What is Azure AD B2B?

Discover the benefits of using Azure AD B2B in your organization. Learn how it can improve collaboration and streamline access for external partners, and boost your users’ productivity, safely and securely.
What is Azure B2B?
Microsoft Entra B2B (formerly Azure AD B2B) is a feature/service within the Microsoft Entra ID that allows collaboration between your users and trusted guests from outside organizations. The biggest benefit is the seamless and secure framework for your partners, clients, and vendors to access your resources and applications.
B2B is enabled by default in all Microsoft Entra ID tenants, but no connections exist at tenant creation. There are many administrative settings and controls to manage your connection to other companies.
What are the differences between Azure AD Federation and Azure B2B?
Azure AD Federation is focused on single sign-on (SSO) and identity federation between your on-premises Active Directory and Microsoft Entra ID (Azure AD). This is performed when you want to extend your on-premises AD with Azure AD. It allows for seamless integration and SSO for your users in on-premises AD and Azure AD.
Azure AD Federation lets you use protocols like SAML (Security Assertion Markup Language) and OpenID Connect to create trusts between environments. This can be a rather complicated setup as it involves enabling Active Directory Federation Services (AD FS) on Windows Servers in your on-premises Active Directory. Microsoft highly recommends moving away from this ‘legacy’ technology and embracing Microsoft Entra ID. I’ll offer more information on this later.
The main difference between these two technologies is that Microsoft Entra B2B enables secure collaboration with external guest users who are not part of your directory. In addition, federation relies on pre-existing accounts in trusted Identity Providers (IdPs), while B2B uses various external authentication options.
What are the differences between Azure AD B2B and Azure AD B2C?
Although both of these technologies deal with external identities, they do serve distinct purposes. Microsoft Entra B2B is ‘business-to-business’ and Azure AD B2C is ‘business-to-consumer’.
The purpose of B2B is to securely enable collaboration and the sharing of resources with validated external entities while maintaining separate directories. However, the purpose and focus of B2C is to manage authentication and authorization for consumer-facing apps, offering seamless user sign-in experiences.
Benefits of Azure AD B2B
There are several benefits to implementing Azure AD B2B (Microsoft Entra B2B).
- simple access to your company’s secure resources
- Self-Service sign-up portal
- administrative control over connections to your resources
The biggest advantage is giving your suppliers, partners, and trusted entities simple access to your company’s secure resources, without needing to deal with multiple domains – you work with the single domain you already utilize. All of the technical infrastructure and configuration are handled by Microsoft Entra – all you need to do is specify what users and organizations have access and to invite them as guests.
Some examples of secure resources include Microsoft Teams, SharePoint Online sites, and OneDrive files. Other systems could include CRM, ERP, or custom-developed apps. You also have the option of including other infrastructure resources like Azure VMs, SQL databases, and Azure Data Lake platforms enabling troubleshooting or development collaboration across a wide variety of technologies.
From the Microsoft Entra ID portal ‘Users’ view, you can click ‘Invite external user’ and send an email invitation directly to them. Once they accept your invitation, and sign in with their credentials, you can assign them to security groups and applications right along with your users.
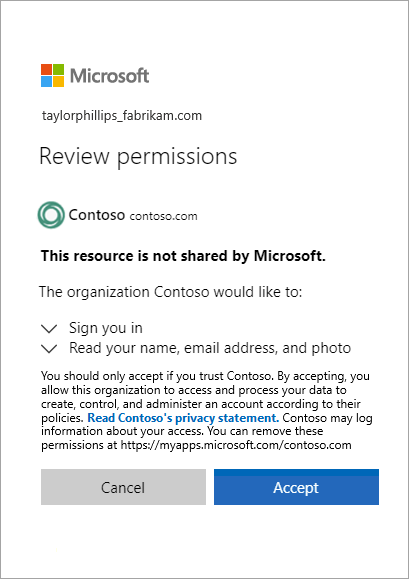
You also have a Self-Service sign-up portal to customize. The other major benefit is the amount of administrative control you have over all of these connections. You can choose explicitly what each external user (guest) has access to including applications and groups.
