How to Properly Secure and Govern Microsoft Entra ID Apps

Microsoft Entra ID, formerly Azure Active Directory (AD), is Microsoft’s cloud-native identity management platform. It only takes one compromised Entra ID user account to consent to a rogue app that siphons all the user’s Microsoft 365 data or to take over their mailbox. Business Email Compromise (BEC) amounts to $8 million in losses on a daily basis globally.
This article is sponsored by ENow Software.
In this article, Sander Berkouwer – a Microsoft security MVP and long-time identity management expert – explains how misconfigured Entra ID application registrations and enterprise apps can lead to data compromise, and then 3 questions you need to answer to detect and remediate incorrectly configured Entra ID apps.
Microsoft Entra ID: establishing an app governance strategy
Microsoft Entra ID is an industry-leading identity management platform for authenticating and authorizing access to applications and resources. But it requires adequate oversight to ensure that your organization stays secure.
One challenge I commonly see organizations struggle to address is implementing an effective application governance strategy. Whether internal developers are creating applications or employees are purchasing 3rd party Shadow IT solutions, many organizations are continuously – and unknowingly! – integrating these apps into Entra ID.
However, admins must to be able to say with confidence that you have a solid grip on the applications your organization uses in the cloud. You need to know what applications users have deployed inside your tenant, and be able to provide the organization with a list of admin-approved applications.
While this may seem cumbersome, there is a very clear, easy path for remediation and discovery of potential application-related security challenges in Entra ID. But first, we must ensure there is full understanding of our Entra ID application estate.
Understanding your current Entra ID application estate
Entra ID is the directory and identity management service that offers authentication and authorization services to various Microsoft services like Azure, Microsoft 365, and other cloud applications. Getting started, there are two important questions you will need to answer.
1. Have I minimized potential attack patterns by correctly configuring the settings for applications installed in my tenant?
Before you can properly secure access to apps and data, you need to understand conceptually how Entra ID differs from Windows Server Active Directory, app registrations, enterprise apps, and consent. For instance, user consented apps have different API permissions than admin consented apps.
User consent merely grants permission to the application, service and/or system for the scope of the consenting user. Common supply attack patterns include targeting vendors of multitenant apps to syphon data from organizations at scale with unprecedented impact, as the SolarWinds hack indicated. When admin consent is provided, the application, service, and/or system is available to everyone in the organizations and permissions can be consented to beyond the scope of one user.
If you are unclear about any of these fundamentals, it is important you first read this primer on Entra ID application registration and enterprise apps on Petri.com.
2. Have I adequately strengthened my organizations security posture by locking down access to admin-consented apps?
It’s important to understand your role as an admin, and how it pertains to properly securing and governing Microsoft Entra ID applications. Have you ever wondered how many app registrations have an expired certificate or secret? Or will be expiring in the next two weeks? What about the number of enterprise applications that are highly privileged or the percentage that was configured without admin consent?
I have, and you should be asking yourself the same questions. Microsoft’s free native tools and the Entra ID portal did not provide me with any clear, immediate answers, so I turned to a third-party solution.
Introducing the ENow AppGov Score and Solution
ENow AppGov Score is a free assessment tool that quantifies your application governance state. The scoring system takes into account Microsoft recommended identity best practices and the input of very experienced Microsoft security MVPs, including myself. The assessment includes over 24 checks that cover enterprise applications, app registrations, and tenant settings.
ENow AppGov Score was created as a free security assessment tool because ENow’s clients requested help solving the challenges associated with implementing an application governance process.
“We quickly realized that application governance was a huge blind spot for most organizations and that since it was such a common problem, we wanted to provide a free tool that would help organizations better understand their current state” -Jay Gundotra, CEO and technical founder of ENow.
The company’s long 19-year history of assisting organizations across the globe simplify complex monitoring scenarios with Microsoft unified collaboration tools and Active Directory has helped them make a difficult problem like implementing an application governance strategy easy and clear.
The ENow AppGov Score assessment tool is an enterprise app that can be quickly used by anyone that has the Entra ID admin rights to consent to the permissions it requests. You will need to approve the application with the following API permissions:
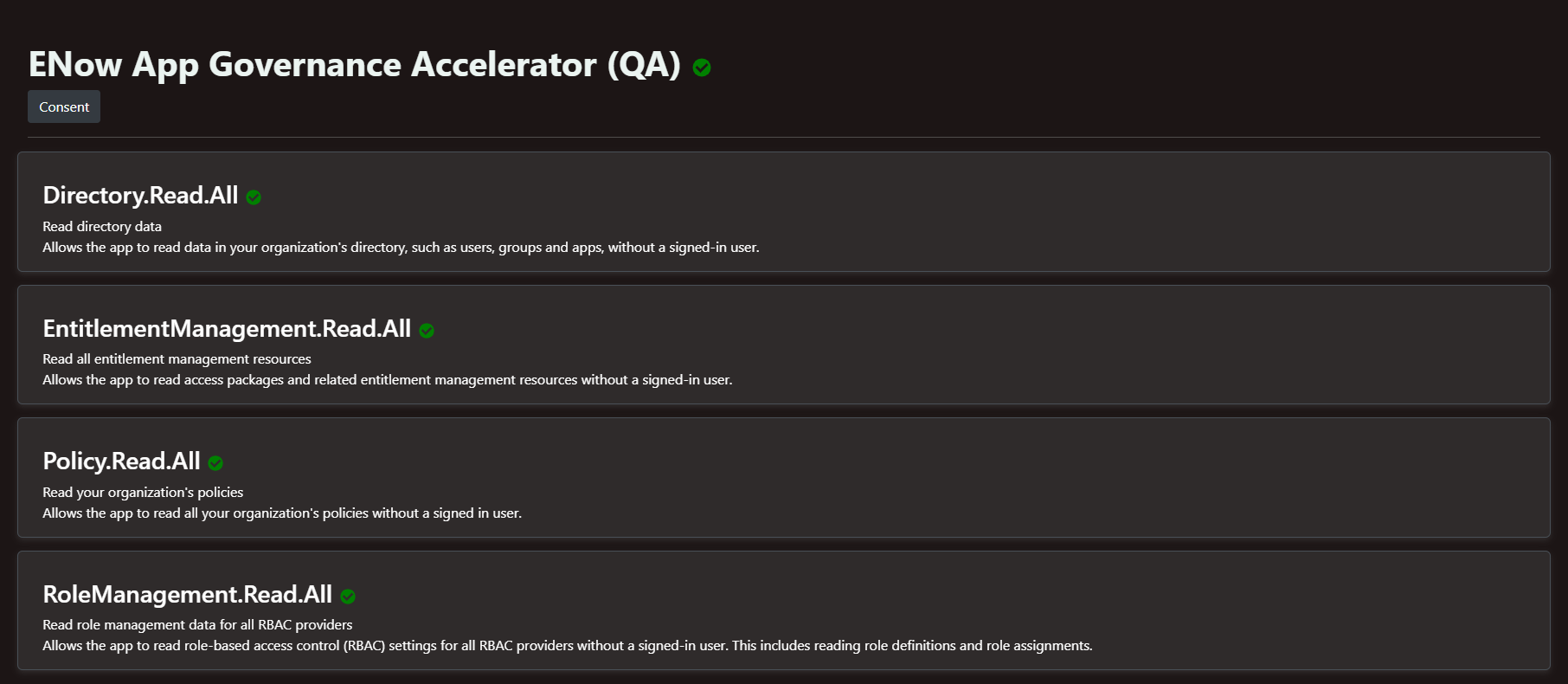
Once you consent, you will receive an email when your AppGov Score assessment report is available. For smaller organizations, the report generates in a few minutes. For larger organizations, it can take up to an hour. Once you have the report, I recommend that you review it to understand the areas that need to be addressed immediately.
