How to Configure Windows LAPS in an Azure Active Directory Scenario

Windows Local Administrator Password Solution (Windows LAPS) is a powerful tool that allows organizations to better manage and protect their local administrator account passwords on Windows devices. This feature is available on Azure Active Directory-joined or Windows Server Active Directory-joined devices. In this article, I will explain how to configure Windows LAPS in an Azure Active Directory (recently renamed Microsoft Entra ID) scenario and how to manage it from Microsoft Entra, the company’s new identity and access management platform.
Windows LAPS vs. Microsoft LAPS: What’s the difference?
Windows LAPS is currently in public preview, with much of the capability available for all Azure Active Directory (Azure AD) customers. While the legacy Microsoft LAPS is still available for download, Windows LAPS offers several advantages over its predecessor.
- Firstly, Windows LAPS is an entirely separate implementation that is native to Windows.
- Windows LAPS also includes several new features not available in legacy Microsoft LAPS, such as the ability to back up passwords to Azure AD, encrypt passwords in Windows Server Active Directory, and store password history.
- Since Windows LAPS is now included in Windows, additional licensing is not required to take advantage of it. It’s also possible to use with the Azure AD free tier, meaning Azure AD Premium licensing is not required.
The vast adoption of legacy Microsoft LAPS over the previous decade means that this new solution will need to offer a migration procedure that’s as simple as possible. The migration process that Microsoft recommends to organizations is a side-by-side approach: They can run both solutions in parallel until the migration to the new Windows LAPS is complete.
The new native Windows LAPS capabilities are included in the April 2023 Patch Tuesday updates, and they support the following editions of Windows and Windows Server:
- Windows 11 (Pro, Education, Enterprise)
- Windows 10 (Pro, Education, Enterprise)
- Windows Server 2019
- Windows Server 2022
If you’re using any of these versions of Windows and you’ve installed the April 2023 security updates, you’re ready to go and start configuring Windows LAPS. There’s no separate installer or agent required! However, while Windows LAPS is now built-in, you will likely need to use a configuration tool such as a Group Policy Object (GPO), ConfigMgr, or Intune to manage configurations on the client.
Before we get started with the configuration of Windows LAPS, you should be aware that Microsoft has acknowledged two potential regressions related to interoperability with legacy LAPS scenarios. “If you install the legacy LAPS agent on a device patched with the April 11, 2023 security update and an applied legacy LAPS policy, both Windows LAPS and legacy LAPS will enter a broken state where neither feature will update the password for the managed account,” Microsoft explained. As of this writing, the company is already working on a fix for this issue.
Windows LAPS configuration in an Azure AD Scenario
Windows LAPS for Azure AD joined devices can be configured with just a few clicks. We’ll start by enabling the feature tenant-wide. Microsoft recommends using the Microsoft Entra portal for the best experience.
Enabling Windows LAPS from the Microsoft Entra admin center
- Browse to the Microsoft Entra admin center select choose Go to Azure Active Directory
- From Azure AD, choose Devices → All Devices.
- Here, open the Device settings menu.
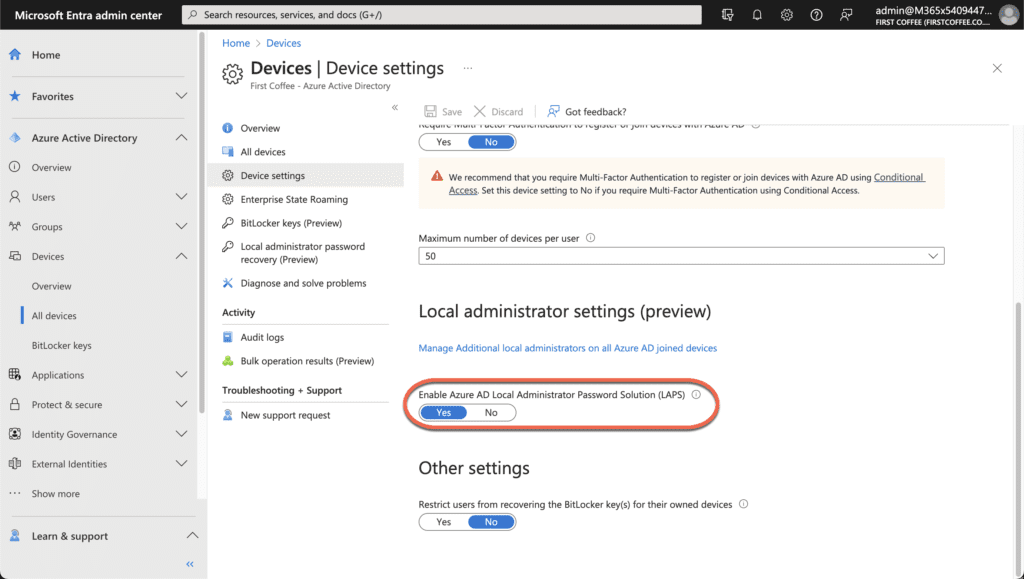
- Scroll down to the Local Administrator Settings (preview) section.
- Toggle the slider for Enable Azure AD Local Administrator Password Solution (LAPS) to Yes.
Once enabled at the Azure AD tenant level, we can move to Intune and explore the various methods to configure Windows LAPS.
Configuring Windows LAPS within Intune
Here are the different ways to configure Windows LAPS within Intune.
- Windows Powershell with the Azure AD Powershell Module.
- Deploying a custom Open Mobile Alliance – Uniform Resources (OMA-URI) profile that uses a Windows Configuration Service Provider (CSP).
- The Intune settings catalog.
- A rich native Intune configuration profile.
Depending on your use case, you may choose any one of the above options to configure Windows LAPS for Azure AD joined devices. In this guide, however, I’ll show you how to do that using a rich native Intune configuration profile.
- From the Microsoft Intune admin center, choose Endpoint Security:
- Next, click on Account Protection.
- On this page, click on Create Policy.
- In the platform dropdown menu, choose Windows 10 and later.
- In the Profile box, choose Local admin password solution (Windows LAPS).
- Click on Create when you’re done.
- Now, you’ll have to enter a name and description for your profile and click Next.
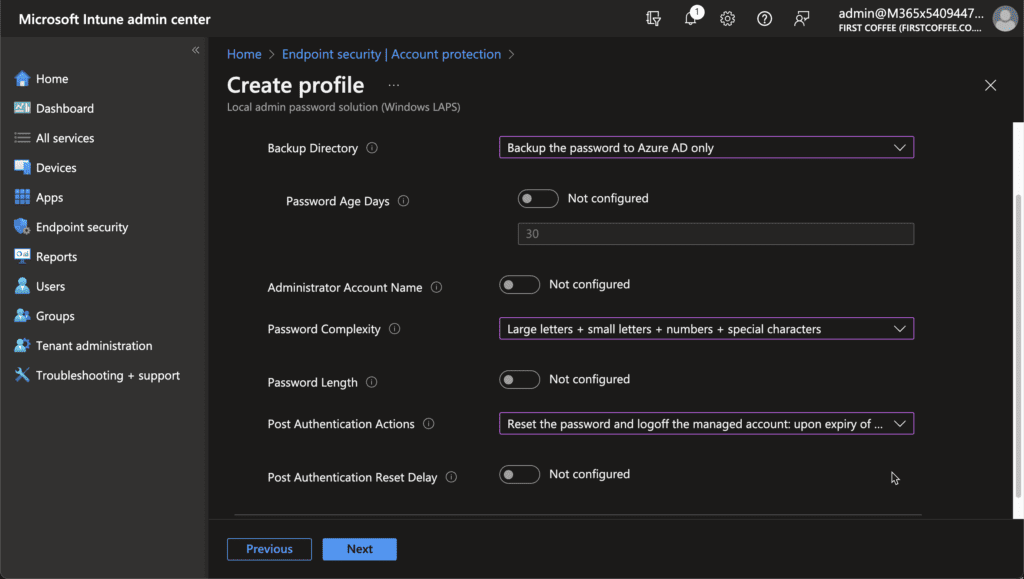
- In the Configuration settings tab, configure the policy as required using the reference table below
| Setting | Description | Default | Options |
|---|---|---|---|
| Backup Directory | Use this setting to configure which directory the local admin account password is backed up to. | Disabled (password will not be backed up). | – Disabled (password will not be backed up). – Backup the password to Azure AD only. – Backup the password to Active Directory only. |
| Password Age Days | Use this policy to configure the maximum password age of the managed local administrator account. | 30 | 1 to 365 for AD 7 to 365 for Azure AD |
| Administrator Account Name | Use this setting to configure the name of the managed local administrator account. Note: This option does not create an account, it only determines which account is to be managed if present. | If not specified, the default built-in local administrator account will be located by a well-known SID (even if renamed). | |
| Password Complexity | Use this setting to configure the password complexity of the managed local administrator account. | Large letters + small letters + numbers + special characters | – Large letters – Large letters + small letters – Large letters + small letters + numbers – Large letters + small letters + numbers + special characters |
| Password Length | Use this setting to configure the length of the password of the managed local administrator account. | 14 characters | 8char to 64char |
| Post Authentication Actions | Use this setting to specify the actions to take upon expiration of the configured grace period. | Reset the password and log off the managed account. | – Reset password: upon expiration of the grace period, the managed account password will be reset. – Reset the password and log off the managed account. -Reset the password and reboot. |
| Post Authentication Reset Delay | Use this setting to specify the amount of time (in hours) to wait after an authentication before executing the specified post-authentication actions. | 24 hours | 0 (disabled) to 24 hours |
- Once you’ve chosen the right configuration, click Next.
- On the Scope tags screen, assign any scope tags that are required and click Next.
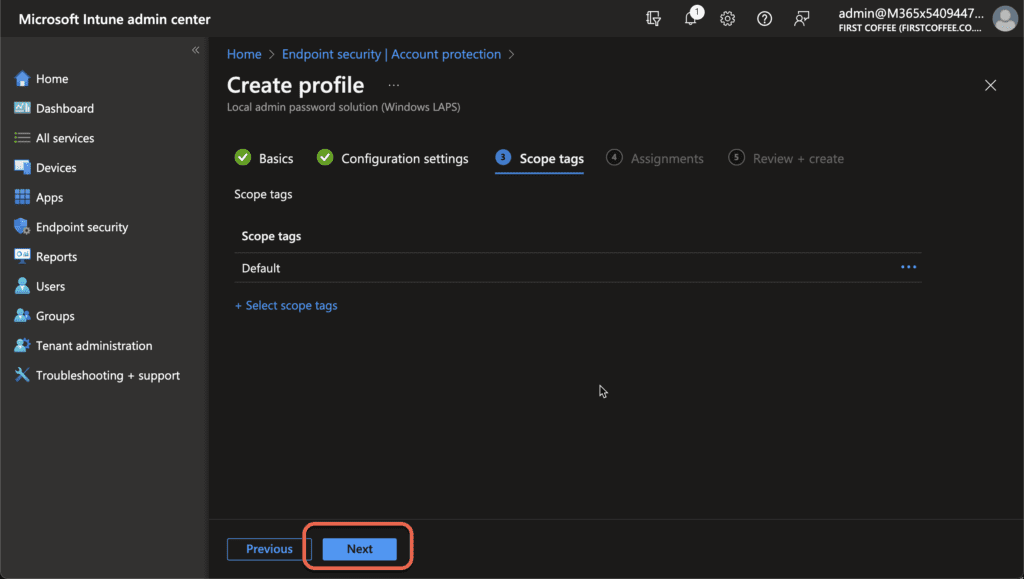
- On the Assignments page, choose the groups of users or devices to be targeted, or choose All Devices. Click Next when you’re done.
