Role-Based Access Control Comes to Intune
Microsoft recently announced the addition of Role-Based Access Control (RBAC) to Intune. In this Ask the Admin, I’ll look at what is new and how RBAC can help you manage administrator access to Microsoft’s Mobile Device Management (MDM) service.
Intune is Microsoft’s popular cloud-based MDM service. Over the past 18 months, the company has been transitioning parts of the Intune infrastructure over to the Azure management portal. As part of that work, Microsoft recently added the capability to manage access to Intune using RBAC.
For more information on Microsoft Intune, read Introduction to Microsoft Intune on the Petri IT Knowledgebase.
Integrating Intune with the Azure management portal has allowed Microsoft to also provide deeper integration with Azure Active Directory (Azure AD), the cloud directory service used to manage access to born-in-the-cloud apps, Office 365, and other Microsoft services. Azure AD includes the necessary infrastructure to bring RBAC to Intune.
Intune leverages existing Azure AD Directory Roles for high-level access to the service, including Global Administrator. Company Administrator for managing everything in Intune, and Intune Service Administrator for managing Intune but without access to Azure AD.
For more granular control, Microsoft has added the following roles:
- Intune Role Administrator
- Policy and Profile Manager
- Application Manager
- Helpdesk Operator
- Read Only Operator
But that is not all. Microsoft allows you to create custom roles that include permissions for specific functions. The creation of custom roles can also be automated using the Microsoft Graph API. Managing RBAC is conceptually a little harder than just assigning users to groups. For example, for each role you need to decide which permissions will be assigned, i.e. what actions can be taken on what entities, who will be given access to the role (members), and the scope of the role (scope) or which Azure AD users and devices the role can manage.
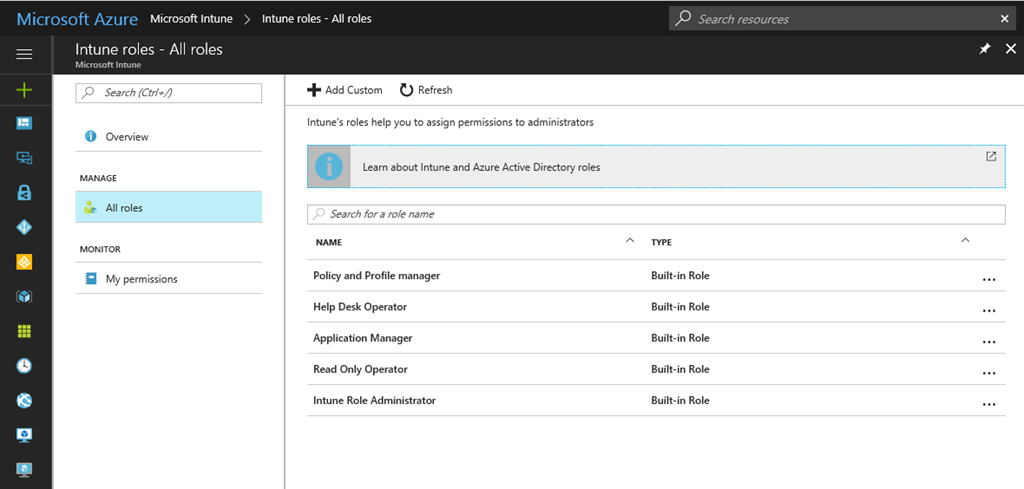
Defining the members and scope for each role is known as an assignment. Roles can have more than one assignment. RBAC provides more flexibility than group-based access control. For example, you might create a custom role that allows staff who work on the accounts helpdesk to assign applications in Intune only to employees in the accounts department.
The new RBAC controls in Intune will be familiar to System Center Configuration Manager users and offer organizations more granular control over exactly what access staff have to Intune. The new controls will allow tighter security to be implemented, ensuring that IT staff only get exactly the privileges they need. If you are currently using the groups from the classic Silverlight portal, you should look at migrating to RBAC.
For more detailed information on working with RBAC in Intune, Microsoft has a detailed post here. The post includes a matrix of all the Intune permissions that can be assigned to roles.
Follow Russell on Twitter @smithrussell.
Related Article:




