Active Directory vs. Azure AD (and Other Identity Providers)

This article will look at Active Directory (AD), Azure Active Directory (Azure AD), and explain how they differ and can complement each other. We’ll also compare these Microsoft solutions to some of the major alternative identity providers.
This article is not meant to be an exhaustive resource and will not provide step-by-step instructions on how to deploy these services, but Petri has excellent articles which cover those topics.
Windows Server AD vs Azure AD
I think it’s fair to start with the oldest of Microsoft’s current directory services siblings. Active Directory is Microsoft’s on-premises directory service, succeeding Windows NT Directory Services (NTDS), should you be old enough to remember it. NTDS was great at the time but had significant limitations regarding scalability, replication, administration, stability, etc.
Active Directory is widely used by the vast majority of organizations since its release over two decades ago – it was released to manufacturing on 15 December 1999 and reached general availability on 17 February 2000.
Your users are well used to Active Directory without even knowing it: They simply switch on their client devices, enter their username (typically but not always pre-cached) and password, and continue with their daily business activities. Active Directory is straightforward, quick, safe, and secure if you have it all set up and maintained the way you want it.
A central identity provider
Active Directory typically serves as your central identity provider, often spanning multiple forests and domains, some with users and others with only resources. It manages your users and computers (client workstations and servers) but doesn’t natively manage mobile devices or tablets (iOS and Android) or Software-as-a-service (SaaS) apps.
You have to host Active Directory yourself, configure it, maintain it, take care of security, replication, backup, high availability, scalability, etc. It could be a simple two domain controllers (DCs) network, or you could have well over 100 DCs throughout dozens of locations combined with read-only DCs.
Your DCs ideally only run services related to the directory as well as DNS and maybe DHCP. It’s good practice to not run other applications on them like web or database servers, both from a performance and (especially) security point of view. It also helps you with scheduling downtime for reboots.
Active Directory licensing
Unlike its cloud sibling, Active Directory doesn’t have a complex licensing model. You license your domain controllers, always a Windows Server machine and ideally a recent one. As a reminder, Windows Server version 2022 has been released in August 2021.
When hosted in your own data centers or comms rooms, then you could purchase a single Windows Server Datacenter edition which is intended for virtualized data centers since it lets you run unlimited instances on the licensed hardware. Do make sure you research this topic and speak with your licensing specialist, many people get this wrong and inadvertently violate their licensing agreement.
What is Azure Active Directory?
Azure Active Directory is an enterprise identity service that provides single sign-on (SSO), Multifactor Authentication (MFA), and Conditional Access (CA) almost out of the box. To be fair, there is a little bit of configuration work to be done by you (the tenant owner or administrator), but it is much simpler and straightforward to achieve these services in Azure AD compared to hosting them yourself.
Your users will power on their devices, which could either be corporate-owned and managed devices or personal ones if your company has set up a bring your own device (BYOD) policy. Users will then need to enter their usernames and passwords, hopefully, get prompted for an MFA challenge (even an SMS challenge is better than nothing), and whatever you allow them to use will become available to them.
With SSO, they could use an externally hosted app (HR, finance, etc.), access training, and much more without having to enter their credentials every single time. This will improve productivity, security, and user satisfaction. Just the mere fact of your users not having to manage multiple sets of usernames and passwords is a life-saver (take this from a cranky IT guy).
A managed service
A major difference between Active Directory and Azure AD is that the latter is a managed service. You don’t set it up yourself and there are no servers to set up – there are some agents but they are optional to enable specific enhanced functionality. Microsoft hosts and manages it on your behalf.
Azure AD is fully integrated across a number of Microsoft’s cloud services like Office 365, providing you with one central directory for your users and devices. It also makes it easy to collaborate with other tenants and external users.
Azure AD excels in managing mobile devices (there’s native support for iOS and Android) and SaaS apps. It provides great and streamlined integrations with many apps across multiple categories such as business management, collaboration, and finance. Take a look at Microsoft’s Azure Active Directory section in the Azure Marketplace for more examples.

Microsoft offers a free version of Azure AD called Free, but there also are three further editions called Office 365 apps, Premium P1, and Premium P2, with varying differences in feature content and prices. You actually become a Free tier user of Azure AD when you sign up to a number of Microsoft cloud services like Azure, Office 365, Dynamics 365, Intune, and Power Platform.
Case in point, how much time do you as an organization spend on resetting your users’ passwords? The self-service password reset (SSPR) feature alone might be enough to justify the premium license to your finance director. Take a look at Microsoft’s How it works: Azure AD self-service password reset for further details.
Make sure you take a good look at the premium features to determine if you want or need them and if the premium price is worth paying. I am not trying to sell you Microsoft licenses, but given the state of the Internet with almost daily reports of major organizations being hacked (often successfully), paying for these additional features might just keep you in your job and your company out of the papers.
Take a look at Microsoft’s Azure Active Directory (Azure AD) pricing site to get an overview of Azure AD prices, and you can also visit read our Azure Active Directory Premium P1 vs. P2: Features Comparison article to learn more about the different features.
Using Active Directory and Azure Active Directory together
Now that we have covered the two main topics and understand the differences between Active Directory and Azure Active Directory, let’s take a look at how we can best use them together.
Azure AD Connect
Microsoft’s Azure AD Connect allows us to create a hybrid identity by synchronizing objects like users from our on-premises Active Directory to our cloud-based Azure AD.
With password hash synchronization (PHS), Azure AD Connect will also synchronize a hash, of the hash, of your users’ password), enable Pass-through Authentication (PTA), Active Directory Federation Services (AD FS), and more. The setup can be very simple for a small organization and rather involved for a more complex environment.
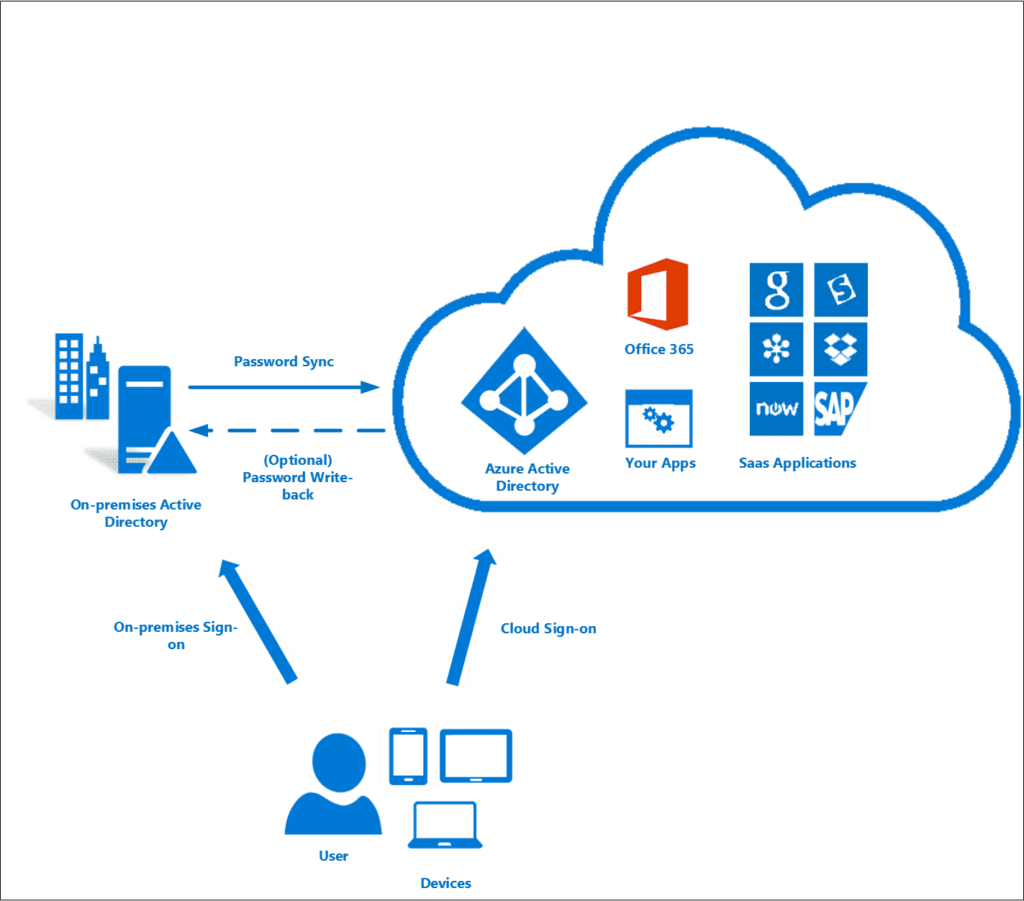
Microsoft is planning to retire versions 1.x of Azure AD Connect on August 31, 2022, and some older versions 2.x of the sync tool are also going out of support in March 2023. You can learn more about which Azure AD Connect versions are currently supported in our separate post.
Active Directory Federation Services (AD FS)
AD FS is an SSO identity service that allows you to share your identity information with partners outside your organization. AD FS uses claims-based access control authentication.
While AD FS is still widely used, especially by more mature and larger organizations, Microsoft nowadays considers it a deprecated service. Just to be clear, Microsoft might not outright call it depreciated but the recent trends certainly support this statement.
AD FS requires a considerable investment and proper planning into on-premises infrastructure, as well as a very impactful reliance on your external partners – if they change a setting (for good, bad, or no reason), it will affect your environment to the point of immediately breaking things). I have successfully used AD FS many times, but nowadays I would not lightly recommend it for a new or existing setup.
Azure Active Directory Domain Services (AADDS)
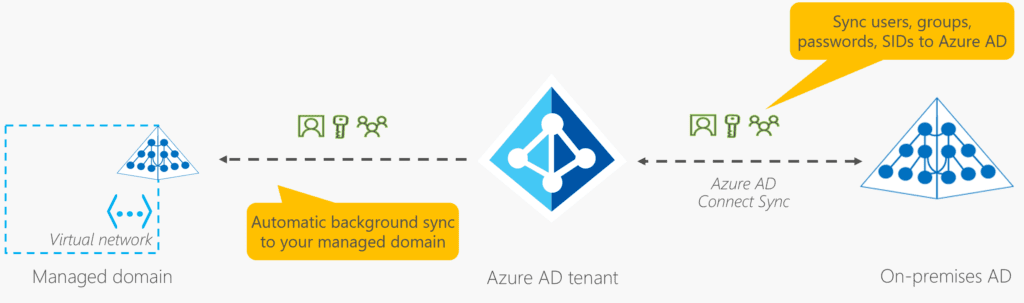
Azure Active Directory Domain Services (AADDS) is Microsoft’s most recent addition to its directory services family. AADDS is Microsoft’s managed Active Directory offering, again fully hosted in its Azure cloud.
One of the main selling points of AADDS is that it allows you to run legacy applications in the cloud that can’t use modern authentication methods. Your old but still critical HR or finance application, loved by your users who know it inside out and are doing their best to resist change, will get another couple of years of use while you prepare a replacement for it. You can lift and shift these legacy applications from your on-premises environment into a managed AADDS domain without needing to manage the domain in the cloud.
There are some limitations compared to running your own Active Directory: Group policies (GPOs) are not synchronized from your on-premises domain to your managed domain. In an established environment, this can be quite a problem since a lot will be handled by GPOs.
The same goes for your organizational units (OUs), they don’t make it across either. Take a look at Microsoft’s How objects and credentials are synchronized in an Azure Active Directory Domain Services managed domain for further information.
Third-party identity providers
Your individual requirements might require you to consider other identity providers aside from Azure AD. You might already use one of them and be perfectly happy with it, or you may prefer to have an additional layer of security. Compliance is also often a reason to separate your identity provider from the rest of your infrastructure.
Using third-party identity providers in combination with Azure AD also works. All major vendors publish integration guides and will be happy to support you with your deployment, especially since it’s in their best interest to keep you as a customer. Some of the major vendors in this space include Okta, PingIdentity, OneLogin, Auth0, ZScaler, and CyberArk.
Conclusion
In the directory services space, Microsoft caters to most if not all possible scenarios. A pure on-premises environment that is slowly but surely becoming a rarity will still work just well with just Active Directory.
Cloud-first organizations with a distributed workforce, empowering their users to connect using their personal or corporate-owned devices and accessing on-prem and cloud-based SaaS resources will be better served with Azure AD. Due to the exposure, this will also require more investment into cybersecurity.
Not one solution fits all needs. A hybrid identity setup between Active Directory and Azure AD will be the most obvious choice for many environments. Last but not least, you shouldn’t dismiss Microsoft’s managed AADDS and all third-party identity providers.
Related Article:



