Azure Sentinel, Microsoft’s Cloud-Native SIEM Solution, Is Now Generally Available
Microsoft announced September 25th on its Security blog that Azure Sentinel has reached general availability. Based on Azure Monitor Log Analytics, Sentinel adds a cloud-native Security Information and Event Management (SIEM) solution to Azure’s already long list of services. SIEM lets organizations collect event logs from different systems, centralize them, and perform analysis to identify potential issues and threats. The key difference between Sentinel and other SIEM solutions on the market is that Sentinel provides insight into Microsoft’s cloud services, like Azure and Office 365.
Designed to work with hybrid cloud environments, Sentinel monitors events from on-premise devices and cloud services. At launch, there are 25 data collectors providing access to a variety of Microsoft and non-Microsoft services and solutions. There’s also integration with other popular clouds, like Amazon AWS. While Sentinel is not as mature as market leaders like Splunk, if your organization is Azure-first, then it’s worth looking at.
I’ve been working with Sentinel while it was in preview and it’s easy to set up and configure. There’s a free tier that lets you keep data for up to 7 days, which is ideal for testing scenarios. Because Sentinel is a cloud-native solution, it could also help organizations reduce infrastructure costs as it can scale resources as needed. Two pricing plans, Pay-As-You-Go and Capacity Reservation, offer organizations additional flexibility. Capacity Reservation can save up to 60% on Pay-As-You-Go pricing, which costs $2.46 per GB. Sentinel pricing is for the data analytics performed on your logs. You’ll need to pay separately for the data ingested by Azure Monitor Log Analytics. But Microsoft is providing free data ingestion for Office 365 audit logs, Azure activity logs, and alerts from Microsoft threat protection solutions. Additionally, you’ll need to pay Azure Monitor Log Analytics data retention prices if you want to keep your data for more than 90 days.
Sentinel can be integrated with other Azure services to provide automated responses to security events. You can even use your own machine learning models for customized analysis using Azure Machine Learning Studio. And use of machine learning and artificial intelligence (AI) to analyze event data enables Sentinel to respond to the current threat landscape.
In my time with Sentinel, I’ve only looked at the built-in connector for Windows Server, which lets you import security events. Sentinel supports importing custom data streams in the Common Event Format (CEF), so if you don’t find a data connector for a specific system or kind of event, you should be able to work around it.
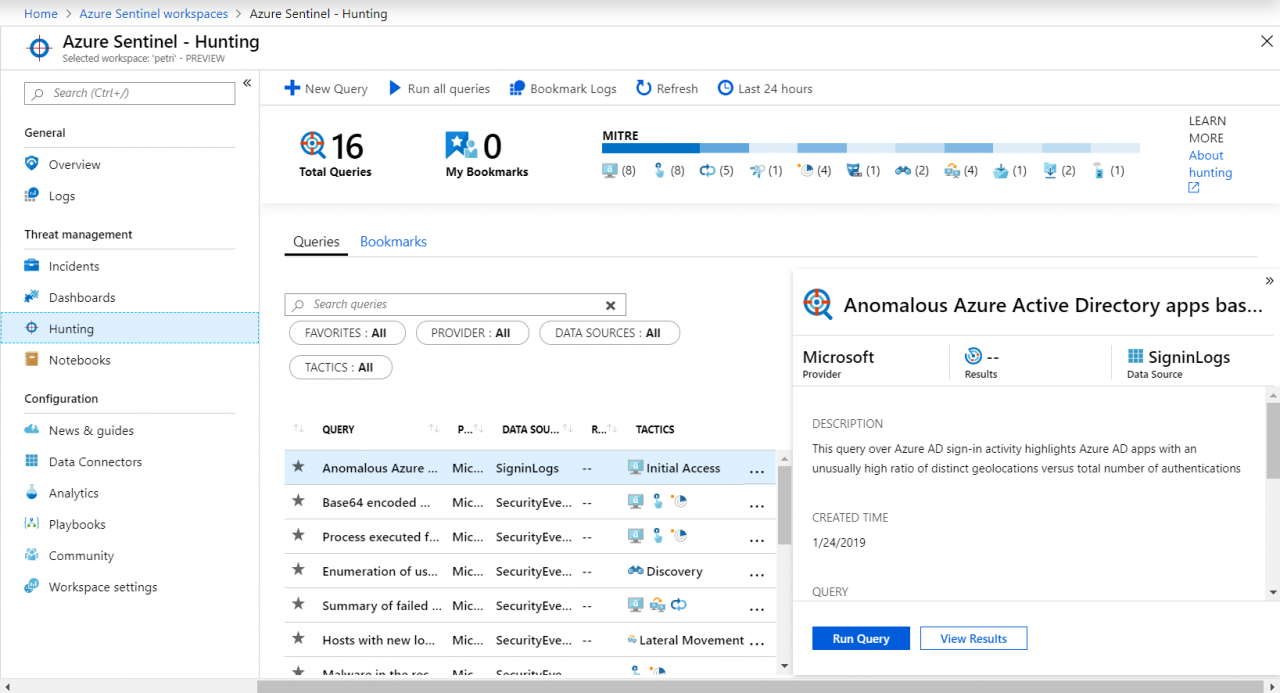
Microsoft says on its blog: Now RapidDeploy uses the complete visibility, automated responses, fast deployment, and low total cost of ownership in Azure Sentinel to help it safeguard public safety systems. “With many SIEMs, deployment can take months,” says Kreilein. “Deploying Azure Sentinel took us minutes—we just clicked the deployment button and we were done.”
You can read the full case study on Microsoft’s website here. I’ve started looking at Sentinel on Petri and will delve into it in more detail over the coming months. But as RapidDeploy’s experience suggests, it does appear to be very easy to set up and to get useful information that can be actively used to block threats without needing to involve consultants or long implementation projects.
For more Petri articles on Azure Sentinel, click here.
Related Article: