What Is Microsoft Entra ID Conditional Access? (And How To Use It)

Conditional Access is a security feature that allows organizations to control corporate resource access based on certain conditions. Common reasons for utilizing this technology include the enforcement of multifactor authentication (MFA), requiring stronger authentication measures during authentication, and more. Learn more about how to use Conditional Access to protect your data and devices.
What is Conditional Access (CA)?
Conditional Access is a core security feature of Microsoft Entra ID (formerly Azure AD). It focuses on access control for applications and identities in Microsoft’s 365 cloud services.
Think of it as a security policy engine that analyzes various signals and attributes of incoming authentication and authorization requests and enforces organizational policies to either grant access or deny access to resources based on those criteria. The scope of settings, conditions, and criteria when setting up these policies affords you the ability to craft one that meets your security and compliance needs.
Why do we need Conditional Access?
The main reason we need these policies is due to the quickly evolving security landscape and the fact that traditional access control methods are becoming less robust. The strongest case for why companies need it is the enforcement of multifactor authentication (MFA). CA adds an extra layer of protection by going beyond passwords and mitigating risks like unauthorized access or compromised devices in your organization.
Other reasons include compliance requirements, cybersecurity insurance requirements, Zero Trust security models becoming more prevalent (more on that shortly), and, on a ‘positive’ note, an enhanced end-user experience. IT Pros and admins can configure users on approved network subnets to NOT have to use MFA. A ‘trusted location’, if you will.
Conditional Access and Zero Trust
Conditional Access aligns with the core principles of Microsoft’s Zero Trust security model. The model = trust is never assumed, and every access attempt is verified.
Here are some high-level bullet points of how CA supports this evolving model.
- Dynamic access control – CA continuously evaluates access attempts based on real-time criteria. This aligns with the core tenet of continual verification in Zero Trust.
- Contextual access decisions – CA looks at various criteria beyond knowledge-based passwords, offering a more robust security approach.
- Device compliance checks – CA can block access from devices not meeting requirements. With Zero Trust, only your trusted devices can make successful logins.
- MFA enforcement – CA can enforce multifactor authentication for specific scenarios. This also aligns with Zero Trust principles.
What are Conditional Access Policies in Microsoft Entra ID?
Conditional Access policies in Microsoft Entra ID allow organizations to control access to specific applications and resources based on specific criteria surrounding the logins – device, time of day, location, etc. IT Pros and admins can create multiple policies to accommodate the nuances and unique circumstances surrounding their infrastructure, where their users log in from, and how they log in.
How do they work?
Based on established controls, policies dictate if a user is granted or blocked from accessing a specific application or service. At their core, they work like if-then statements. If a user wants to access an application like Word Online from an unknown or untrusted location, they will need to use multifactor authentication (MFA) to gain access. If perhaps they are logging in from one of your corporate offices, the MFA prompt will be deemed unnecessary.
CA signals and decisions
There are several common signals (or criteria) used with CA policies. These include:
- Device – Policies can define specific device platforms for granting access or not (e.g. laptop only, iOS, Android, etc.).
- User or group membership – You can easily target only specific users or groups for criteria. You can also require a specific condition for all users, but add some users as exceptions (e.g. break-glass accounts…)
- IP addresses, IP ranges, and location information – As I stated above, if a user is signing in from another country, MFA can be required for the user to gain access. If they are logging into their laptop in a corporate conference room, they can log in with a username and password.
- Browser- you can specify a requirement for specific browsers or up-to-date versions when validating attempts.
- Application – Varying applications and application types can be considered distinct from CA policies.
Essentially, the only decisions you consider are granting access or blocking access. There are nuances of course, but the granularity allows you to create multiple policies for applications.
For instance, when granting access, you put additional requirements on the authorization attempt – Require MFA, require authentication strength (passwords), require an approved client app, or require terms of use, among others.
Common Conditional Access policies
When you design and implement your Conditional Access strategy, you should follow some common policies. Let me give you a list.
- Require MFA for administrative/privileged accounts – this should be an absolute staple. Whenever a privileged account is logging in, require MFA, regardless of circumstances. Admin accounts are multiple times more likely to be compromised by threat actors and hackers.
- Block sign-ins for legacy authentication – If a user is attempting to log in using legacy authentication methods, disallow the sign-in.
- Require trusted locations for security information registration – when a new user is requested to set up their MFA methods, require them to perform the said procedure from a trusted location (e.g. in a corporate office, connected to a VPN from home, etc.)
- Require company-managed devices (e.g. Intune) for specific applications – If a user needs to launch a critical or confidential CRM app, or security application, require the user to log in from a company-managed device.
I want to mention a recent feature update Microsoft announced – a new re-authentication policy labeled as ‘Sign-in frequency – every time’. This allows organizations to force users to perform a new authentication each time they access specified applications and/or specific login types.
How to set up Conditional Access?
Let me give you a brief overview of how to find Conditional Access in the Microsoft Entra ID portal and the basic setup.
- First, browse to the Microsoft Entra admin center and navigate to Protection -> Conditional Access.
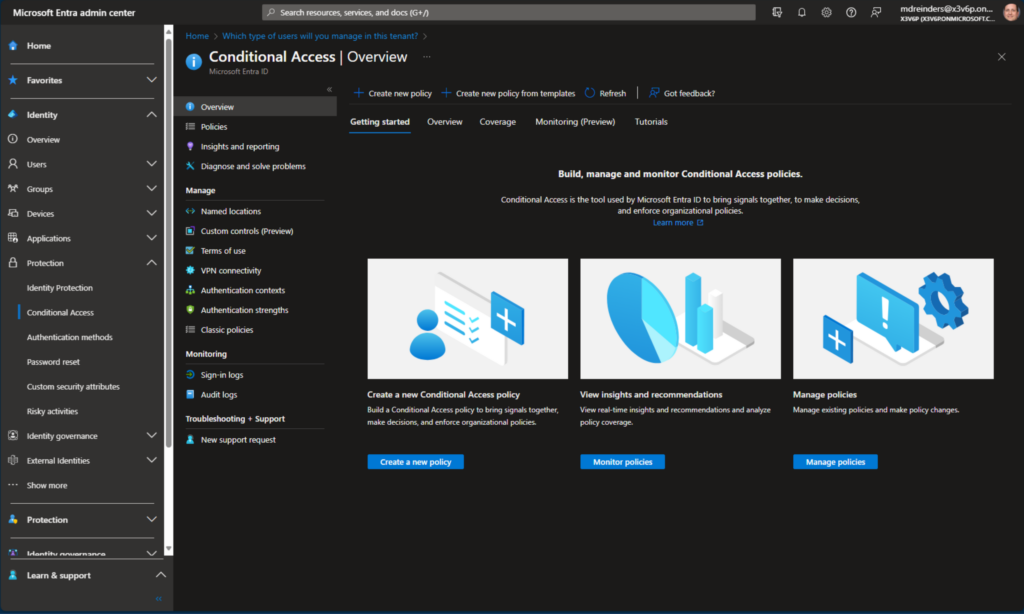
- Next, you can click on the Policies navigation link on the left.
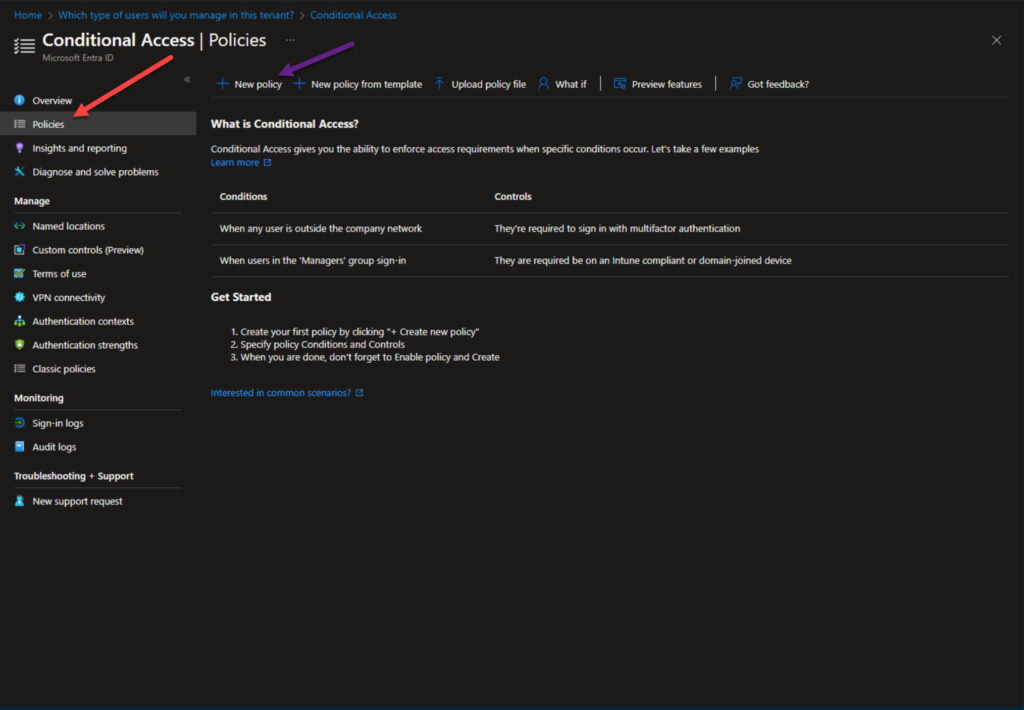
- Click the ‘+ New policy‘ link on the top and review the banner at the bottom in case this is your first time creating a policy. You may need to disable your security defaults to continue.
Want to save some time and get a headstart? You can click the ‘+ New policy from template‘ button to create policies from pre-configured templates Microsoft has graciously created for companies. Various categories of policies include Zero Trust, Remote work, Protect administrator, and Emerging threats.
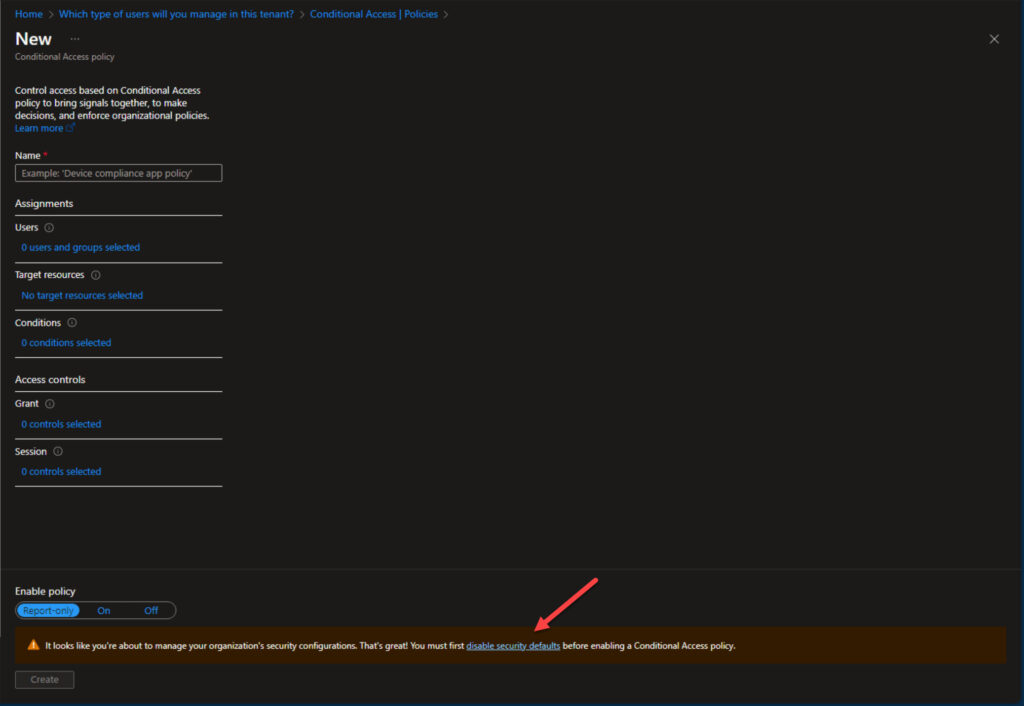
- Click on each of the remaining sections (Users, Target resources, Conditions, Access controls (Grant, block), and Session to select the appropriate controls.
I will likely create another ‘how-to’ post going into greater detail here to highlight common policies, the various configuration changes you can make, and the various controls and criteria I’ve discussed in this post to put into testing and production.
Licensing
The main licensing requirement for using Conditional Access is Microsoft Entra ID P1 licenses (or P2). Customers on Microsoft 365 Business Premium also have access to CA. If you want to use risk-based policies, you will need Identity Protection, which needs P2 licenses.
Microsoft Entra ID P1 licenses are $6/month and P2 licenses cost $9/month. You can review this Microsoft website to learn more about pricing.
One interesting note – when licenses required for Conditional Access expire, your policies aren’t disabled. Policies continue to operate, but you are unable to update any of them.
Conditional Access and Intune
Conditional Access comes into its own when used with Microsoft Intune. While the ability to control where users can log in from and the apps they use is welcome, the real power is in ensuring that devices are compliant with Intune policies.
You might not want users logging in from China if you know that’s not a location where employees are based or travel to but it’s even better if you can determine exactly which devices are being used to access corporate resources and whether they are secure. In a Bring-Your-Own-Device (BYOD) scenario, using Intune and Microsoft Entra ID Conditional Access together is the best way to secure access to your organization’s data.
Conclusion
In today’s ever-changing security and threat landscape, Conditional Access in Microsoft Entra ID stands as a very important tool for enterprises and companies of many sizes to help secure their ever-evolving work landscape. With more workers being geographically diverse and remote, it is essential to validate that your users are who they say they are. This security infrastructure, part of Microsoft’s Zero Trust security model, aims to do just that.
If you have any questions or comments, please feel free to leave a comment below. Thank you for reading.
Related Article:



