How to Find and Block Breached Passwords in Active Directory

Cybercriminals love passwords. They’re simple to guess, easy to steal, and can offer unfettered access to a goldmine of data to hold for ransom or sell to other cybercriminals. For those same reasons, compromised passwords are a constant headache for IT teams, who spend far longer than they’d like helping users reset them and fixing problems related to credential theft. Verizon estimates that almost half (49%) of all breaches involving external actors involve stolen credentials.
This post is sponsored by Specops Software
However, passwordless authentication is some way off being affordable and effective enough to roll out across the average organization. Essentially, passwords are the best tools businesses have to authenticate users in Active Directory. So instead of bemoaning them, we need ways to make sure organizations aren’t at risk from passwords that have already been compromised by cybercriminals.
The good news is there are ways to root out breached passwords from Active Directory. I’ll explain why detecting compromised passwords is such a key security step, then walk you through two ways you can find and block breached passwords.
Why track down compromised passwords?
Let’s say you’ve got a strong password policy (which hopefully you do!) that stops users from creating weak passwords that are too short, lack complexity, or are iterations of ones they’ve used before. The problem is that even strong passwords can become compromised through phishing attacks. Devices can become infected with malware, and human error can lead to data breaches. This risk is amplified when people reuse their work passwords on personal devices and websites that are more susceptible to compromise.
Breached credentials sell for good money on the crime-as-a-service marketplace – threat actors know that it’s much easier to log in to a system than hack in. IBM estimates it can take almost a year (an average of 327 days) to identify a breach from stolen or compromised credentials. So, waiting for a user’s password to expire or hoping to spot the early signs of an attack starting are risky choices.
Manual Active Directory password audit: step-by-step guide
Organizations need a way to regularly and reliably check whether they have compromised passwords in their Active Directory environment. The process discussed here will generate files with extremely sensitive data that could lead to a compromise of your passwords and network. If this kind of thing is new to you, I’d suggest practicing on a test domain first, rather than your live Active Directory. Warnings out the way – let’s get started.
Extract Active Directory NTLM password hashes
First, you’ll need to get a copy of your password hashes from Active Directory. This is pretty simple as long as you’re logged in to a domain controller (DC) with a Domain Admin level account.
- First, you’ll need to run ntdsutil from an elevated command prompt, then set the active instance to ntds.
Act ins ntds
- Next, use the Install From Media (ifm) command.
Ifm
- This will let you dump the Active Directory database and the SYSTEM file with the following command. You should see a similar screenshot to the one below:
Create full c:\audit
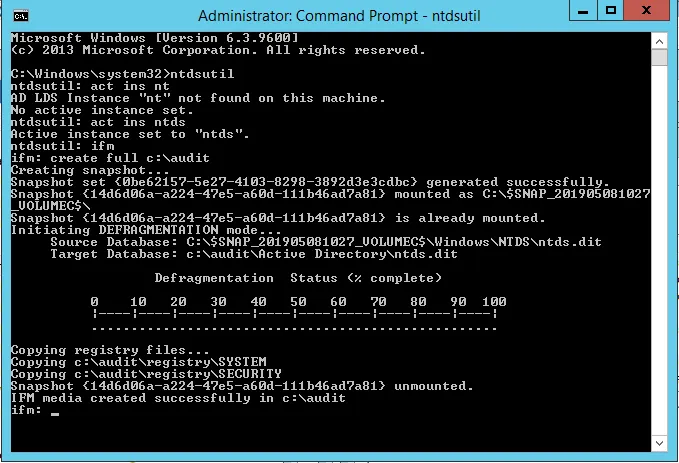
- Following these steps will dump the NTDS.dit and SYSTEM files into the c:\audit folder.
For security reasons, you don’t want to store a copy of your password hashes on a network-connected device. Once you’ve got the files, copy them from your DC to a PC (preferably a fast one with a decent graphics card) that’s disconnected from the network. You can then delete the files from your DC.
Dumping the password hashes from the database
The next step is to dump the password hashes from the database. I’d recommend a free tool you can get from GitHub that I’ve found reliable: NTDSAudit from Dionach.
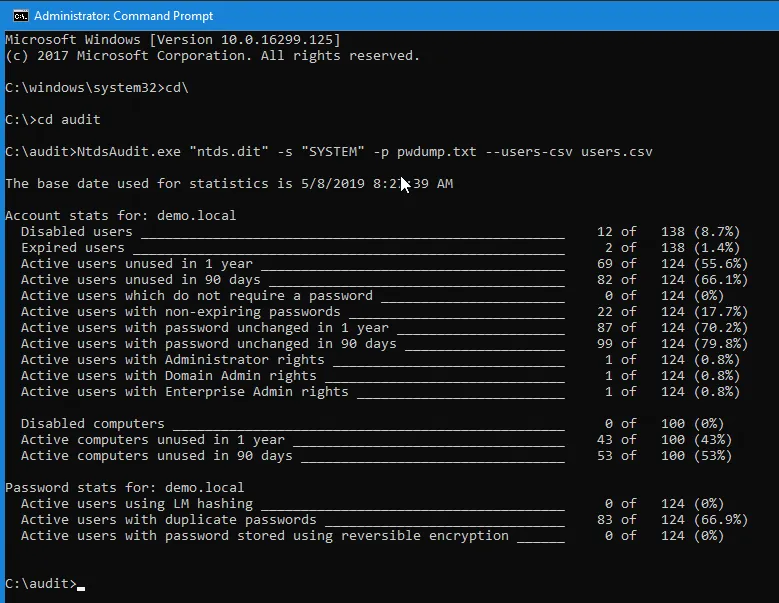
- Simply place NTDSAudit.exe in the same folder as your NTDS.DIT and SYSTEM files, then run the following command:
Ntdsaudit.exe “ntds.dit” -s “SYSTEM” -p pwdump.txt –users-csv users.csv
- You should end up with a similar screen to the image below. This will give you some helpful stats as well as the two files: pwdump.txt and users.csv.
Cracking Active Directory NTLM password hashes using hashcat
We’ve now got the password hashes and can attempt to crack them. Note there are lots of tools to choose from, but most will be flagged by antivirus software so you might need to disable it. Feel free to choose what works best for you. For the purpose of this article, I’ll use hashcat.
You can download Hashcat or build it from source and place it somewhere on your computer of choice. It’s preferable to have a discrete graphics card for this exercise, as you’ll be able to calculate hash candidates quicker on a faster machine. Cracking NTLM hashes can be slow without the presence of a fast GPU. You’ll also need to ensure the correct GPU computer framework is present on your computer, whether that’s CUDA, HIP, or OpenCL depending on your platform (configuration is outside of the scope of this guide).
You’ll also need a wordlist to attack the hashes with, as a brute-force or mask attack can be very slow. We will be using the rockyou.txt wordlist a common starting point for brute-force and password-cracking attacks. This rockyou.txt wordlist is distributed out of the box on Linux distributions such as Kali Linux, however, you’ll need to download it yourself on a Windows host.
Windows Defender will also flag hashcat as malware, so you’ll need to whitelist the directory you’re working from if you’re using Windows:
- Navigate to the folder you’ve downloaded hashcat to, or if you’ve installed it from your package manager, navigate to a working directory.
- You can then run hashcat from the command line with the following command. Modify it as required for your operating system:
./hashcat -m 1000 -O -w3 pwdump.txt rockyou.txt
This command will run an attack of mode 1000 (as we are using NTLM hashes), using an optimized kernel (which has some limitations on the length of candidates it will generate, but it will perform better for this exercise) and the appropriate hardware available on the machine. If you’ve installed the required compute frameworks, hashcat should use your discrete GPU by default.
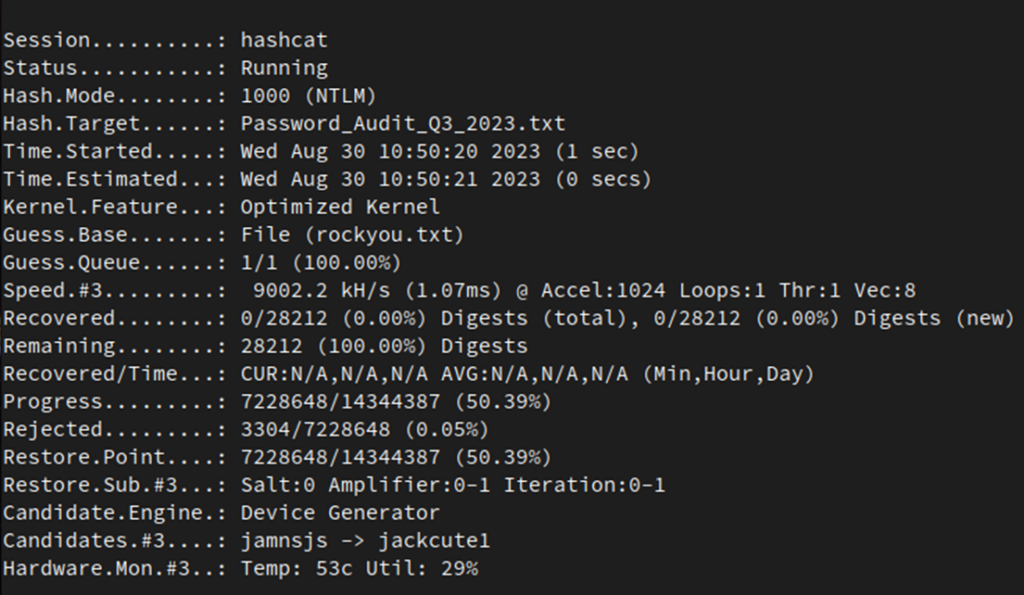
As the attack does not specify a rule, this would be considered a dictionary attack. It will simply use rockyou.txt as the list of password candidates without modifying them in any way.
A follow-up attack could be completed as a rule attack, using the rules of your choice. In this case, I’m using oneruletorulethemall.rule, which you can find on GitHub.
./hashcat -m 1000 -O -w3 pwdump.txt rockyou.txt -r oneruletorulethemall.rule
The command will manipulate the records in the wordlist creating new password candidates, based on common password patterns found in other datasets. This will take longer than the previous dictionary attack, however, it will generate new candidates that were not present in the original attack.
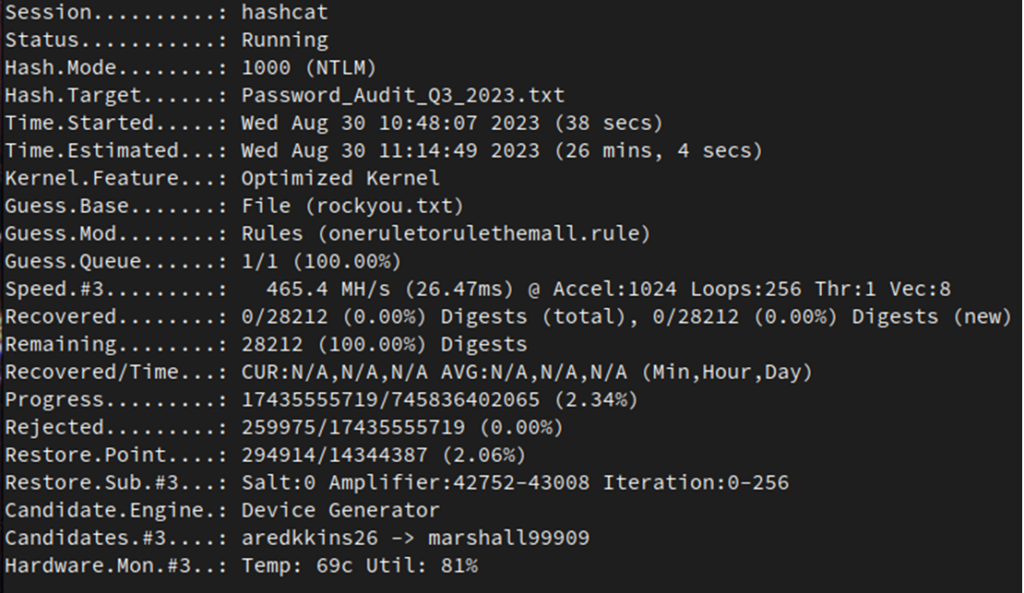
You can then use various other attack types, with different dictionaries and rules, as well as run a brute-force attack should you need to. Hopefully, you’ve managed to crack some of the passwords present in the Active Directory dump you’re working from, but this may take some trial and error depending on how strong your users’ password hygiene is.
