Top Azure Cloud Security Controls to Understand
This short guide will provide a top-level overview of the crucial Azure cloud security controls and best practices to be aware of. The highlighted suggestions will provide you with options worth considering for deployment across your estate to strengthen your security posture and mitigate the evolving number and severity of cloud-based threats and risks that exist.
Microsoft Azure is one of the most widely used and versatile cloud computing platforms on the market today. Recent statistics suggest that 41% of organizations entrust ‘significant’ workloads to Azure in some capacity, with the platform witnessing an 8% growth over the last two quarters, maintaining almost a third of the cloud infrastructure services market share.
One of Azure’s primary strengths is in software-as-a-service (SaaS), offering many enterprise-grade tools and offerings, which range from data management, storage and networking to advanced analytics, IoT applications and even machine learning and artificial intelligence capabilities. It also offers infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) solutions, which combine to create a robust, flexible, and scalable environment to host applications.
Despite the convenience and benefits of this public cloud infrastructure, there comes a plethora of security risks that need proper, proactive mitigation. IT professionals and key decision-makers in businesses worldwide have a duty to uphold data integrity and compliance with relevant data protection standards. This is why it’s crucial for them to understand the key Azure security controls available to deploy to their incumbent, native cloud environments.
Native Azure cloud security controls
Azure provides a number of native security controls and features built into the platform. This means that users don’t have to solely rely on third-party security tools and fully-managed solutions from different vendors, although that can bolster defenses significantly.
However, it’s important to understand the nature and purpose of Azure’s built-in security controls as a critical first step. Here are the key controls to bear in mind, separated into broader parent categories.
Identity and Access Management (IAM)
Identity and access management is imperative to oversee across your infrastructure. If using Azure, these are the key controls you should be aware of.
- Microsoft Entra ID (formerly known as Azure Active Directory or Azure AD): Provides a seamless cloud identity and access management solution that connects all users to all native apps, devices and information via single sign-on and strong multi-factor authentication (MFA) controls enabled. RBAC (role-based access control) is also enforced.
- Privileged Identity Management (PIM): A service built into Entra ID that enables you to manage, control, and delegate access to important resources located across your estate, including resources in other Microsoft Online Services like Microsoft 365.
- Entra ID Identity Protection: A built-in feature that aids organizations in detecting, investigating, and containing identity-based risks and threats. It uses risk evaluations, anomaly detections, and remediation to automatically mitigate threats related to user identities. It can be fed into built-in tools like Conditional Access or fed back to a third-party SIEM (security information and event management) tool.
Security monitoring and alerting
Azure can be used as an asset to help conduct real-time monitoring and alert users to the presence of security incidents, anomalies, or suspicious activity. This relies on the strategic use of:
- Azure Security Center: A centralized, baseline security posture management tool. This tool collects events from Azure and correlates them in a security analytics engine to provide you with specific recommendations for improving security posture.
- Azure Sentinel: A scalable SIEM and security orchestration automated response (SOAR) solution aggregating data that’s obtained across your environment that may correlate to the same security incident.
- Azure Defender: A paid add-on Azure service that offers advanced protection controls for servers, SQL, DNS, and container registries, among others, as well as non-Azure servers in a different cloud environment or on-site. Defender also offers JIT (just-in-time) access, real-time alerts, and adaptive application controls.
Network security
Locking down systems, apps and files stored in any cloud environment is crucial, and it’s imperative that any network that it sits on remains secure and free from compromise. Within an Azure infrastructure, take advantage of these in-house tools to bolster your network security.
- Azure Firewall: A cloud-native, intuitive network firewall solution that provides real-time threat protection for cloud-based workloads sitting on your Azure infrastructure. It offers complete traffic detection with plenty of scalable deployment options.
- Azure DDoS Protection: DDoS (distributed denial of service) attacks are prevalent in this day and age, particularly for businesses migrating to the cloud. Azure DDoS Protection provides advanced mitigation features to defend against exhaustive attacks that render applications or servers unavailable for extended periods. Users can deploy this tool at any endpoint that uses the Internet as a backdrop.
- Azure Virtual Network: This is a built-in service that enables the creation of secure private networks in your Azure cloud environment, isolated from the public Internet. Deploying an Azure VPN means that all resources can securely communicate with each other and access open-source resources with highly secure connections.
- Azure VPN Gateway: This is a service that uses specific virtual network gateways to send encrypted traffic between Azure virtual networks and on-premises locations over a public HTTPS connection. It supports IKEv2 and SSTP protocols as well as VLAN connections.
Baseline Azure security best practices
In addition to leveraging Azure’s many native security features, organizations should also follow these best practice recommendations as far as individual and collective security are concerned.
- Deploy MFA where possible – Enforce multi-factor authentication for all user and administrative logins to add an extra layer of protection.
- Follow the least privilege principle – Only grant users the minimum permissions needed to perform their tasks and be selective with provisions.
- Monitor actively – Review logs, metrics, and analytics closely to detect issues and anomalies early, with real-time alerts configured to isolate potential threats.
- Patch promptly – Regularly apply the latest security patches to operating systems, applications, and Azure services to eliminate vulnerabilities.
- Encrypt data – Leverage Azure’s SSE (service-side encryption) capabilities such as Azure Storage to autonomously encrypt data when persisted to the cloud. Also, use Azure Disk Encryption (ADE) to protect and safeguard data at rest while maintaining compliance.
- Keep backups of data – Use tools like Azure Backup to create regular backups of data, applications, files, folders, and VMs as a recovery option for accidental or malicious data loss. Don’t forget to deploy backup solutions for SQL Server databases running on Azure either.
- Restrict inbound network access – Limit external inbound internet traffic to your Azure environment to only what is required using a mixture of Azure Firewall, DDoS protection, and Virtual Network.
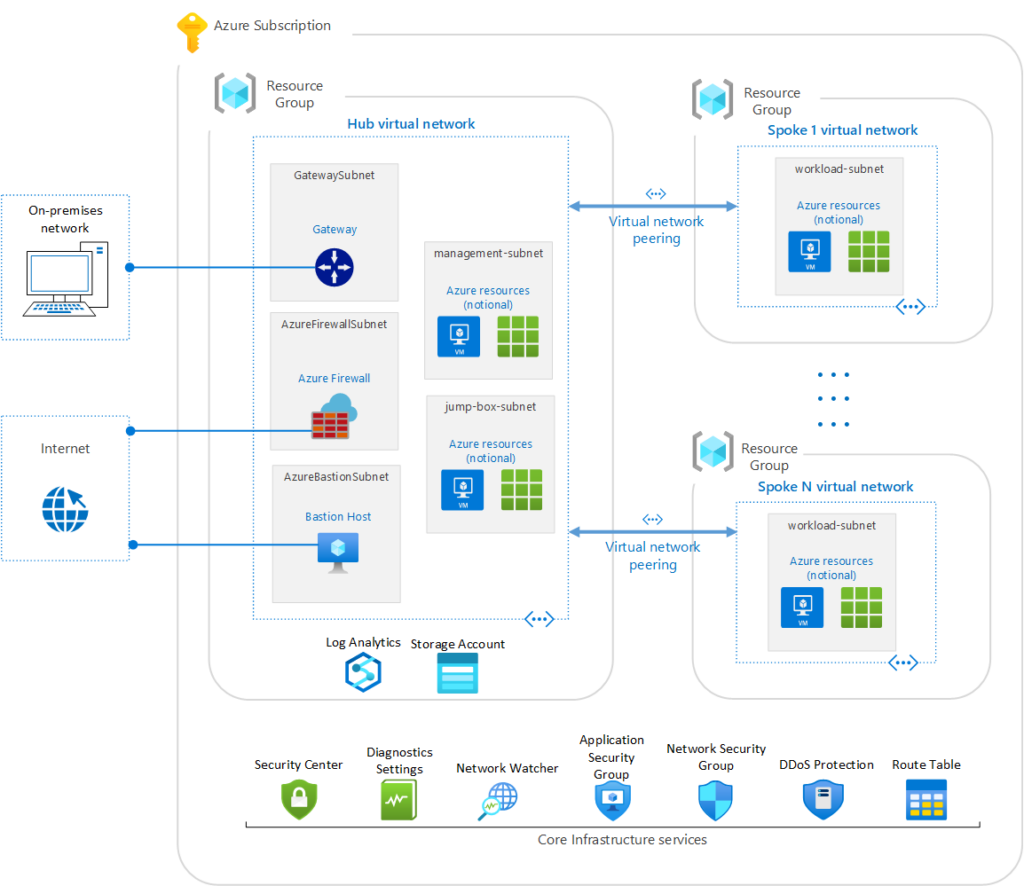
Third-party security solutions for Azure cloud security controls
While Azure’s native tools provide robust core security capabilities, organizations can create additional layers of security by leveraging innovative third-party solutions that are befitting for their estate.
This includes (but is not limited to) using cloud access security broker (CASB) solutions that monitor and control access to SaaS applications while enforcing security policies. Companies should also consider deploying WAFs (web application firewalls) to create an additional barrier between a native app and the Internet, which can filter and monitor HTTP traffic and prevent XSS (cross-site scripting) and SQL injection attacks, which are alarmingly common.
Human-powered processes like ethical hacking, Microsoft Azure penetration testing, red team assessments, vulnerability scanning, and others also work wonders at helping organizations uncover unknown or hidden vulnerabilities prone to exploitation. These could exist in web application code, or in highly covert connections between endpoints and servers.
Solutions for highly regulated industries
As a whole, organizations in highly regulated industries – like finance and healthcare – may benefit significantly by consulting with specialist providers that can deploy enterprise-wide security monitoring and detection solutions, as well as real-time incident response services. With skilled experts watching network traffic for any suspicious activity, it’s reassuring to know that your Azure environment remains locked down and in safe hands.
Invest in strategic third-party tools if warranted
Azure provides a multitude of robust native cloud security controls that organizations should take advantage of to strengthen cloud protection. While it’s imperative that you follow baseline best practices around patching, backups, access control, and connectivity, knowing how to position your Azure environment as securely as possible will provide long-term stability and reassurance. Consider investing in strategic third-party tools for enhanced threat detection and vulnerability management if warranted.
It’s clear to see that having a strong understanding of key Azure cloud security controls and tools will help IT teams secure cloud environments while realizing the full benefits of the platform.



