Introduction to Microsoft Intune
In today’s Ask the Admin, I’ll provide an overview of Microsoft Intune.
Part of Microsoft’s Enterprise Mobility + Security solution, Intune handles the task of managing PCs and mobile devices, such as Windows 10 tablets, Android phones and Apple iPads. At the heart of Intune is Mobile Device Management (MDM), which is a set of standards for managing mobile devices and provides features similar to, but not as comprehensive as Group Policy. MDM is not a Microsoft technology, so Group Policy remains the best solution for managing domain-joined Windows devices.
A relatively recent addition to Intune is Mobile Application Management (MAM), allowing organizations to manage Microsoft mobile apps without users needing to enroll their devices. In BYOD scenarios, users are often reluctant to enroll devices with MDM because it means handing over complete control to IT. MAM is a compromise that gives organizations some control over how business data is used on devices not owned by the company. Finally, mobile app security gives organizations the ability to isolate business data so that corporate files can be wiped without touching users’ personal information.
Integration with Azure Active Directory (AAD) and Azure Rights Management (Azure RMS) provides identity management and data protection, respectively. Intune additionally provides security features required by organizations for managing data and devices, including multi-factor authentication for users enrolling Windows devices to Intune if your organization has the right infrastructure in place. Endpoint Protection for Intune is a managed version of Windows Defender that includes reporting capabilities, and Windows Firewall rules are also configurable.
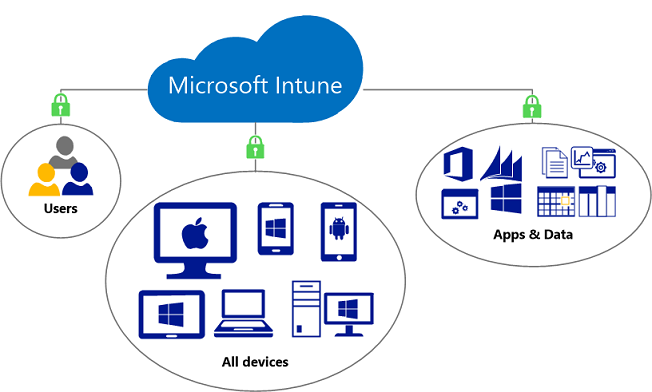
Intune can be used as a lightweight alternative to Active Directory. It provides some software distribution features, inventory, limited configuration management for Windows PCs, and remote support options in the form of Remote Assistance for Windows 7, and TeamViewer support for Windows 10. Plus, it’s also possible to use MDM policy to perform remote wipes if a device is lost, and there’s a feature that allows VPN and Wi-Fi profiles to be provisioned for secure access to corporate networks.
System Center Configuration Manager (SCCM) and Intune
Intune and SCCM can be integrated to extend SCCM into the cloud for managing mobile devices, providing a central management console for managing all your organization’s devices. But if Intune is quick and easy to deploy, and requires no on-premises infrastructure, a hybrid SCCM/Intune deployment is complex to manage and has a steep learning curve.
Microsoft recommends using SCCM, or a hybrid management approach, for organizations with 50,000 or more endpoints, or when management of traditional “fat clients” is required. SCCM provides advanced features not found in Intune, such as the ability to provision Windows to bare metal, Role Based Administration Control (RBAC), advanced reporting, full app inventory, targeting via Collections, and because SCCM moves part of the processing and storage overhead on-site, a hybrid SCCM/Intune deployment scales better than standalone Intune. SCCM also provides access to advanced tooling, such as the SCCM console, PowerShell, and logging.
Intune isn’t the only MDM solution on the market, and other products from AirWatch and Citrix are also popular. But Microsoft is in a unique position to provide a complete management solution with support for integration with SCCM. Over the next couple of months, I’ll be looking at how to set up and manage devices using Intune on the Petri IT Knowledgebase.
Related article: How to Package and Deploy Windows Applications with Intune




