
Azure Bastion native client support provides a secure way to log into Windows and Linux virtual machines (VMs) using the Remote Desktop Protocol (RDP) or Secure Shell (SSH). There’s no need to expose the VMs to the Internet, or even to your network. That means you can “air gap” the virtual machines to prevent zero-day vulnerabilities in remoting protocols from being attacked by compromised networks.
In this post, you are going to learn how to log into Azure virtual machines with the native Windows RDP client through Azure Bastion.
How to use Azure Bastion native client support to log into virtual machines with the Windows RDP client
- Log in to Azure using the Azure CLI so you can access Azure Bastion native client support.
- Launch the native Remote Desktop client using the az network bastion rdp command as shown below to connect to virtual machines in the same virtual network as Azure Bastion.
az network bastion rdp –name “<BastionName>” –resource-group “<ResourceGroup>” –target-resource-id “<VM Resource ID>”
Keep reading if you want more details about how to use Azure Bastion with the Windows RDP client to log into Azure VMs.
Why you need the new Azure Bastion Standard SKU
Our own Russell Smith previously wrote a post about securing remote virtual machines using Azure Bastion. The technology has improved quite a bit since it first launched, with added support for hub-and-spoke network designs to allow the reuse of potentially expensive resources.
Azure Bastion Standard, a new tier with additional features, including session management, was also added. Moreover, Azure Bastion Standard added the ability to log into machines using native remote desktop (or SSH) clients instead of connecting through the Azure Portal.
Azure Bastion Standard is required to use the native Windows RDP client. The higher cost of Azure Bastion Standard implies that you will deploy Bastion as a shared resource, rather than as a workload-specific resource.
You can find more details about Azure Bastion in the support pages below:
- Using Azure Bastion in a Virtual Network-based hub
- Using Azure Bastion with Azure Virtual WAN hubs
- Azure Bastion pricing table
Enabling Remote Desktop client support
Adding support for the native desktop RDP client was probably one of the biggest feature requests when Azure Bastion was first released. Developers and operators did not want to log into their machines through the Azure Portal.
Support for the native Remote Desktop client brought the following new features:
- A more familiar client experience.
- Support for copy/pasting text, images, and files, as long as copy/pasting support is enabled by the Azure Bastion administrator.
- A secure login process to Azure Bastion that’s managed by Azure Active Directory.
If you want to support native RDP (or SSH) clients, then you must alter the configuration of your Standard (required) tier for Azure Bastion. The follow instructions assume that you already have a Bastion host configured and that you have a Windows VM located in the same virtual network as the Bastion host.
- Log into the Azure Portal.
- Open the Azure Bastion resource and browse to Configuration.
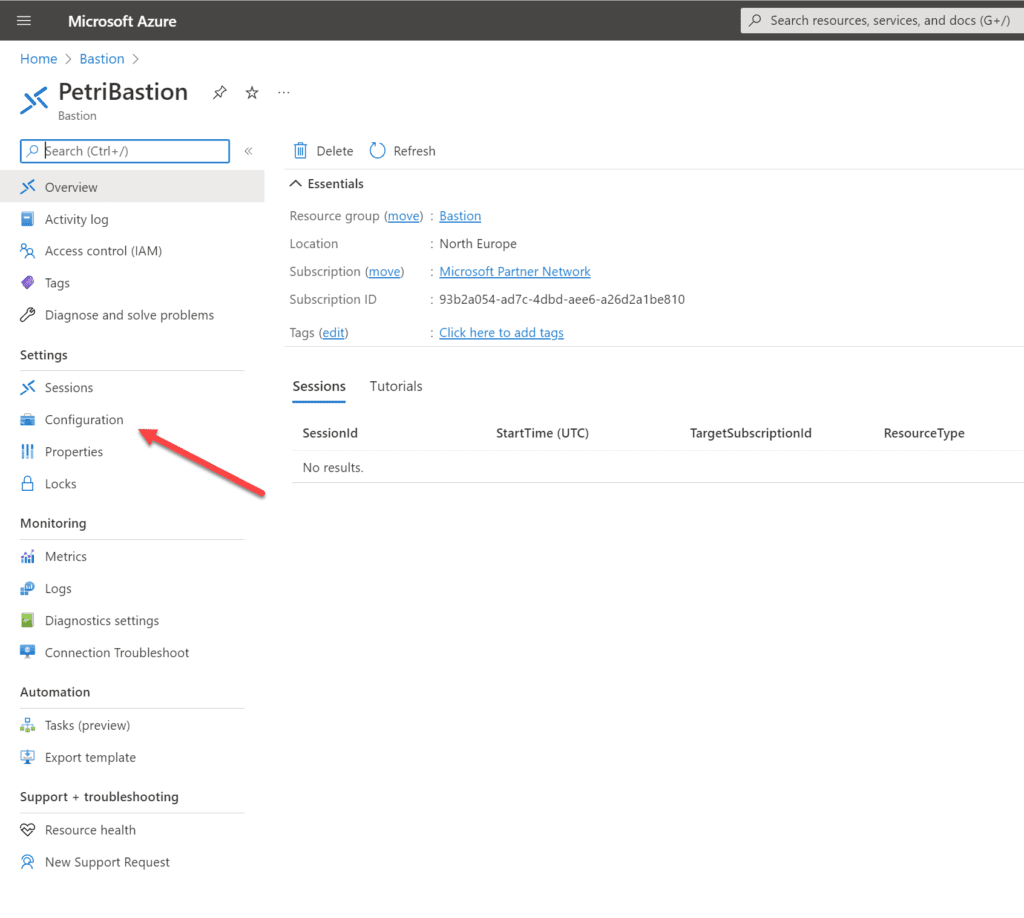
- Enable Native Client Support to allow connections by RDP or SSH native clients.
- Optionally, you can enable copy and paste actions in all sessions handled by this Azure Bastion resource.
Once those actions are completed, developers and operators can log into virtual machines using their Windows RDP client.
Logging in using the Remote Desktop client
Before you attempt to log in, you will need to:
- Install the latest version of Azure CLI on your PC. You can find instructions on how to do that on this page.
- Open the Azure Bastion in the Azure Portal and copy the resource name. You can see in the image below the resource group name and Bastion name configured in my Azure tenant.
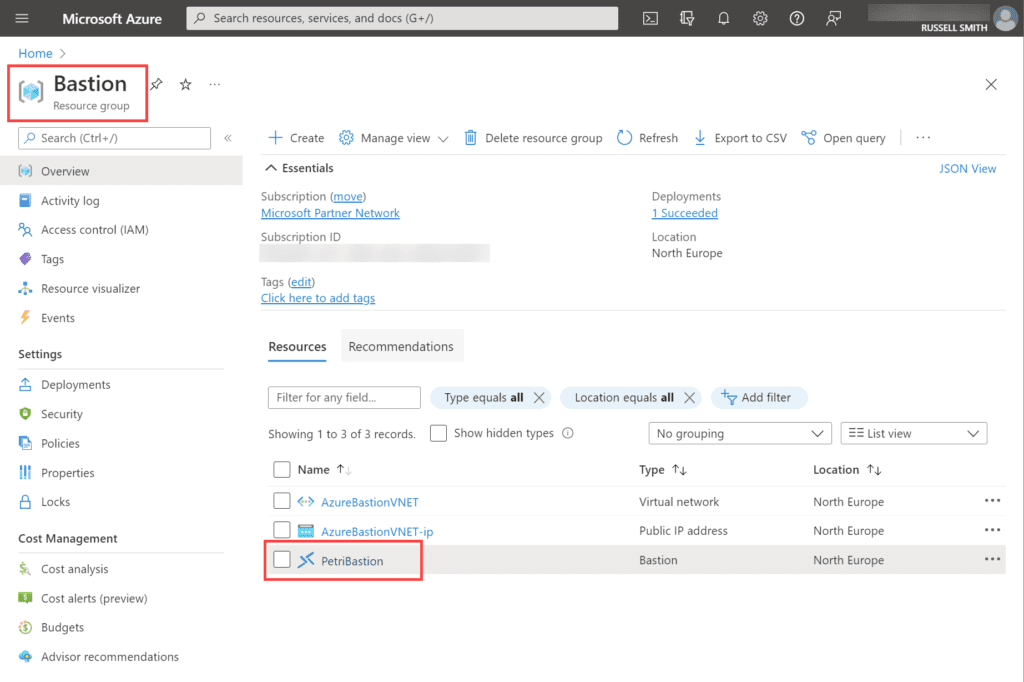
- Get the name of the resource group that contains your Azure Bastion. See the image above.
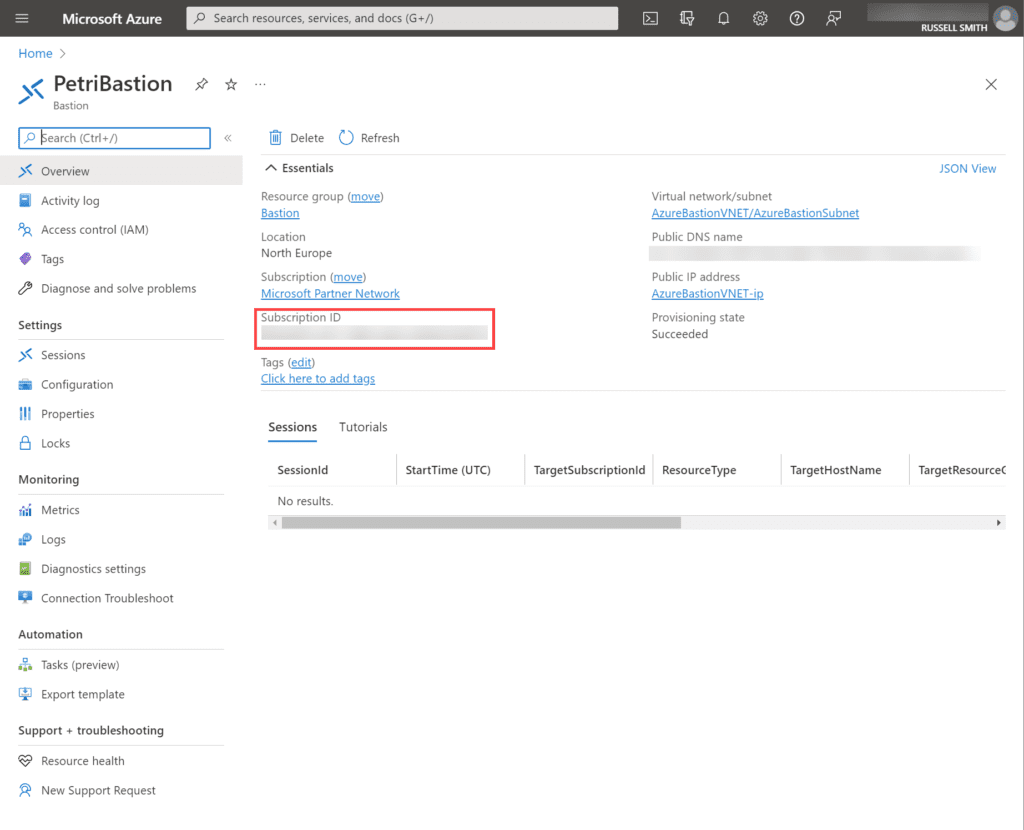
- Get the name of the subscription that contains your Azure Bastion. You can get the subscription ID for your Bastion by clicking the Bastion name, as show in the image above. In the Overview section for your Bastion host, you will find the subscription ID where the bastion host is located. See the image below.
- Get the resource ID of the virtual machine that you want to log in to. You can find the resource ID for the VM by going to the VM in the Azure portal and then clicking JSON Overview. It will take you to the page show below, where you can copy the VM’s resource ID.
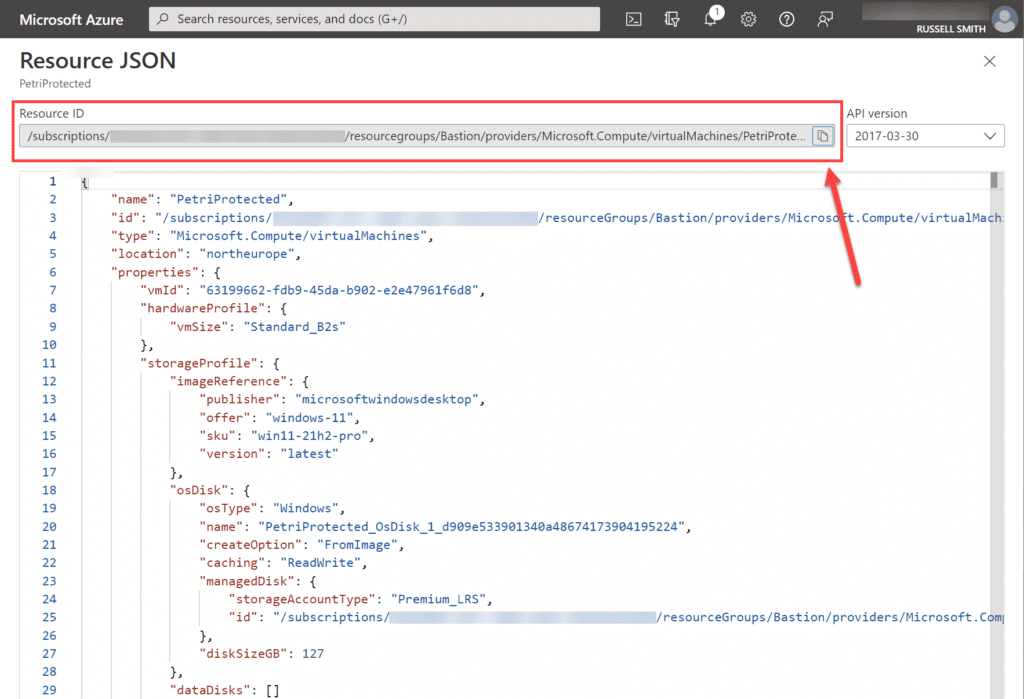
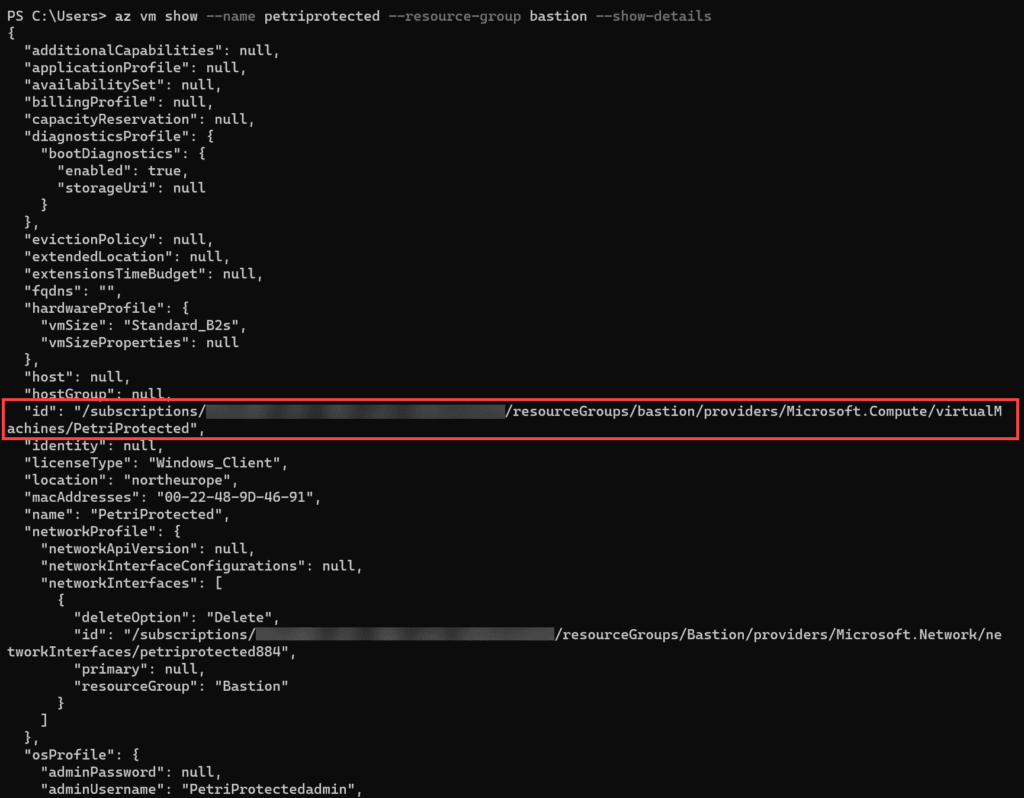
- Alternatively, you can get a VM’s resource ID using Azure CLI and the following command, replacing ‘petriprotected’ with the name of your VM, and ‘bastion’ with the name of the resource group where your VM is located:
az vm show –name petriprotected –resource-group bastion –show-details
On your PC:
- Log into your Azure tenant using the Azure CLI – this will log you in via Azure AD, including any security mechanisms provided by Azure AD such as multifactor authentication (MFA). In this example, I will use Windows Terminal and a PowerShell tab to log into Azure using the Azure CLI.
Error 13 ‘az network’ Permission Denied (conn.rdp)
It’s important that you run Windows Terminal as an administrator, otherwise the ‘az network bastion rdp’ command will fail with a permissions error. This might be a bug but that’s been my experience at the time of writing.
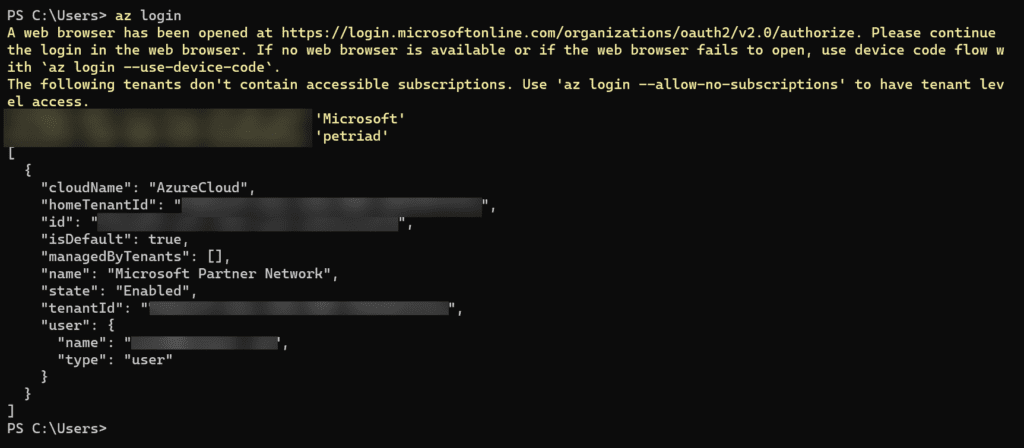
Log in to Azure using the Azure CLI and set the working subscription
Before you can launch the RDP client, you’ll need to log into your Azure tenant and choose a subscription.
az login
- List the Azure subscriptions that are available to you. Note that if you only have one subscription in your Azure tenant, you can skip listing and setting your subscription in Azure CLI. Go straight to launching the native RDP client below.
az account list
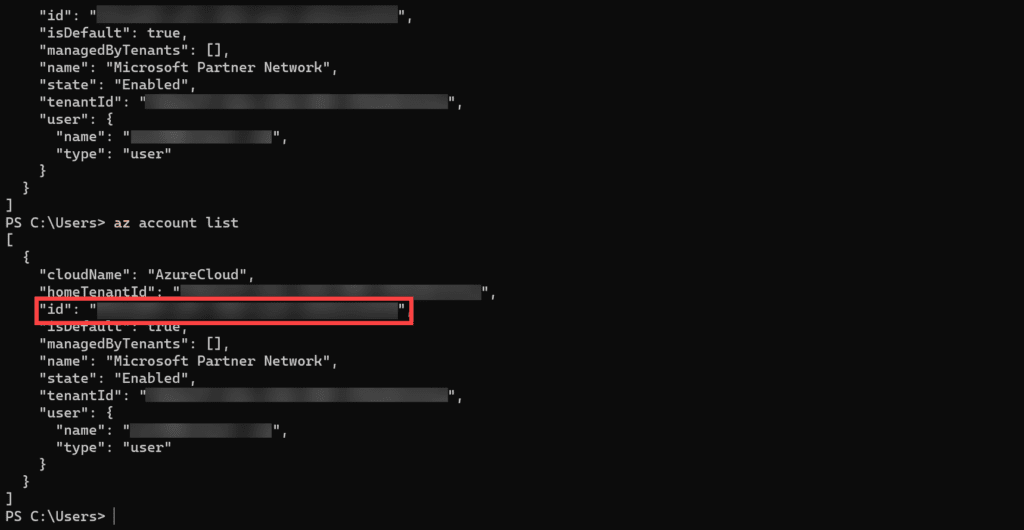
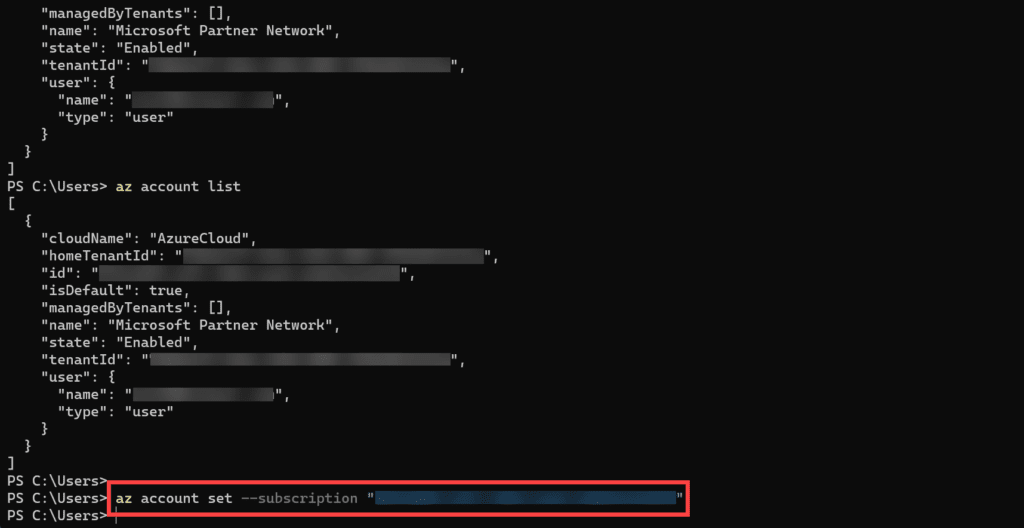
