How to Setup a Microsoft Azure Virtual Network
Alongside its platform and infrastructure as a service offerings (IaaS), Microsoft Azure comes replete with custom networking tools that make it simple to set up a virtual network and cross-boundary connections between the Microsoft datacenter and you. In this article, I’ll show you how to setup a Microsoft Azure virtual network and talk about the new Azure point-to-site and site-to-site VPN.
Microsoft Azure Virtual Networks
Virtual networks are just that—a virtual, logical path that you can configure within your Microsoft Azure account that runs on top of the physical network in Microsoft’s data centers.
Virtual networks run IP only. IP address assignment is handled by DHCP, where static IPs are not supported. You would want to create an Azure virtual network for three main reasons:
- Customizing the IP numbering scheme used instead of accepting the default IP numbering from Microsoft, which is useful if you have an overall address corpus and want to use IP address management tools.
- Segregating services among virtual machines that run different tiers of a service, such as web and middle tiers.
- Enable virtual private networks between either a single computer on your own network or your entire on-premises network, and the Microsoft Azure data center network.
Setup a Microsoft Azure Virtual Network
Creating virtual networks is pretty simple:
1. Open the Azure management portal.
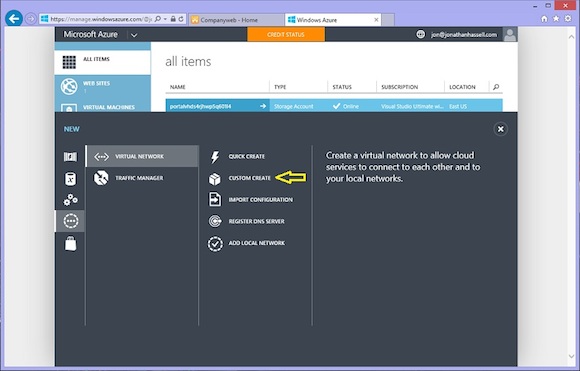
2. From the New menu, under Network Services, choose Virtual Network.
3. Click Custom Create (see below).
Creating a new virtual network in Microsoft Azure. (Image: Jonathan Hassell)
4. On the Virtual Network Details page, enter a friendly name and the service region where this virtual network should be established. Click Next.
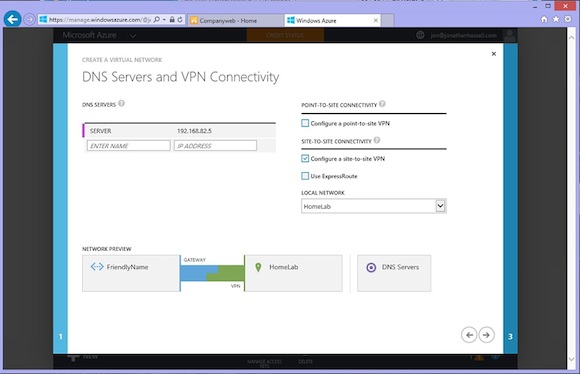
5. On the DNS Servers and VPN Connectivity screen, enter the information for any virtual machine that will be hosted on this virtual network. This is essentially like filling out a DHCP scope with options. You can leave it blank, and Azure will handle DNS, but if you want to create VPNs, then you should enter the IPv4 addresses of your on-premises DNS servers. You can also click the check boxes to configure either point to site or site-to-site VPNs. More on those later, so click Next.
The Microsoft Azure DNS Servers and VPN Connectivity screen. (Image: Jonathan Hassell)
6. The Virtual Network Address Spaces page appears. This is where you determine the IP numbering scheme you will use. You can use any of the private spaces you like. By default, Azure will give you 10.0.0.0/8 and automatically will build in a 10.0.0./11 subnet for future use. Click Next.
7. You’re done. Now you can create virtual machines as you see fit and assign them to this virtual network.
Tip: Be careful! It is very difficult and in most cases impossible to change properties of virtual networks and to reassign virtual machines attached to one virtual network to another virtual network. Additionally, you have to create virtual networks prior to spinning up new virtual machines. This is because you cannot attach an existing virtual machine to a new network. So plan diligently and double-check your setup before committing. Otherwise you may have to start over if you make a mistake.
Microsoft Azure Point-to-Site VPN
About a year or so ago, Microsoft introduced point-to-site VPN connectivity to Microsoft Azure, which essentially means individual computers can create VPN connections directly into the Microsoft Azure data center. The computer can then access virtual machines, databases, websites and other resources as if they were on the network local to the individual computer.
Why would you want to use a point-to-site VPN? If you are a developer or an IT pro that is looking to build out a lab environment or a testing virtual machine within Microsoft Azure, then you can use the point-to-site VPN to have a single network that frees you from worrying about addressing problems, DNS and other issues that crop up when moving a solution that’s hosted on one network to another.
It is also a cinch to set up: You can simply download a connectoid packet right from the Microsoft Azure management portal and double click on it to create the connection, which is secure by default.
The VPN client included in the box with Windows 7 and 8 works just fine, and no other configuration or hardware devices are needed to create the VPN connection. It is a quick and dirty method to get connection from, say, one PC you are using on your desk to a virtual machine that is hosted up in Microsoft Azure.
To do point-to-site VPNs correctly, follow the steps in the first section of this article. However in step 5, click the point-to-site VPN checkbox. Next, the Point-to-Site Connectivity screen appears. You can configure the address space that the VPN will use. Azure automatically adds a 10.0.0.0/24 space, which gives you 254 potential addresses for your on-premises endpoint to use. Click Next, and follow the rest of the wizard as it appears.
Microsoft Azure Site-to-Site VPN
A site to site VPN in Microsoft Azure lets you set up one network that connects your on-premises network with a virtual network within Microsoft Azure. It uses the public Internet as the transport medium in between the two locations. Once you have set up a site-to-site VPN, you can host virtual machines in the cloud numbered in the same scheme connected to the same network as your on-premises servers.
You can host a domain controller in Azure to provide fault tolerance, and you can export and import VMs to your heart’s content. This essentially makes Azure a large extension to your existing datacenter that you control.
Setting these up takes some doing, so we will cover site to site VPN configuration in an upcoming Petri IT Knowledgebase article.