Azure AD B2B pricing
The pricing model for Microsoft Entra B2B follows the pricing for Microsoft Entra ID in general concerning users. Let me supply a table that summarizes the basic pricing tiers, associated costs, and benefits.
Table 1 – Microsoft Entra B2B Pricing Models
| Plan | Starting Price (Per User/Month) | Included Features |
|---|---|---|
| Microsoft Entra ID Free | Free | – Included with Microsoft cloud subscriptions (e.g., Azure, Microsoft 365). Basic collaboration. |
| Microsoft Entra ID P1 | $6.00 | – Comprehensive identity and access management features. Included with Microsoft 365 E3. |
| Microsoft Entra ID P2 | $9.00 | – Advanced capabilities beyond P1. Included with Microsoft 365 E5. |
| Microsoft Entra ID Governance | $7.00 | – Identity governance features for P1 and P2 customers. Special pricing is available for Microsoft Entra P2 customers. |
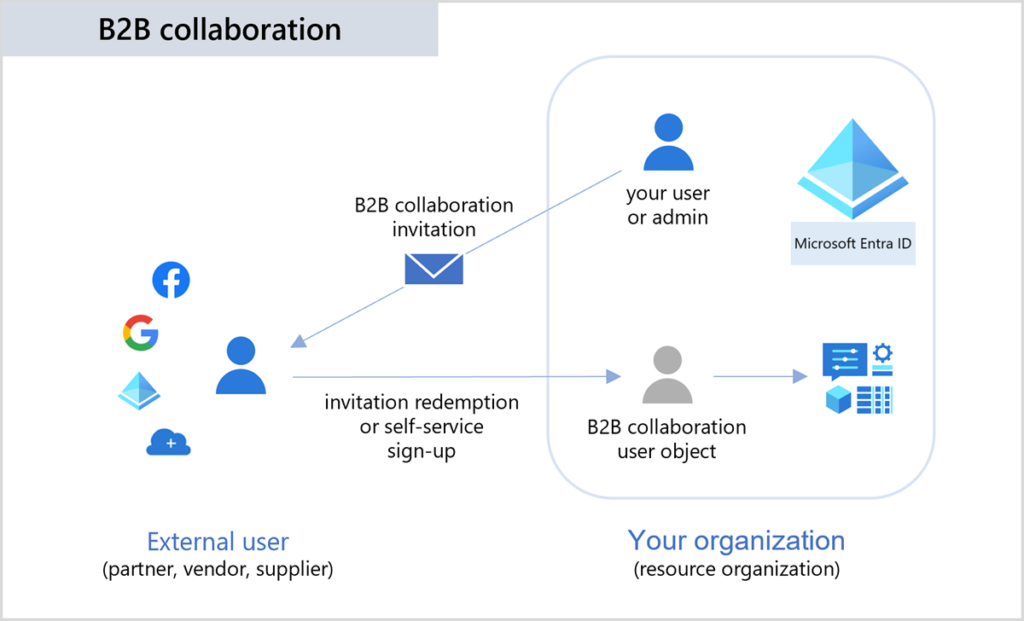
How does Azure B2B authentication work?
I’ve touched on, at a high level, the crux of Microsoft Entra B2B logins for users, but let me give you a more detailed overview of the steps.
- An admin in the Microsoft Entra ID portal sends an email invitation for an external user to be added to their tenant as a guest.
- The guest user clicks on the link included in the invitation email and chooses an authentication method (Google account, existing Microsoft account, one-time passcode (OTPC), etc.
- After signing in, Microsoft Entra is permitted to verify their identity.
- Microsoft Entra verifies the user’s credentials with the external identity provider. If successful, the information is sent back to Microsoft.
- Microsoft Entra verifies everything and changes the status of the guest from ‘invitation pending’ to ‘accepted.’
- Microsoft Entra grants the user an access token containing information about the guest user and their associated permissions.
