How to Synchronize Password Hashes Between AAD and Domain Services
In the second part of this two-part series, I show you how to synchronize password hashes between AAD and Domain Services, and how to join a Windows Server VM to the new domain.
Synchronize Password Hashes
Before you can use Domain Services with your AAD user accounts, password hashes must be synchronized between AAD and Domain Services. In this example, I’m going to assume that you have cloud-only users in AAD. Cloud-only users must change their passwords to synchronize password hashes to Domain Services. Users can change their account password in the Azure AD Access Panel if self-service password resets are enabled in AAD. This feature requires AAD Premium licenses.
If you want to force a password change for an existing user, you can do so in the Azure management portal by clicking Reset password in the Profile pane for the user. You will be provided with a temporary password for the account which you must give to the user. They will be required to change it at the next logon. But if you would like users to change their own password, give them the following instructions.
- Log in to the AAD Access Panel.
- Click the profile in the top right of the Access Panel and then click Profile in the menu.
- Under Manage account, click Change password.
- On the change password page, type the old account password, and then type and confirm a new password for the account.
- Click submit.
You should wait 30 minutes before logging in to AAD Domain Services using the account.
Create a VM for AAD Domain Services Management
Once AAD Domain Services is set up and you have at least one account that can access it, managing the domain is much like managing any other Windows Server Active Directory domain. All you need is a VM that can connect to the domain’s subnet and the right tools, like the PowerShell module for Active Directory or the Remote Server Administration Tools (RSAT). The easiest way to get started is to deploy a Windows VM in Azure. There are a few requirements:
- It must be on the same VNET as your AAD Domain Services, or a VNET that is connected to your AAD Domain Services subnet.
- Should be on a different subnet from Domain Services.
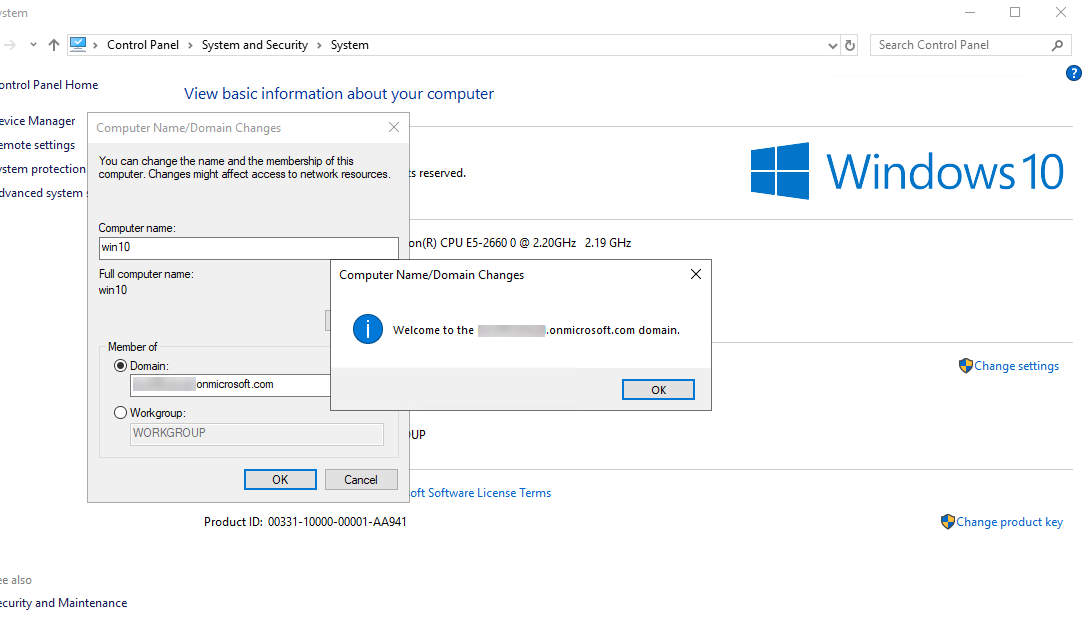
You can join a Windows VM to Domain Services in the same way that you join a device to Windows Server Active Directory. Use the instructions in Joining Windows Server 2012 to a Domain on Petri, skipping straight to the section ‘Join the computer to a domain’. This works for newer versions of Windows Server as well. You will need the fully qualified domain name (FQDN) of your Domain Services domain that you entered as part of the instructions in the first part of this series and a user account that is a member of the AAD DC Administrators group. The AAD DC Administrators group is added to the local Administrators group as part of the domain-join operation.
If you don’t already have a Windows Server VM running in Azure, you can provision one using the instructions in Create a Virtual Machine in the Azure Cloud on Petri.
For example, if your Domain Services FQDN is petriad.onmicrosoft.com and you have a user called ‘admin’ that is a member of the AAD DC Administrators group, when you are requested for a username and password, just type admin as the username and then whatever the password is for the admin account. You will be required to restart the VM to complete the domain-join operation.
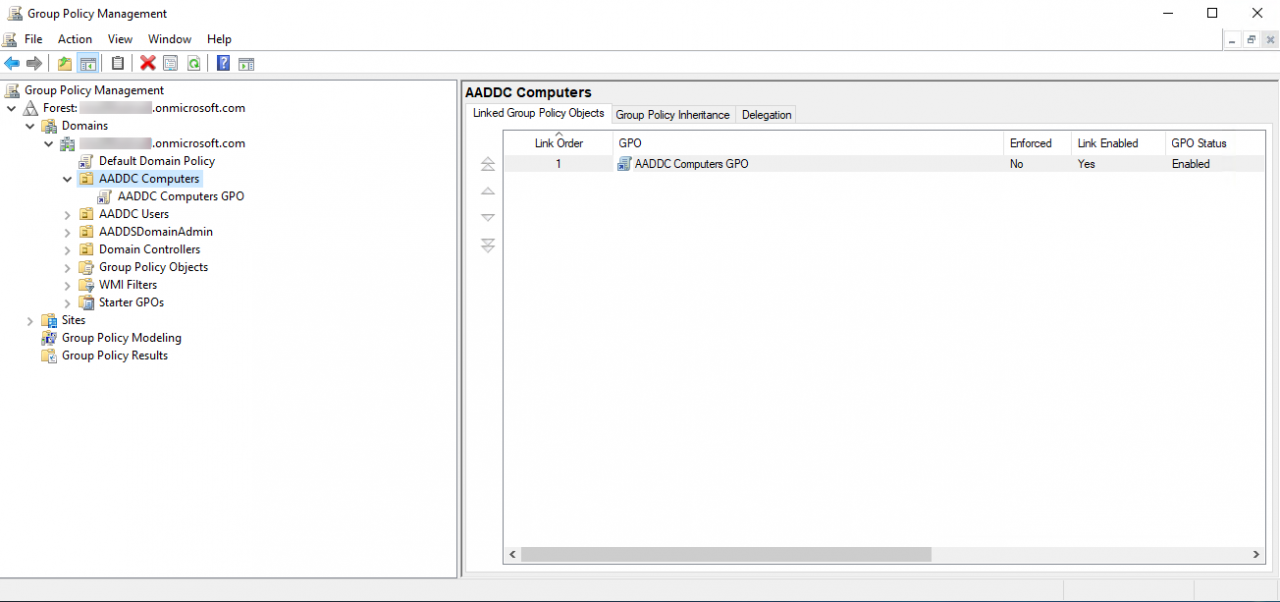
After rebooting, log in to the VM using an account that is a member of the AAD DC Administrators group. You can then use any standard tools, like Group Policy Management, to manage Domain Services. For more information on working with RSAT, see How to Install the Remote Server Administration Tools in Windows 10 on Petri.




