Best Practices: Office 365 Tools to Eliminate Email Security Misconfigurations
According to Microsoft, 90% of security threats start from malicious email. And while it would be nice to think that customers using Exchange Online Protection (EOP) should always receive the highest level of protection, the reality isn’t quite so simple.
EOP is a complex service. It provides a lot of granular configuration options and the ability to customize protection to suit a diverse range of customer needs. But with that flexibility comes the risk that custom configuration settings can leave clients unwittingly exposed.
As Microsoft has built out its Defender for Office 365 service on top of EOP, it has respected many of the granular configurations and customizations. And this work ensures customers can still tailor Defender for Office 365 to their unique requirements.
Microsoft knows only too well how clients can be their worst own enemies. It noted recently that it had found some firms had configured Defender for Office 365 to bypass filters, the detonation service, and excluded thousands of known phishing URLs from checks.
As an IT professional, it shouldn’t be a surprise that custom policies and configurations often lead to security issues. Temporary policies are often left in place indefinitely. And sometimes policies can be found in Exchange Online that have been carried over from legacy versions of on-premises Exchange Server that have been out of support for years.
Sundeep Saini, a product manager on the Defender for Office 365 team, says “It wasn’t sufficient that we educate customers of the problem, we had to actively help with getting customers to a more secure state.” To eliminate ineffective configurations and prevent gaps in protection coverage, Microsoft is introducing new capabilities in Defender for Office 365.
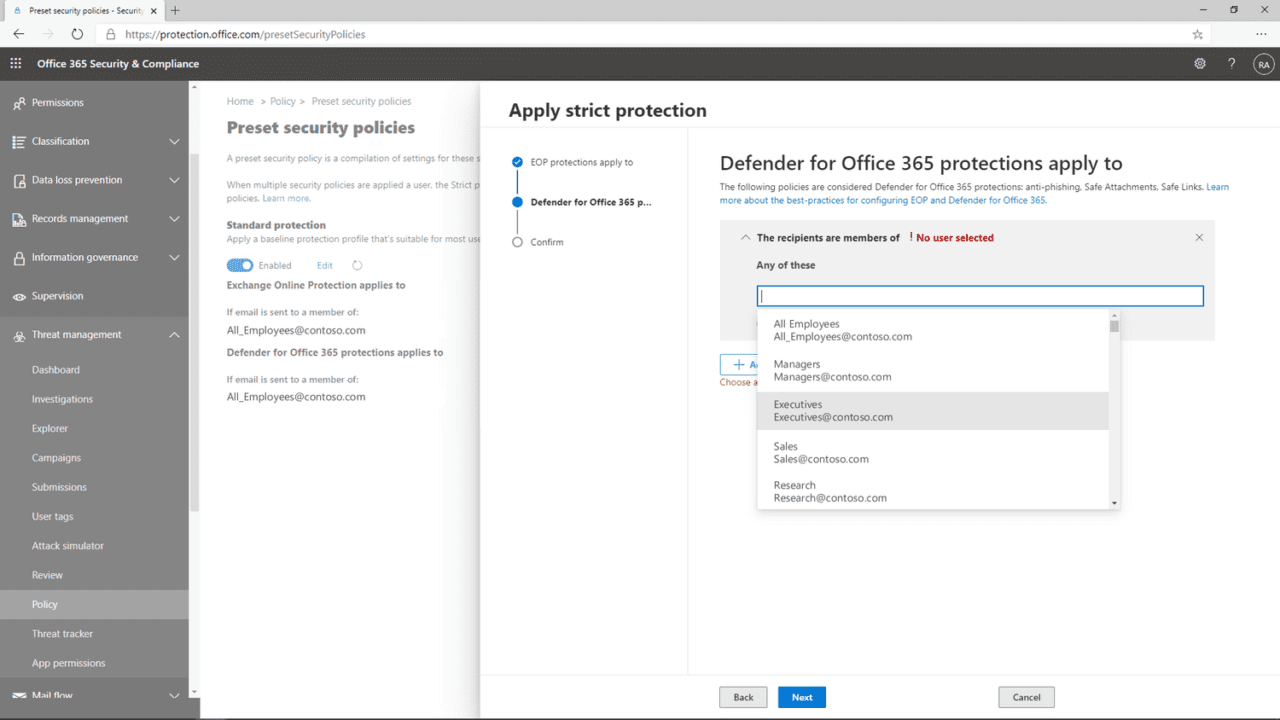
Preset security policies
Last year, Microsoft released preset security policies for EOP and Defender for Office 365. The policies provide a way for organizations to apply a recommended baseline security configuration with all the necessary settings for spam, malware, and phishing. The presets come in two forms, standard and strict. The standard preset can be applied to most users in an organization. And the strict preset is designed for high value users or priority targets.