- Find the ID of the subscription that contains your Azure Bastion resource and select that subscription. I only have one subscription in my Azure tenant but I will set it anyway using the command below.
az account set --subscription "<subscription ID>"
Launch the RDP client using Azure CLI
Now let’s start the native Windows RDP client using Azure CLI.
- Launch the RDP client, replacing the variables for $BastionName, $BastionRG, and $VMResourceID for the VM and Bastion host that you want to access. Note that to use variables, you must be using a PowerShell tab in Windows Terminal.
$BastionName = 'PetriBastion' $BastionRG = 'Bastion' $VMResourceID= '<Subscription-Id>' az network bastion rdp --name $BastionName --resource-group $BastionRG --target-resource-id $VMResourceID
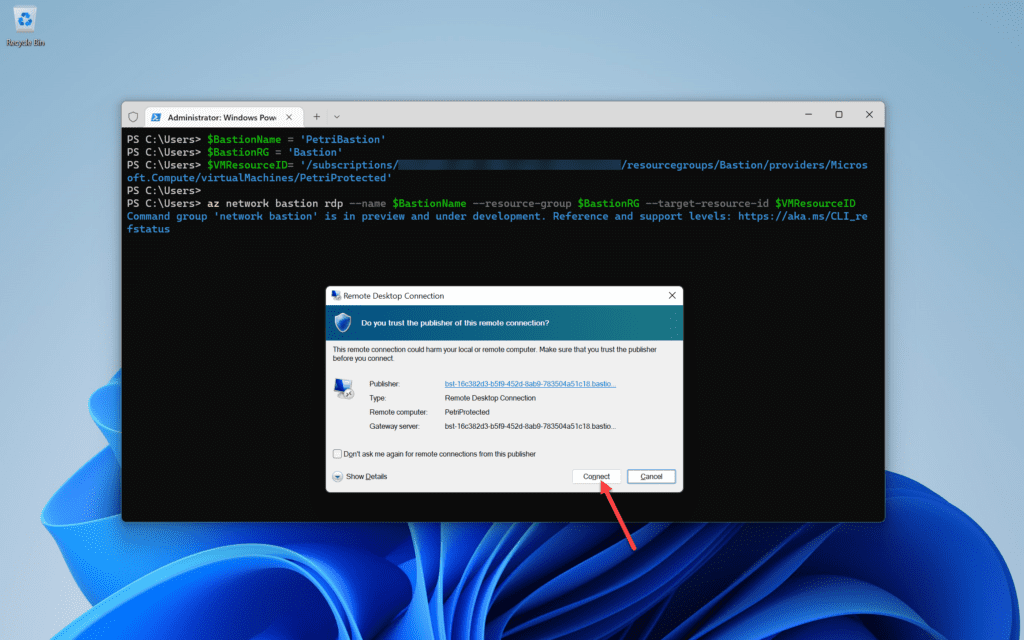
The Remote Desktop client will open on your PC and prompt you with valid log-in credentials for the guest OS, as long as the following requirements are met:
- The Azure Bastion resource is running and healthy.
