Microsoft Releases New Conditional Access Policy to Require Reauthentications

Key Takeaways:
- Microsoft has introduced a new reauthentication policy called “sign-in frequency – every time” for Entra Conditional Access.
- The new policy requires users to perform a fresh authentication before accessing corporate resources.
- Microsoft has highlighted various scenarios necessitating interactive reauthentication, including accessing high-risk resources through a VPN.
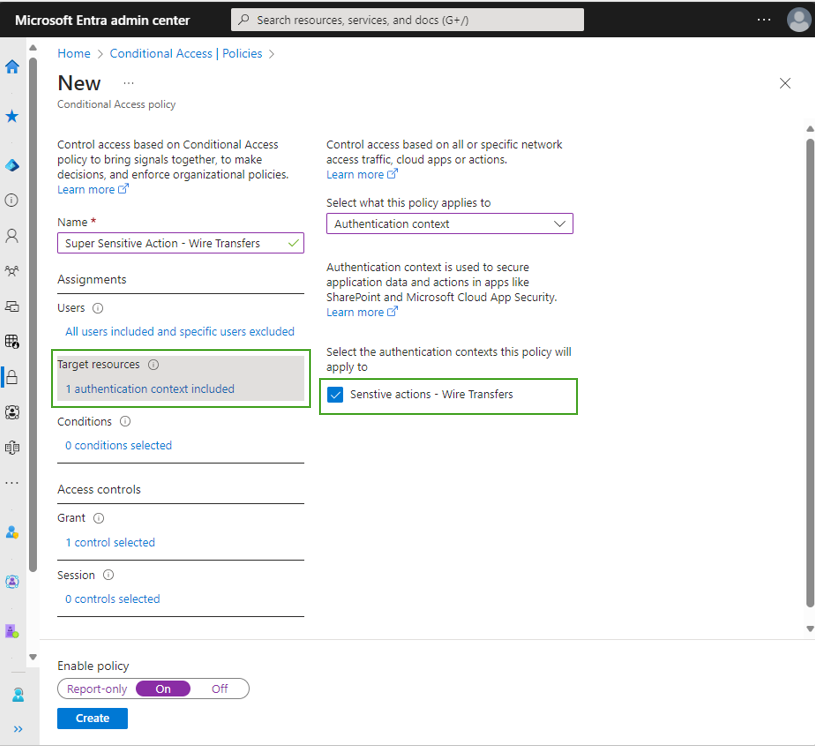
Microsoft has announced a new reauthentication policy for its Microsoft Entra Conditional Access service. The new “sign-in frequency – every time” policy allows organizations to require users to perform a fresh authentication each time they access critical applications or perform sensitive actions.
Single sign-on is an authentication method that lets users access multiple applications or services with a single set of credentials. It requires users to authenticate once and access all authorized resources without needing to re-authenticate. Single sign-on is designed to enhance security by reducing the risk of credential reuse.
The “sign-in frequency – every time” policy is tailored for organizations using single sign-on (SSO) yet desiring occasional reauthentication prompts for users accessing corporate resources. For instance, IT administrators can configure risk-based reauthentication policies to address suspicious sign-in activities, mitigating token theft risks in enterprise environments.
What are the other scenarios where interactive reauthentication is necessary?
Microsoft detailed the following scenarios where administrators might want to require a fresh authentication:
- Accessing high-risk resources behind a VPN.
- Performing sensitive actions such as updating credentials and Microsoft Intune enrollment
- Privileged role elevation in Privileged Identity Management (PIM).
- Signing into Azure Virtual Desktop machines.
Microsoft advises that the “sign-in frequency – every time” policy shouldn’t be used with all applications because it could cause multifactor authentication (MFA) fatigue. The company recommends using time-based user sign-in frequency to protect Microsoft 365 apps.
“Triggering reauthentication too frequently can increase security friction to a point that it causes users to experience MFA fatigue and open the door to phishing attempts. Web applications usually provide a less disruptive experience than their desktop counterparts when require reauthentication every time is enabled,” Microsoft explained.
In case you missed it, Microsoft has recently introduced a new “Utilization and Insights” portal for Entra ID Premium customers. The portal allows administrators to monitor the number of Entra ID P1 and P2 licenses, along with their features. Microsoft plans to add support for more SKUs and corresponding features at general availability.