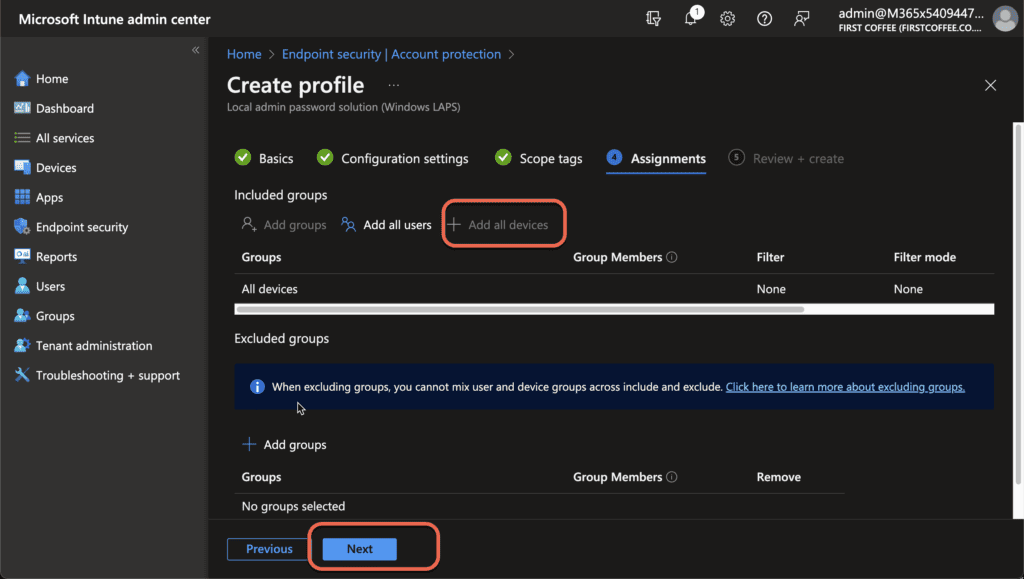
- Finally, choose Review & Create to complete the creation of your Windows LAPS profile in Intune
Manage Windows LAPS from Microsoft Entra
After creating our Windows LAPS profile in Intune, we can manage it from the Microsoft Entra profile. Here, we’ll be able to see the list of all devices that have Windows LAPS configured.
From the Microsoft Entra admin center, we’ll go back to the Devices page of the Azure AD section.
- From the Azure AD section on the left, click on All Devices.
- Next, Click on Local Administrator password recovery (Preview).
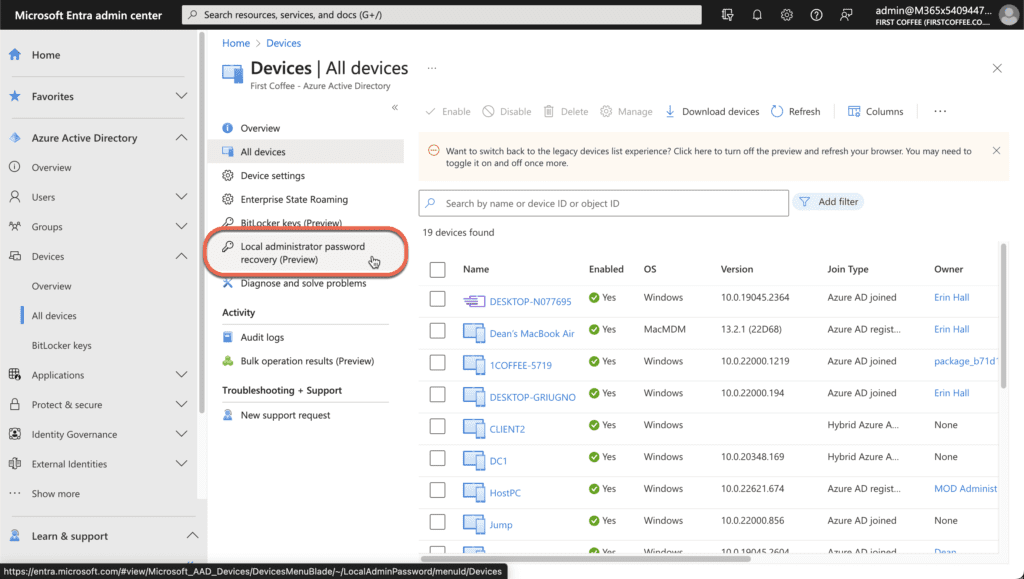
The Local Administrator password recovery (Preview) screen shows a list of all devices that have Windows LAPS configured, and it contains the following fields for each device.
- Device name: The name of the Azure AD device. This is also a link to the Azure AD device.
- Local administrator password: This field includes a link to show the local administrator password.
- Last password rotation: Date/time that the password was last changed.
- Next password rotation: Date/time that the password will be changed next.
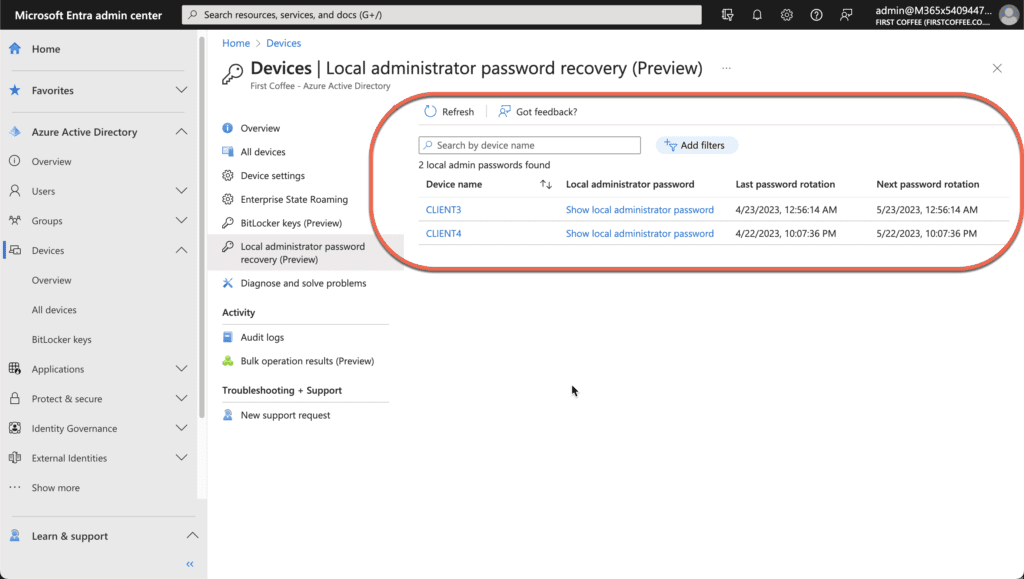
- To view a device’s local administrator password, choose Show local administrator password.
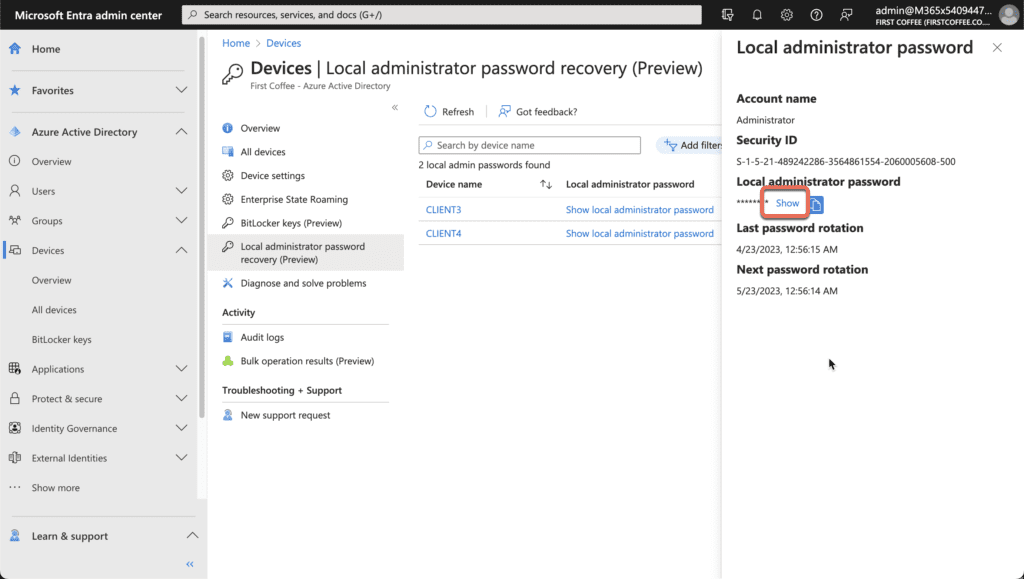
- A new pane will appear with the same details seen in the table. From here, choose Show:
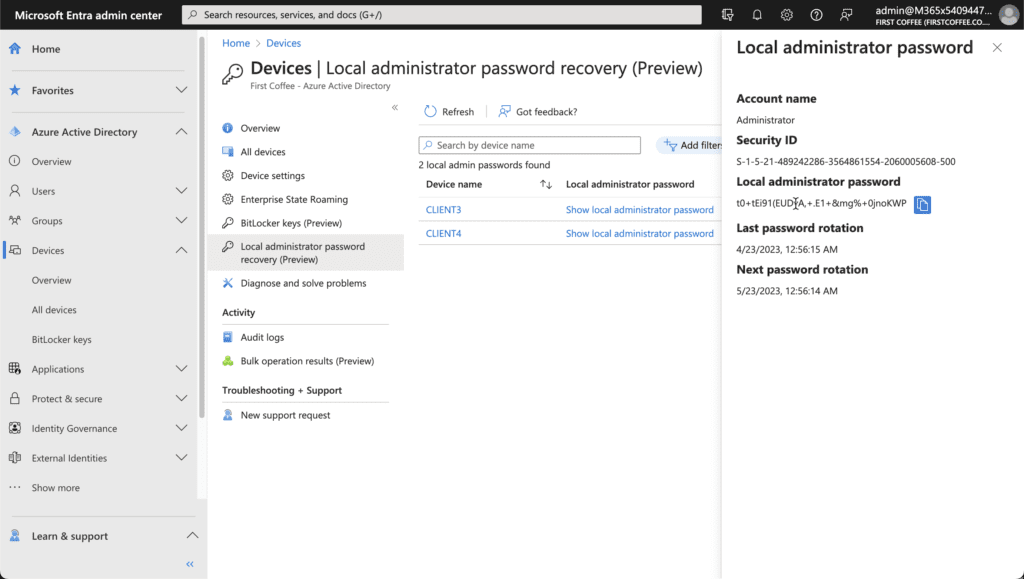
- Here, you can see the local administrator password:
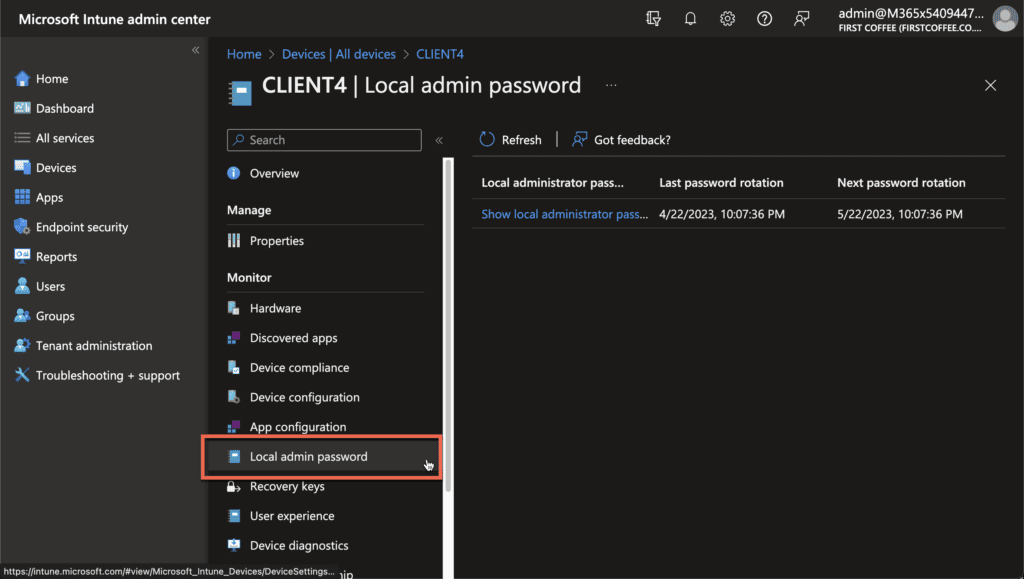
Manage Windows LAPS with Intune
While Microsoft Intune can be used for the initial configuration of Windows LAPS, it can also be leveraged to perform key actions related to Windows LAPS. For example, in the Devices blade of the Intune admin center, you can rotate the local admin password for a device that is managed by Windows LAPS.
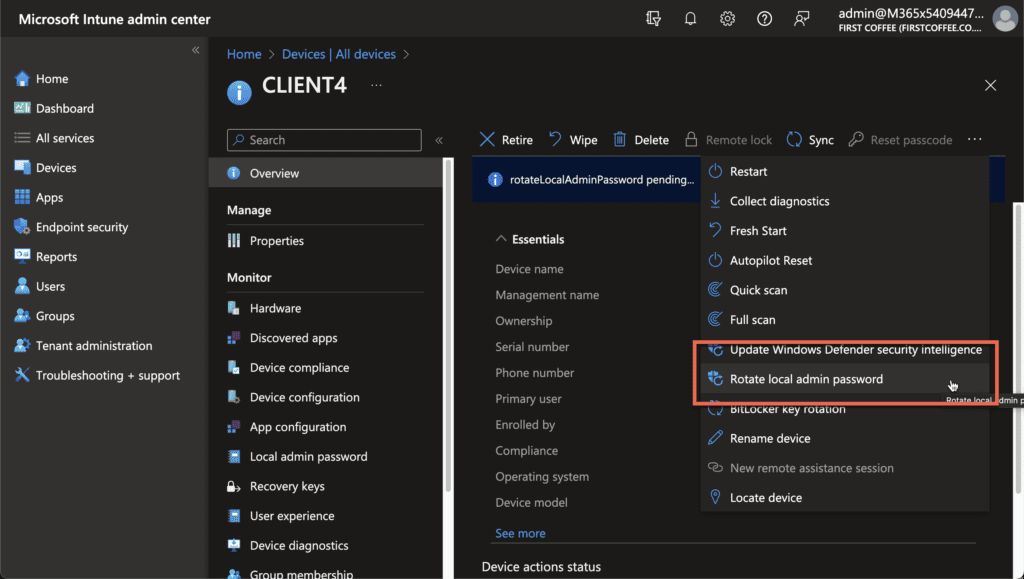
It is also possible to view the Local admin password in the Intune console, bypassing the need to use the Azure AD admin center or the Microsoft Entra admin center. To do that, you can simply choose the Local admin password in the Monitor section for the managed device:
Why you need to manage access to Windows LAPS
For a number of reasons, it’s important to strictly control access to the LAPS feature for admins in the environment. Microsoft has leveraged the native and built-in role based access control (RBAC) capabilities in Azure AD and Intune to ensure organizations can limit access to the feature.
Lastly, if you’re not ready to enable Windows LAPS in your environment yet, you can also start experimenting with it with the new emulation mode. When you’re ready to move away from the legacy Microsoft LAPS, you can choose to migrate over to the new features gradually.



