
A software-defined perimeter (SDP) is a modern network security framework for creating a virtual network perimeter to protect an organizational infrastructure from outsiders. In this article, I’ll explain how a software-defined perimeter works and what are the main use cases for this new computer security approach.
With increasingly complex network and application security requirements, a traditional hardware-defined network perimeter may not be good enough for some organizations these days. As we’ll see in this article, a software-defined perimeter can provide better protection against cyberattacks and other risks related to untrusted access inside a network perimeter.
What is a software-defined perimeter?
A software-defined perimeter is a network security framework designed to hide your Internet-connected organizational infrastructure from external attackers. This approach is also known as a “black cloud” as it hides your organizational systems within the virtual perimeter.
A software-defined perimeter allows you to control and distribute access to internal applications, services, and other resources based on users’ identities. An SDP serves as an intermediary between users and an organization’s endpoints, and the infrastructure acts as an authenticator and authorizer.
An SDP can also micro-segment network access and dynamically create one-to-one connections between users and organizational resources such as applications or services. Moreover, an SDP provides fine-grained access controls to your IT environment, and it can offer better protection from several types of cyber threats and attacks. This includes denial-of-service attacks, man-in-the-middle attacks, port scanning, brute scanning, and lateral movement attacks.

What are the main benefits of using a software-defined perimeter?
A software-defined perimeter is a comprehensive solution to secure your organizational resources from external attackers. Here are the main benefits of using an SDP in your IT environment :
- Reducing your organizational attack surface to minimize risks of cyberattacks.
- Getting fine-grained access controls over your resources including applications and services.
- Isolating mission-critical applications and data from other organizational apps and services.
- An SDP supports a variety of devices and a broad risk-based policy.
- An SDP can simplify complex organizational policy management for IT or system administrators.
What are the best use cases for a software-defined perimeter?
A software-defined perimeter offers several benefits in terms of security and access management. It also helps you accomplish several organizational and business goals by serving as an effective resource management and tracking mechanism. Here are some of the top use cases for a software-defined perimeter:
Providing seamless access to your organization’s resources
An SDP can help you establish seamless access to public and private cloud resources in a single environment. Due to the software-defined nature of an SDP, it can be used to connect and establish secure connectivity between authenticated users and the applications. This avoids the need of implementing third-party connectors or setting up infrastructure to establish a secure connection.
An SDP can be a more secure and modern alternative to a virtual private network (VPN) when it comes to provisioning users with resources. It allows your employees to access applications faster while being able to verify their authenticity.
Protecting cloud-based resources
Organizations can leverage a software-defined perimeter to restrict third-party access and prevent users from moving laterally within a network. An SDP can also help to reduce the risk of unwanted access or exploitation of any form of your organizational resources by hiding cloud instances for added security.

How does a software-defined perimeter work?
Unlike traditional network-based security architectures, a software-defined perimeter focuses on securing the applications, users, and the connection between them. An SDP uses a zero trust security approach to prevent illegitimate users from accessing an entire network.
Once a user and the device they’re using are authenticated, the software-defined perimeter sets up an individual network connection between the device and the backend server that’s being accessed. Unlike traditional network security architectures, you are not given access to an entire network but to a private network connection that only you have approved access to.
In an SDP, trust is never implicit: Users and their devices need to earn trust before gaining access to an organization’s network. An SDP also receives no inbound connection and responds only to outbound connections for added security.

An SDP builds a secure perimeter by isolating network services and applications residing on-premises or in the cloud from vulnerable networks. An SDP can also help you to build an air-gapped, secure, and on-demand organizational network.
The architecture of a software-defined perimeter
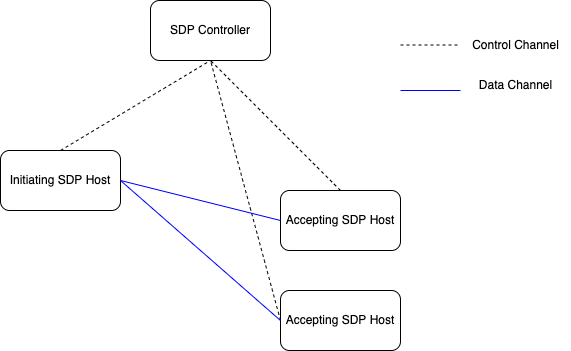
The architecture of a software-defined perimeter consists of two main components – SDP controllers and SDP hosts.
An SDP controller identifies the devices in a network using their public key, geolocation, or other primary identifiers. An SDP controller also enforces access regulations in the network. Once a device and user are authenticated, the SDP controller passes the information to the SDP gateway to determine their access.
An SDP host, on the other hand, can be used to either initiate or accept an SDP connection. It’s a server that controls the flow of data between applications and devices within a network.
Based on the action that’s being performed, an SDP host can either be an initiating SDP host or an accepting SDP host.
- An initiating SDP host fetches the list of accepting SDP hosts from an SDP controller and is responsible for establishing a Transport Layer Security (TLS) connection with the hosts.
- An accepting SDP host is responsible for linking authorized devices to the apps in the network that have been requested.
How does a software-defined perimeter compare to a VPN?
A virtual private network also allows you to secure your organizational resources and their accesses over a network by building encrypted connections. While both SDPs and VPNs are meant to secure your organizational resources from external threats, they are fundamentally different.
Here are some of the major differences between SDP and VPN based on certain core security aspects:
| Feature | SDP | VPN |
| Security | SDPs provide tighter security than VPNs due to their zero trust security policy | VPNs heavily rely on a network-centric security model or trust-based network design. |
| Access authorization | Fine-grained access through continuous assessments | VPNs work on network access authorization, which could increase vulnerabilities. |
| Implementation and Delivery | SDP can be deployed and delivered through a Software-as-a-Service (SaaS) paradigm | VPNs can be implemented either through a dedicated appliance or through complex network configurations |
| Scalability | Highly and easily scalable | Scalability is subject to infrastructure, maintenance, and operational costs |
| User Experience | Fast and efficient as you can work with multiple applications residing in different locations | Performance can sometimes be slow or unreliable |
| Management | Being a software-defined service, an SDP is relatively easier to manage | Managing a VPN can demand resources including costs and technical staff. |
| Downstream Integrations | SDP can easily be integrated with any downstream applications or security services | Integrating a VPN with downstream apps or services can be quite complex. |
How to implement a software-defined perimeter
To implement a software-defined perimeter, you can either choose to set up your own SDP infrastructure yourself or use the different SDP providers on the market.
Setting up your own SDP
To create your own SDP, you’ll first have to first a mechanism to verify and authenticate users. This can be done using a single sign-on (SSO) solution, security tokens for authentication, multi-factor authentication (MFA), or other security mechanisms such as Security Assertion Markup Language (SAML).
Next, you will have to create a mechanism to verify the devices with which authenticated users will gain access to your systems. This pre- and post-connection device verification process can be done in multiple ways using different data points such as device location, device ID, registry information, and more. You can also determine rules or security policies that devices and users need to adhere to gain access to the systems.
Finally, you will have to set up a secure means of connection and data transmission between users’ devices and your applications or services. These network tunnels are crucial in safeguarding your information. Moreover, there are several intermediary steps that you need to take care of in between these aforementioned broader tasks to build a software-defined perimeter.
Main SDP vendors
Alternatively, you can choose a service provider from any of the readily available vendors. However, it is crucial to draft a list of requirements before you choose your SDP vendor. You will also need to take into consideration your existing integrations and applications that need to operate in the SDP.
As of today, Perimeter 81, AppGate, and CloudFlare ZeroTrust are some of the top SDP providers that offer security, control, and several other useful features.
Conclusion
A software-defined perimeter is a secure way of providing access to specific resources in an IT environment. Deploying an SDP within your organization will not only secure and safeguard your network, applications, and resources, but it can also help you establish better access controls and build an efficient zero-trust network security model to protect your company’s resources.



