What is Azure AD Domain Services?

In this article, I explain what Azure AD Domain Services is and how you can use it to simplify deployment of applications and services in the cloud that normally rely on on-premises Active Directory (AD).
Azure AD Domain Services is a cloud-based service provided by Microsoft that enables businesses to utilize Active Directory in Azure. You can use these domain services without needing to deploy, manage, or even patch domain controllers as Microsoft manages them in the cloud (Platform as a Service – PaaS). This allows your users to utilize SSO (Single Sign-On) to manage resources on-premises and in the cloud.
What is Azure AD Domain Services (Azure AD DS)?
The new name for Azure AD Domain Services is Microsoft Entra Domain Services. This is an interesting PaaS (Platform as a Service) offering from Microsoft. The service provides managed domain services you’re used to if you’re familiar with Windows Server Active Directory (AD). Things like domain join, LDAP access, Group Policy, and legacy Kerberos and NTLM authentication.
One of the biggest benefits of this solution is the autonomy you have from needing to install, manage, configure, and maintain Active Directory domain controllers (DCs). Through your paid service, Microsoft handles that as part of the ‘platform’.
In a nutshell, you can think of this as ‘Active Directory Domain Services in the cloud.’ But, there are key nuances and terms you’ll need to be familiar with. Let’s read on for more details.
How does Azure AD Domain Services work?
There is a beautifully simple wizard in Microsoft Entra ID/the Azure Portal that creates a new managed domain for you. You create a DNS namespace (like reinders.com). Two DCs are then created and deployed in the Azure region you select. And for you Azure aficionados, this is a replica set. Again, you don’t need to manage the replica set at all. The Azure platform (Microsoft) handles the DCs including backups and encryption at rest using Azure Disk Encryption.
Azure AD Domain Services replicates identity information from your Microsoft Entra ID tenant. This affords your IT Pros agility in designing the solution because you can utilize Azure AD DS if your company is cloud-only, or synchronized with an on-premises AD DS environment.
Azure AD Domain Services features and benefits
Previously in this article, I wrote about a big benefit of Azure AD DS – the platform taking care of all aspects of maintaining domain controllers. In addition, there are more features and benefits worth pointing out.
Domain Services is fully compatible with a traditional AD DS environment for things like domain-join, secure LDAP (LDAPS), DNS management, Group Policy management, and various forms of LDAP. These features provide identity services to applications and virtual machines (VMs) you have in your Azure space.
Simplified deployment
As I mentioned above, Microsoft Entra provides a single wizard in the Microsoft Entra admin center to deploy Domain Services.
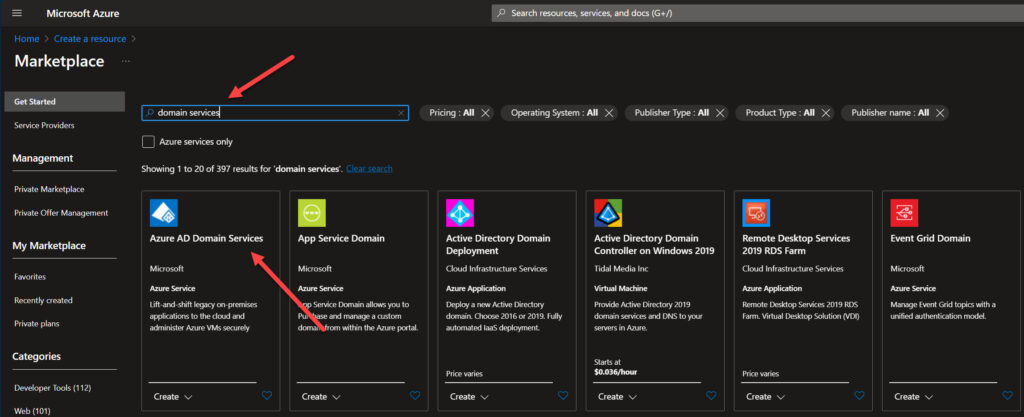
- In the Azure Portal (home), simply click the ‘Create a resource’ link.
- Then search for ‘Domain Services.’
Integration with Microsoft Entra ID
All of your user accounts, credentials, and group memberships are automatically synchronized from your Microsoft Entra tenant. When you add users and groups to your Microsoft Entra ID tenant, they are automatically kept in sync with Domain Services.
Single Sign-On (SSO)
Passwords for your users in Domain Services are the same as in your Microsoft Entra ID directory. Your users can seamlessly domain-join devices with their corporate credentials. They can also remote desktop to machines and authenticate against the managed domain (AD).
Maintain legacy protocols and applications
With support for NTLM and Kerberos authentication, your IT Pros can deploy applications that rely on these legacy protocols. This lets your organization ‘go all in the cloud’ from the ground up.
Limitations of Azure AD Domain Services
There are some very important limitations of Azure AD Domain Services. Let me mention a few and offer some advice.
- No Domain Admin or Enterprise Admin rights. Yep, you won’t have accounts with these specific permissions. This would prevent you from deploying on-premises Exchange Server for example.
- No Geo-distributed deployments. Your managed Azure AD DS is limited to the virtual network from which you deployed it.
- You only have access to a single domain. You won’t be able to use additional domains or forests. You can only use the single forest root domain.
Comparing Azure AD Domain Services with on-premises Active Directory and Microsoft Entra ID
This all started with Active Directory. Then came along Azure Active Directory (AAD), which is now called Microsoft Entra ID. Soon after Microsoft launched AD as a Platform as a Service in Azure, which is called Azure AD DS and then renamed it to Microsoft Entra Domain Services.
How do you keep track of these behemoths, their name changes, and their features and differences from each other? Keep reading, I’ll give it a whirl.
How does Azure AD Domain Services differ from Active Directory?
As previously written, Azure AD DS/Microsoft Entra Domain Services is a managed platform service in Azure that offers a subset of features from Active Directory. Microsoft takes care of deploying and maintaining the overall infrastructure of AD and the domain controllers.
However, to be able to manage this for thousands and thousands of customers, some features are missing in Microsoft Entra Domain Services, namely additional domains, forests, sites, and replication.
The other big difference is who maintains the Active Directory infrastructure – domain controllers. With Active Directory, you need to manage the entire stack. With Azure AD DS, Microsoft handles all of it.
This table provided by Microsoft gives you a quick overview of the most common differences IT Pros and security officers will want to be familiar with.
| Feature | Managed domain | Self-managed AD DS |
|---|---|---|
| Managed service | ✓ | ✕ |
| Secure deployments | ✓ | Administrator secures the deployment |
| DNS server | ✓ (managed service) | ✓ |
| Domain or Enterprise administrator privileges | ✕ | ✓ |
| Domain join | ✓ | ✓ |
| Domain authentication using NTLM and Kerberos | ✓ | ✓ |
| Kerberos constrained delegation | Resource-based | Resource-based & account-based |
| Custom OU structure | ✓ | ✓ |
| Group Policy | ✓ | ✓ |
| Schema extensions | ✕ | ✓ |
| AD domain / forest trusts | ✓ (one-way outbound forest trusts only) | ✓ |
| Secure LDAP (LDAPS) | ✓ | ✓ |
| LDAP read | ✓ | ✓ |
| LDAP write | ✓ (within the managed domain) | ✓ |
| Geo-distributed deployments | ✓ | ✓ |
How does Azure AD Domain Services differ from Microsoft Entra ID?
Despite similar nomenclature, these two platforms are very different. Microsoft Entra ID acts as the directory service for all things Microsoft 365 and all of your users’ cloud-based work. Azure AD Domain Services is a platform that provides most of your Active Directory needs in a cloud-based service.
Let me mention some more differences here.
- The lack of Group Policy and OUs in Microsoft Entra ID.
- Microsoft Entra ID is a flat, single-domain model. Although with Azure AD DS you only have the option for a single domain, the underlying infrastructure is fundamentally based on different designs.
- Azure AD Domain Services supports traditional authentication methods as Active Directory does, like NTLM and Kerberos. Microsoft Entra ID supports more modern methods like OAuth 2.0 and OpenID Connect.
- Microsoft Entra ID can be integrated with on-premises AD using Microsoft Entra ID Connect software. Azure AD DS can be integrated with on-premises AD, allowing you more consistency between environments.
Options and recommendations
Up to this point, I’ve given an explanation and overview of the three main services I’ve described in this article. Plus, ‘hybrid’ takes on a very interesting meaning when discussing the marrying of any two of these technologies to build one heterogeneous framework for your network and identity needs. But what is the best solution? Well, certainly, no size fits all.
Your organization undoubtedly has specific user needs, data retention needs, security and compliance needs, etc. Even though no one recommendation here will work for everyone, let me do my best.
- Use Active Directory if you have an existing on-premises infrastructure and have shied away from cloud adoption at this point (really, you should seriously start considering…). Also, if cost is a strong concern, choose AD.
- Use Microsoft Entra ID if you primarily use cloud-based applications and resources, need a scalable and secure identity management environment, or already utilize Microsoft 365 and Azure services and applications.
- Use Microsoft Entra Domain Services if you need to migrate existing applications to the cloud, want a hybrid identity management solution with full AD functions, and are willing to invest in a Platform as a Service solution, with its required operational costs.
Azure AD Domain Services pricing
Speaking of costs, let me give you a quick overview of Microsoft Entra Domain Services pricing. This table is provided by Microsoft and illustrates their three main pricing levels based on the size of your company and overall usage requirements and expectations.
More reading on Petri.com: How to Set Up Azure AD Domain Services
| Not available | Standard | Enterprise | Premium |
|---|---|---|---|
| AAD DS Core Service | |||
| Suggested Auth Load (peak, per hour) | 0 to 3,000 | 3,000 to 10,000 | 10,000 to 70,000 |
| Suggested Object Count | 0 to 25,000 | 25,000 to 100,000 | 100,000 to 500,000 |
| Backup Frequency | Every 5 Days | Every 3 Days | Daily |
| Instances | |||
| Managed domain | $0.15/hour/set | $0.40/hour/set | $1.60/hour/set |
| Features | |||
| Replicas | Not available | Available | Available |
| Extra sync options | Not available | Available |
Conclusion
As you can see, the three main Microsoft options are a little challenging to understand, if nothing else. Understanding key terms and vocabulary is paramount.
More reading on Petri.com: How to Synchronize Password Hashes Between AAD and Domain Services
Your current state has a lot to do with what your options are in this space. Many customers use a hybrid approach joining Active Directory with Azure AD/Microsoft Entra ID. Probably the most logical future is to migrate your Active Directory to Microsoft Entra Domain Services. You would completely free yourself from logging into a domain controller ever again, on paper.
I welcome any comments or questions in the form below. Thank you for reading.
Table of contents
- What is Azure AD Domain Services (Azure AD DS)?
- How does Azure AD Domain Services work?
- Azure AD Domain Services features and benefits
- Limitations of Azure AD Domain Services
- Comparing Azure AD Domain Services with on-premises Active Directory and Microsoft Entra ID
- Options and recommendations
- Azure AD Domain Services pricing
- Conclusion



