LDAP, OpenLDAP, and Active Directory: What’s the Difference?

LDAP, OpenLDAP, and Active Directory are the most used identity and access management solutions today. In this article, we’ll explain how they work and help you determine which one is the right choice for your network.
LDAP vs. Active Directory: What’s the difference?
In general, there’s a pretty good chance that you’re more familiar with ‘Active Directory‘ vs. ‘LDAP.’ Active Directory is a database set of services Microsoft introduced with Windows 2000 to manage users and computers in a domain/network environment.
LDAP, however, is a software protocol that lets users locate an organization’s data and resources. Whereas LDAP is the protocol that services authentication between a client and a server, Active Directory is a software implementation built on top of it.
Let me dive deeper to explain the main differences between LDAP and Active Directory.
What is LDAP?
Again, LDAP (Lightweight Directory Access Protocol) is an underlying protocol that allows the transfer of domain information between a database and users’ access. It is used to manage and access directory services. Over the past few decades, LDAP has been enhanced to meet the current requirements of IT pros and what security dictates.
The LDAP protocol facilitates authorization and user authentication of your network resources including servers, applications, networks, file servers, printers, and more. Vendors have created software utilizing LDAP that includes interfaces, tooling, and other functions.
Back in the nineties, Tim Howes, a software engineer developed LDAP along with some colleagues, to create a low-overhead version of the X.500 directory access protocol or DAP. Back then, X.500 saw limited usage because it was bandwidth-intensive and required large-footprint systems.
LDAP was created to reduce demand on the overall network infrastructure and to offer user management and authentication to files, applications, servers, and other network resources – all while maintaining an as-secure-as-possible environment.
What is LDAP Authentication?
How does LDAP authenticate? Well, there are two core types of authentication: Simple Authentication and SASL.
Simple Authentication is definitely on the simple side so it is more widely used. The only requirements are a unique username and password. It does require the information to be sent in clear text from the client to the server.
Yes, that’s not very secure: This open traffic on your LAN puts your users and resources at risk. A straightforward resolution to this risk is to use an encrypted channel that your LDAP server supports.
SASL (Simple Authentication and Security Layer) enhances security by binding an LDAP server to another authentication mechanism, like Kerberos. The LDAP server sends clear text to the other authorization service. This considerably reduces the vulnerability of your network to hackers and malicious attacks.
What is an LDAP query?
LDAP queries are used to obtain information from a directory service. They consist of commands based on the ‘C’ language. Here are some examples.
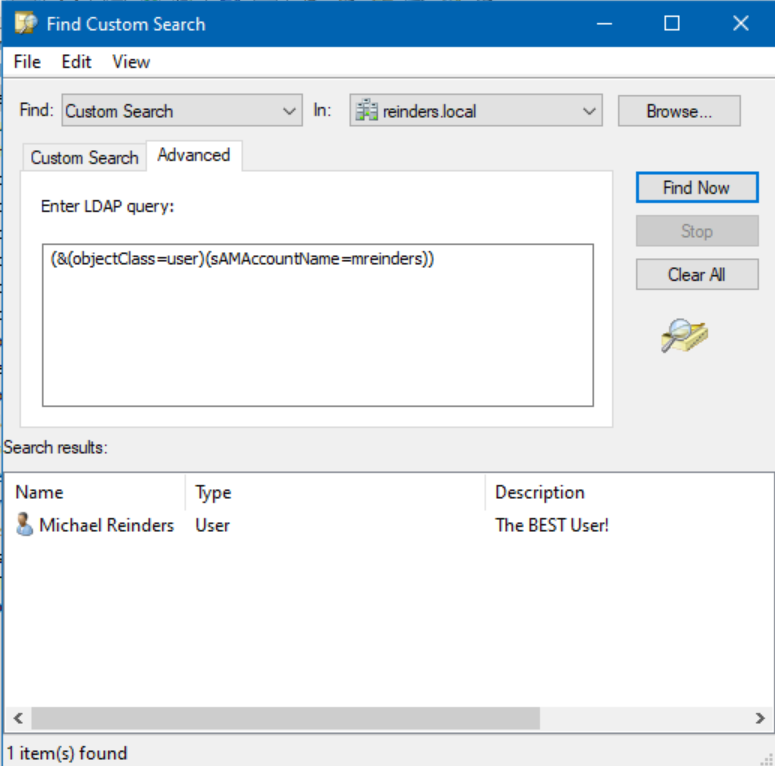
In Active Directory Users and Computers, right-click on the root of your domain, and click “Find…”
In the ‘Find:’ dropdown, choose Custom Search. Now, click the Advanced tab.
Here, you can enter the following query: (&(objectClass=user)(sAMAccountName=mreinders))
What is Active Directory?
This is a very big and important question. As I explained earlier, Active Directory is Microsoft’s directory service for Windows-based domain networks. In my humble opinion, the most efficient way for you to become refreshed on what exactly is Active Directory is to read my ultimate guide on what is Active Directory.
How does Active Directory integrate with LDAP?
LDAP is the underlying protocol at work within Active Directory. To help you understand, I’ll give an example with Exchange Server.
When you make a change within the GUI of the Exchange Admin Center, there’s actually a PowerShell command running behind the scenes making the actual changes. Similarly, when you add a user in Active Directory Users and Computers, LDAP queries are executed against the AD database on your connected domain controller (DC). How do they integrate exactly?
- LDAP orchestrates searching in Active Directory. When a user searches for a user, computer, or printer, LDAP runs a search and finds the results.
- Based on multiple levels of permissions on Active Directory, users get access to information and resources through LDAP authentication. LDAP administrators require elevated permissions to add or manipulate information in your AD repository database.
OpenLDAP vs. Active Directory: Which one is better?
Alright, let’s engage the other entity this post is about. That would be OpenLDAP. And, as you can probably deduce, it is an open-sourced implementation of the LDAP (Lightweight Directory Access Protocol) protocol. It is also free.
So, does that mean you should migrate from AD to OpenLDAP? Well, not necessarily. This is tricky. Let me explain what I mean.
Is OpenLDAP the same as LDAP?
Well, there are several ways to answer this question. The complete answer is ‘no.’ “Well, of course, you used quotes…that’s not an answer…” Yes, yes, I know.
The surprising fact, at least to me, is that OpenLDAP is actually a directory software solution for your enterprise, albeit a smaller enterprise (most likely). Active Directory of course comes with the latest versions of Windows Server and provides a tried and true robust platform for managing identity and access management.
How does OpenLDAP work?
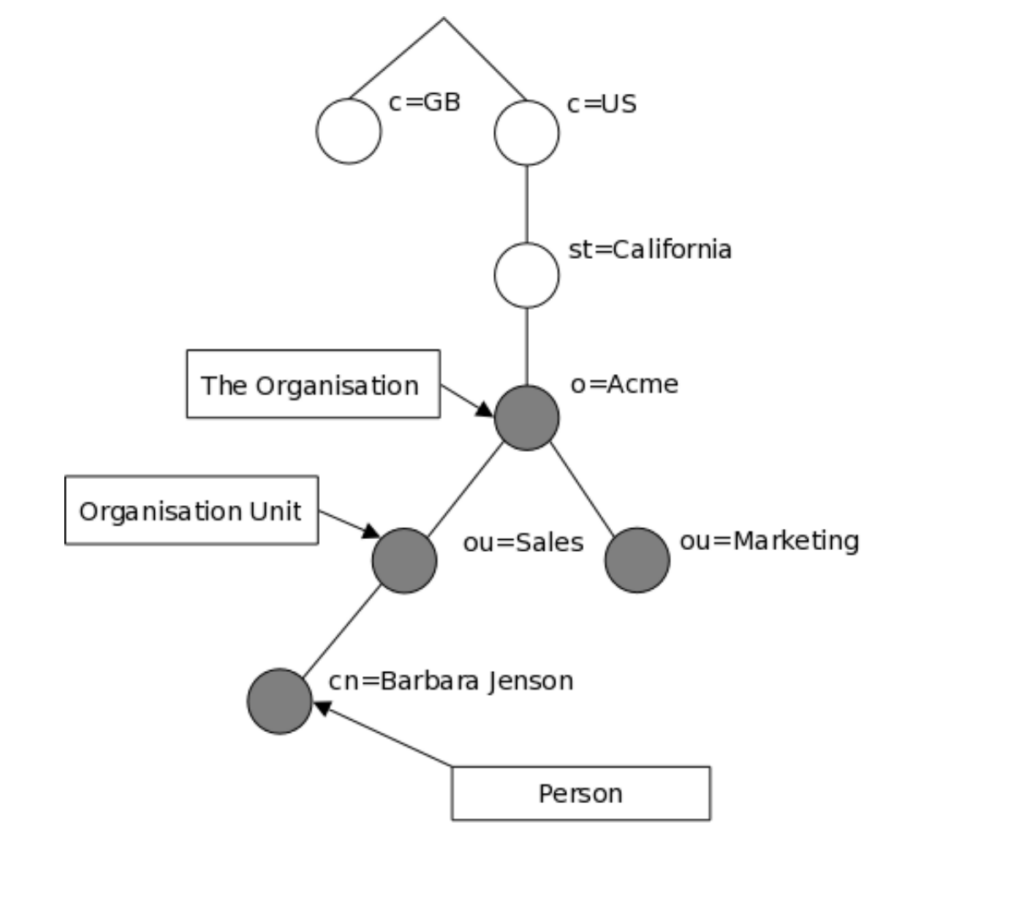
OpenLDAP used the LDAP protocol and provides a free and standard iteration that anyone can access. It does offer a robust set of utilities and tools and other functionalities that can be used on any platform, however, OpenLDAP does not offer a GUI of any kind.
Being platform agnostic is definitely a perk whereas Active Directory of course requires Microsoft Windows. OpenLDAP is highly customizable, cross-platform, and offers excellent flexibility. However, there can be a strong learning curve for new IT pros, especially potential converts from Active Directory. Your IT pros will require a decent amount of training and expertise to manage and install OpenLDAP in your enterprise.
OpenLDAP offers better support for Linux-based applications and systems, networking equipment, NAS, SAN, and other systems. Plus, enterprises that use data centers or cloud infrastructure can leverage OpenLDAP servers, a far more effective solution than Active Directory.
What are the main differences between OpenLDAP and Active Directory?
Let’s go through the core differences between OpenLDAP and Active Directory. The latter certainly has more features than OpenLDAP and offers a more scalable approach to Identity Access Management (IAM). However, while Active Directory may seem more robust feature-wise overall, OpenLDAP’s exclusive focus on the LDAP protocol gives it much more depth when it comes to the implementation of LDAP.
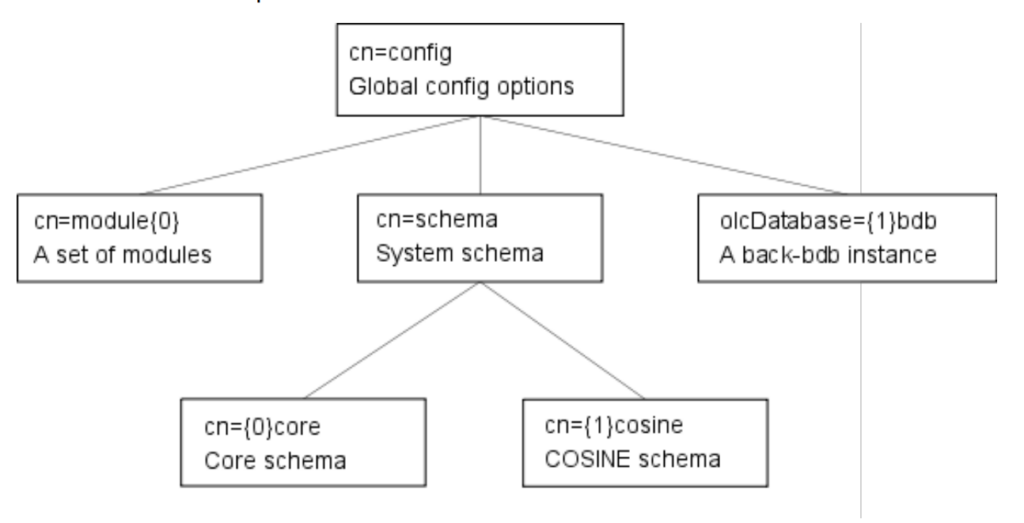
What are OpenLDAP’s advantages and disadvantages?
The main advantages of OpenLDAP are its cost (zero) and flexibility. It is far easier to manage OpenLDAP on-premises and in the cloud than Active Directory. As long as you have a solid team of engineers, they can configure OpenLDAP based on your corporate policies and security requirements. It is also platform agnostic, a big plus in this day and age.
There are of course disadvantages. OpenLDAP is a bit outdated. The learning curve and required engineering effort in implementing OpenLDAP can be a deterrent.
More, server configuration with OpenLDAP can be rather complex. It can become challenging to maintain the integrity of the directory, match application dependencies and modify the directory schema without significant effort and potential for regression of the directory service and its reliability.
What are Active Directory’s advantages and disadvantages?
Let’s go through the major advantages of using Active Directory. First, it has been around for over twenty years and really hasn’t changed much under the hood. In fact, the domain and forest functional levels haven’t technically changed since Windows Server 2016. This tells you it is a solid and robust platform.
Familiarity is also a perk: Active Directory is a very well-known name in this space. There are reams and reams of documentation on Microsoft’s Learn website to assist IT pros with implementation, management, and troubleshooting efforts.
Let’s process a few disadvantages of Active Directory – the first one is cost. There are license costs associated with Windows Server.
Second, Active Directory is solely designed for your on-premise environment. If you want to utilize this in the cloud, you will need to use Azure Active Directory and use a form of integration between the two. This can get complicated and requires full-time engineers to maintain and diagnose/troubleshoot.
The third disadvantage is the requirement to use Windows. There are workarounds for Mac and Linux devices, but they are not built-in and are not necessarily supported by Microsoft Support.
Conclusion
Well, there certainly is a lot here. At a minimum, you should have an understanding of what LDAP, OpenLDAP, and Active Directory are. You should also have knowledge of what they are and what their respective purposes are.
There are many advantages and disadvantages to implementing OpenLDAP and Active Directory. Weighing the costs, engineering requirements, where your enterprise is, and where it wants/needs to go (the cloud), is paramount in your decision-making process.
If you have any questions or comments, please leave them below in the Comment section – I would love to hear from you. Thank you for reading!



