The Ultimate Guide to Web Application Firewalls (WAF)

An often-overlooked element of security is the Web Application Firewall (WAF), especially in cloud computing. In this article, I explain what a WAF does, the different kinds of WAF, and I discuss why you should deploy one or more WAFs in your architecture.
What is a Web Application Firewall (WAF)?
A Web Application Firewall, often referred to as a WAF, is a special kind of firewall that inspects and filters network traffic to web applications. A web application can come in many forms, but it typically is something that presents itself as an HTTP or HTTPS service that is accessed, either on private networks or the Internet, by remote clients. Some examples might include:
- A static website.
- A web application with dynamic content.
- An application host that shares a client application, such as a React-based client.
- An API server
There are many ways that malicious actors start attacks on organizations, like:
- Physical attacks start on the physical premises of the intended victim. This might include placing a listener appliance or simply looking for Post-its with passwords.
- Social engineering is where the attacker impersonates someone of importance to try to gain something like a password reset.
- Identity theft to get credentials on a network, maybe through the use of phishing.
- Obtaining network entry through the use of malware.
- Attacking a web application to damage an organization.
The job of a WAF is to deal with that last attack vector, which is the one we often think of when we consider IT security. But it’s the vector that many organizations might not protect appropriately.
How does a WAF work?
A Web Application Firewall sits between client devices, like an end user’s PC, and the web application that they want to use (or attack). The WAF is presented to clients in a way that is either transparent or appears to be the actual web server. When a request is made by the client, or the client sends data to the web application, the WAF will be one of the first appliances to see the packets as they enter the network.
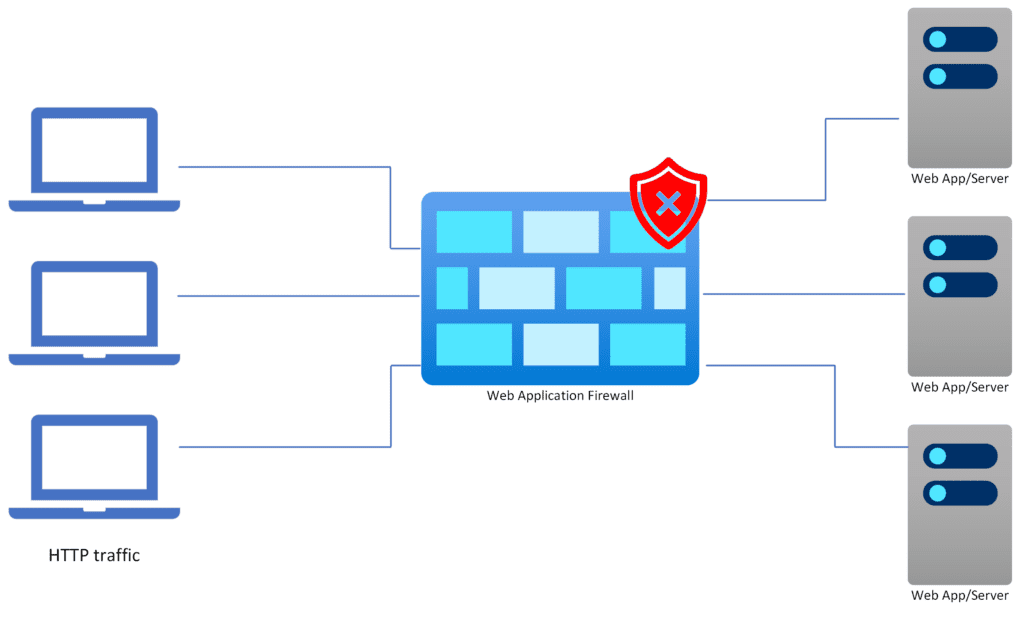
The WAF will inspect the traffic. If the request is rated as OK, then it is relayed to the backend web servers. If the request is rated as an attack, then it is acted on in some way, depending on the type of WAF and the options provided by the manufacturer. Typically:
- Logging is enabled for all requests to enable troubleshooting
- Alerts can be raised
- Threats are blocked
Why is a WAF important?
