Protecting Files in Office 365 Document Libraries Against Guest Users
Office 365 Makes Rights Management Easy
I like rights management. It’s a feature that is much easier to deploy and manage in the cloud than on-premises, yet it is a mystery why more tenants don’t use the technology to protect confidential and sensitive information. Microsoft has done their best to make rights management more approachable, including a new Encrypt message feature, and while progress is being made, it’s not enough.
Collaboration and Guest Users
Which brings me to Office 365 Groups and Teams and the ability of these collaborative applications to welcome guest users into their midst. Generally, everything goes well, and guest users can interact with other group members freely and easily, thanks to the relatively simple membership model that gives every member the same level of access to group resources. Owners are the only exception because someone must corral the cats and manage membership and settings.
The downside of the simple membership model appears when you invite guests to join a group or team and realize that guest members can see, open, and even remove documents in the shared document library. Although logical (remember, everyone has equal access), it might not be what you want.
Private Channels Coming
Microsoft says that they are working on private or secure channels, a popular request in UserVoice to restrict the content of specific channels to specific members. The idea is that you might want to have private sections of a team that you don’t want everyone to see, including guest members. It’s relatively easy to see how a private channel might work for conversations, but more difficult when you throw in all the resources attached to tabs belonging to a channel, including a folder in the SharePoint document library.
Updating SharePoint Permissions
Bob German of Microsoft offers a solution to the problem by amending SharePoint permissions. In this case, the problem is how to isolate some documents from members of a group who have tenant accounts. The same principle applies to guest users.
Although the solution work, the Teams user interface has some problems coping with differentiated permissions, which is what you’d expect because Teams uses the simplified group membership model. In any case, I dislike messing with SharePoint permissions because it’s easy to make mistakes to be either too permissive or too restrictive. And incorrect permissions have a nasty habit of exposing sensitive information to curious users. This truth became obvious for some tenants when they began using Delve, only to find that incorrectly set permissions allowed Delve to highlight some confidential files to users. In addition, we don’t know if changes like this will interface with how some aspect of Office 365 works in the future. (See this post for another view on the topic of changing SharePoint permissions).
The exercise proves the difficulty of erecting barriers within an application like Teams that is designed to enable collaboration. The lesson we might learn is that if you want to be highly specific about document permissions, you might be better off using a traditional SharePoint team site instead of one that depends on the group membership model.
Two Potential Solutions
But getting back to where we started, which is the scenario where you have a group or team that includes some guest users and want to protect documents against external access. If you want to solve the problem with out-of-the-box Office 365 functionality, I think you have two options:
- Use two separate group/teams. One holds the information you are willing to share with people outside the company; the other is for internal use only with no guest users. The problem here is that users might forget what context they are in when they store documents and end up making some confidential material available to external users by accident. However, on the plus side, the scheme is simple to implement, works, and doesn’t require any special training or software.
- Use rights management to protect confidential information. The basic idea behind rights management is that you define the rights that you want users to have over documents. Rights are operations like print and edit and different sets of users can be given different rights. When an author assigns a template to a document, the sets of users defined in the template can use their rights to access its content. Anyone who is not specified cannot open the document because they do not have the right to decrypt its protection.
Protecting a Document
Protecting a file is straightforward. Go to the backstage area of the file and select Protect Document, then Restrict Access, and finally select the protection template you want to use (Figure 1). When the app saves the document, it also applies the templates to secure the file.
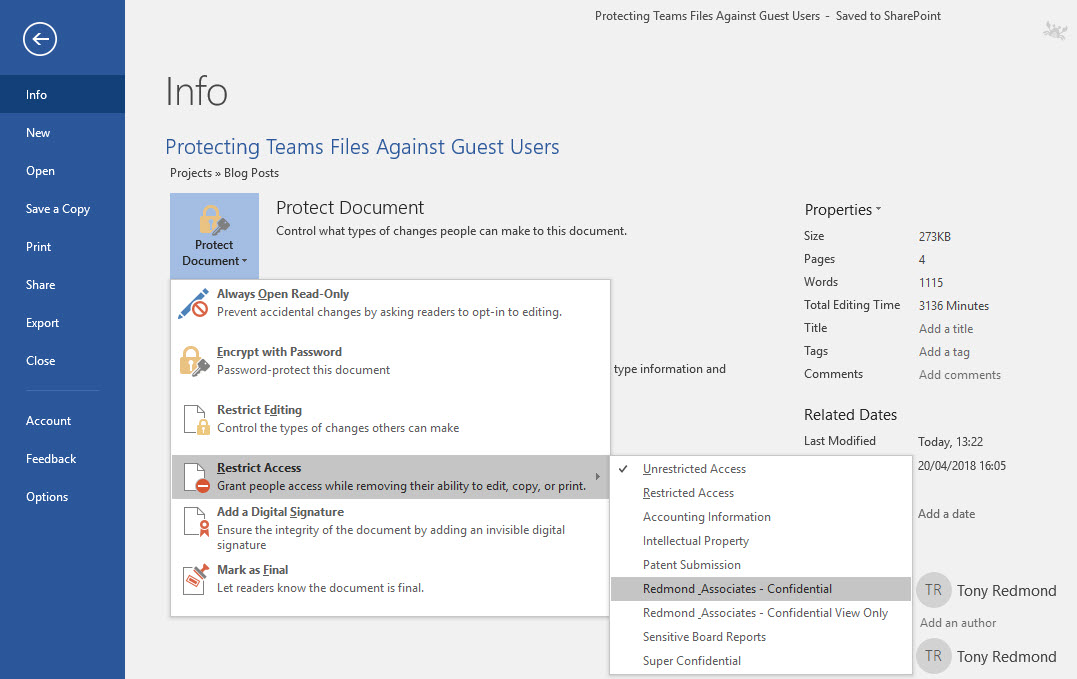
If you assign templates that restrict access to tenant users to documents, guest members can see that the documents exist and what their titles are because the metadata for the files are not protected. However, they cannot open the documents, even if they download copies to their workstation. Guest users might be frustrated because they know who created documents and what the titles of those documents are, but the content remains safe and secure.
Tenant users can use the desktop or mobile apps to open documents (Figure 2). They’ll see that the document is protected and can view the rights they have over the file.
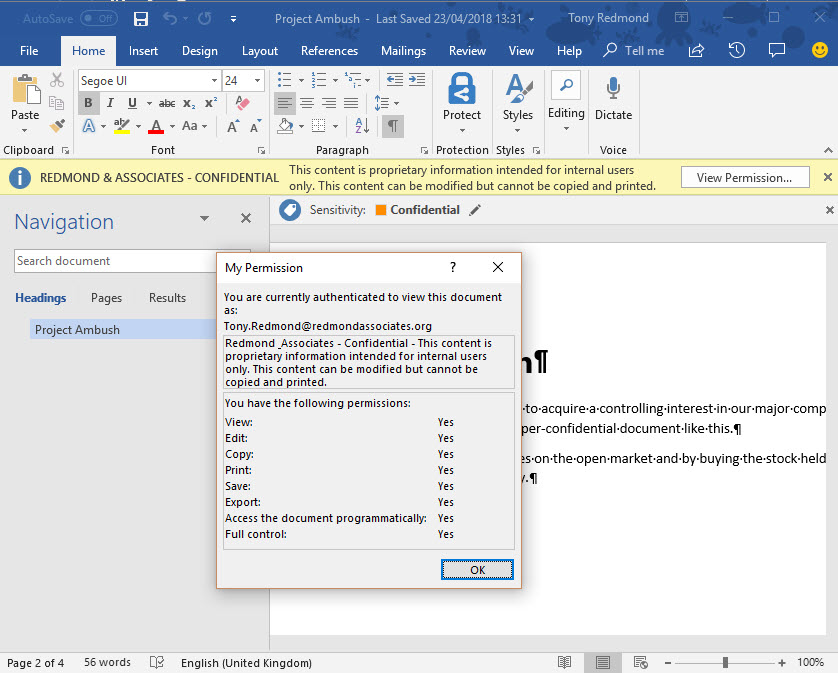
The good thing about using protection is that even if someone makes a mistake and puts a confidential document in the wrong place – or attaches it to email sent outside the organization – the protection remains with the document and no information can leak. This is critical in the era of regulations like GDPR that penalize companies heavily for data breaches.
