Windows 10 Enterprise Feature: Credential Guard
In this Ask the Admin, I’ll explain how Credential Guard protects domain user account passwords in Windows 10 Enterprise edition.
During the development of Windows 10, Microsoft touted several new security features that would make Windows 10 ‘the most secure version of Windows ever,’ a phrase that gets rolled out every time a major new release of Windows is looming. Although Windows Hello has attracted a lot of media attention, some other features, such as Passport and Device Guard, are intended for corporate use and don’t necessarily get the coverage they might otherwise deserve.
Recently I was looking at the differences between Windows 10 Pro and Enterprise editions, and noticed a feature exclusive to Enterprise: Credential Guard. After scratching my head for a bit wondering what that could possibly be, it clicked that this is what Microsoft had referred to as Virtual Secure Mode (VSM) during the preview. I’d written briefly about VSM on Petri back in May, Windows 10 Security: Microsoft Passport and Virtual Secure Mode, but at that time details were scant.
Now that Windows 10 has launched, what I’d originally assumed to be a feature in all SKUs, is limited for the time being to Enterprise edition. In this article, I’ll dive a little further into the technical details of Credential Guard, and how it works to protect Active Directory domain credentials.
Virtualization-assisted security in Windows 10
Windows 10 uses Isolated User Mode (IUM), which with the help of an Intel VT-x compatible CPU, Trusted Platform Module (TPM) 2.0 and Unified Extensible Firmware Interface (UEFI) 2.3.1, isolates memory in a higher trust level from the OS. No drivers are allowed to run in IUM, and strict signing is enforced. Just the minimum number of binaries are loaded to provide the required functionality, and IUM processes cannot be accessed by the OS, where processes run in Normal Mode.
The complete list of requirements for Credential Guard are as follows:
- Windows 10 Enterprise
- Active Directory (any forest or domain level)
- Physical device (i.e. virtual machines are not supported)
- UEFI firmware 2.3.1 or higher
- Secure firmware update process and MOR implementation
- Secure Boot
- Intel VT-x or AMD-V
- Intel VT-d or AMD-Vi I/O memory management unit
- Second Level Address Translation
- 64-bit CPU
- TPM 2.0
If an Intel VT-d or AMD-Vi I/O memory management unit is not present, Credential Guard can still be enabled, but without Direct Memory Access (DMA) protection. Additionally, if the device has TPM 1.2, or no TPM device, then the keys used to encrypt Credential Guard are not protected.
Isolating the Local Security Authority (LSA)
Virtualization-based security (VBS) and Secure Boot enable Credential Guard to protect domain credentials from malware running in the OS, even if the logged in user has administrative or debug privileges. Domain credentials are especially vulnerable, because once compromised, they can potentially be used to log in to more than one device, or used to obtain other credentials.
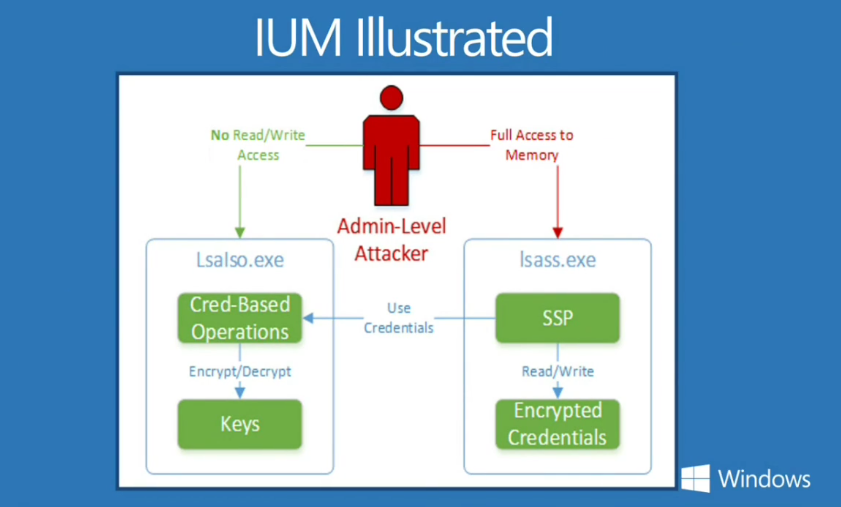
Prior to Windows 10, the Local Security Authority, which the OS uses to store secrets, could be compromised if a process was able to gain privileged access to the OS. When Credential Guard is enabled in Windows 10, the LSA is moved and isolated in IUM, and is accessed by the LSA process in the OS using remote procedure calls (RPC).
Credential Guard is compatible with domain controllers and network resources running any version of Windows Server, thanks to the use of Kerberos and NTLM stubs, leaving software unaware that Credential Guard is enabled on the Windows 10 device. Although Credential Guard doesn’t support legacy cryptography, such as MS-CHAPv2, NTLMv1, or Kerberos with DES.
Computer accounts, Silos and Authentication Policy
Like user accounts, Windows 10 computer accounts use asymmetric key authentication, and this enables them to be stored in IUM. This is important, because computer accounts are also a security object, with administrative access to the device, so need to be protected from credential extraction.
With this knowledge in hand, you can combine Windows Server 2012 R2 Silos and Authentication Policies to ensure that selected users, such as those with privileged access to the domain for example, can only log in to devices where Credential Guard is enabled and also protecting the local machine account. For more information on Authentication Silos and Policies, see Restrict Privileged Accounts with Authentication Silos in Windows Server 2012 R2 on the Petri IT Knowledgebase.
Don’t forget that even when Credential Guard is enabled, you should still follow best practices for privileged accounts. Credential Guard doesn’t protect credentials stored in Credential Manager, or other software that stores passwords, and privileged domain credentials should be used only on devices that are designated specifically for privileged domain administration, reducing the risk of compromise even further.
Enabling Credential Guard
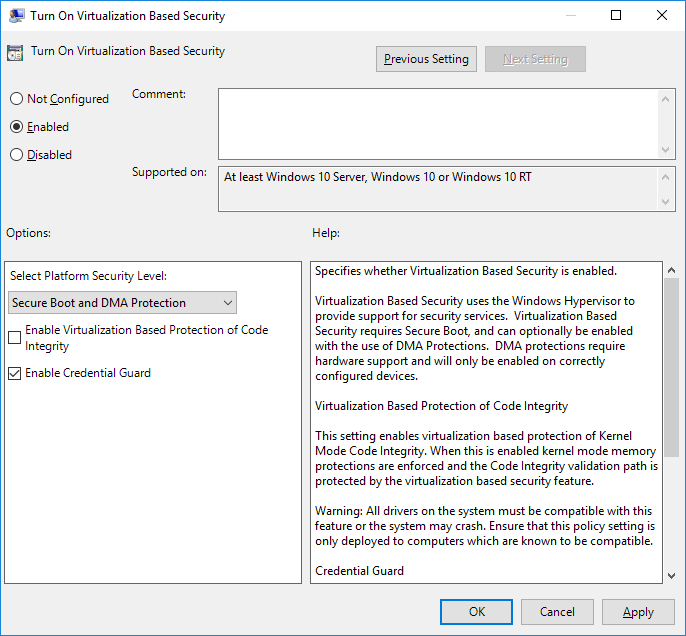
Credential Guard can be managed using Group Policy, and the Turn On Virtualization Based Security setting is located under Computer Configuration > Administrative Templates > System > Device Guard.
To enable Credential Guard in an offline image, enable Hyper-V and IUM from an elevated command prompt using DISM:



