Microsoft Adds Time-Based One-Time Passcode Support to Azure AD

Microsoft has released time-based one-time passcode (TOTP) support for Azure Active Directory (recently renamed Microsoft Entra ID) customers. The new security feature allows end users to validate their identity with temporary one-time passcodes generated by an authenticator app.
Time-based password (TOTP) is one of the most popular multi-factor authentication (MFA) methods. It’s a temporary numeric passcode created by a standardized algorithm that uses the current time of the day as an input. Users are required to enter the passcode within a specific time (30 to 90 seconds) before it expires. It can help to prevent hackers from gaining access to sensitive data in enterprise environments.
“Integrating a time-based OTP with an authenticator app as a second factor in B2C scenarios user flows enables a higher level of security compared to existing email and phone factors,” Microsoft explained. “This can help users by eliminating the need for users to wait for codes to arrive in email or text messaging apps. The short lifespan of OTP codes also makes them very hard for attackers to intercept.”
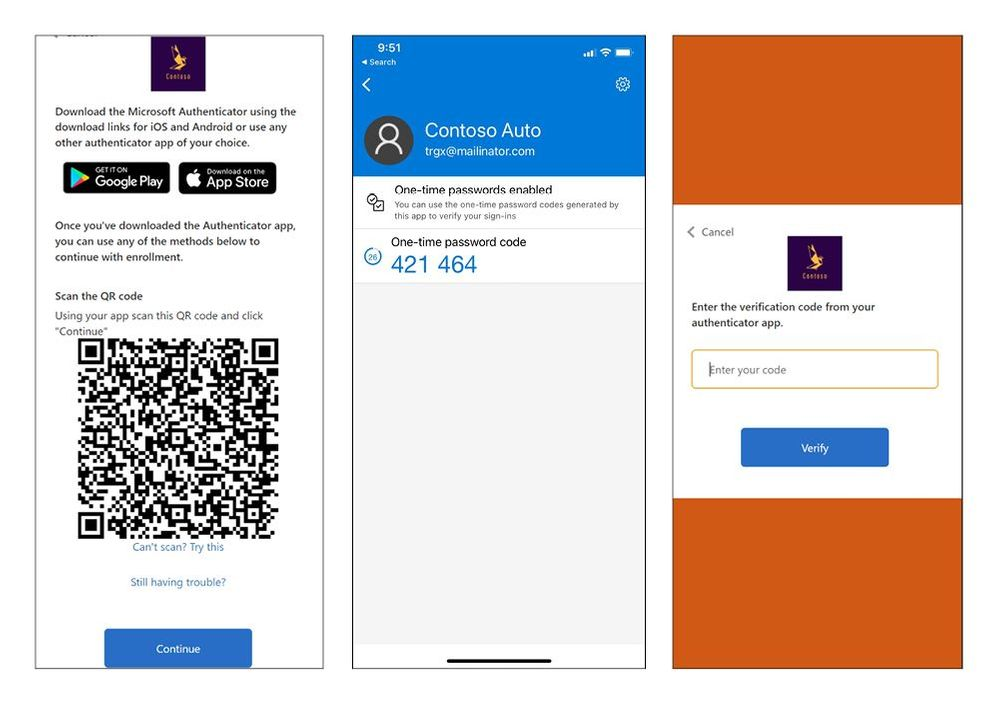
Time-based OTP supports all popular authenticator apps
Once the TOTP-based MFA is enabled, users will need to install an authenticator app on their devices. They can use the app to scan the QR code or enter it manually while signing up or logging in for the first time. However, users will be required to enter a TOTP code that appears on the authenticator app during subsequent sign-in attempts.
Microsoft notes that the security feature works with any authenticator app that supports time-based one-time password verification. However, the company recommends customers to use Microsoft Authenticator for generating TOTP codes.
Microsoft has also published a detailed guide to help IT admins configure time-based OTP for Azure AD user accounts. Let us know in the comments below if you think that the new feature can help to prevent security breaches in your organization.


