
Microsoft Sentinel, which was previously known as Azure Sentinel, is a Security Information and Event Management (SIEM) solution for Azure and Microsoft 365. Just like other SIEM solutions, it combines Security Information Management (SIM) and Security Event Management (SEM). In this article, we’re going to explain how Microsoft Sentinel works and how this solution can help organizations to protect their cloud and on-premises resources.
What is Microsoft Sentinel?
There are several great SIEM solutions available on the market, but Microsoft Sentinel is one that stands out when we talk about cloud computing. Microsoft Sentinel was originally launched as Azure Sentinel back in 2019, and at the time the focus was clearly on Azure services. However, as Microsoft started building a multi-cloud strategy and introduced connectors to other cloud vendors, the platform was rebranded to Microsoft Sentinel.
As of today, Microsoft Sentinel allows organizations to collect event logs from different systems and analyze them to identify evolving threats. Microsoft Sentinel also leverages behavioral analytics and machine learning to improve the detection of evolving threats.
What are the main features of Microsoft Sentinel?
There are six requirements SIEM solutions must satisfy:
- Data aggregation
- Dashboards
- Alerts
- Correlation
- Retention
- Forensics analysis
Let’s take a closer look at these requirements for SIEM solutions and see how Microsoft Sentinel implements them.
Data aggregation
Data aggregation is the process of collecting data from multiple sources at a time. Almost 100 data connectors are available with Microsoft Sentinel, allowing organizations to easily ingest data from almost anywhere.
Microsoft Sentinel offers connectors for other cloud platforms such as Amazon Web Services (AWS) and Google Cloud Platform (GCP). You can connect Microsoft Sentinel to on-premises resources as well.
Dashboards
The data ingested by Microsoft Sentinel is stored in Log Analytics, which allows logs to be sorted, filtered, and analyzed. Kusto Query Language (KQL) is used to query data with over 100 workbooks that are available out of the box.
The solution allows organizations to build dashboards and create data visualizations. Dashboards are not limited to default workbooks, though. KQL can be used to create your own queries and build custom dashboards.
Alerts
In Microsoft Sentinel, you can schedule workbooks, both default and custom, to be executed on a schedule. In case something out of ordinary is detected, actions can be defined. The most basic action is sending an alert and notifying a person or team that they need to act.
Alerts can be sent in different forms including email, Teams channel messages, or creating a work item in a project management tool. Alerts are the most basic action that can be performed, though you can do much more. Once a query is executed on a schedule and an anomaly is detected, a specific action can be triggered.
Rather than sending an alert, our action can be anything that can be started by a trigger. For example, if we detect that an account has been compromised, you can set up an action to disable the account in question. If a brute force attack is detected, you can also configure an action to block IP addresses from which the attack originates or temporarily close ports that are being targeted.
Sending an alert is useful and it will notify someone that they need to act. But the question is: “When are they going to act?” If an alert is sent in the middle of the night, will you have someone to deal with it? If a number of alerts are sent at the same time, will you have enough employees to handle them?
By the time someone acts, it may be too late. Fortunately, you have the option to automate responses and stop attacks until your team can investigate them properly. This type of response exceeds traditional requirements for SIEM solutions, and it’s a useful addition to the fight against modern cyber threats.
Correlation
As security threats have become more sophisticated in recent years, many organizations are seeing an increase in multistage attacks. Essentially, to bypass security checks, attacks are deployed at multiple stages and points of entry, which increases the chances of an attack being successful.
For this reason, you need to set up some correlation between different data types. This will allow your organization to search for anomalies across different logs over time, so it can connect the dots and detect incidents during multistage attacks. As Microsoft Sentinel stores data from many different sources in a single location (Log Analytics), you’ll be able to easily query any ingested data.
Retention
To detect multistage attacks, you’ll need to query data over time, which brings us to data retention. Log Analytics allows organizations to store data for up to two years, which might be overkill when it comes to this type of attack. However, many compliance standards require security logs to be stored for a longer period of time.
If an organization uses a SIEM platform and all security-related logs are already stored there, it provides a single point to ensure compliance is reached (contrary to retention at multiple points if controlled at the data source). With the ability to keep data for up to two years, Microsoft Sentinel is aligned with the retention period of most industry standards. If a longer period is required, data from Log Analytics can be sent to a storage account for long-term retention (up to 7 years).
Forensic analysis
The last requirement for SIEM is the ability to perform forensic analysis. Once your organization becomes aware that a security incident has occurred, it needs to be able to investigate it and find out the “where, how, and what”: where was the entry point, how the incident evolved across the system, and what kind of reach (or damage) it had.
This forensic analysis requirement actually combines the previous two: You need to be able to search across different logs (correlation) and across time (retention). Once initial access was gained, the attacker will try to exploit your data as much as possible and access different resources. As a result, you need to be able to determine the precise level of exploitation of your company’s data.
Very often, once initial access was gained, the attacker will stay dormant for a period. If access is used aggressively, the risk of detection is much higher. However, attackers are much more likely to try to stay inside as long as possible to gain access to as much data as possible.
You also need to take into consideration that most incidents are detected six months (or more) after a security breach occurred. Therefore, you need to have a retention policy that allows your organization to search across its logs for a longer period of time.
What makes Microsoft Sentinel different from other SIEM solutions?
All the requirements of a SIEM solution are met by Microsoft Sentinel. But what makes Sentinel different from other SIEM products?
We mentioned the ability to automate responses to threats, which is an excellent addition to the list. However, there is another capability that makes a true difference – machine learning (ML).
The amount of information that is being generated multiplies each year, and the same can be said for security logs. As a result, it becomes increasingly difficult to search for anomalies in this ocean of data. Combine that with zero-day exploits and multistage attacks, security becomes almost an impossible job. Through options like User and Entity Behavior Analysis (UEBA) and multistage attack detection (Fusion), Microsoft Sentinel uses machine learning to detect incidents in real-time.
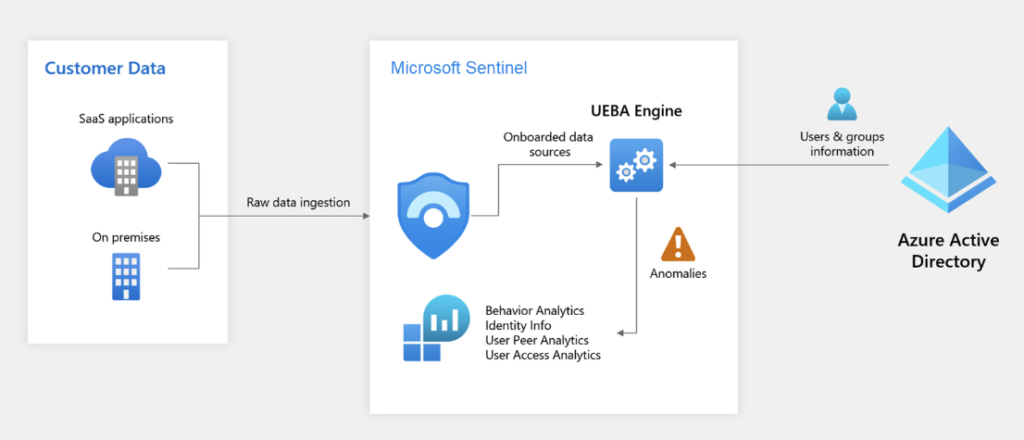
Data is analyzed and used to create a baseline, establishing expected behavior and events. This is combined with Microsoft’s database of known incidents and exploits to amplify the results and detect suspicious activity. The larger data set over a long period results in the best possible results, and the machine learning capabilities in Microsoft Sentinel allow the detection of the smallest anomalies in your systems.
Last but not least, organizations can also bring their own machine learning into Microsoft Sentinel. By connecting their own machine learning models, organizations can address specific security problems and improve the analysis of their data.
Summary
Microsoft Sentinel is a complete SIEM solution: It can ingest data from almost anywhere, query the data to create dashboards and alerts, and query across different data types and over time. It can also keep data for long periods and be used to investigate incidents etc.
Microsoft Sentinel also brings new features to the table such as automated incident response and machine learning, and they can make a real difference in stopping an attack and system compromise. Technology is developing at an accelerated pace, but so are threats. Compared to other SIEM solutions, Microsoft Sentinel may well go the extra mile and better protect your organization from the bad guys.
Related Article:


