Microsoft Now Lets IT Admins Review & Remove Inactive Azure AD Users

Microsoft has unveiled a couple of security improvements to Azure Active Directory (recently renamed Microsoft Entra ID). The company has released a new access reviews feature in preview that lets organizations remove inactive user accounts that could potentially cause security risks.
More specifically, IT administrators can now delete accounts from Azure AD that haven’t logged in for a specified number of days. The new access review feature is a part of the Azure Active Directory Identity Governance service. It comes in handy for businesses that want to prevent contractors and former employees from accessing sensitive information.
“Both interactive and non-interactive sign-in activities are covered under sign-in activity. As part of the review process, stale accounts can automatically be removed. This, in turn, improves your organization’s security posture,” Microsoft noted.
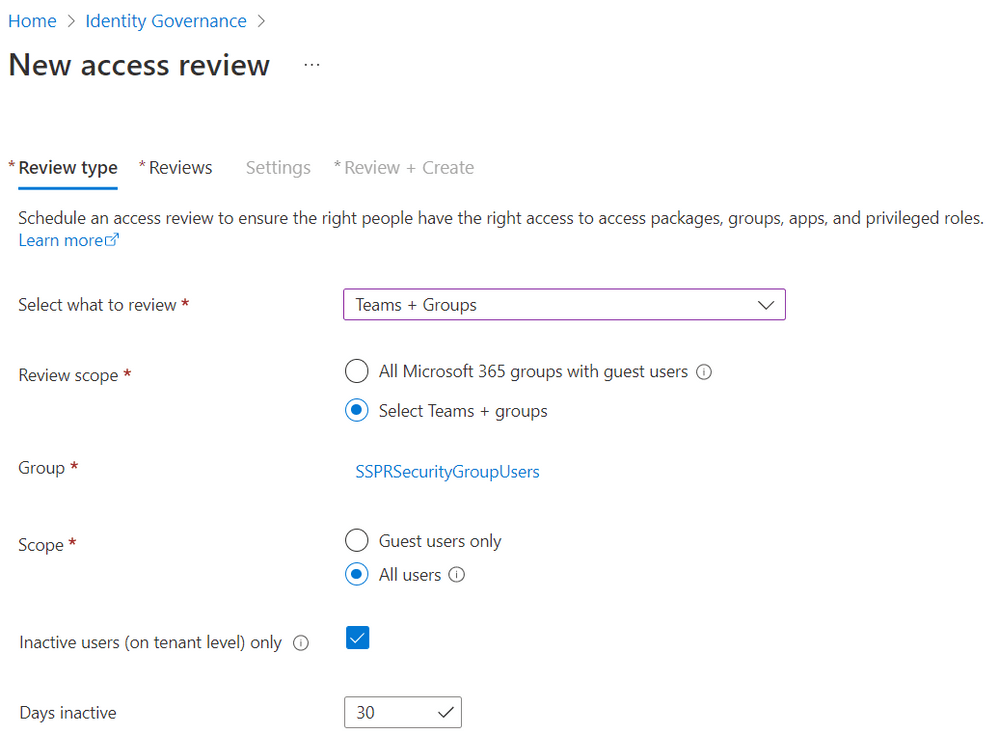
Microsoft says that IT Pros can configure settings to automatically remove all guest or user accounts that have remained inactive for up to two years. However, this capability is apparently available for customers with an Azure AD Premium P2 license, and you can check out the step-by-step guide for more details.
Microsoft brings security defaults to millions of Azure AD users
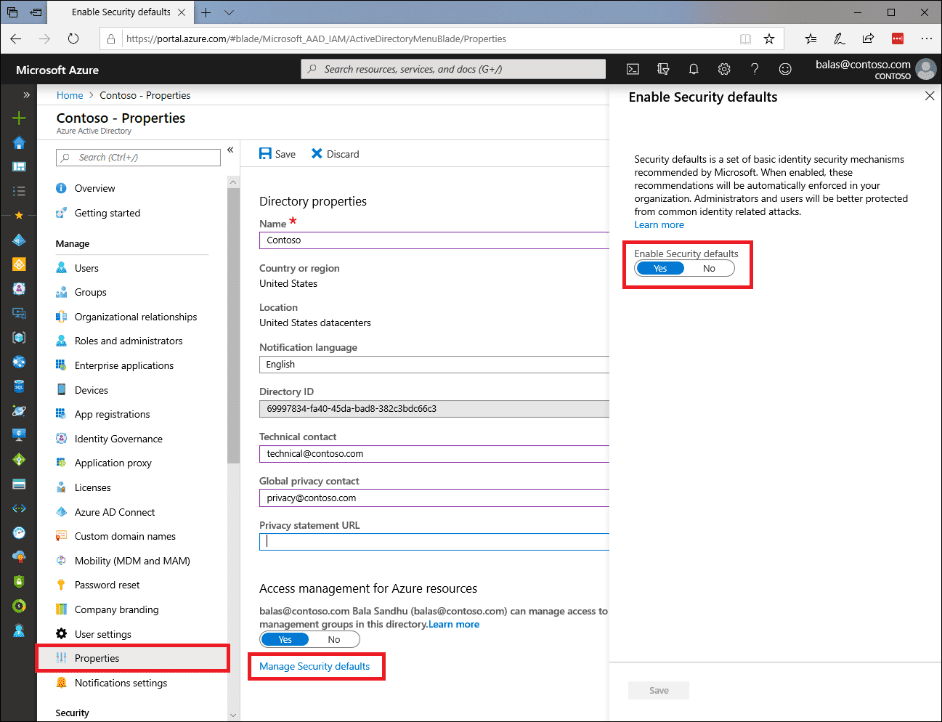
Additionally, Microsoft is getting ready to roll out the security default protections to more Azure Active Directory (AD) customers. Starting next month, the Redmond giant plans to enable security defaults for old Azure AD tenants created before October 2019. This change will impact all organizations that are not using best security practices such as modern authentication & multifactor authentication (MFA).
Microsoft introduced security baseline protections for new Azure AD tenants back in 2019 to help businesses protect end-users from password spray and phishing attacks. It was also aimed at companies using the free edition of Azure AD. As of today, around 30 million customers are using Azure AD security defaults, and the software giant now plans to expand its reach to 60 million additional accounts.
Once rolled out, IT Pros will have 14 days to enforce multifactor authentication for all end-users in their organization. Employees will need to use the Microsoft Authenticator app to register for MFA.
It will be up to the IT admins to disable the security defaults via the Microsoft 365 admin center or Azure Active Directory properties. However, Microsoft has warned that it could lead to security breaches.



