Understanding Network Basics: What is TCP, Subnetting, and More
- Blog
- Networking
- Post

In this article, we’ll explain the basics of networking, networking architecture, networking types, and networking security. We’ll also detail what is TCP, subnetting, and all other core networking technologies you should know about.
Sharing data and resources between individuals, and across industries and countries, is a significant part of daily life. Establishing a computer network provides a reliable solution for exchanging resources, though it can be quite complex if you don’t have sufficient knowledge about core networking technologies.
What is TCP?
The TCP or Transmission Control Protocol is the standard communication protocol used to enable data communication over a network between devices. It’s one of the core pillars of the Internet protocol suite, alongside the Internet Protocol (IP) and the User Datagram Protocol (UDP). We commonly use TCP/IP to refer to the Internet protocol suite.
HTTP is another important networking protocol used to receive information on the public Internet. It can transfer data in various formats like video, audio, hypertext, and more. We’ll share more details about how the Internet works later.
What is a computer network?
A computer network is a group of computers and other devices that are interconnected either through cables or Wi-Fi. The connected devices can send and receive data and share resources. The network involves hardware components like switches, routers, cables, and wireless access points. And software components like operating systems.
The computer network facilitates you to communicate effectively and share software and databases among computers and other devices. The existence of the Internet, live-streaming, e-commerce, etc., depends on the computer network.
Computer networks and the Internet
The Internet is a type of computer network (WAN) that connects a wide range of devices around the world. It facilitates communication between devices using standard protocols. The Transmission Control Protocol (TCP) and Internet Protocol (IP) are the main protocols. The Internet Protocol assigns a specific name and address to each device connected to a network.
The Internet is not directly connected to each device. But instead, it relies on switching devices called routers to connect with other devices in a building or area. The router receives communication from devices through one of its incoming communication links and forwards it to end systems using outgoing communication links. Internet Service Providers (ISPs) and Network Service Providers (NSPs) facilitate the transmission of data packets over the Internet to exact IP addresses assigned to connected devices.

The main types of computer networks
Computer networks are divided into different types based on geographical locations and requirements. Here are some of the main types of computer networks:
Local Area Network (LAN)
Local area networks (LANs) connect computers and devices over short distances, allowing them to share resources like data, printers, and databases. Usually, LANs use Ethernet cables, which provide an interface to connect multiple devices. It’s the perfect network choice for schools, organizations, and homes where devices are all located in the same room or building.
| Pros | Cons |
| It offers a high-speed network. It’s inexpensive to install and maintain. It enables database and e-mail-related services. It facilitates sharing of printers, scanners, and files. | It covers a short distance Printing is slower across a LAN |
Wireless Local Area Networks
A Wireless Local Area Network (WLAN) connects computers and other devices to the network using radio waves instead of cables. Compared to a LAN, a WLAN is more convenient because there’s no need to physically install cables. WLANs transmit data as packets. And each packet contains data as layers, header, body, and a unique MAC address (Media Access Control).
Wireless Local Area Networks use the 2.4 GHz and 5 GHz Wi-Fi bands to transmit data. The 2.4 GHz band can provide better coverage but it transmits data at slower speeds. However, the 5 GHz band provides faster speeds at a reduced range.
| Pros | Cons |
| You can connect without a cable provided you are in range of an antenna. It supports a range of devices, including computers, smartphones, tablets, IoT devices, and more. It’s cost-effective as it requires limited equipment to set up compared to a wired network. It’s highly scalable. | Depending on how the WLAN is configured, it might not be as secure as a wired network. There’s a reduced data transfer rate compared to wired networks with higher latency. It requires a government license. |
Wide Area Network
Wide Area Networks (WANs) connect computers and other devices over a large geographical area. They use fiber optics, satellite links, or telephone lines to connect the devices. The Internet is the perfect example of a WAN.
Generally, large organizations like multinational corporations and banks, etc. use WANs to communicate with branch offices and business partners across the world. A WAN is usually connected to Local Area Networks and Metropolitan Area Networks rather than individual computers. And it uses the TCP/IP protocol to interconnect devices in a network.
| Pros | Cons |
| It covers a large geographical area. It enables you to distribute workloads by hiring employees from different parts of the world and allocating work to them. It provides accessibility to centralized and updated data. It has increased bandwidth. | It’s expensive to install and maintain. It attracts malicious attacks due to the use of a wide variety of technologies and devices. It’s challenging to maintain a WAN without occurring any issues. |
Metropolitan Area Network
A Metropolitan Area Network, abbreviated as MAN, is like a LAN but it spans a large geographical area. MANs use optical fiber to communicate and are connected to two or more LANs using routers.
| Pros | Cons |
| It covers a large geographical area. It provides high-speed data connectivity. | It’s expensive to implement and maintain. It increases congestion. It’s less fault tolerant. |
Network topologies
Network topology refers to the physical and logical arrangements of communication links and nodes in a network. Physical arrangements show the physical layout of communication links and nodes in a network. Whereas logical topology focuses on how data is transferred between nodes.
There are several types of network topologies:
Bus topology
A bus is a simple type of topology in which a common transmission channel or bus is used for communication. In this topology, nodes are connected to taps (the connectors), and droplines (cables used to connect the bus).
Each device connected to the bus can use all the resources of the bus while transmitting the data. Although it’s cost-effective and simple to install and maintain, all systems fail to communicate when the bus fails.
Ring topology
As the name suggests, a ring topology is circular in which each device is connected to two other devices. It functions based on a token system. The nodes capture free tokens and attach data with the IP address to the tokens to enable the communication process.
These tokens take data to the destination nodes, and the receiver processes the data from the tokens. Then tokens became free to carry more data. The data transmission speed may be slow through ring topologies as it’s unidirectional. Therefore, each set of data needs to travel through the ring path.
Mesh topology
A mesh topology facilitates direct communication between nodes as all nodes are connected to one another. There are two types of mesh topology: full and partial mesh.
In a full mesh, all nodes are connected to each other. And in a partial mesh, not all nodes are connected to one another. A mesh topology provides more privacy and security as they facilitate direct communication.
Star topology
In a star topology, all nodes are connected to a single central device called a hub or switch, and it acts as the server. The nodes are clients, and they contact the hub for communications. The failure of a node in a star topology may not affect the functioning of other nodes. Star topologies are easy to scale and less expensive than other topologies.
Hybrid topology
A hybrid topology uses a combination of two or more topologies for better communication. All topologies are connected and benefit from the advantages of each topology for building an efficient hybrid topology. A hybrid topology can handle a large number of nodes and it allows users to modify the network according to their requirements.

The main types of network architecture
A network architecture is a framework that includes the network’s physical components, logical functions, and operational principles. There are two main types of network architecture: peer-to-peer (P2P) and client/server.
Peer-to-peer networks
A peer-to-peer network is a computer network in which all computers are connected to each other and share equal resources. They can perform the roles and responsibilities of both servers and clients. Peer-to-peer networks are suitable primarily for small geographical areas.
| Pros | Cons |
| It’s cost-effective as there’s no need for a dedicated server. If one computer fails, others can work without any interruption. It’s easy to set up and maintain. | It’s suitable only for a small area. It cannot have data backup as there’s no centralized system. It’s vulnerable to cyberattacks as computers in the network are self-managed. |
Client/server networks
A client/server network, also known as a centralized architecture, is a powerful network architecture in which the central computer acts as a server system and other computers as clients. The central computer is connected to the client computers and it is in charge of processing all the requests from client computers.
The server stores all the shared data and handles network administration and security.
| Pros | Cons |
| It provides improved network speed. It offers enhanced network security as a centralized server manages the shared resources. It’s possible to back up data frequently. | If the server fails, the network fails completely. It’s essential to have a network administrator. It’s expensive to set up and maintain. |
What is an IP address?
An IP address or Internet Protocol address is the numerical network address of a device on the Internet used for communication. Usually, the length of the IP address is a 32-bit number and it’s known as IPv4. The growth of Internet users also paved the way for the deployment of another version known as IPv6, which uses a 128-bit number.
An IPv4 address is a 32-bit address and supports DHCP and manual address configurations. It uses dot-decimal notation and consists of four sets of decimal numbers separated by dots. The decimal numbers in the IPv4 range from 0 to 255. For example, 192.149.252.76. It can store 232 addresses.
IPv6 is a 128-bit address, and it can provide up to 2128addresses. It is represented in hexadecimal format and it consists of eight fields separated by columns (:). IPv6 offers an adequate number of addresses to cope with the future growth of the Internet.
The Dynamic Host Configuration Protocol (DHCP) is a mechanism to assign IP addresses to devices within a network. It simplifies the process of assigning IP addresses among network devices. For example, if it’s a Wi-Fi network at home, the router is also the DHCP server. At the enterprise level, a dedicated DHCP server will often manage IP addresses.
Public and private IP addresses
A public IP address is assigned to the network router by the Internet Server Provider (ISP). Although private IP addresses are considered safer, public addresses can access the Internet directly.
Public IP addresses are easy to track. However, it’s possible to hide public IP addresses by connecting to a Virtual Private Network (VPN) or a proxy server. For example, public IP addresses are like a PO Box number of a home address.
Private IP addresses are assigned to devices by the network router, and each device within a network should have a private IP address. It enables devices on the same internal network to communicate with each other.
Though private IP addresses are safer than public addresses, they are traceable by devices connected to the same network. For example, a private IP address is the address of a house.
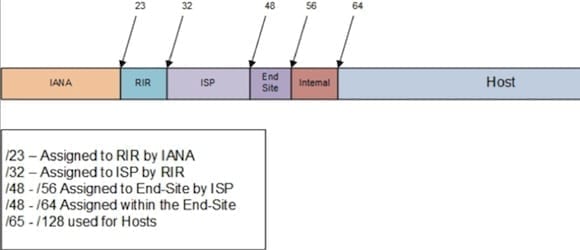
What is subnetting?
IPv4 subnetting is the process of splitting a network into subnets to make free more IPv4 public addresses. Subnetting reduces congestion as it helps to efficiently route traffic to a particular device in the subnet.
There are some important differences between IPv4 and IPv6 subnetting that we explored in a previous article on Petri. With IPv6 subnetting, the 128-bit address
Other unique identifiers in a network
The unique identifiers in a network make the information addressable to the proper location on the Internet. Here are some unique identifiers that enable the data transmission makes possible:
Host name
The hostname is a domain name assigned to a device connected to a computer network that helps to identify the device.
MAC addresses
Media Access Control (MAC) addresses are unique identifiers usually assigned by device manufacturers. It’s also referred to as an Ethernet hardware address or physical address. It consists of six groups of two hexadecimal digits separated by colons or hyphens. Sometimes, it appears without any separator.
The use of MAC addresss is essential in IEEE 802 technologies, including Wi-Fi, Bluetooth, and Ethernet to identify devices in a network.
Network ports
A port is a number that is used to identify a transaction over the network by specifying its host and service. It helps to differentiate between IP services such as HTTP, SMTP, and FTP. Port numbers vary from 0 to 65535, and they are a 16-bit digit.
Network sockets
A socket is an endpoint of two-way communication between two devices on the network, and it’s a combination of IP address and port number.
Apart from the identifiers mentioned above, there are other unique identifiers like ARP (Address Resolution Protocol), RARP (Reverse Address Resolution Protocol), and more.