Online services aren’t limited just to e-commerce. E-commerce is bigger than ever and is a juicy target for bad actors. Cloud Computing has become the new norm for many organizations, opening up new opportunities.
Organizations can integrate through the use of cloud-native applications that offer APIs that are presented on the Internet. An event in one organization can be relayed to others through webhooks sent to an HTTPS listener that is shared on the Internet by another organization.
TLS-encrypted (what is often called “SSL”) access to the APIs of cloud-native applications is more agile than sending messages across the VPNs or leased lines of 20 years ago – developers in different organizations can react to the needs of their respective employers and create mutually profitable partnerships without waiting months for a private network connection to be created.
Cloud migration is opening up new ways to share internal services with employees too. Once upon a time, all services needed to be accessed from an office with a wired connection or via a VPN client. Privacy can be achieved through the use of a TLS-encrypted connection to a web application over the Internet. Any web application can be securely and privately shared with employees no matter where they are: head office, a remote branch office, on the road, or working from home.
The need to backhaul client connections to the head office and route them to the server is gone. Performance can be improved, through lower latency, and complexity can be removed by simply allowing clients to connect to modern HTTPS services over the Internet.
The Internet was designed to be resilient. If one route dies, another route can be found – that’s not always strictly true but that’s the theory behind the military origin of the Internet. HTTP or HTTPS handles latency over the Internet better than legacy client/server protocols, making web applications a perfect fit for modern design.
You can understand why the use of web applications has exploded when you consider the benefits of their use. The increased use of web applications requires that we consider suitable protection for this growing attack vector.
WAF vs. firewall
The heart of network security is usually a firewall appliance or firewall. The firewall is perfect for dealing with filtering and dealing with general network traffic but it is a generalist that inspects traffic lower in the stack, focusing mostly (but not exclusively) on transport protocols such as TCP, UDP, and ICMP.
The Web Application Firewall is designed to handle one thing: traffic destined for web applications. The WAF understands requests at the application layer (HTTP or HTTPS). The WAF is designed to defend against the misuse of HTTP/HTTPS.
Many networks will include a WAF and a firewall. An example of this scenario might be where:
- A web application presents a service to the Internet. Requests to the web application are inspected at the application layer and malicious use of HTTP/HTTPS is blocked.
- Access to other services by the web application might be routed through the firewall The network firewall will limit internal traffic based on source/destination/protocol/port rules to enforce desired isolation and to reduce the blast area of a successful breach (through whatever means).
What features does a WAF contain?
The specialized role of the Web Application Firewall requires it to provide several essential features.
Protect against web application attacks
The primary purpose of the Web Application Firewall is to protect web services from online attacks. Other attacks on the network will come via different vectors that should be protected against using methods such as a network firewall, anti-malware, identity protection, processes, education/awareness, and more.
Some of the types of attacks handled by a WAF
A malicious actor tries to use the features of HTTP/HTTPS protocol and the web application against the intended victim. These kinds of attacks might include:
- Probe: Scanning a web application to understand the architecture and find one or more vulnerabilities.
- Cross-Site Scripting (XSS):A website can use input from a user to generate output. An attacker can inject code into a web application with the intention of it being used by other clients.
- SQL Injection: The purpose of this is to use sequences of special characters to send a command to a backend SQL Server and break out a command, such as launching a shell, that can be leveraged by the attacker.
- Distributed Denial of Service (DDOS): A form of attack that uses huge amounts of traffic to shut down a web application (or all applications) to either stop operations, distract the security staff, or expose a vulnerability.
- Cross-Origin Resource Sharing (CORS): A web client can manipulate the headers of a request to demand target content that should not be shared.
- Binary planting: Where an attacker plants an executable file with malicious code to attack either a web application or clients.
Monitoring and logs
An essential task of any firewall is to enable monitoring and logging. The Web Application Firewall, whether it is physical or virtual, on-premises or cloud-based, has some finite throughput capacity. Monitoring the WAF is essential to manage performance.
