How to Fully Patch the PrintNightmare Vulnerability
If you are an admin and have been scrambling the past week to patch the PrintNightmare vulnerability, you are not alone. The messaging around this zero-day has been confusing with Microsoft saying they have a solution, industry experts saying it’s not effective, and now Microsoft saying “you’re patching it wrong”.
Microsoft isn’t quite saying that you are patching wrong but what they are providing is additional guidance about making changes to your registry that may not have been changed after installing the latest update. In this guide, we will walk through multiple paths and options to securing your infrastructure against PrintNightmare.
Background
On July 6th, Microsoft released an out-of-band patch known as KB5004945. At the heart of the issue is a remote code vulnerability that would allow an attacker to use Windows Print Spooler to perform elevated file operations. An attacker who is able to successfully exploited this vulnerability would be able to view, change, or delete data; or create new accounts with full user rights.
In the following days after the release, researchers have uncovered a way to bypass the patch that Microsoft released. As it turns out, according to Microsoft, installing the patch is not the only step that you need to take to fully protect your environment and in some scenarios, you will need to make a change to your registry as well.
Protecting your Environment without a Patch
Not everyone can install the patch that Microsoft has released. It is being reported that customers with Zebra printers are finding that the patch is disabling the printers entirely. In this scenario, the patch may protect your environment but at the cost of disabling all printers entirely.
The first step you need to take is to determine if you are running the PrintSpooler service, you can determine this by taking the following steps:
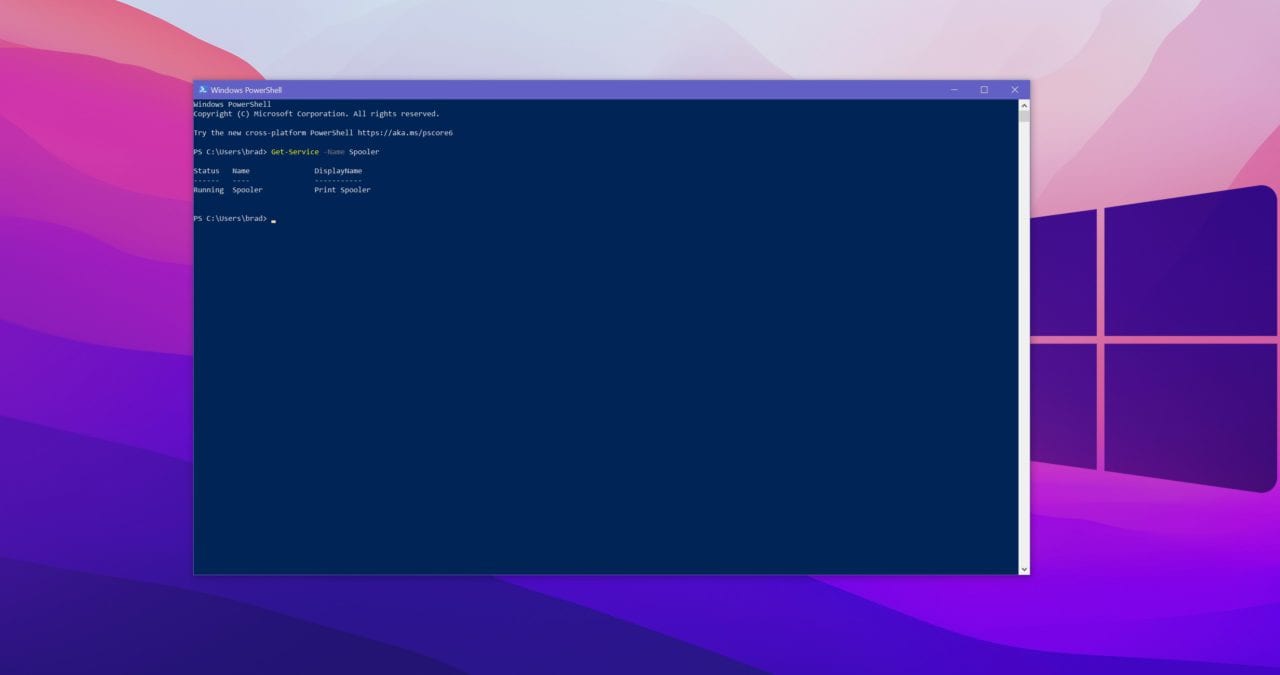
- Hit Windows Key and type PowerShell
- Enter the following command: Get-Service -Name Spooler
- If you see the words “running” this means the service is running.
Option 1 – Disable the Print Spooler service
- If disabling the Print Spooler service is appropriate for your enterprise, use the following PowerShell commands:
- Stop-Service -Name Spooler -Force
- Set-Service -Name Spooler -StartupType Disabled
- Impact of workaround Disabling the Print Spooler service disables the ability to print both locally and remotely.
Option 2 – Disable inbound remote printing through Group Policy
- Computer Configuration / Administrative Templates / Printers
- Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
- You must restart the Print Spooler service for the group policy to take effect.
Protecting your Environment with a Patch
If you have determined that installing the patch is safe for your environment, these are the steps you need to take to fully mitigate the PrintNightmare vulnerability.
After applying the patch, CVE-2021-34527, you will need to check the registry for specific values. To do this, follow these steps:
- Hit the Windows Key
- Type Registry Editor, hit enter
- Navigate to HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- If this registry key does not exist on your system, no further action is needed
- If this registry key does exist on your system,set NoWarningNoElevationOnInstall = 0 (DWORD) or not defined
- Also change UpdatePromptSettings = 0 (DWORD) or not defined
After following these steps, Microsoft says that your environment will be protected against the PrintNightmare vulnerability. These are important steps to follow as this will protect your environment from an actively exploited zero-day.
Conclusion:
Given the pervasiveness of ransomware spreading across the IT industry and new reports of attacks popping up weekly, it is imperative that IT admins figure out faster and more effective ways to manage their environments.
In years past, it was acceptable to wait a couple of weeks before applying updates to see if they caused more harm than good. But with recent security updates, malicious actors are moving faster and doing more damage in shorter periods of time than we have ever seen before.
If you haven’t done so already, making sure you have resilient backup and recovery processes are more important with each passing week. If you haven’t planned to test a recovery scenario, add that to your ever-growing task list.