What is Azure AD B2C?

Azure Active Directory (Azure AD) B2C is a cloud-based customer identity and access management service that provides business-to-customer (B2C) Identity-as-a-Service. It allows organizations to secure and manage their customer-facing applications – so external parties can seamlessly sign up and log in. Learn more about the features and benefits of Azure AD B2C below.
What is Azure AD B2C?
Azure AD B2C is a Customer Identity Access Management (CIAM) offering from Microsoft that is based on Azure Active Directory (now Microsoft Entra ID). The solution provides business-to-consumer Identity-as-a-Service. It lets your customers use their preferred identities to get single sign-on (SSO) access to your tenant and applications with appropriate permissions. You can set up and maintain this access easily in the Azure Portal.
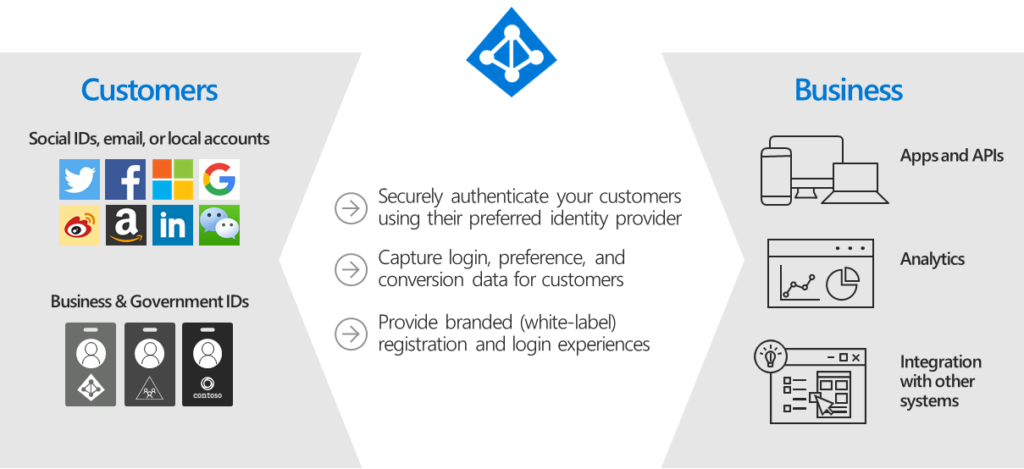
Because Azure AD B2C is a Platform-as-a-Service (PaaS), Microsoft takes care of supporting millions of users and billions of authentications per day offering stability, monitoring, and security peace of mind.
Azure AD B2C features and benefits
Azure AD B2C provides many features and benefits for your organization when managing the identities and access of your external users, specifically consumers, partners, and others who interact with your web-based applications.
Azure AD B2C features
Here are some highlights of Azure AD B2C:
- Flexible authentication protocols: You can support a diverse myriad of authentication methods like OAuth, OpenID Connect, SAML, and other authentication protocols for a seamless customer experience.
- Fine-grained access control: Implement access control policies based on user attributes, context, and device attributes for enhanced security and compliance regulatory needs.
- Customizable sign-in and sign-up flows: You have full control to design engaging user workflows with branded login pages, self-service password resets courtesy of Microsoft Entra ID (previously Azure AD), and social login options with several identity providers.
- API integration: Integrate Azure AD B2C with your current applications and services through RESTful APIs and other development tools like Visual Studio.
Benefits of Azure AD B2C
Here are some benefits of Azure AD B2C:
- Reduced operational costs: Remove the need for managing an on-premises infrastructure and gain a pay-as-you-go pricing model.
- Improved user experience: Convenient SSO and secure sign-ins for external users, making onboarding to your application solution easy.
- Enhanced security: Implement identity protection and robust access controls to safeguard and protect your applications, IP, and other data from unauthorized access or breaches.
Who is Azure AD B2C designed for?
Let me explain three groups or use cases that are a good match for what Microsoft Entra B2C is designed for.
- (Business) partners: Organizations collaborating with external partners can include vendor portals, supply chain management, and other frontline worker scenarios or environments.
- Consumers: Companies offering online services to individuals include financial services apps (Bank of America, Chase, etc.), educational platforms, and healthcare portals.
- Citizens: Public institutions offering online resources like libraries, community sites, and other educational institutions.
I will go into an example in a little while.
What are App Registrations in Azure AD B2C and how do they work?
When you create a customer-facing connection with Azure AD B2C, you are creating an Azure AD app registration. This is done with the power of Microsoft Graph and it holds all the permissions that your app has in your organization.
After your new app registration is created and securely configured, your application will automatically have appropriate access to your user accounts. The granular list of permissions is extensive. Typical permissions in these types of use cases would be things like ‘Directory.Read.All’ – this allows your application to read all directory information, such as users and their contact information.
Azure AD access tokens
Curious about how a customer logs in and what happens behind the scenes? Let me give you a brief overview.
- Client application
- Initiates login/authorization request to the Azure AD login page.
- The user authenticates and an authorization code is received and sent back to the originating application/website portal.
- Application Endpoint
- The application sends the auth code, client ID, client secret, and resources to Azure AD.
- Azure AD validates all the information and the access token is issued.
- Client application
- The application uses the token to access the protected resources.
- The resource server validates the token and grants appropriate access and permissions.
When a user logs in for the first time with Azure AD B2C, an access token is given to the user. These are used to authenticate the user and provide protected resources to them. These are typically soon-to-expire tokens for security reasons. They are issued by Azure AD and contain information about the user and their granted permissions.
Microsoft Entra External ID vs Azure AD B2C
Microsoft Entra External ID is a future replacement CIAM that Microsoft is currently working on. It went into preview at Microsoft Ignite 2023. Microsoft Entra External ID isn’t a new name for Azure AD B2C. Azure AD B2C continues to be the current CIAM offering from Microsoft.
Use cases for Azure AD B2C
Let me provide a hypothetical example of how an organization could benefit from Azure AD B2C.
Let’s talk about MileHigh Adventures. They are not your average travel agency. They offer breathtaking travel and experience packages, from scaling Mount Everest and trekking through the Amazon rainforests.
However, managing the logistics and bookings for these adventurous trips presented a challenge. MileHigh’s website was based on outdated technology, lacking secure sign-ins and an efficient customer access solution. In addition, customers were faced with complex identity experience scenarios. Then, MileHigh discovered Azure AD B2C.
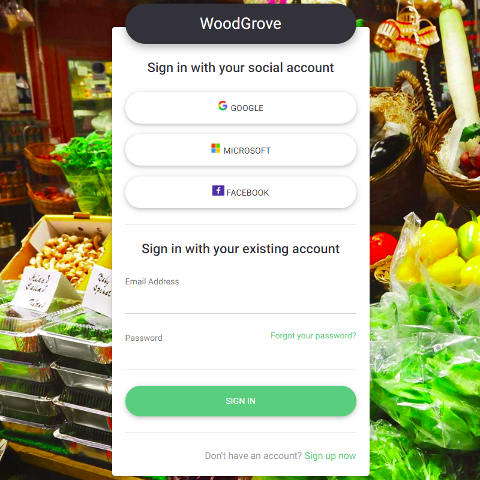
They transitioned their sign-in page to include SSO functionality with Azure AD, thereby giving their customers the ability to use their favorite social media credentials to log in to MileHigh’s website.
MileHigh’s transformation consisted of the benefits I’ve mentioned including:
- Enhanced security: Azure AD’s multifactor authentication (MFA) and fraud detection validate secure transactions with customer data and logins.
- Seamless sign-Ins: SSO replaces the clunky login process with a modern, branded interface. Customers can now sign up for their bookings using their preferred social media accounts like Google and LinkedIn.
- Personalized journeys: MileHigh was able to use Azure AD B2C’s user attributes to personalize their email communications and tailored recommendations for each (external) customer.
Seamless identity management for your customers
I’ve explained how seamless sign-in and single sign-on (SSO) benefits your external parties, customers, and guests.
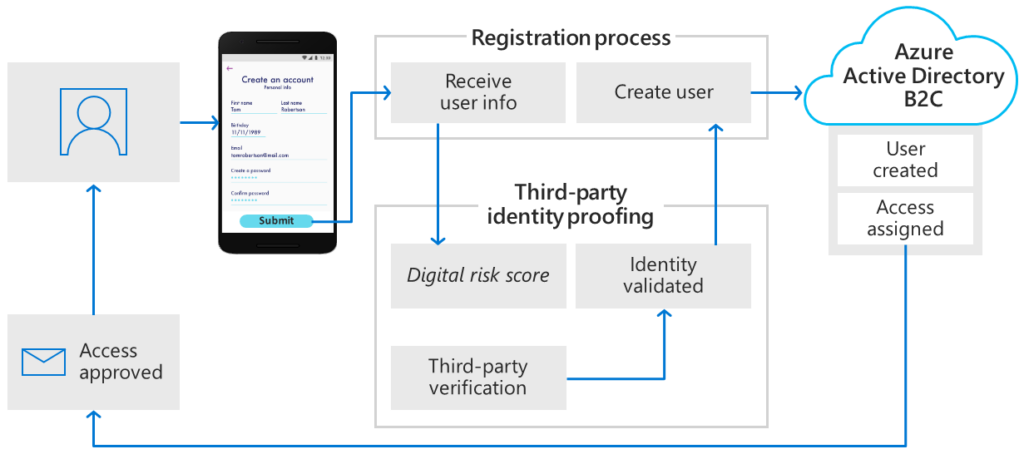
Jim, a MileHigh customer for many years, was frustrated with how long it took him to book and plan his adventures on their antiquated website. After MileHigh integrated Azure AD B2C, he was able to easily use his Facebook account and link it with the SSO setup for MileHigh’s new website. What took him hours in the past can now be completed, with ease, in minutes.
Can my customers use single sign-on (SSO) to access my apps?
Yes, this is one of the biggest benefits and productivity gains for your user journeys towards a more seamless sign-in experience. Jim, on the day of his recent trek to Machu Picchu, was able to use his pre-registered passport details to expedite his customs process and sign in with his Facebook account to confirm his trek itinerary.
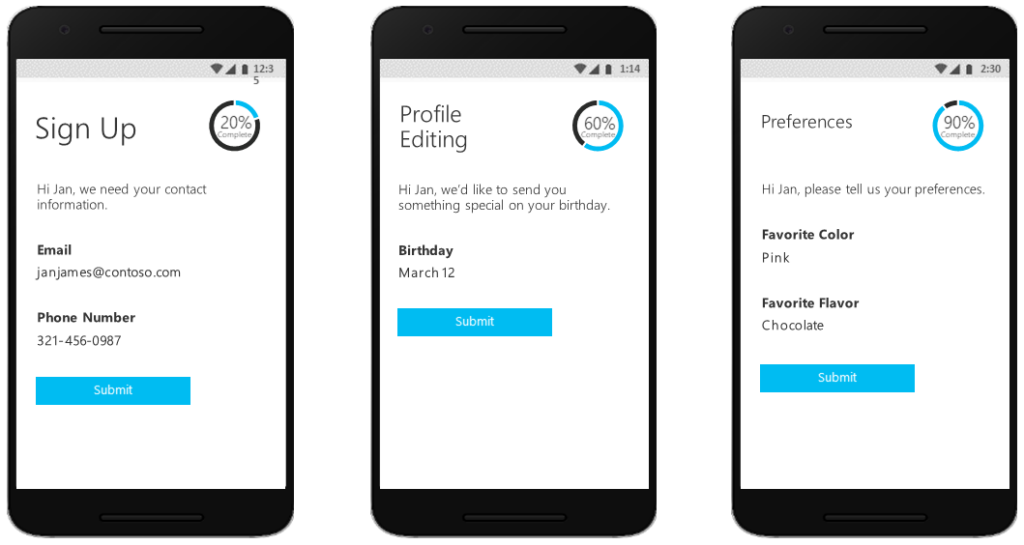
Throughout his adventure, MileHigh guides used mobile apps linked to Azure AD B2C to track his group’s progress and ensure everyone’s safety. After he returned home, he used SSO to again sign in to his MileHigh site to upload pictures and share his experience with fellow travelers.
Best practices for managing Azure AD B2C
As with any aspect of managing the safety of your company’s data, there are best practices involved with making sure Azure AD B2C is implemented safely, and securely. Let me first discuss the ‘end-user’ impacts. I’ll then discuss security.
From a user experience perspective, make sure you support multiple authentication methods. Offer the most prominent social login options, password-based logins, and other popular methods to cater to a diverse user base and customer base. Design an intuitive user flow – user-friendly sign-in and self-service password reset options are paramount to maintaining your customer’s loyalty and positive experiences.
Azure AD B2C security considerations
There are a good number of security and compliance measures you need to take into account. Let me list them here.
- Maintain data residency compliance: Choose the appropriate data storage region to maintain data privacy and HIPAA regulations.
- Enable MFA – Integrating multifactor authentication should be an absolute requirement. You don’t want any security breaches from easily preventable ingresses to jeopardize your livelihood.
- Implement strong password policies: Enforce a 25-character minimum password length and require complex passwords.
- Monitor user activity: Be sure to keep tabs on your Azure Sign-In logs. You may also want to purchase additional monitoring items like Azure Monitor or Microsoft Sentinel to let Microsoft take care of notifying you of any suspicious activity.
SSO, MFA, and built-in auditing for safe and seamless external user identity management
Utilizing Microsoft Entra B2C is generally straightforward. Determining your needs, verifying your prerequisites are in place, and designing a robust but efficient end-user experience for your customers are crucial. Azure AD B2C is designed to help businesses manage customer identities and access their applications in a secure and scalable way. With SSO, MFA, and auditing built-in, you can ensure your customers a safe and seamless process of logging into your company’s website portal.
Please leave a comment or question below and thank you for reading.



