Remove Stale Computer Accounts from Active Directory Using PowerShell
Keeping Active Directory (AD) tidy can help reduce replication bandwidth if you have domain controllers in different sites, and make troubleshooting and management easier. In this Ask the Admin, I’ll show you how to easily remove a computer account from AD, and how to query the directory for accounts that haven’t been used in a long time.
Remove Computer Accounts Using PowerShell
To remove one or more computer accounts using PowerShell, log on to Windows Server 2012 R2, or a Windows 8 management workstation that’s a member of your Active Directory domain, using an account that has permission to delete AD objects. If you decide to run the commands on a machine that isn’t a domain controller, the AD module for PowerShell must be installed.
- Open a PowerShell prompt, using either the icon on the desktop taskbar (Windows Server), or by switching to the Start screen, typing powershell and selecting Windows PowerShell from the search results (Windows 8).
- In the PowerShell prompt, type remove-adcomputer -identity workstation01 and press ENTER, replacing workstation01 with the name of the computer account you want to remove.
Search AD for Inactive Computer Accounts
Now that we know how to remove computer accounts using the command line, let’s query AD for computer accounts that haven’t been used for a long time. Computer account passwords are automatically reset by AD every 30 days, so you can determine yourself what length of time you should let pass before deleting the accounts from AD. A year or more would likely be a safe option.
In this example, I’m going to use the get-adcomputer cmdlet, and the select and sort object cmdlets to format the results:
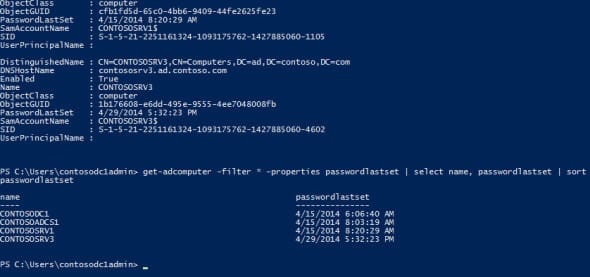
get-adcomputer -filter * -properties passwordlastset | select name, passwordlastset | sort passwordlastset
We need to add in the –properties parameter because the passwordlastset attribute is not displayed in the results by default. Select name and sort are then used to ‘pull out’ and order only the required information.
Now let’s add a more complex filter. We can use the get-date cmdlet to create a variable that sets the filter to show accounts that have had their accounts reset more than one year ago. To create the variable, type $date = (get-date).addyears(-1) and press Enter.
Now we can modify the command to include a less than (-lt) argument in the filter:
get-adcomputer -filter {passwordlastset -lt $date} -properties passwordlastset | select name, passwordlastset | sort passwordlastset
In my test environment, I don’t have any computer accounts more than a month old, so to prove the filter works, I can change the date variable to $date = (get-date).adddays(-16).
Finally, once we are sure the filter is right, we need to add the remove-adobject cmdlet as follows, without the select and sort cmdlets. Notice that I’m using the remove-adobject cmdlet and not remove-adcomputer, because remove-adcomputer is not able to delete accounts that have embedded ‘leaf’ objects, such as computer accounts for virtual machines.
Related articles:
get-adcomputer -filter {passwordlastset -lt $date} -properties passwordlastset | remove-adobject -recursive -verbose -confirm:$false