Common network devices
Network devices are the physical devices that facilitate communication over networks. Following are some of the common types of network devices:
Network hubs
A hub is a device that connects with multiple devices on a LAN network and sends the message received from a port to other ports without filtering them. It functions at Layer 1 (physical layer) of the Open Systems Interconnection (OSI) model, and there are mainly three types of hubs:
- Active hubs can manage their own power supply and boost signals it sends to other ports.
- A passive hub only provides message signals to the connected devices without boosting or repairing them.
- An intelligent hub is as same as an active hub, but it can identify issues with connected devices.
Network switches
Switches send messages directly to the destination device by examining its MAC address. It stores MAC addresses of all connected devices in its address table. Switches operate at Layer 2 (data link layer) of the OSI model. There are different types of switches are available, including unmanaged switches, managed switches, smart switches, fixed switches, and more.

Routers
The router sends data packets to the destination by examining their IP addresses. It has an updated routing table that facilitates the router to route data to its destination without fail. It operates at layer 3 (network layer) of the OSI model. There are different types of routers, such as wireless routers, edge routers, core routers, and distribution routers.
Common types of cables
A networking cable is a hardware used to connect networking devices together to send data. There are three main types of network cables:
Coaxial cable
Coaxial cabling is highly resistant to signal obstructions as it has a copper conductor surrounded by a metal shield. Although it’s complex to install, it’s easy to handle due to greater cable lengths.
Fiber optic cable
Fiber optic cables are highly resistant to moisture and fluorescent light. Therefore, it’s the standard cable for connecting network devices across buildings.
Shielded Twisted Pair (STP) cable
STP is a type of twisted pair cable wrapped with an additional shield that helps to reduce electromagnetic interference (EMI). STP cable is used in environments with high amounts of EMI or when the network cable needs to be run along the same route as main electricity cables.
Unshielded Twisted Pair (UTP) cable
UTP cable is also a type of twisted pair cable that possesses improved electromagnetic capability. Although it’s not shielded, it’s highly suitable for telephone wiring and LANs.

Computer network security
Computer network security consists of policies and measures taken to analyze, detect, monitor, and prevent security threats and attacks. Authentication is a significant part of network security. Using a username and a strong password is the most common authentication method.
Two-factor authentication and multi-factor authentication increase the security of data and information. Firewalls also play a role in securing data effectively.
What are firewalls?
A firewall is a network security measure that can monitor network traffic based on security policies to detect unusual and suspicious activities. The firewall system can effectively prevent or reduce the effect of malware attacks. It also can detect security vulnerabilities and take measures to improve the security system.
With the help of an integrated intrusion prevention system, firewalls can react quickly to all levels of malicious activities.
Common network attacks
Networks are vulnerable to attacks, and there are two main types of attacks: passive and active.
Passive attacks are a type of cyberattack in which intruders intercept data transmission via a network. Wiretapping, idle scan, passive port scanner, etc. are some examples.
In active attacks, the attackers inject malicious code into software and initiate commands to gain access to the network. Phishing, spoofing, denial of service (DOS) attacks, Smurf attacks, etc. are some examples.
Conclusion
Having a deep understanding of network basics including TCP and subnetting helps to set up a computer network. It also facilitates you to serve organizations efficiently by enabling better communication between devices over the network and protecting organizations’ data from possible security threats.



