How to Protect Windows Devices with Microsoft Defender for Endpoint

Endpoint security plays a vital role in safeguarding enterprise cybersecurity, particularly in the context of remote work scenarios. As the number of endpoints accessing corporate networks rises with the growth of remote work, the need for robust endpoint security becomes increasingly paramount, enabling a secure environment for users on the move. In this article, I will detail how you can protect Windows devices using Microsoft Defender for Endpoint, the company’s enterprise endpoint security platform.
What is Microsoft Defender for Endpoint?
Defender for Endpoint is a comprehensive solution that encompasses a wide range of capabilities designed to counter advanced threats on various devices, including Windows, Linux, macOS, iOS, and Android platforms. It leverages behavioral sensors, cloud security analytics, and threat intelligence to deliver robust protection against cyberthreats.
In addition to its advanced threat protection capabilities, Microsoft Defender for Endpoint offers a suite of features, such as vulnerability management and assessment, attack surface reduction, automatic investigation and remediation, and managed hunting services. It is available in two plans, Plan 1 and Plan 2, with the option to add a vulnerability management feature.
I should be clear that Microsoft Defender for Endpoint is an integral part of Microsoft 365 Defender, which is an Extended Detection and Response (XDR) solution. This comprehensive security solution provides unified visibility and protection across endpoints, identities, emails, and cloud applications, offering enhanced security and centralized management for organizations.
By combining its powerful threat detection and response capabilities with its integration into Microsoft 365 Defender, Microsoft Defender for Endpoint presents a comprehensive and unified approach to enterprise security.
How to enable Microsoft Defender for Endpoint
Let’s enable Microsoft Defender for Endpoint in our environment:
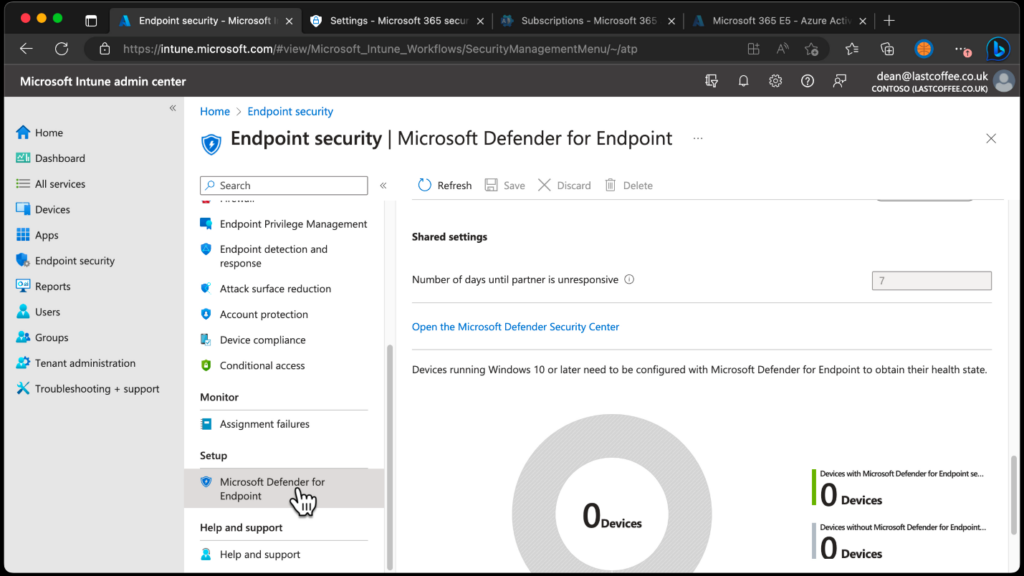
- Sign in to the Microsoft Intune admin center.
- Select Endpoint security > Microsoft Defender for Endpoint, and then click Open the Microsoft Defender portal.
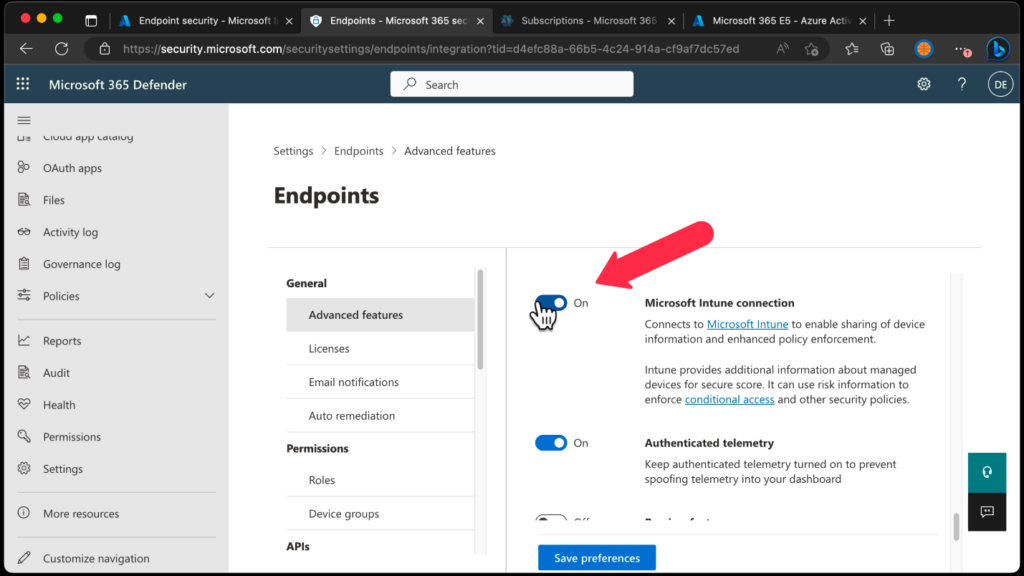
- In Microsoft 365 Defender, (previously the Microsoft Defender Security Center):
- Select Settings > Endpoints >Advanced features.
- For Microsoft Intune connection, choose On.
- Select Save preferences.
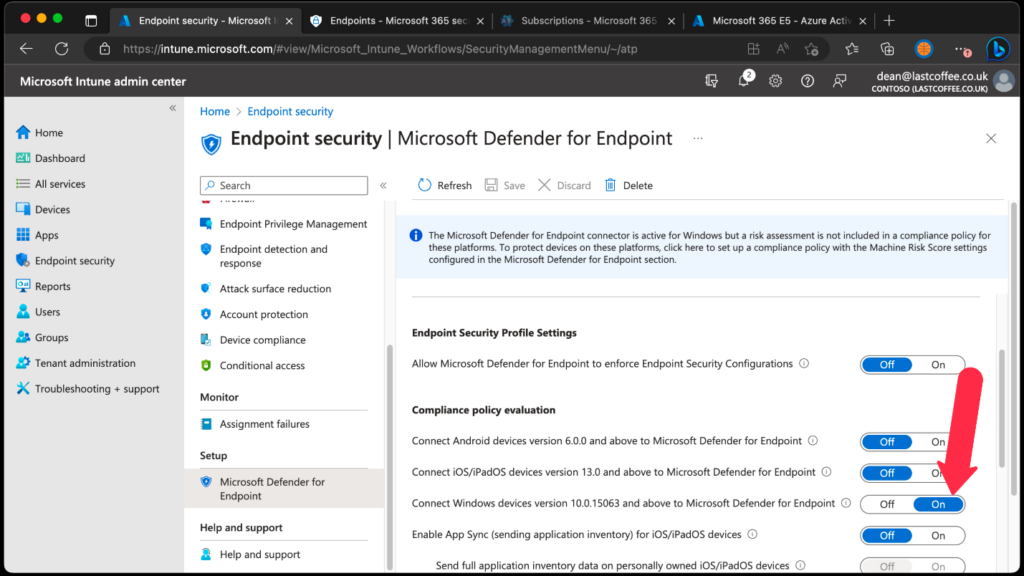
- Next, return to the Microsoft Defender for Endpoint page in the Microsoft Intune admin center.
- To use Microsoft Defender for Endpoint with compliance policies, configure the MDM Compliance Policy Settings. To do that, just set Connect Windows devices to Microsoft Defender for Endpoint to On.
Onboarding and offboarding for Microsoft Defender for Endpoint
In the context of Microsoft Defender for Endpoint, onboarding refers to the process of connecting and integrating a device into the Microsoft Defender for Endpoint environment. It involves setting up the necessary configurations, policies, and security measures to ensure that the device can effectively utilize the advanced threat protection capabilities provided by Microsoft Defender for Endpoint.
Minimum requirements for onboarding
The supported Windows editions for Microsoft Defender for Endpoint include:
- Windows 11 (Enterprise, Education, Pro, and Pro Education)
- Windows 10 (Enterprise, Education, Pro, and Pro Education)
- Windows 8.1 (Enterprise and Pro)
- Windows 7 SP1 (Enterprise and Pro, Requires ESU for support)
- Windows Server
- Windows Server 2008 R2 SP1 (Requires ESU for support)
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server version 1703 or later
- Windows Server 2019 and later (including Core Edition)
- Windows Server 2022
Onboarding process
Let’s onboard a device:
- Sign in to the Microsoft Intune admin center.
- Select Endpoint security > Endpoint detection and response > Create Policy.
- For Platform, select Windows 10 and Later.
- For Profile type, select Endpoint detection and response, and then select Create.
