different from analog security. In this article, we’ll explore how Windows Hello for Business and seamless single sign-on (SSO) can help organizations to mitigate many identity-related risks.
We’re holding on to technology from the sixties
The world of digital business is far different than what it was a couple of decades ago. In the past, popular soda brands could protect their recipes by locking their vaults and Xerox machines.
To compartmentalize the usage of mainframes, user accounts were created. Because time on mainframes was valuable, passwords were introduced. A simple, yet effective, way for a system to compare a value stored in computer memory to a value typed on a keyboard by a person.
However, we’re still using the same method today when we sign in, mostly.
We’ve scaled it up and met our doom
What’s worse: on average we’re using 100 accounts for all sorts of different apps, services, and systems. One might think that the passwords used on Facebook, Snapchat, and PlayStation are of no concern to IT admins.
However, when these credentials leak, they may also impact organizational credentials, because the only thing that we could agree on to identify us globally and uniquely is our email addresses. As Microsoft’s recommended practice is to use the same address for email as for sign-ins, this puts organizational credentials at risk.
Combining leaked credentials with privacy regulations that allow us to download and/or remove all our data from services, provided we can prove who we are (“Hi. Here’s my password.”), makes identity theft, data theft, and other (organizational) disasters more likely than ever before. You may or may not hear of the three large ransomware incidents per day, but if that number surprises you, you may have bigger problems.
This can all be avoided
Luckily, all this doom and gloom can be avoided, at least in the digital world. It doesn’t even require bigger brains, additional software licenses, or more advanced admins. It just needs some clear thought.
When you know that 80% of all ransomware incidents can be traced back to leaked, phished, and default credentials, there’s only one conclusion you can draw: For your organizational credentials, you need an organizational system.
Luckily, that system exists, for both legacy applications, on-premises systems, and for cloud applications and services. As an industry, we’ve been building on frameworks, protocols, and entire ecosystems to allow organizations to tie all access to one set of credentials.
Organizations can make a conscious choice to stop signing in with passwords but use credentials that cannot be leaked, cannot be phished, and cannot be eavesdropped and replayed. As a Microsoft-oriented organization, you can choose to have these credentials in Active Directory (AD), in Azure AD, or in both.
Ironically, in contrast to the analog world, going passwordless in the digital world doesn’t mean gaining access becomes more difficult. It doesn’t mean you have to turn even more locks in the right direction. It doesn’t mean you can’t exit the data center because you’ve sweat too much and are triggering the weight difference alarm when you leave. Deploying the right technology in the right way makes the sign-in and sign-out experiences easier and more convenient than passwords.
Choosing a single sign-on (SSO) solution
When talking about deploying the right technology, the first one you need to deploy and embrace is a single sign-on (SSO) solution. If this sounds hard, don’t worry. You’ve probably worked with single sign-on solutions for the best part of your career.
Active Directory, and its NT-based SAM predecessors, are typically single sign-on solutions. The premise is simple: you sign in once, then you get access to all integrated applications and systems without having to sign in over and over again. It’s seamless. And it works wonders if the landscape consists of applications, systems, and services that understand open authentication protocols such as Kerberos, NTLM, and LDAP.
These three protocols outdate the Internet. Therefore, they are not particularly suitable as authentication protocols on inherently insecure, public networks. For this purpose, open protocols like WS-FED, SAML, and OpenID Connect exist. They were born in the cloud. So, while they are not native to Active Directory, they can be augmented by adding a federation solution such as Active Directory Federation Services (AD FS).
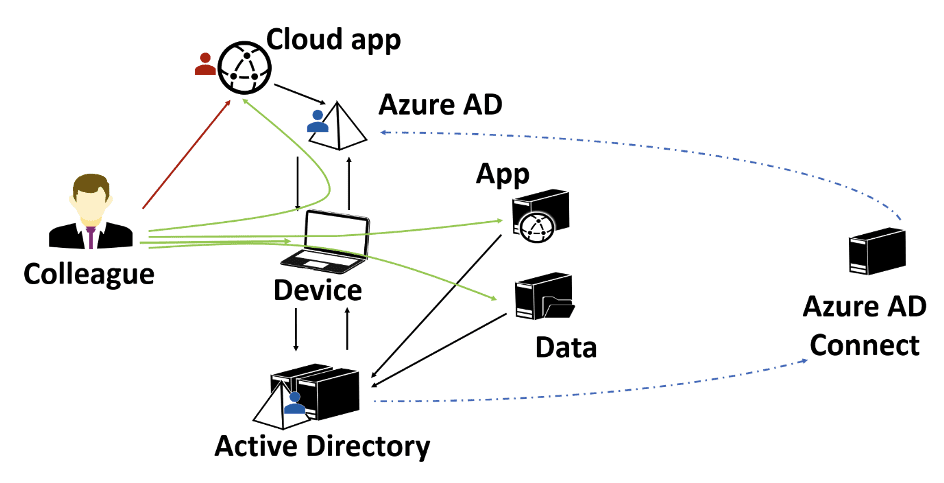
Better yet, use Azure AD instead of Windows Server Active Directory. Azure AD can be seen as the cloud-based nephew of Active Directory. Besides sharing a cloud platform with millions of other organizations, Azure AD only works with open protocols, unlike Windows Server Active Directory,
Choosing a passwordless sign-in method to use with Windows Hello for Business
The second technology to add to the mix is at least one passwordless sign-in method. There are many passwordless sign-in methods available:
- A personal identification number (PIN)
- Face recognition
- Fingerprint recognition
- A FIDO2-capable physical security key
- The Microsoft Authenticator app on your phone.
All of these methods can be used to sign in to applications, services, and systems when configured correctly to integrate with the aforementioned single sign-on solution.
To sign in to Windows-based devices, Windows Hello for Business can be used. Based on a one-time registration of the device, your favorite passwordless sign-in method can be used. If the device supports it, you can use biometrics. If nothing else works, you’ll sign in with an easy-to-remember PIN.
A PIN doesn’t really sound like an improvement on passwords, but with Windows Hello for Business, it is. That’s because, under the hood, Windows Hello for Business doesn’t use the PIN to authenticate to the identity platform. The PIN does not leave the device.
The device compares the value of the PIN to a value that is stored in memory, but the device memory is encrypted. When the device features a Trusted Platform Module (TPM), the encryption keys are stored safely in its context. This makes Windows Hello for Business authentications phishing-proof. Also, the PIN is only valid for the device it was registered on. Different PINs can be used on different devices.
What do you get with Windows Hello for Business and SSO?
Bringing these two technologies together offers organizations the ability to store and update credentials in one centralized location and a straightforward management solution. Passwordless sign-in methods can be managed centrally too.
When adding Azure AD to the mix, self-service password reset, self-service access management, privileged identity management, and identity protection are also available. With the right licenses, leaked credentials that are detected by Microsoft automatically require a real person in your organization to reset the password. And the user must sign in again to all connected systems before being granted access.
On-premises, cloud, and hybrid possibilities
Single sign-on and passwordless can be achieved in purely on-premises implementations featuring Active Directory, Active Directory Certificate Services, Active Directory Federation Services, and a third-party multi-factor authentication solution. However, it is easier to implement and manage when Azure AD is used, either as the only identity and access management (IAM) platform within the organization or as a hybrid identity implementation in conjunction with Active Directory.
To ‘Azure AD Join’ or ‘Hybrid Azure AD Join’?
The easiest way to implement both single sign-on and passwordless is by ‘hybrid Azure AD-joining‘ devices (adding an Azure AD relationship to domain-joined devices) or by ‘Azure AD-joining’ devices.
A hybrid Azure AD-joined device has a relationship with the Active Directory domain, and thus the Kerberos realm, by default. An Azure AD-joined device does not have this relationship, but it can be taught to interact with Active Directory when in a hybrid identity implementation.
For hybrid access, three trust models exist:
- Key trust model
- Certificate trust model
- Cloud trust model
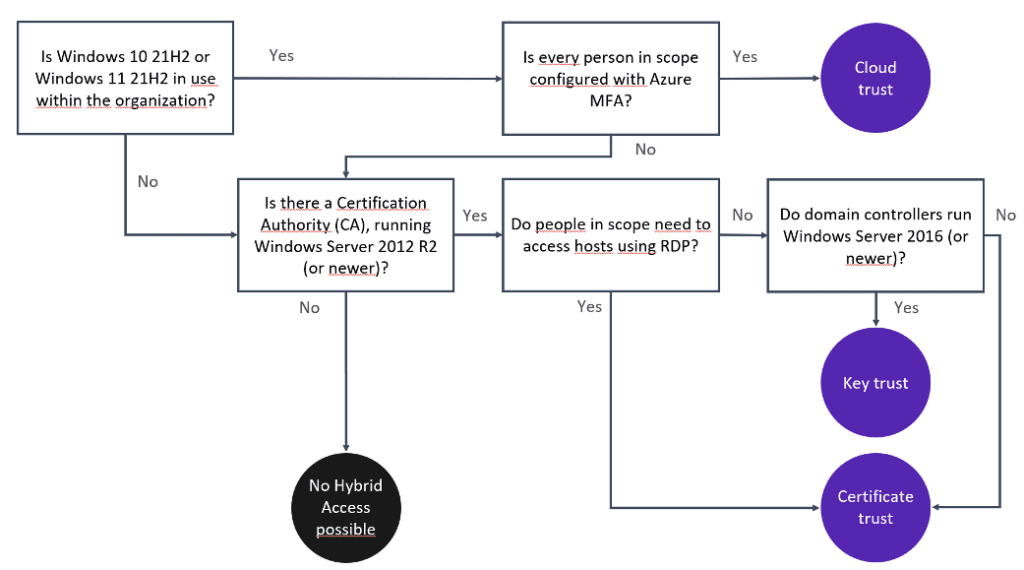
Each of the three models comes with its own strengths and weaknesses but the cloud trust model is the easiest to deploy, the easiest to maintain, and the most user-friendly. The key trust and certificate trust models require a Public Key Infrastructure (PKI), whereas the cloud trust model does not.
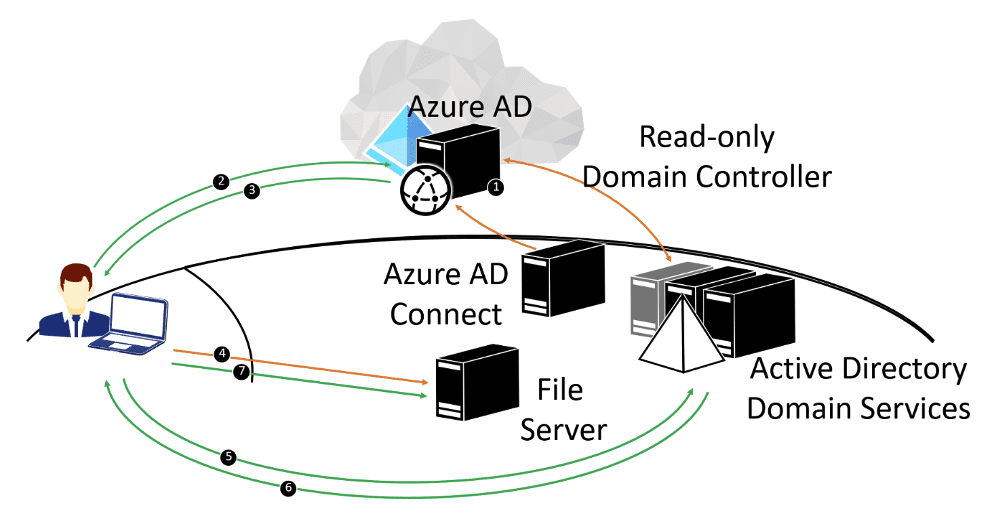
Windows Hello for Business and seamless single sign-on (SSO) offer a tremendous opportunity to mitigate many identity-related risks that organizations face today. In contrast to securing analog organizational resources, there are no additional barriers. Combining single sign-on and passwordless authentication makes accessing organizational resources easier.
As a bonus, Windows-based devices need no longer be domain-joined to make organizational resources available. For Azure AD-joined devices, accessing resources works just as well, and organizations mitigate the risk of lateral movement attacks.


