Microsoft’s New Authentication Strength Feature Provides More Control Over CA Policies

Microsoft has announced the general availability of Conditional Access authentication strength policies for Azure Active Directory (Azure AD). The new feature allows IT admins to choose which multifactor authentication (MFA) methods can be used while accessing network resources.
Multifactor authentication (MFA) is a security feature that allows customers to use two or more methods of verification to prove their identity and gain access to a system. It helps to protect users against cyberattacks such as password guessing and credential theft.
How does Conditional Access authentication strength work?
Azure Active Directory’s Conditional Access feature already lets organizations enforce specific access controls based on predefined conditions to protect data and resources. The Authentication Strength feature provides an additional level of protection by allowing IT Pros to mention the type of MFA methods that should be used.
“With Conditional Access authentication strength, administrators can define a minimum level of authentication strength required for access, based on factors such as the user’s sign-in risk level or the sensitivity of the resource being accessed. This can be especially useful for organizations that operate in highly regulated industries or have strict compliance requirements,” Microsoft explained.
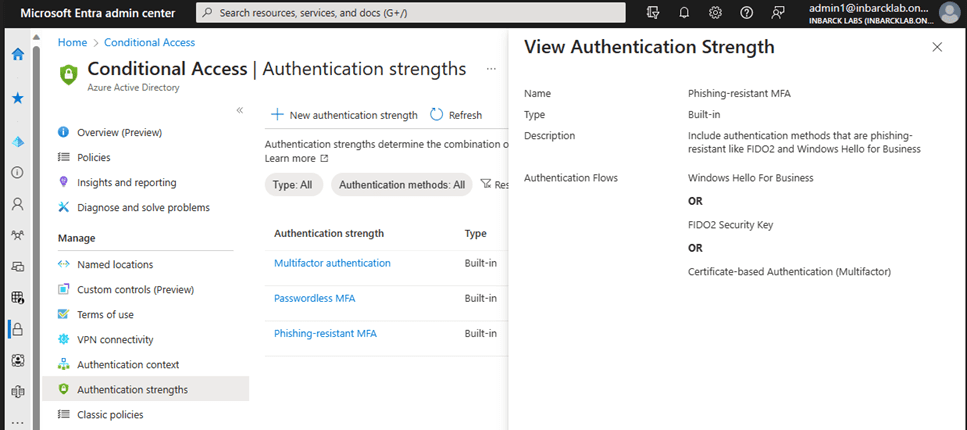
Microsoft notes that customers can choose between three built-in Authentication Strength methods such as Temporary Access Pass or password. They can also choose to set up custom authentication strength policies based on specific needs.
- MFA strength: It’s the set of combinations (like Microsoft Authenticator and Certificate-based authentication) that could be used to meet the “Require multifactor authentication” setting.
- Passwordless MFA strength: It supports authentication techniques that don’t require a password but satisfy the MFA requirements.
- Phishing-resistant MFA strength: It’s a set of techniques that require communication between the sign-in surface and the authentication method. For example, the FIDO2 security key and Windows Hello for Business.
Conditional Access authentication strength requirements
The authentication strength feature could help organizations to address various scenarios. For instance, a user needs to access an application or take sensitive action within the app. Moreover, IT admins can configure the feature to let guest users securely access the resource tenant.
Microsoft notes that IT admins will have to purchase an Azure AD Premium P1 license to use Conditional Access within their organization. Customers will also need to configure combined MFA and SSPR registration. This capability is already in place for all Azure AD tenants created before August 15th, 2020.