Online Apps Cannot Open Protected Documents
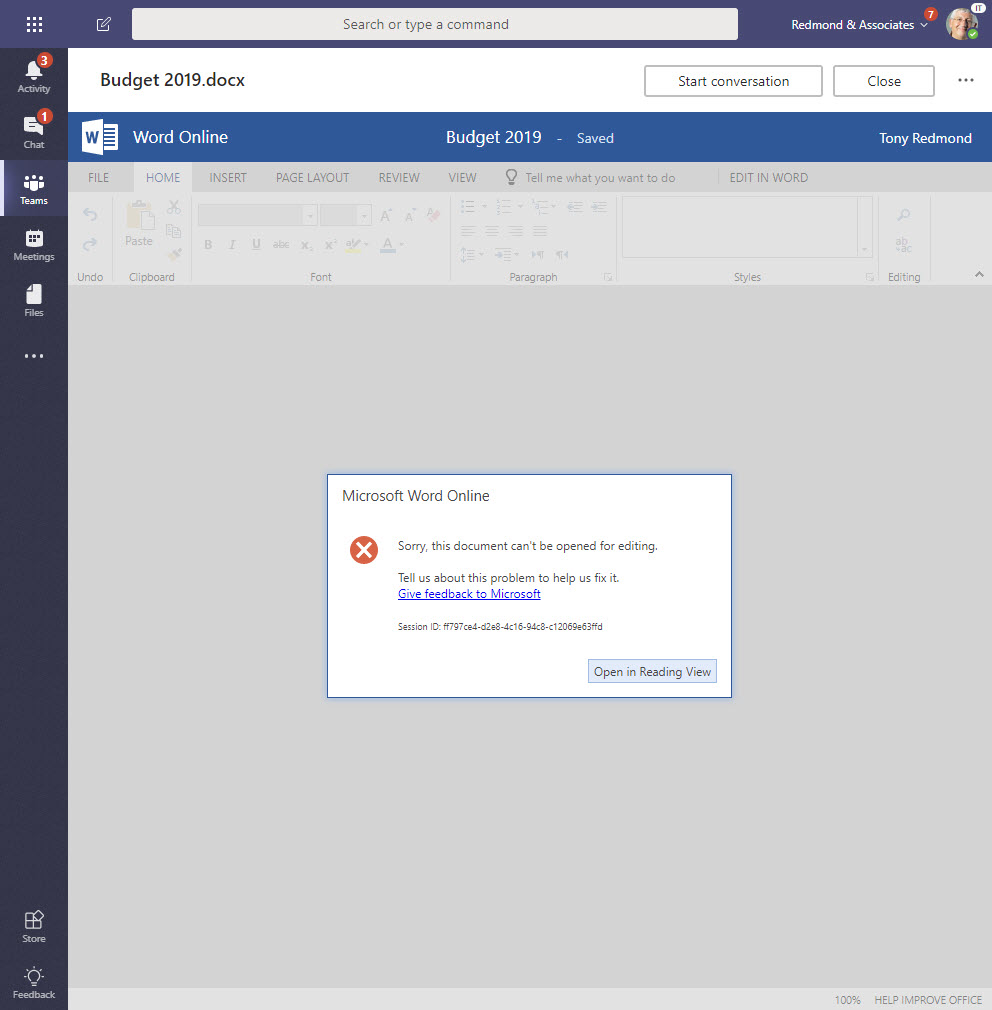
One downside of using rights management is that tenant users cannot edit or preview protected documents using the online apps (like Word Online – see Figure 3). Online apps can’t open protected files because these are not “RMS-enlightened applications” and cannot obtain the necessary licenses (see this article for more detail).
Visual Hints for Guests
To give guidance to guest users, the right way to set this up is to give them a visual clue by creating a channel with a name like “Confidential – Internal Documents” and protect everything placed in the document library folder belonging to the channel. If you use an Office 365 group (which don’t have channels), then just create a folder in the document library.
If a guest goes near a folder clearly marked for internal use only, they have no grounds for complaint when they cannot open the documents. Before anyone gets upset about guest users running into problems when they try to open a document, let’s understand that this is the same that happens if guests try to use third-party or internal apps available through channel tabs. Guests are unlikely to have access to those apps, but no on worries about that problem.
Unified Office 365 Labels Coming
Nothing good comes without effort. In the case of protection, tenants must create and publish suitable templates to allow users protect documents. Users is also necessary to help people understand how and when to apply protection.
When Microsoft unifies Office 365 classification labels with Azure Information Protection labels, it will be easier to secure documents. At that point, you will be able to use auto-label polices to find and protect sensitive documents automatically, and you’ll be able to apply a default classification label (and template) to a document library to protect every document in the library.
Helping Guest Users Do the Right Thing
Azure B2B Collaboration allows tenants to support guest users in Office 365 Groups and Teams. It’s nice to be able to collaborate with people outside your organization, but that’s no reason to reveal everything and anything to them. Protecting confidential information is an effective way to stop information leaking.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.