- This information is then sent to the application (Teams, SharePoint, etc.) with the appropriate permission levels.
An example scenario – Global Pharmaceuticals
Let me paint a hypothetical scenario of a company utilizing Microsoft Entra B2B and how they benefit from it.
Global Pharmaceutical (GP), a fast-growing global company, faced many challenges in managing its complex supply chain. They relied on multiple vendors for packaging, ingredients, and logistics. This resulted in cumbersome and inefficient communication channels and data exchange. They needed a new solution fast – Microsoft Entra B2B!
GP invited their key vendors to collaborate through B2B. The IT Pros at GP proactively received a list of their partners’ email addresses (in their own environments). Vendors and partners then accepted the invitations emailed to them. The integration is straightforward – no need to learn and keep track of another set of credentials.
GP shared secure documents and specifications through a secured and fast SharePoint Online site. Gone were insecure email attachments, potential loss of data due to data spread, and any loss of critical information. Microsoft Teams channels were created in the environment, giving both sides real-time communication and seamless collaboration.
GP also created and shared Power BI dashboards for their partners to offer them an easy-to-read snapshot of each partner’s monthly sales figures and projections.
Using policies to protect your apps and services
You can use several methods to protect your apps and services when sharing them with Microsoft Entra B2B. The most important is Azure AD Conditional Access (CA) policies. I recommend using them in your environment, period. With CA policies, you can restrict logins based on geography, time of day, device type, and sign-in risk, among others. All of this is built into Microsoft Entra ID.
The second most important, and this is only second by a hair, is multifactor authentication (MFA). I recommend you use MFA in as many scenarios and endpoint areas as you can. Using it with Microsoft Entra B2B simply checks off another box for this additional ‘edge scenario’ into your tenant/organization.
Post implementation, be sure to schedule a weekly, monthly, or quarterly review of your Microsoft Entra ID Sign-In logs. You can easily filter results based on each application you have shared out, or even on a specific user (guest) account. This gives your IT Pros a lot of information about how, where, and when exactly someone attempted to access these applications and services.
Integrating with external Identity Providers
There are a few key ways to access external identity providers when verifying credentials in Microsoft Entra B2B. Let me go through the big ones for you:
- Social Identity Providers
- This is Google, LinkedIn, Facebook, etc.
- When configured in your Microsoft Entra tenant, guest users simply use their existing logins to authenticate.
- Not recommended for highly secure and sensitive resources.
- Direct Federation
- This method allows Google, Facebook, and Okta to use SAML and WS-Fed protocols to authenticate guest users directly.
- You create trust relationships between your Microsoft Entra ID tenant and the external IdPs.
- Email One-Time Passcode (OTPC)
- This quick and easy option sends a one-time passcode to the guest user’s email address for authentication.
- Again, label this as ‘quick and dirty’ as it is a less secure method.
- Microsoft Entra B2C (look familiar?)
- That’s right. To go ‘all-in’, you can engage in Microsoft Entra B2C collaboration and take greater control over the guest user sign-up and sign-in experience.
- B2C, as described in my previous article (insert link) provides a fully branded sign-in experience and offers various authentication methods.
- The most robust offering, but the most complex. Will likely incur additional costs.
Seamless and secure access to your company resources
Microsoft Entra B2B empowers companies of all sizes to take the guesswork of how to offer their trusted partners and contacts secure and seamless access to their resources. By inviting guest users, you can share applications and customize the onboarding experience, boosting productivity across the board, and fostering meaningful and two-way trusted relationships.
Please drop a comment or question below and thank you for reading!
Table of contents
- What is Azure B2B?
- What are the differences between Azure AD Federation and Azure B2B?
- Benefits of Azure AD B2B
- Azure AD B2B pricing
- How does Azure B2B authentication work?
- An example scenario – Global Pharmaceuticals
- Using policies to protect your apps and services
- Integrating with external Identity Providers
- Seamless and secure access to your company resources