You can move on to other wordlists, such as COMB, or a current dataset from hashmob.net, and some other rules. However, please note that this will take some experimenting as it’s more an art than a science.
The automated (and easier) way to find compromised passwords
The manual process we just walked through can be a useful way of figuring out if you’ve got compromised passwords. However, it’s not something you want to be doing all the time. Adding a third-party solution to Active Directory such as Specops Password Policy can keep you on top of compromised passwords automatically.
Specops Password Policy uses Breached Password Protection to scan Active Directory against a list of 3 billion unique weak and compromised passwords. Our research team’s attack-monitoring data collection systems update the service daily to ensure your network is protected from real-world password attacks happening right now. This can all be set up through a simple integration with Active Directory.
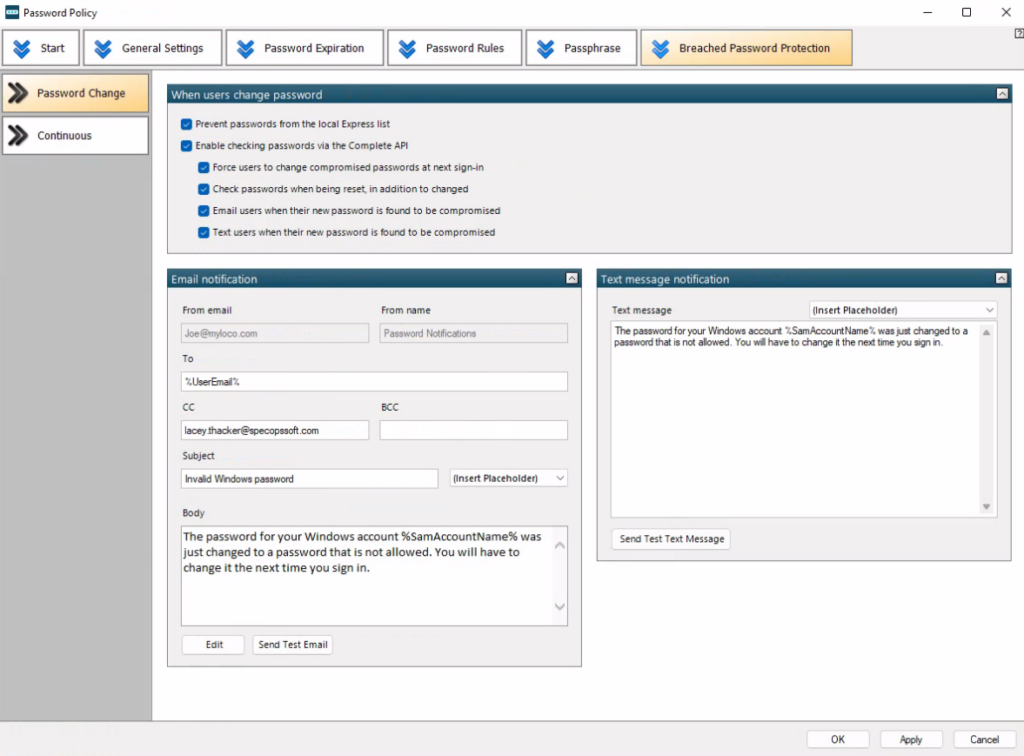
All users will be prevented from using known compromised passwords and guided toward creating a different password that fits your policy. On top of that, if Continuous Scan is activated, users will be alerted by SMS or email as soon as their password has been identified as compromised.
Looking for a simple but effective security tool to rid your organization of breached passwords? Try Specops Password Policy for free today.