Preset security policies have proved popular with Microsoft’s customers. And they provide an easy way to stay up to date with the latest security recommendations and settings. Preset security policies can be applied to users, groups, and domains. You can also exclude users, groups, and domains to create exceptions.
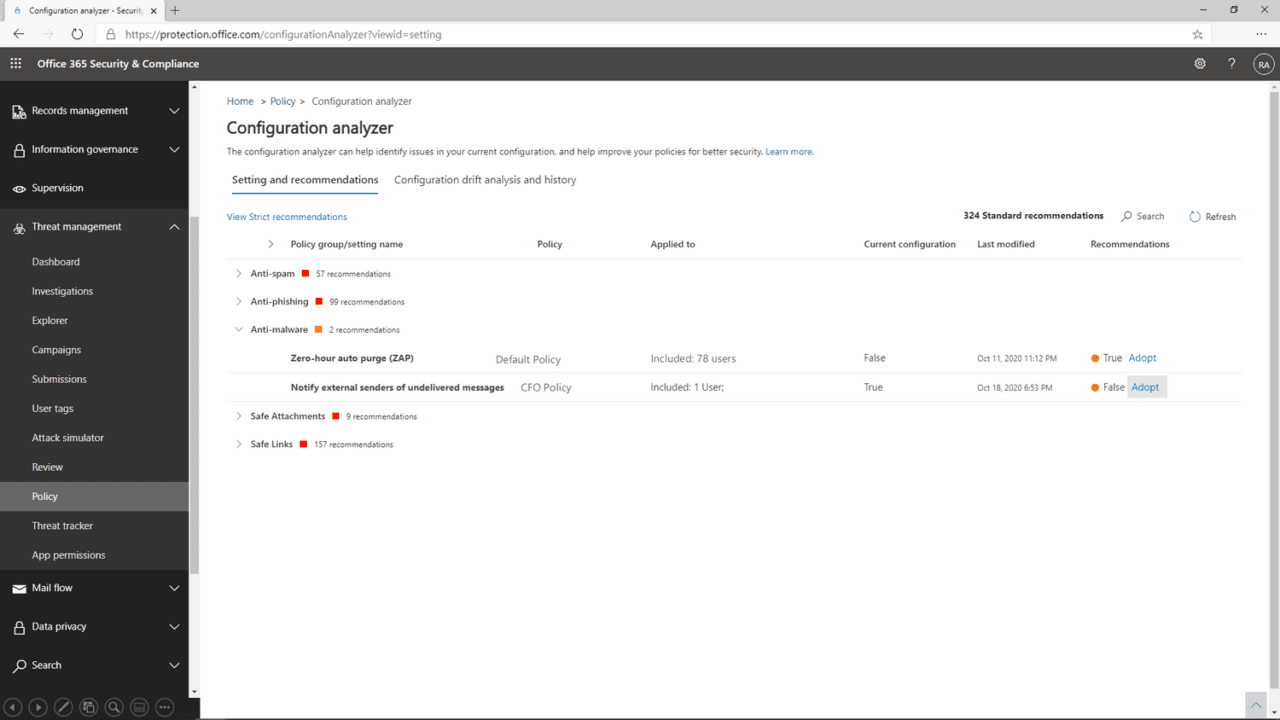
Configuration Analyzer
Configuration Analyzer was also introduced last year. It lets organizations see policy issues in the admin portal, with a list of remediations so that a tenant can be easily configured to meet Microsoft’s strict security recommendations.
Microsoft says that Configuration Analyzer has been used to make 290,000 policy changes on more than 26,000 tenants. It lets organizations update their configuration to the recommended standard in just a few steps.
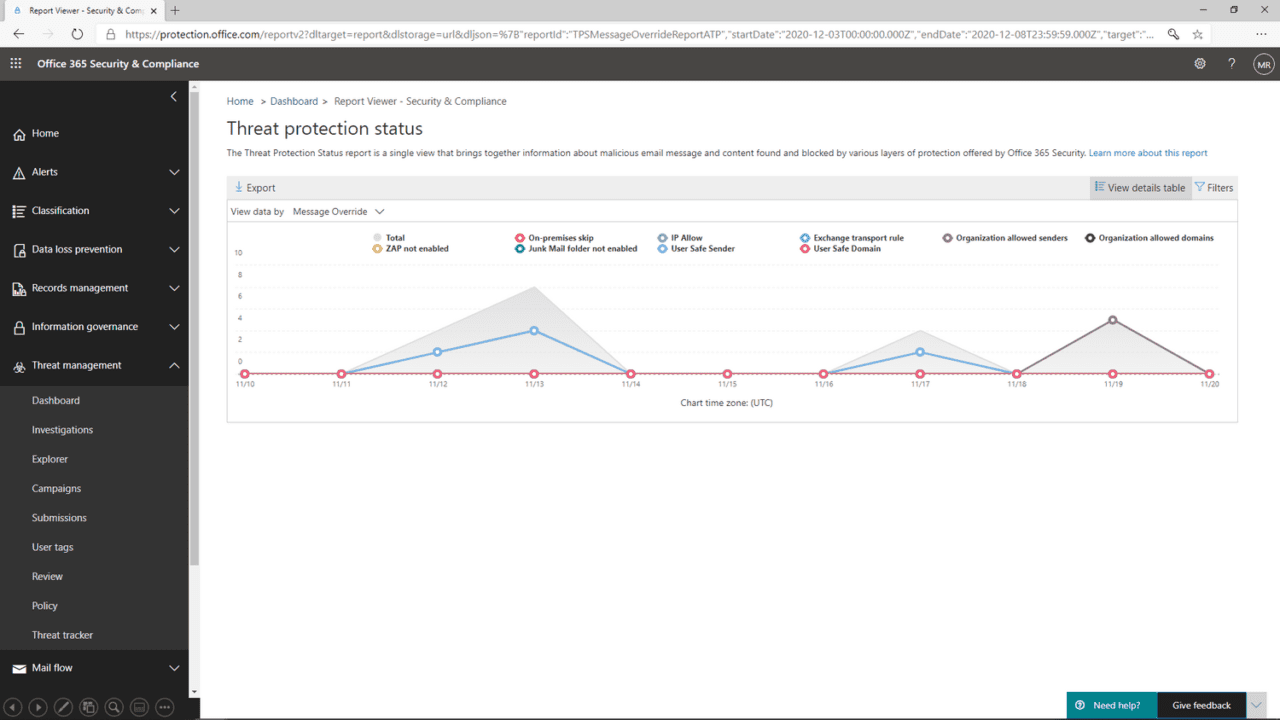
Overrides reports and alerts
Overrides are configurations that permit Office 365 to deliver known suspicious and malicious content to users. They can be applied at the user or tenant level. Overrides pose a threat to organizations because while policies might be configured correctly to protect the tenant, overrides can render them useless because overrides allow Office 365 to bypass policy.
A view in the threat protection status report lets organizations see overrides across a tenant. It’s also possible to investigate further to see the causes of overrides in an environment.
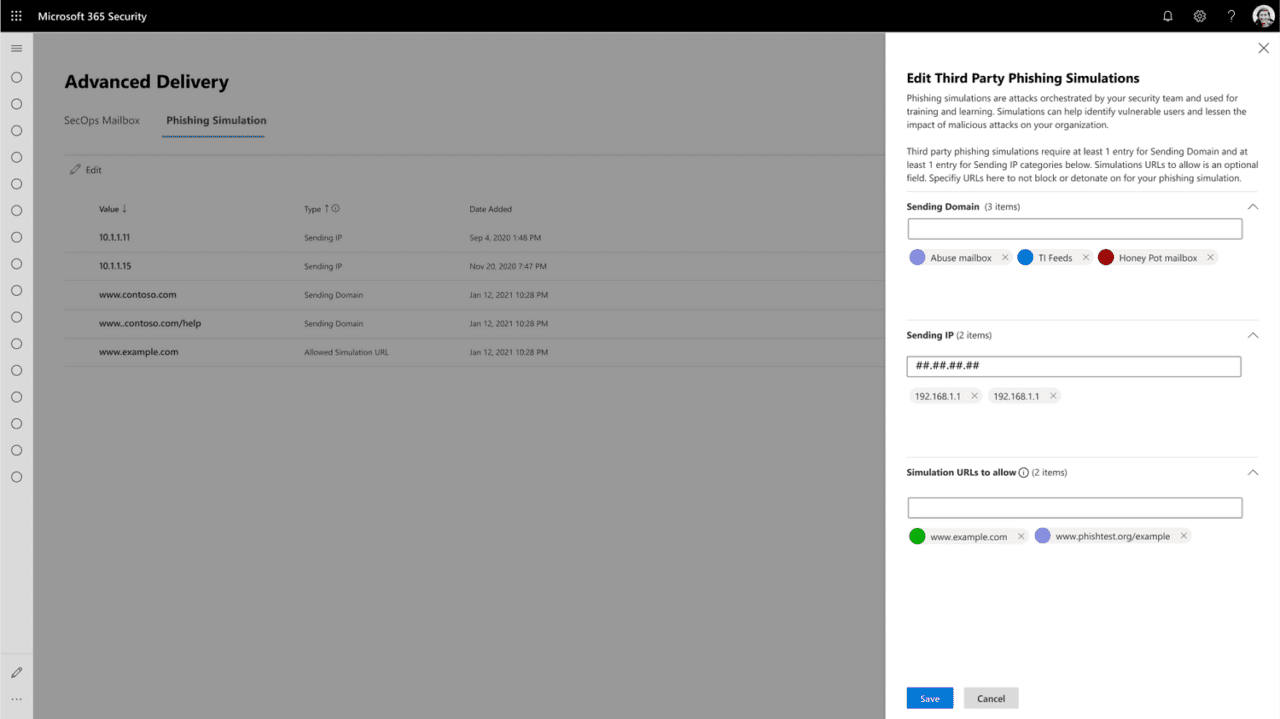
Advanced Delivery for phishing simulations and SecOps mailboxes
This month, Microsoft is planning to extend it’s secure by default posture to include Exchange Transport Rules (ETR). ETRs are sometimes used in phishing simulation and for SecOps mailboxes.
Advanced delivery for phishing simulations and security operations mailboxes is a new feature that lets organizations configure message delivery for these scenarios without using ETRs.
For more information on how to configure advanced delivery, check out Microsoft’s blog post here.
Exchange Online vs on-premises Exchange Server security
I’ve heard reports that Microsoft Exchange Online customers are less secure than their on-premises Exchange Server counterparts. I don’t have the data to hand but as you can see, Microsoft Exchange Online customers need to take some responsibility for ensuring their configurations are secure.
And these tools should help customers better secure their environments and make sure they stay current with the latest recommendations from Microsoft.