The Dirty Truth About IT Offboarding Automation
Every system administrator dreams of building the perfect Rube Goldberg machine of IT automation to manage the employee IT lifecycle, end to end, including IT offboarding. A new hire joins the company, HR files a ticket, and BAM! In an instant, all of the birthright accounts, access, and permissions are granted in a glorious cascade of provisioning magic. Then, when an employee exits the organization, another beautifully orchestrated IT workflow instantly revokes all access and protects corporate data from waltzing out the door.
This is the promised land of IT automation, and yet, to date, it hasn’t been delivered. In a recent survey of 375 IT professionals by Nudge Security, one-third of respondents said they have automated 75% or more of their IT offboarding process. However, respondents’ IT automation investments didn’t directly translate to significant time savings or higher levels of confidence in the efficacy of their IT offboarding process.
The reality is that IT organizations are still spending about five hours per employee to identify and offboard a departing employee’s cloud and SaaS access. Despite that effort, 70% of the respondents in our survey have experienced the consequences of incomplete offboarding: security incidents, business disruption, and wasted SaaS spending, to name a few.
This post is sponsored by Nudge Security
Here’s where conventional IT automation has fallen short when it comes to offboarding employees’ cloud and SaaS access, and how IT organizations can address these failures:
Discovering SaaS assets—managed and unmanaged
Thanks to the ease with which cloud and SaaS tools can be adopted, traditional top-down IT procurement processes have been superseded by business-led and employee-led IT. This new reality disrupts conventional IT automation processes that rely on lists of sanctioned enterprise applications and services.
Without complete visibility of IT assets, offboarding often begins with the world’s worst scavenger hunt: tracking down unsanctioned cloud and SaaS accounts, identities, and resources. The only alternative is to limit the scope of offboarding to IT-sanctioned applications only, which would expose the security risks of data loss and unauthorized access.
To address this issue, IT organizations may need to implement more advanced tools that can automatically discover and manage these unsanctioned accounts, such as SaaS security and governance platforms with SaaS discovery capabilities that look beyond already known, sanctioned, and IT-managed SaaS assets.
Deprovisioning SaaS access and identities
In a perfect world, every SaaS identity would be managed by an enterprise sign-on (SSO) system, allowing for a single kill switch when employees exit the organization. But that’s far from reality. Not every cloud or SaaS application can be onboarded to SSO due to a multitude of reasons, including the exorbitant price some SaaS providers charge for a product tier that includes SSO (i.e., the SSO tax).
While SSO, password managers, and identity federation can help to automate deprovisioning for a large portion of managed SaaS identities, IT organizations still need to exert manual effort to ensure proper deprovisioning of SaaS accounts accessed by username and password. Otherwise, they risk those credentials leaving along with the employee on a Post-It note or otherwise being compromised by a threat actor. Fortunately, some innovative SaaS security solutions provide capabilities to help automate password resets for unmanaged SaaS accounts.
Managing SaaS-to-SaaS integrations
Another area where IT offboarding automation has fallen short is in revoking OAuth grants given between SaaS applications. Because these grants are often given by employees and managed by third-party providers, it can be difficult for IT organizations to ensure that access is properly revoked when an employee leaves. This can leave sensitive data and systems vulnerable to unauthorized access.
To address this issue, organizations may need to implement stricter controls on OAuth grants, such as requiring reauthorization after a certain period of time, or automatically revoking access when an employee is offboarded. Some SaaS security platforms also offer tools to help manage OAuth grants and ensure that access is properly revoked when necessary.
Coordinating with SaaS business owners
Unlike legacy IT administration, SaaS administration is highly decentralized and is often owned by individual business line managers, technologists, or simply whoever signed up first for the SaaS application. As such, IT offboarding truly takes a village. Unfortunately, it’s the IT administrator who is responsible for figuring out who in the village is the right point of contact for each SaaS application and then chasing them down to complete offboarding tasks like transferring or deleting data, deleting accounts, and reclaiming and renegotiating SaaS licenses.
Conventional IT automation tools offer some alerting capabilities, but they haven’t kept up with the pace at which SaaS applications are adopted and SaaS administration changes hands. IT administrators need a way to not only identify all SaaS application owners to engage during IT offboarding, but also to orchestrate and automate engagement with SaaS application business owners. Additionally, they need to be able to ensure that offboarding tasks are done quickly and correctly.
While IT automation has made significant strides in supporting the employee IT lifecycle, it has yet to fully deliver on the promise of effortless offboarding—especially as employees introduce more cloud and SaaS applications outside the purview of centralized IT and procurement. The challenges of discovering and deprovisioning unsanctioned SaaS accounts, as well as managing app-to-app integrations, have proven to be obstacles for conventional IT automation, and still require hours of manual IT effort.
However, with the help of more advanced SaaS security and governance solutions like Nudge Security, IT organizations can effectively address these issues and reduce manual offboarding effort by up to 90%. By doing so, they can not only save time and resources but also mitigate the risks of security incidents, business disruption, and wasted SaaS spending.
How Nudge Security can help with IT offboarding
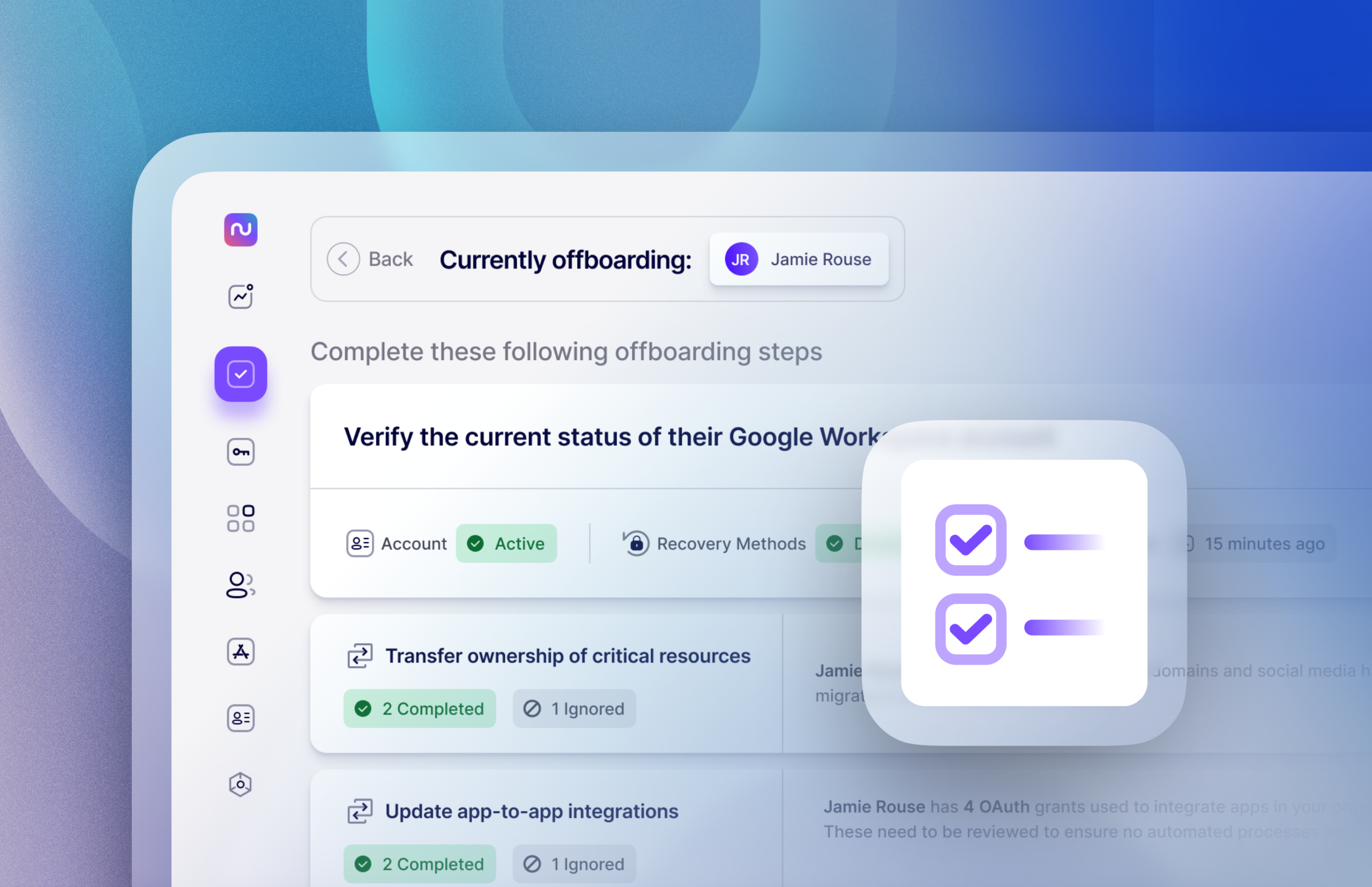
Nudge Security’s purpose-built IT offboarding playbook can help organizations save up to 90 percent of the time and effort involved in SaaS offboarding by streamlining the time-consuming, easy-to-miss tasks like revoking OAuth grants and resetting passwords for accounts outside of single sign-on (SSO).
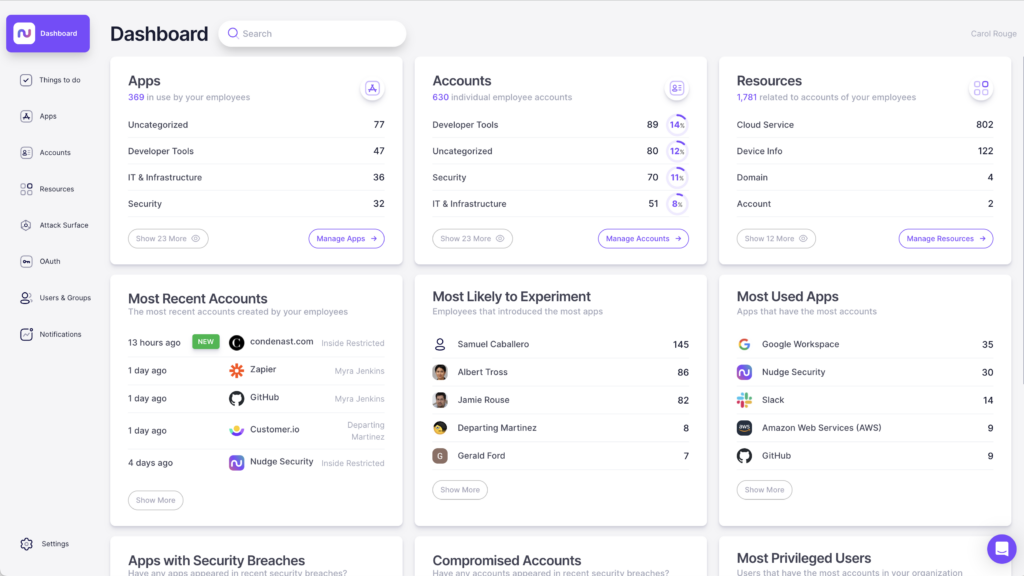
Nudge Security continuously discovers and inventories all the SaaS and cloud applications your employees are using, including shadow IT, giving you a single system of record for departing users’ accounts and OAuth grants that need to be deprovisioned, revoked, or transferred. The product’s employee offboarding playbook walks users through a comprehensive checklist for IT offboarding in alignment with Google and Microsoft best practices, enabling your team to transition employees securely and completely every time.