- There is a route from the Azure Bastion resource to your virtual machine.
- All firewall appliances, Network Security Groups (NSGs), and the guest OS firewall of the virtual machine allow the RDP connection from Azure Bastion.
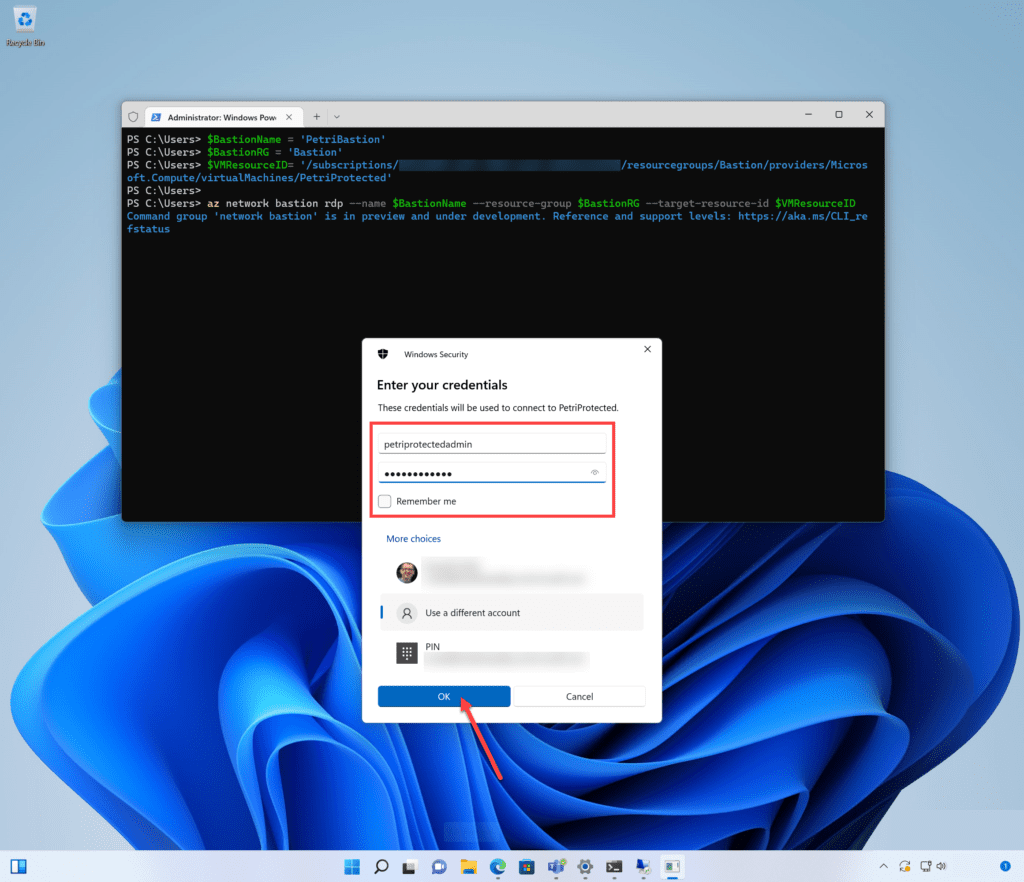
Assuming that copy and paste are enabled, the developer/operator will have a familiar session experience. One could probably create a custom PowerShell cmdlet to simplify the login experience if the same Azure Bastion resource was to be used repeatedly.
Conclusion
Using Azure CLI to connect to VMs behind an Azure Bastion Host is hardly ideal. It would be great if in the future, Microsoft built this functionality directly into the native RDP client in Windows.
But in the meantime, using Azure CLI to launch connections to Windows and Linux VMs protected by a Bastion Host is the only option you have. Assuming of course that you don’t want to connect to VMs using the Connect > Bastion option in the Azure Portal.