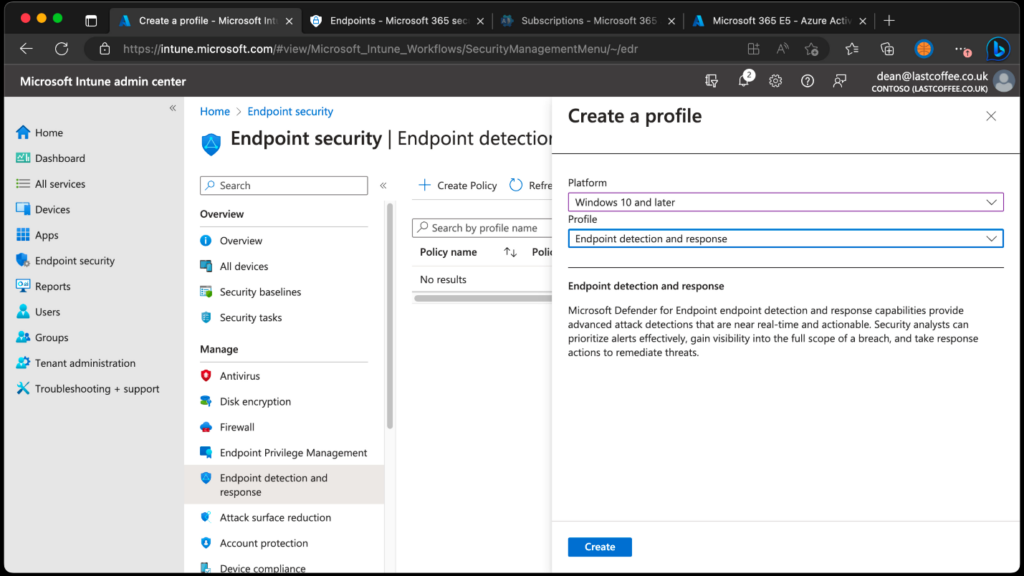
- On the Basics page, enter a Name for the profile, then choose Next.
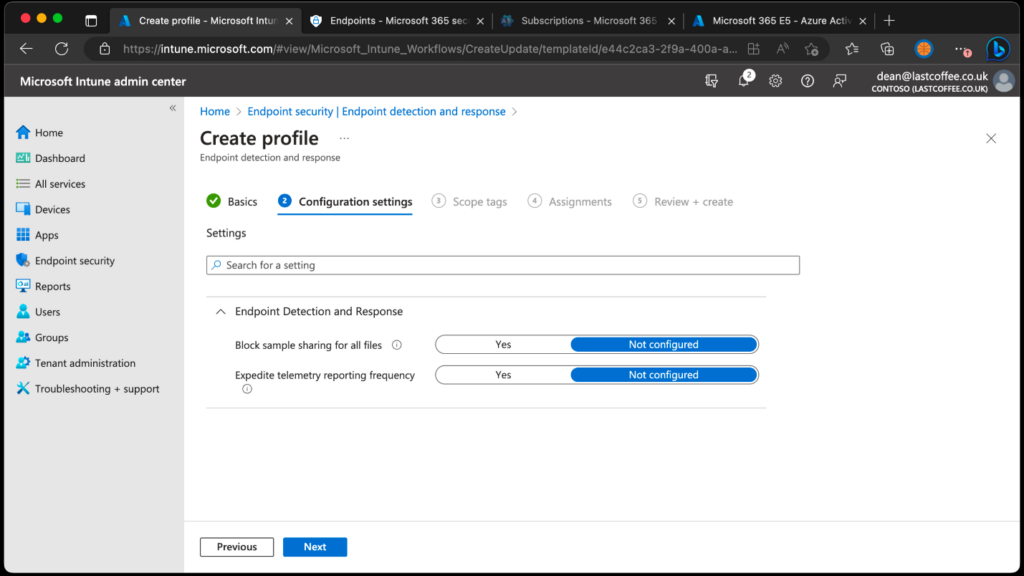
- On the Configuration settings page, configure the following options for Endpoint Detection and Response:
- Block sample sharing for all files: Modifies the configuration parameter for Microsoft Defender for Endpoint’s sample sharing feature.
- Expedite telemetry reporting frequency: Enable this option for devices categorized as high risk to ensure more frequent transmission of telemetry data to the Microsoft Defender for Endpoint service.
By completing these steps, devices targeted by the policy will be onboarded to the Microsoft Defender for Endpoint service.
Creating an attack surface reduction policy
Microsoft Defender for Endpoint’s attack surface reduction capabilities are your endpoint’s first line of defenese against well known attacks and exploits. Attack surface reduction includes various features such as exploit protection, device control, app and browser Isolation, web protection, and app control.
Let’s create a basic attack surface reduction policy.
- Sign in to the Microsoft Intune admin center.
- Select Endpoint security > Attack surface reduction > Create Policy.
- For Platform, select Windows 10, Windows 11 and Windows Server.
- For Profile, select Attack Surface Reduction Rules, and then select Create.
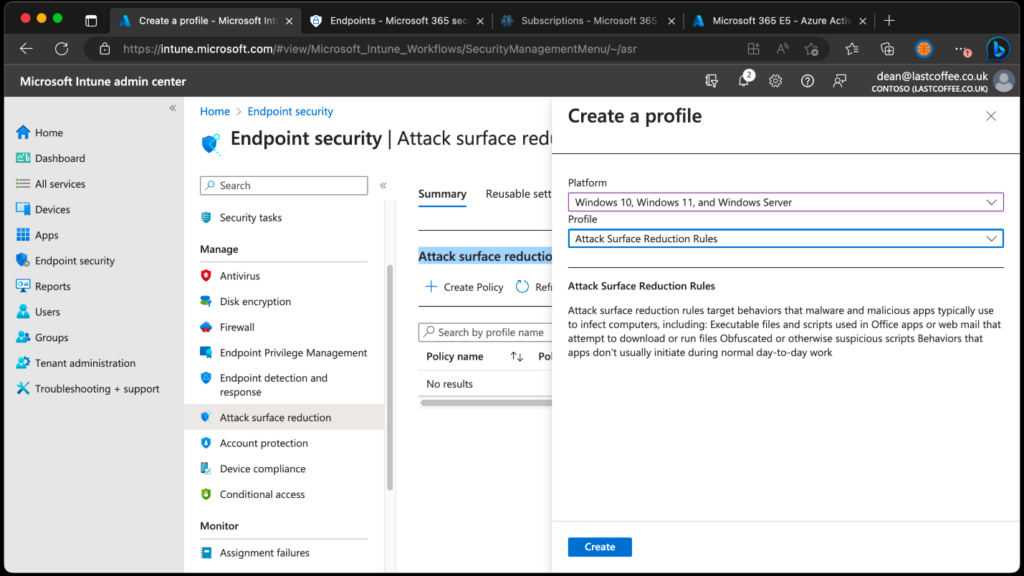
- On the Basics page, enter a Name for the profile, then choose Next.
- On the Configuration settings page, configure the required options for Attack Surface Reduction.
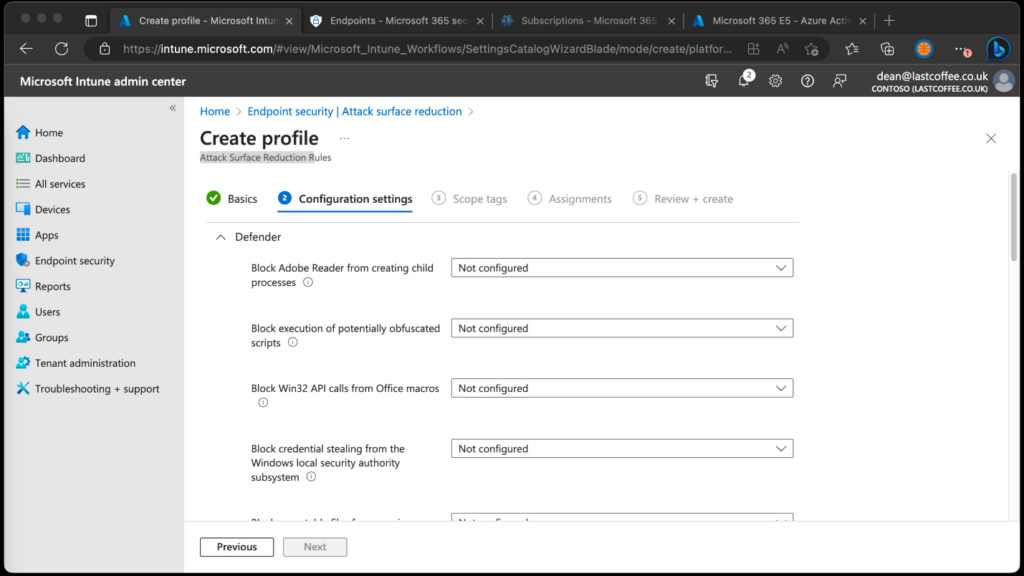
- Once complete, choose Next.
- In the Assignments tab, choose Add groups to select a group, or Add all devices to deploy the policy to all onboarded endpoints.
- Select Next, then Create.
You’re done!
Securing your endpoints is essential
In the modern business landscape, data holds immense value for organizations. The loss or compromise of data can pose significant risks to an entire business. Endpoints serve as gateways to enterprise networks and they can serve as potential entry points for malicious actors.
Endpoint security software shields these entry points from risky activities and potential attacks. With its attack surface reduction capabilities coupled with the next-generation extended detection and response features, Microsoft Defender for Endpoint is an extremely capable security solution for your endpoints.
Related Article:



