Choosing between Virtual Private Network and Zero Trust Remote Access Solutions
As we enter a time of crisis that will see a significant number of employees asked to work from home, organizations need to provide effective but secure remote access to corporate resources. The tried and tested virtual private network (VPN) might seem like the obvious choice. But so-called ‘zero trust’ is gaining popularity and could surpass traditional VPN access. Gartner says that 60% of enterprises could replace VPNs with zero trust by 2023.
VPNs and perimeter networks
VPNs are a common way of allowing remote users to securely access resources behind a perimeter network. Firewalls are used to create a perimeter behind which sits all a company’s valuable IT assets. You can think of it as like building a moat around a castle. But just like the castle analogy, perimeter networks fail to protect on several levels.
Perimeter networks don’t protect resources against insider attacks. And if a hacker steals a user’s credentials, they have the key to the castle, and they can act freely in the context of the stolen user’s account. VPNs can also lead to compromise when third-party contractors use unmanaged devices to connect to corporate resources.
Most seasoned Windows IT system administrators will be familiar with the basics of configuring VPNs. And while VPNs can sometimes provide a quick remote access solution, they can be difficult to manage and work with. Not to mention that users might have issues connecting to VPN servers and maintaining reliable connections.
Windows VPN and DirectAccess
Windows 10 and Windows Server support several different remote access technologies. Windows Server has a built-in VPN server role. And Windows 10 has a built-in VPN client that can be used to connect to a Windows Server VPN server.
Microsoft DirectAccess uses technology similar to VPNs but works seamlessly for end users. When DirectAccess is configured, users don’t need to establish a remote connection to a server using a VPN client. DirectAccess makes sure that client computers are always connected to the corporate network.
DirectAccess is still supported but Microsoft hasn’t committed to extending support beyond the lifecycle of Windows Server 2019. Microsoft says that Windows 10 ‘Always On VPN’ should be used as a replacement for DirectAccess.
Windows 10 Always On VPN
Always On VPN goes beyond the features of DirectAccess to provide conditional access and system health checks using Network Policy Server (NPS), integration with Windows Hello for Business and Azure Multifactor Authentication, and more. You can see a complete list of the advanced features on Microsoft’s website here.
Zero trust network access
Zero trust is not a new security concept. But partly because it isn’t as straightforward to understand as VPNs since it isn’t a security product, there hasn’t been large adoption. But that is starting to change as the technology to implement zero trust is readily available. And the current coronavirus crisis could see zero trust projects rise as more employees are expected to work from home.
Zero trust is a security framework that dates from 2009. In short, the idea is that you shouldn’t trust anyone. Not even your own employees. Every person accessing your network must be verified. And access control policies limit the access employees have to corporate IT resources. Policies should provide just enough access to complete work-related tasks and nothing more.
Microsoft’s identity-centric zero trust model
If zero trust is a security concept rather than a product, what is needed to implement the technology? There are of course many vendors providing zero trust network access solutions, like Microsoft, Palo Alto, and ScaleFT. But as Petri is a site mainly dedicated to Microsoft technologies, I want to look in more detail at the Microsoft solutions needed to implement zero trust.
Azure Active Directory (Azure AD) is the primary product around which zero trust is based at Microsoft. Azure AD is an identity management service for cloud-born applications. Azure AD has a feature called Application Proxy that lets users access corporate web applications, and apps hosted behind a Remote Desktop Gateway, using a remote client.
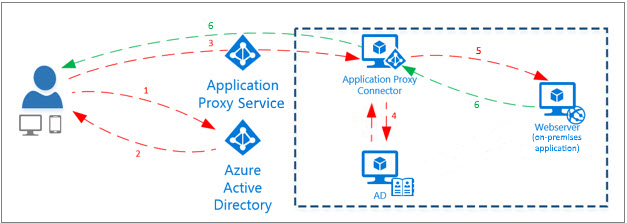
Application Proxy uses an on-premises connector to manage communication between the cloud service and the on-premises application. The connector only uses outbound connections, so you don’t need to open inbound ports or place a server in a demilitarized zone (DMZ). Application Proxy replaces the need for a VPN or reverse proxy.
Azure AD Conditional Access
Application Proxy works alongside Azure AD Conditional Access policies. Conditional Access is used to permit or deny users and devices access to corporate resources. For example, access might be granted only if certain conditions are met. Like whether the user and device are verified by the organization, the user’s IP location information, the user’s group membership, and real-time and calculated risk detection.
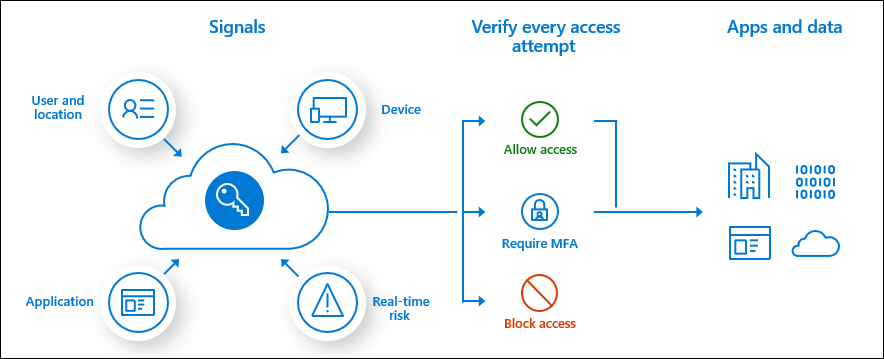
Conditional Access policies can be created to require multifactor authentication, access from managed devices for specific apps, to block access from specific IP locations, and much more.
Windows Server Web Application Proxy
Windows Server has a feature called Web Application Proxy that works like a reverse proxy and Active Directory Federation Services (AD FS) proxy. Web Application Proxy provides similar functionality to Azure AD Application Proxy, but it is a purely on-premises solution.
VPN versus zero trust
As organizations scramble to give more users remote access, the question about which technology to deploy is largely mute due to the speed of changes required and the technology that is already in place. But going forwards, as remote working becomes the new ‘normal’, even if only temporarily, zero trust provides the most secure and flexible solution. And it is something organizations might investigate if other pieces, like Azure Active Directory, are already in place.
For businesses that have already migrated to Windows 10, Always On VPN is the next best alternative. Although it still requires more investment than a traditional VPN server, with requirements for a Network Policy Server and Active Directory Certificate Services. But if you can get funding and mount the technical challenges, Always On VPN is the most secure way to establish VPN connections from Windows 10 to your corporate network using native technologies. Alternatively, there are plenty of third-party products for Windows, from the likes Cisco and Check Point, that are also worth looking at.
Related Article:



