Securing Azure Virtual Desktop with Azure Active Directory Conditional Access

Azure Virtual Desktop (AVD) is a Platform-as-a-Service (PaaS) to provide access to Windows 10 and Windows 11 desktops and applications virtually anywhere. It’s a solution hosted by Microsoft, which makes it secure by design, even though there is a lot of responsibility on the customer to ensure services are secure. In this article, I will explain how to secure Azure Virtual Desktop by focusing on Identity Access Management (IAM), which can be achieved using Azure Active Directory Conditional Access policies.
Security Aspects of Azure Virtual Desktop
In a traditional virtual desktop infrastructure (VDI) environment, for example, Windows Server Remote Desktop Services (RDS), which is hosted on-premises, ensuring that the RD Gateway and RD Broker services are secure can be challenging. And it requires additional infrastructure and configuration.
Security services and responsibilities
With Azure Virtual Desktop, this is all taken care of, which makes it secure by design. However, the following table shows the security services within AVD that are still the responsibility of the customer:
| Security Service | Responsibility |
| IAM (Identity Access Management) | Customer |
| Devices | Customer |
| Application Security | Customer |
| Deployment | Customer |
| Session Host Operating System | Customer |
| Network management | Customer |
| Physical Hosts | Microsoft |
| Physical Network | Microsoft |
| Access to Datacentre | Microsoft |
| Control Pane | Microsoft |
Before I explain how to use Azure AD Conditional Access to secure Azure Virtual Desktop, I want to highlight other security aspects of AVD.
Securing the Azure native services used by Azure Virtual desktop
To secure Azure Virtual Desktop, you’ll need to secure the Azure native services it uses such as Azure virtual machines, Azure Storage, and Azure Virtual Network (VNet)
- Azure virtual machines: AVD is generally used with Windows 10 installed on session hosts, which means we can use any number of third-party endpoint protection tools. Microsoft Defender for Endpoint fully integrates with Windows 10, which means you can use it to protect the session hosts at the OS level.
- Azure Storage: Managed disks and Azure File shares are used with Azure Virtual Desktop. We can protect managed disks by encrypting them, and we can protect Azure file shares by locking down network access and ensuring we back up the data that is stored on them.
- Azure Virtual Network (VNet): We can protect virtual networks by ensuring we do not create unnecessary inbound rules to session hosts, as well as implementing an Azure Firewall or network virtual appliances (NVAs) in front of the VNet as perimeter network security.
- Identity: We will discuss this as part of securing AVD with Conditional Access later
Let’s move on to discussing Conditional Access and how we can protect Azure Virtual Desktop by using Identity and Access Management.
Conditional Access policies overview
In essence, Conditional Access policies are if/then statements. So, if someone wants to access a resource or application, then they need to complete an action. This article focuses on an example where if a user wants to access Azure Virtual Desktop, then they are required to do multifactor authentication (MFA) before they can access it.
The following diagram shows the different aspects of Conditional Access including signals, verification, and the apps to which the user needs access:
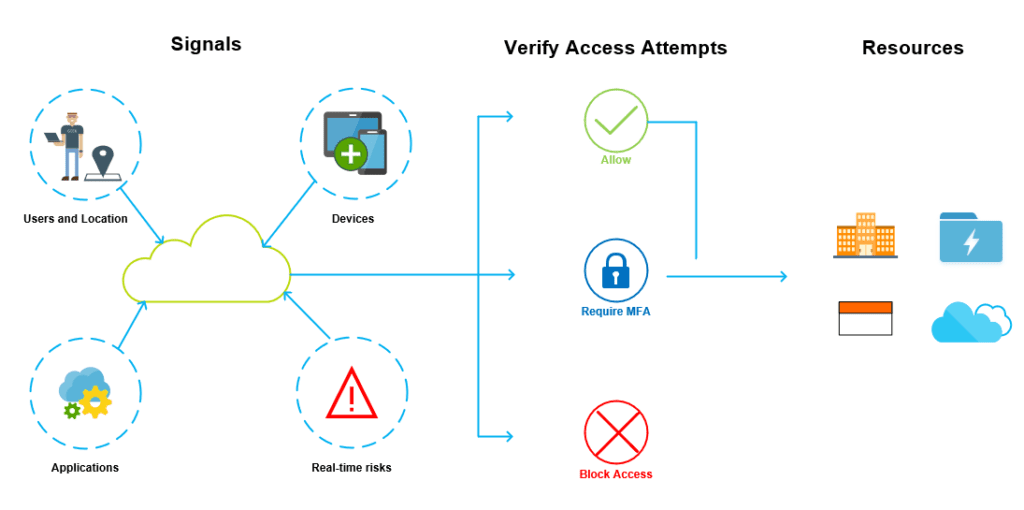
As you can see in the diagram, from a Conditional Access aspect, users and locations, devices, applications, and real-time risk are referred to as signals. These signals allow access to resources within a cloud tenant. However, access needs to be verified.
Conditional Access will then either allow access, force the users to complete an MFA check, or block access. We can use Conditional Access policies to secure and control access to Azure Virtual Desktop in the same way, and we will discuss this in more detail now.
Securing Azure Virtual Desktop with Conditional Access
Before you can implement Conditional Access with Azure Virtual Desktop, you need to ensure the following prerequisite tasks are completed.
Assign the relevant license to the users (Azure AD P1 or P2)
Conditional Access can be implemented in certain scenarios with the free Azure Active Directory basic license. However, a premium Azure AD license is required for Azure Virtual Desktop integration. If you have an existing subscription that includes AVD such as Microsoft 365 Business Premium, the Azure AD Premium license is included.
Create an Azure Active Directory security group to which you can add your users
When you’ll create the Conditional Access policy, you’ll need to assign it to a user or group. Microsoft recommends assigning a security group to Conditional Access Policies as it is less management overhead.
Enable MFA for your Azure Virtual Desktop users in Azure Active Directory
Once the appropriate licensing is in place and users have been added as members of the relevant security group, you’ll need to ensure that MFA is enabled on our user accounts within Azure AD.
Configuring Conditional Access to secure Azure Virtual Desktop
Now that you have all the prerequisites in place, you can go ahead and configure your Conditional Access policy to force users to use MFA when connecting to Azure Virtual Desktop. However, you should consider the following key points.
Apply the policy to the relevant apps
As part of enforcing users to complete MFA verification when accessing Azure Virtual Desktop, you can also configure whether it applies to the web client, mobile apps, desktop clients, or all clients. As there are multiple methods to connect to AVD including web browsers, mobile apps, and desktop clients, it makes sense to configure all clients as part of your Conditional Access Policy.
Specify the frequency of re-authenticating
As part of the MFA configuration, you can specify how often users need to re-authenticate with MFA after the initial authentication. The default value for this is 14 days, however, you can set this to as low as 1 day and as high as 365 days.
Exempt specific network locations
Lastly, you can configure MFA to exempt specific CIDR IP ranges if you have corporate offices where your organization trusts the network, in case you don’t want users to authenticate with MFA.
Summary
In this article, we explained how to secure Azure Virtual Desktop with Conditional Access, which requires the creation of an Azure Active Directory security group and the configuration of multi-factor authentication for your users. Once your Conditional Access policy has been created, it will be quite straightforward to force your users to use MFA when connecting to Azure Virtual Desktop.



