Implementing Access Controls using Microsoft Intune

Implementing identity and access management processes is an effective way to protect sensitive corporate data. It allows organizations to regulate user access and prevent instances of identity theft, data breaches, and unauthorized access to confidential corporate information. In this article, we’ll detail how organizations can significantly minimize their exposure by controlling access privileges with Microsoft Intune.
The problem with local administrator privileges
Access management is a fundamental aspect of modern IT security operations for corporate devices. While the practice of providing non-privileged user accounts to users has long been established, it is increasingly important to protect sensitive corporate data. The growing reliance on technology and the rising threat of cyber-attacks are just two factors here.
Providing users with local administrator privileges is a common practice in many organizations, but it can create significant security risks. Local administrator privileges provide users with extensive control over their devices. This can include the ability to modify system settings and install or remove software in the System context or for all users.
This level of access can make it easy for users to accidentally or intentionally introduce malware or other security threats to corporate devices by clicking malicious links or deliberately tampering with system settings to allow unauthorized access.
Often, users are granted local administrator privileges to reduce the burden on IT support teams. It is thought that by allowing users to install their own software, helpdesk tickets will reduce in volume. In reality, with admin privileges, users may be more likely to experience system errors or software conflicts, leading to increased support requests and time-consuming troubleshooting.
Providing users with local administrator privileges can also make it difficult for IT administrators to manage and enforce security policies, as users with elevated privileges can bypass security measures. If users inadvertently disable or change security features, it can also leave the rest of the corporate network open to attacks.
The ITSecOps challenge
For all of the reasons mentioned above, it has long been known that it is not a good idea for standard users to have privileged access to their work computers. That said, preventing users from having local admin privileges is a common challenge for IT administrators as it can be difficult to find the right balance between security and usability.
For example, some applications require local admin rights to function correctly, making it difficult to restrict access without disrupting business operations. This can be especially true for legacy software that may be critical to the organization.
IT administrators must also consider the potential impact on productivity and user experience. If users frequently require admin rights to complete their work, restricting this access could lead to delays, negatively affecting business operations.
How organizations can restrict local administrator privileges
To mitigate these security and management risks, it is recommended that organizations limit local administrator privileges to a select group of trusted IT pros.
Alternatively, IT teams can employ strategies such as least privilege access and role-based access control, which grant users access based on their job responsibilities and limit access to only the minimum resources required to complete their work. This approach provides users with the necessary access to complete their work while minimizing the risk of introducing security threats to corporate devices.
User Account Control (UAC)
One approach to implementing Endpoint Privilege Management is via User Account Control (UAC). This security feature is designed to prevent unauthorized changes to a computer.
When enabled, UAC prompts the user for authorization before allowing certain types of changes. This feature is an important component of Microsoft’s overall security vision and is crucial for organizations that want to deploy a better-managed desktop environment.
With UAC enabled, apps and tasks always run in the context of a standard user account, even if the user has administrative privileges on their computer. This means that any attempt to make changes to the system settings or files will trigger a UAC prompt.
In enterprise environments, UAC is combined with the approach of limiting privileged access for standard users. This way, when a user attempts to launch an elevated process or install an application in the elevated context, they receive a prompt for administrator credentials – something they typically do not have.
UAC is enabled by default for Windows 10 and Windows 11 computers that are joined to Active Directory or Azure Active Directory.
Windows Local Admin Password Solution
Windows Local Administrator Password Solution (Windows LAPS) is a feature on Azure Active Directory-joined and domain-joined devices that automatically manages the password of the local administrator account. It is a cloud-native iteration of the traditional on-premises Local Admin Password Solution (LAPS) feature.
At present, Windows LAPS is now natively integrated into Windows 11, Windows 10, and Windows Server, but support for Azure Active Directory is in private preview.
Credential Guard
Credential Guard is a security feature in Windows 10 and later that uses virtualization-based security to protect sensitive information like domain credentials. It helps prevent attackers from stealing these credentials and using them to gain unauthorized access to your network.
Credential Guard works by isolating credentials in a virtualized environment, which only trusted system processes can access.
It’s very simple to enable Credential Guard for Windows 10 and later devices. Here’s the step-by-step:
- In the Intune admin center, select Devices.
- Select Configuration Profiles.
- Select Create Profile > Windows 10 and later > Settings catalog > Create.
- Configuration settings: select Device Guard as category.
- Configure required settings.
While it’s easy to enable, it’s important to verify that your configuration has had the desired effect. Here’s a very simple way to verify that Credential Guard is running on a target machine.
- In Start, type msinfo32.exe, and then select System Information.
- Select System Summary.
- Confirm that Credential Guard is listed in Virtualization-based security Services Running.
Microsoft Intune Suite: A unified platform for managing endpoints
The Microsoft Intune Suite was recently announced as an advanced endpoint management and security package. It’s intended to unify, consolidate, and replace existing third-party endpoint management and security tools to establish the Intune Suite as the single platform for managing endpoints. It includes:
- Microsoft Intune Remote Help
- Microsoft Intune Endpoint Privilege Management
- Microsoft Tunnel for Mobile Application Management
- and more…
Pricing
Until very recently, new features released to General Availability for Intune were automatically available to all organizations that have the Microsoft Intune license assigned to their users. With this release, Microsoft has shaken things up a little, announcing that the Intune Suite release is available for an additional fee of $10/user/month.
Microsoft Intune Endpoint Privilege Management
Microsoft Intune Endpoint Privilege Management allows IT and SecOps teams to provide all users with a Standard User account, elevating privileges only when required. This supports the enforcement of least privilege access concepts.
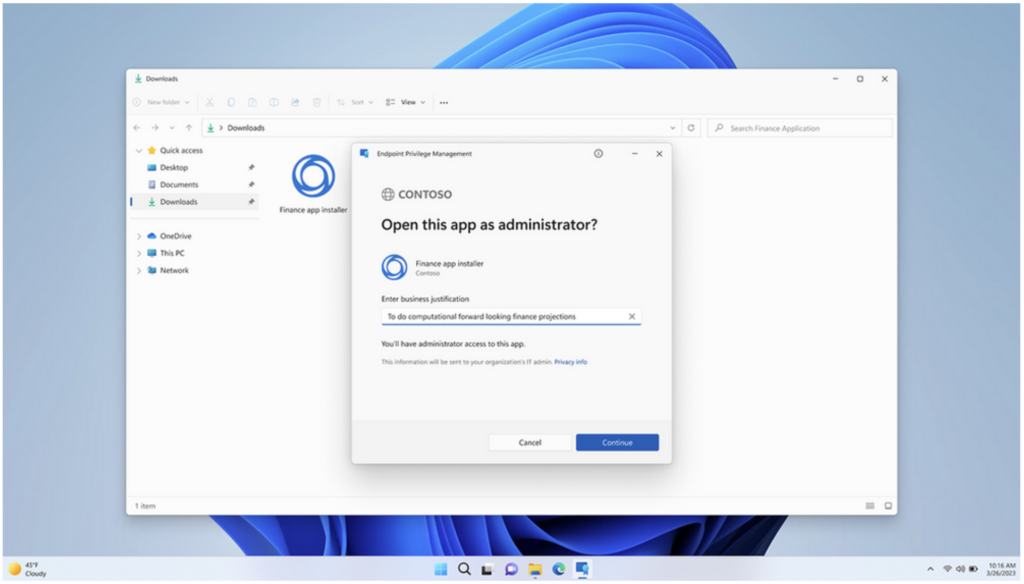
Endpoint Privilege Management has the potential to revolutionize the approach to providing privileged access to users. It allows administrators to create elevation policies, with elevation rules setting the conditions for users to get just-in-time (JIT) elevated access.
For example, a user could have permission to install applications provided they give a business justification. This justification is audited and sent to IT for review.
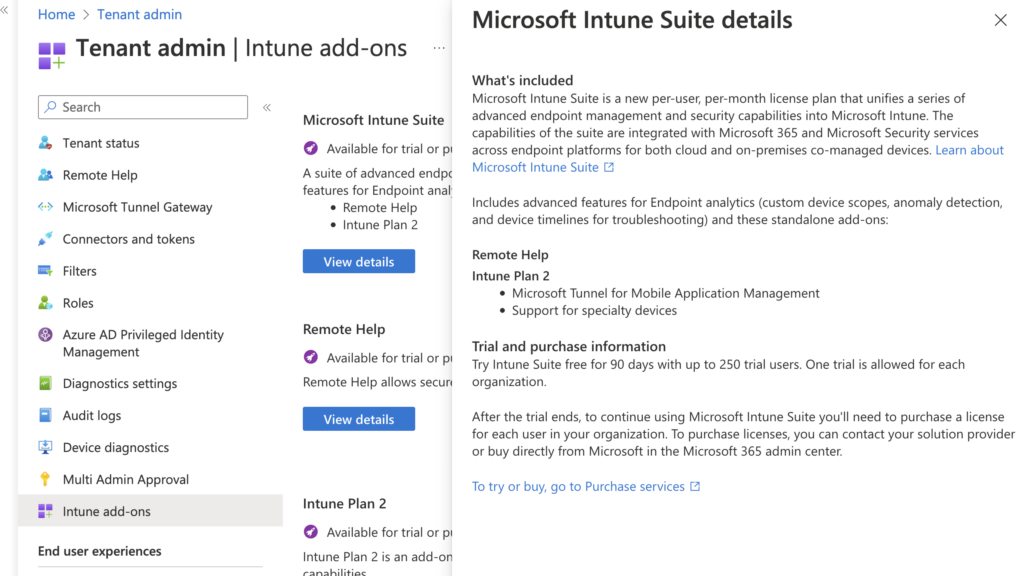
Availability
The Microsoft Intune Suite is available for trial and purchase today. At launch, it only includes Remote Help, Microsoft Tunnel for MAM, and Support for Specialty devices, but Endpoint Privilege Management and Advanced Endpoint Analytics were released in April.
Microsoft Intune Suite brings next-gen endpoint management capabilities
The capabilities of Microsoft Intune are constantly improving and developing, giving IT admins additional controls to enforce the principle of least privilege on their managed endpoints. The release of the Microsoft Intune Suite has brought next-generation capabilities that were previously only available via third party add-ons. But with its relatively high cost per user, it remains to be seen if organizations seriously consider it as an option for their business.