For example, a WAF might need to have more capacity during a period of abnormally high traffic, such as Black Friday. Without monitoring, one will not understand the demand for resources before the event and be unable to plan capacity availability. During the event, monitoring will ensure that planning was correct or that additional capacity must be provided to avoid loss of service availability, reputation damage, or profitability.
Logs provide a history of requests that pass through the Web Application Firewall and the ability to inspect traffic. This kind of data is essential in troubleshooting. One of the things to consider with a WAF is that it can create “false positives”, incorrectly blocking traffic that the WAF thought was malicious. Logs can assist with determining why the traffic was blocked and allow for remediations to be made either in the WAF or the web application to prevent repeat mistakes.
The WAF is the first (and maybe the only) entry point to the network for many applications. This entry point can be a tripwire for other security systems. Data from these logs can a part of incident detection and unified incident investigations when combined with data from other security systems through the use of a Security Information and Event Management (SIEM) system.
Network traffic analysis
Network traffic analysis uses several tools to inspect live and previous traffic using machine learning and behavioral analysis. Threats can be detected live on the network using an intelligent system that is not based on a set of rigid one-size-fits-all rules.
Application profiling
Application profiling is a feature that learns the typical usage of an application. For example, a data entry field might typically contain a certain type of text. An attacker tries to find vulnerabilities by doing the unexpected, such as placing a complex set of characters into a data field to launch a Bash shell on a Linux machine. Application profiling will understand that this attempt is unusual and block it from ever reaching the web server.
Content delivery network (CDN)
The performance of a web application, particularly one used directly by humans, can have a direct impact on the further use of that site by the client. If an e-commerce site is slow, the customer will go elsewhere. The use of a Content Delivery Network (CDN) places much of the content of a web application in a series of globally dispersed caches that are closer to the client. When a client opens a site with lots of images, then the images are loaded from the local cache instead of being downloaded from a distant web server.
Performance can also impact the service provider. If a media-rich site is receiving a lot of traffic, there can be a need to deploy more web servers. The media can instead be cached in a CDN, allowing the service provider to run fewer web servers and reduce infrastructure costs.
Types of web application firewalls (WAF vs WAAP vs RASP vs IPS)
Four kinds of Web Application Firewall might be used.
Web Application Firewall (WAF)
A Web Application Firewall acts as a security barrier between the client and the webserver to protect against attacks such as SQL Injection or Cross Site Scripting by inspecting the application layer and blocking suspected malicious traffic.
Web Application Attack Protection (WAAP)
WAAP extends the concept of a Web Application Firewall by building in additional features such as:
- Bot mitigation: Many attacks come from bot networks (nets). Dedicated protections can be used to block known botnets or suspected bot activity.
- Application-layer DDoS protection: Many DDoS attacks use a huge amount of low-level requests to overload a web application. Application-layer attacks use weaknesses in the HTTP protocol to shut down web applications.
- Behavioral analytics: Modern systems that understand usage instead of implementing legacy rules that are rigid, predictable (for the attacker), and subject to false positives.
Runtime Application Self-Protection (RASP)
Protections are placed in the application instead of at the network edge. One advantage of this method is that the protection systems can monitor the code of the web application. A second advantage is that the protections know the code of the web application and reduce the risk of false positives. However, the protections are at the heart of the web application and not at the network edge and require developers that are skilled in application security.
Intrusion Prevention Systems (IPS)
This is a form of inspection at the network layer that analyses the patterns of traffic passing through the appliance. Much like anti-malware, a frequently updated database describes malicious patterns and these are used to prevent attacks as they happen. IPS is typically a feature of the (network) firewall that brings additional value to the application layer inspection provided by the WAF/WAAP.
Web Application Firewall deployment methods
A WAF is deployed at the “network edge” but the method of that deployment can vary.
Network-based
The network-based WAF is deployed on the same network (or collection of networks) as the web application(s) that it protects. The WAF might be in the network core (or hub) or the same subnet/virtual network as the web application.
The WAF is an appliance of some kind with a finite set of instances. Each instance has a finite capacity for CPU, memory and throughput, that affects the scalability of the web application. Capacity can be expanded or reduced based on the demand of the web application.
An advantage of the network-based WAF is that it is at the actual entry point to the network; there is no way to avoid it as an attacker.
Cloud-based
A cloud-based WAF is an offering that is provided by a third-party service provider. The DNS names for the web application redirect clients to the cloud-based WAF. The cloud-based WAF will relay permitted traffic to the web application that is hosted elsewhere.
The big advantage of a cloud-Based WAF is that the protection is outside of your network. As a SaaS solution, it means that there is less maintenance for the web application operator to handle. Often, the cloud-based WAF is combined with a CDN, combining security and performance enhancements.
Host-based
Unlike the other options, the host-based WAF is placed on the web server(s) offering the potential of RASP functionality. By being integrated with the web application, the WAF can truly understand the application. This can mean that protections are uniquely tuned to the profile of the web application and that false positives should be reduced.
Comparing popular Web Application Firewall solutions
There are many players in the WAF market. This section will briefly describe some options.
Azure Web Application Firewall
The Azure WAF is a platform-as-a-service offering from Microsoft for customers of Azure. The Azure WAF falls into the category of WAAP, offering bot mitigation and application layer DDoS protection (with an additional Standard or per-IP protection plan) in addition to a collection of protections from a set of static OWASP rules.
The Azure WAF can be deployed as a network appliance by adding an additional paid-for add-on to the Azure Application Gateway. It can alternatively be deployed with Azure Front Door, which moves the network edge to one of over 170 edge data centers around the world to accelerate application performance by reducing latency and offering CDN functionality.
The Azure WAF can be managed through the Azure Portal and using infrastructure-as-code. It is deeply integrated into Azure Monitor for monitoring/alerting and, therefore, into Microsoft Sentinel (SIEM).
AWS Web Application Firewall
AWS Web Application Firewall is a WAF offering provided by Amazon Web Services (AWS). Users can define custom inspection rules for the attributes of incoming requests, including headers, body content, and URI parameters.
The AWS WAF can be deployed in combination with Amazon CloudFront, Application Load Balancer, and API Gateway. This makes it easy to deploy and able to provide WAF protections across distributed architectures.
AWS CloudWatch provides monitoring of real-time activity and security events.
Fortra Managed WAF
A WAF can be a complex appliance to manage. A set of pre-built rules attempt to protect the web application, but many application-layer protections have difficulties in discerning between correct and malicious usage. For example, a webhook sent to a listener is easily confused with a SQL injection attack by a rule that expects the number of special characters in a request to be low.
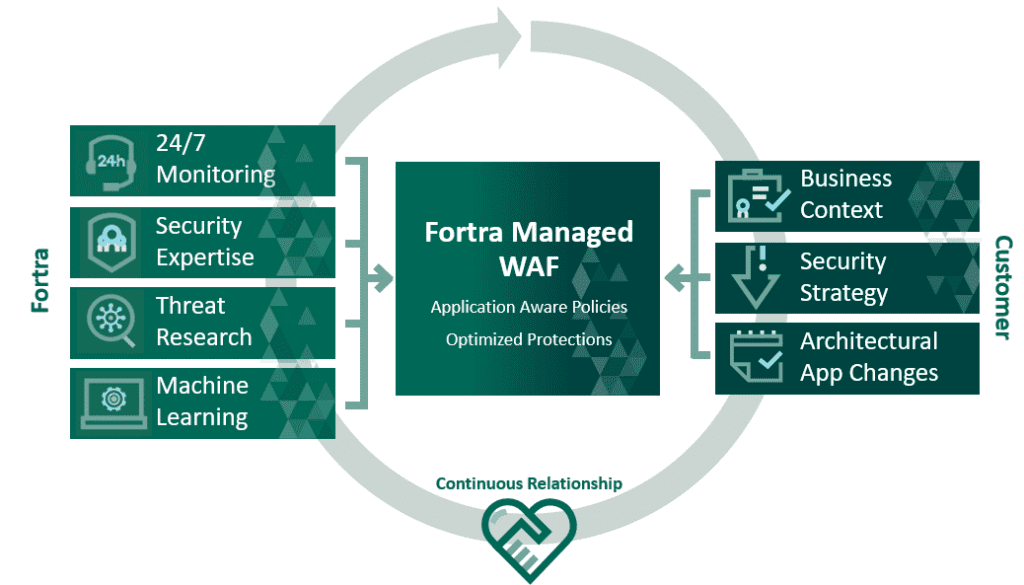
The Fortra Managed WAF is a solution where Fortra deploys, configures, and manages your WAF. The advantage is that developers can focus on coding and security operators can concentrate on dealing with incidents. The complex tasks of configuring a WAF to protect the organization, without shutting down services, are handled by teams of experts.
Built-in defenses include OWASP Top 10, URL tampering, web scraping, buffer overflow attacks, Zero-Day web application threats, and DoS attacks. Behavioral analytics is also used in addition to rules-based protection.
Cloudflare WAF
Cloudflare is a well-known service provider in the market for accelerating application performance through a large network of globally dispersed data centers. WAF functionality is provided by a rules-based engine that is boosted by a threat intelligence system using data from millions of websites.
DDoS protection is provided and unmetered – using a third-party cloud for DDoS protection isolates the attacker from your network(s). Some form of bot mitigation is provided depending on the plan that you subscribe to.
Open source options
Open source solutions will be a primary choice for certain segments that favor free software and open inspection of source code. Some WAF solutions are available as open-source solutions. Some of the options include:
- ModSecurity: A solution that is over 20 years old but will no longer be supported after July 1, 2024.
- Coraza: This is a relatively young WAF that appears to be a replacement for ModSecurity. Many features are still not available.
- open-appsec: This is a newer entry to the market that benefits from a strong community and official third-party code audit. Two machine learning models are used to analyze every request.
What you should look for in a good Web Application Firewall solution
If an organization is going to run web applications with an online presence, then it must use a WAF to protect those and other assets. There are many WAF options on the market so one must know what essential features to look for.
Customizable security rules
Rules are used by a WAF to measure the risk of requests to web applications. A rule may be written for an ideal world, but not all rules are suitable and can lead to false positives, which result in failed requests.
Customization should be possible to override the rule. However, overrides should be granular when necessary – i.e. associated with a web application or a specific URI or even a part of a request for a URI.
Scalable
Modern applications are designed to be elastic, taking advantage of cloud scalability and pay-as-you-go consumption models. As demand for a web application grows/shrinks, the WAF must also be able to grow/shrink.
But scalability must also be present at a global level – enabling a web application to be secured closer to the client and allow for a faster user experience.
Flexible deployment
It should be possible to have a choice of where to deploy the WAF:
- The cloud
- Locally on the network
- On the web server
Ideally, there should be a similar set of features and operating experience across the different deployment scenarios.
Fortra WAF solution
Fortra’s Alert Logic delivers a competitively priced, versatile, enterprise-level, and cloud-ready WAF that comes with a team of experts to eliminate the complexity for you. Managed services experts handle installation and deployment through to configuration, ensuring that the WAF is ready to block threats against your critical web applications.
Features of the WAF-as-a-service include:
- 24/7 support by a security operations center
- Managed deployment
- Ongoing management and tuning
- Zero-day and emerging threat detection
- Rule and behavior-based detection
- Credential attack protection
- Bot management
- Virtual patching
- Adaptive trust-based policies
- Threat intelligence
- Auto-scaling and high availability
- Cloud deployment readiness
- Application delivery controls
Businesses need to distinguish the good traffic from the bad in real-time, and accurately. Fortra’s Alert Logic lets you focus on service development and delivery while Fortra manages your WAF security.
Table of contents
- What is a Web Application Firewall (WAF)?
- How does a WAF work?
- Why is a WAF important?
- WAF vs. firewall
- What features does a WAF contain?
- Types of web application firewalls (WAF vs WAAP vs RASP vs IPS)
- Web Application Firewall deployment methods
- Comparing popular Web Application Firewall solutions
- What you should look for in a good Web Application Firewall solution
- Fortra WAF solution