The Application Governance Score (AppGov)
The central component of the Application Governance Assessment Report is the ENow Application Governance Score, or AppGov Score for short. In a glance, admins can quickly see the state of their tenant from an application point of view:

Based on the three pillars of the ENow solution, the AppGov score report provides information on the state of:
- Enterprise applications
- App registrations
- Tenant settings
The ENow Application Governance Assessment Report runs over 24 different checks against your tenant and then gives you a quantifiable AppGov score.
I ran the AppGov assessment tool for a company I was helping. The report quickly gave me some great insights. This organization had not implemented a proper application governance policy.
Enterprise applications
The first section of the report analyzed all the enterprise applications. It quickly revealed that this tenant had 219 Enterprise Applications (in addition to the Microsoft built-in ones), and that 34% of the enterprise applications were created without admin consent. It also showed that 95% of the enterprise applications have no role assignments (Oops!). I also learned that 23 enterprise applications were considered high risk or had an elevated set of permissions.
Application registrations
The next section of the report analyzed all the application registrations in the tenant. The security assessment tool runs 10 different checks for this area. It revealed that the tenant had 40 applications with public client flows. If you do not know what a test does or why it matters, there is a helpful description located directly below the text.
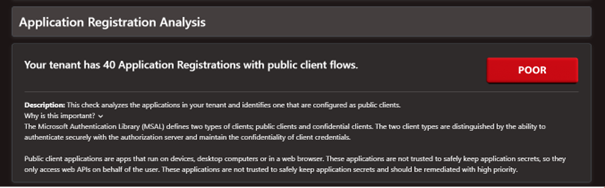
The report also highlighted how many app registrations had expired certificates or client secrets. It showed that several application certificates expire in the next 14 days and several have expiration dates greater than 2 years. The helper text pointed out that Microsoft recommends a validity period of 2 years or less since certificates enable application registrations to identify themselves to Microsoft Entra ID.
With sufficient network packets monitored, an adversary could successfully launch a collision attack. The longer a certificate is valid, the more opportunity an adversary has to successfully perform this type of attack and abuse the certificate for a longer period.
Tenant settings
The final section of the report analyzes the tenant-wide settings and compares them to Microsoft recommended practices. The tool runs 6 different checks for this area. I was able to see that this organization had 13 accounts with application administrative privileges.
The tenant was configured to allow group owners consent and we were given a poor rating for this test. The helper text pointed out that the configuration would make it harder to achieve an effective application governance policy. A better configuration would not allow groups owner consent. This tenant was also given a poor rating because the tenant was configured to allow user consent for apps.
The Tenant Settings Analysis section of the score report provides meaningful information to correctly configure tenant settings. It tells you how you have configured your settings and provides a score for each setting. By changing these settings first, you prevent a situation where you are proverbially mopping the floor with the faucet still running.
Technically, changing these settings isn’t hard but it may require some Entra ID knowledge, communications, and additional processes in your organization.
It seems I have some work to do on this tenant, but the 57% AppGov score also represents a true picture of the tenant I was running the assessment against when compared to Microsoft recommended practices. The best was that I was able to save hours of work manually searching for this information. And now I can invest that time to improve the tenant’s cloud security posture.
Getting Started
As a Dutchman, I’m pleased there is a freemium version of the solution. (We Dutch like free!) Especially as the freemium version provides the information we need in the discovery phase to quickly understand the state of the tenant. It answers the majority of the key questions I noted earlier in this article.
There is one small catch; it does not provide the names of the offending applications. The Application Governance Assessment Report does help organizations learn the size of the challenge in their Entra ID tenant, what to look for, and why it is important. This is a perfect inventory step.
Beyond the AppGov Score: How to Inventory, Remediate and Govern
The fully licensed version, called App Governance Accelerator, provides the data behind each check, in the form of interactive dashboards. It also includes numerous reports that allow admins to evaluate each potential misconfiguration or abused application so they can prevent and remediate security-related problems in their Entra ID tenants.
Another helpful feature is that it tracks your progress and makes recommendations so that you can improve or implement your application governance policy quicker.
The fully licensed version also provides tailor-made reports and graphs to dig through the information initially surfaced in the score report. This allows you to inventory, remediate, and ultimately govern.
Digging into the reports to see what’s going on
From an inventory point of view, in the Activity section, the Sign-ins and platforms report immediately tells me what enterprise applications in the Entra ID tenant are most heavily used sorting by Sign-In Count (desc):
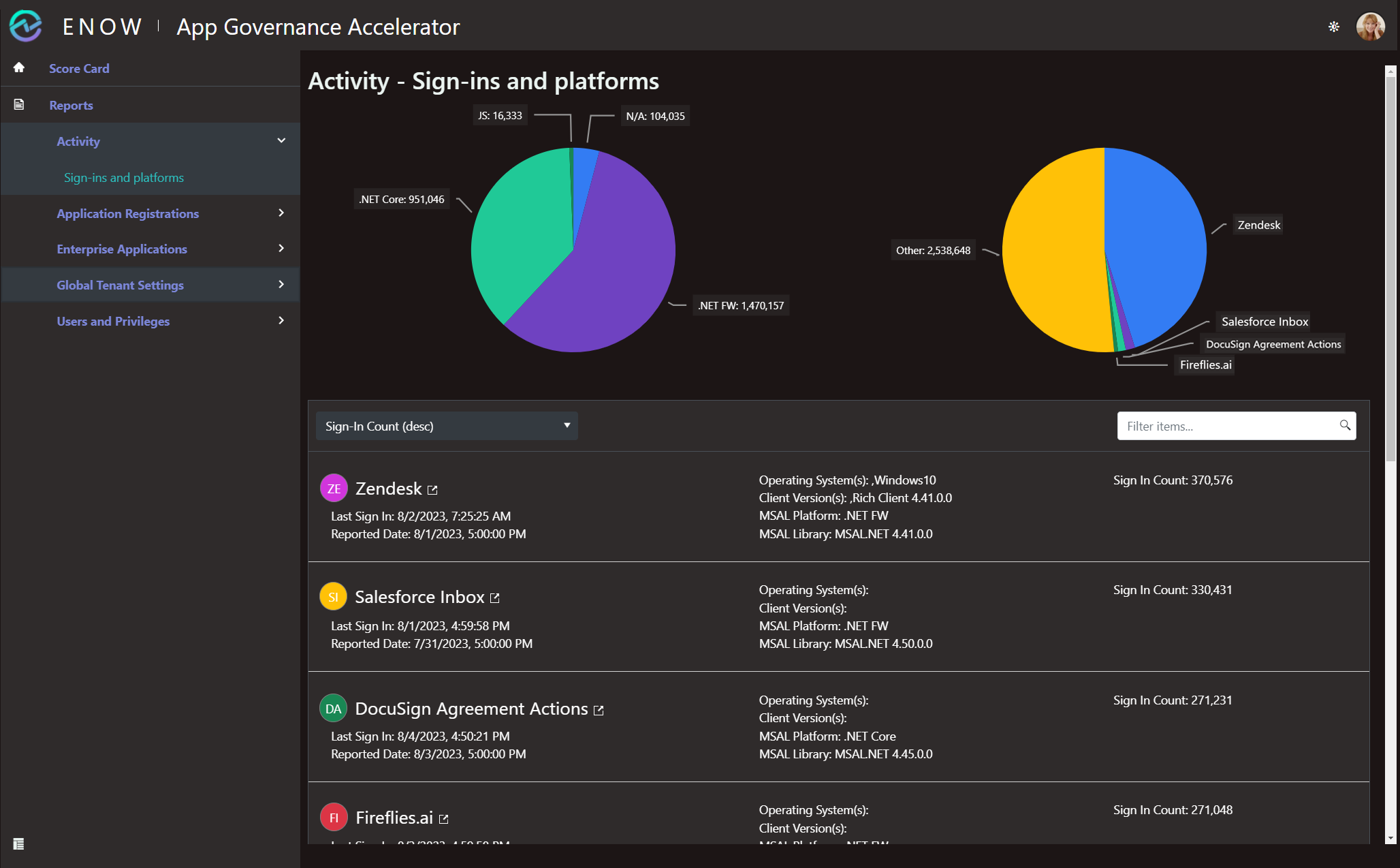
Together with the Change log and Creation log reports in the Enterprise Applications section, and the Created in the last 30 days report in the Application Registrations section, it provides a quick overview of what is happening in the tenant from an application point of view.
Detecting vulnerable apps
Looking at the Sign-ins and platforms report, I notice that several enterprise applications are developed with different library versions of the Microsoft Authentication Libraries (MSAL). To perform an inventory like this, go to the Enterprise Application section and open the Expired Authentication Libraries report:
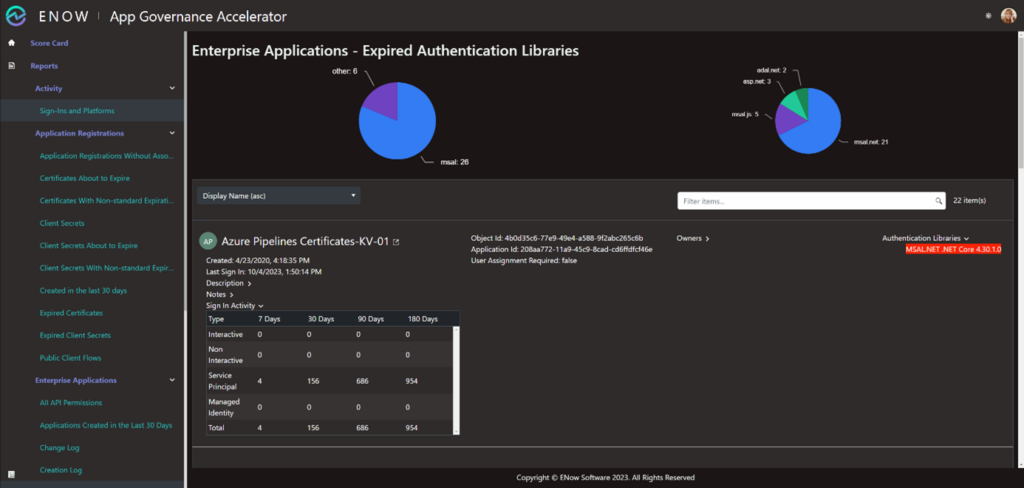
Here, I see that 19 applications, services and/or systems use outdated versions of MSAL and 6 applications, services and/or systems handle authentication with libraries that are not authored by Microsoft or have been altered not to provide this information in the Entra ID logs.
Now, I can work with vendors and/or developers to have the latest stable version of the authentication libraries implemented in their solutions. That way, I benefit from the changes in the libraries that Microsoft made after performing penetration tests and fixing breaches.
This is not fiction. Microsoft’s most recent MSAL update was the result of major technical investigations for Storm-0558’s signing key acquisition. It may also introduce new features to the applications, services and/or systems the organization uses, like Continuous Access Evaluation.
Remediating public client flows
I’m still bugged by application registrations with public client flows, though… According to the Application Governance Assessment Report, these applications are not trusted to safely keep application secrets and should be remediated with high priority.
If I wanted to know more about the public client flows, I could use the Public Client Flows report in the Application Registrations section:
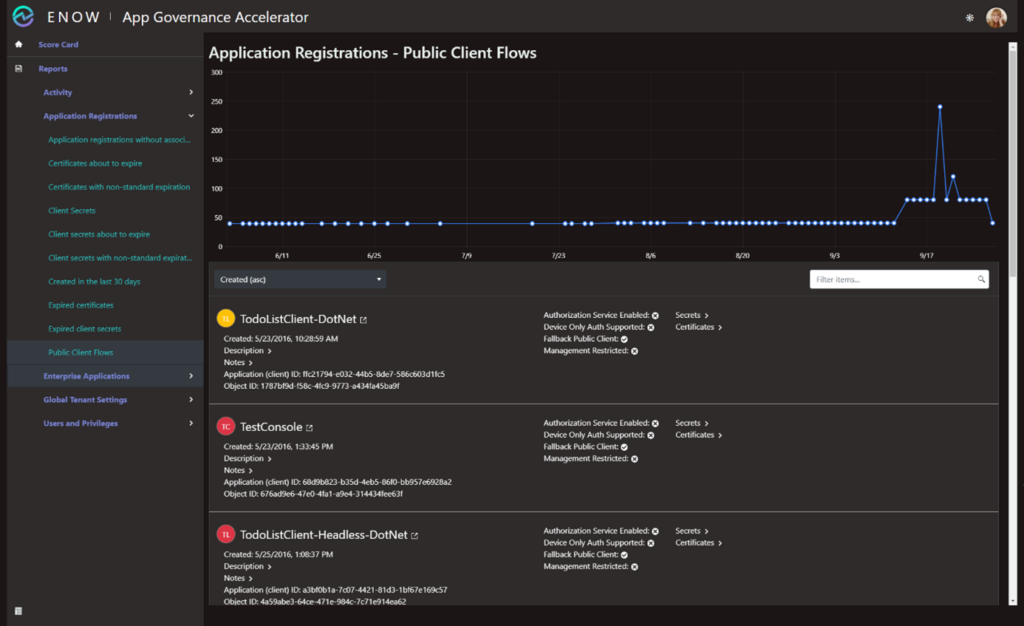
The report provides me with the information I need. Again, I can work with vendors and/or developers to get the configuration remediated. If that is not possible, at least I know I need to keep a close eye on these app registrations and their associated enterprise applications in my logs.
Creating an overview of app administrative privileges
I guess we all know that accounts with global administrator privileges can manage all aspects of the organization’s Entra ID tenant. When it comes to enterprise applications and app registrations, a lot more people can have administrative privileges, as do some accounts that you might not expect.
The Accounts with administrative application privileges report in the Users and Privileges section provides an overview:
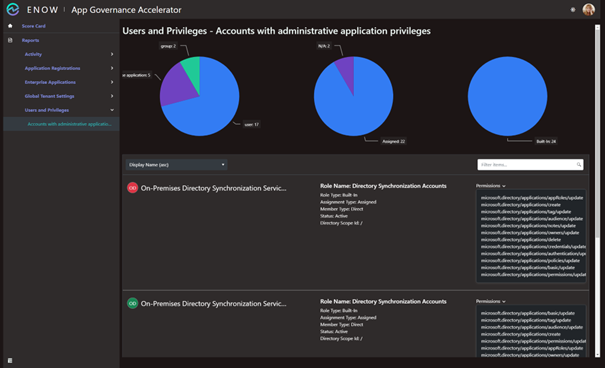
This report provides information on built-in roles, like Global Administrator and Application Administrator, but also any custom roles admins may have created, including the actual scope and directory permissions.
Evaluating all options
ENow’s App Governance Accelerator solution provides the AppGov Score at a glance, accompanied by tailor-made reports to really dig deep and remediate problems with applications in Entra ID.
Microsoft’s Application Governance solution also works with Entra ID apps but it is different. It provides an enormous amount of information and requires much deeper knowledge of Entra ID identity principles.
Microsoft’s solution, labeled App Governance, is more integrated into Defender for Cloud Apps and therefore provides deeper insights into permission and data usage. However, full functionality requires a Microsoft 365 E5 license for every user and a Workload Identity Premium license for every application registration in the tenant. Lastly, the Microsoft solution is limited to O-Auth based applications.
ENow’s Application Governance Assessment Report offers free information for the discovery phase of your Entra ID application governance journey. It already allows you to prevent future application abuse.
The full license provides all the knowledge you need to quickly implement an application governance policy and to monitor app compliance. ENow improves its Entra ID Application Governance Assessment solution on a regular basis to include more expert insights, community feedback, and workflows. So, expect more exciting features to help tackle security challenges posed through Entra ID applications.
Share your free AppGov Score in the comments below!



