Office 365 Makes Message Encryption Even Easier
Office 365 Encryption for All
In October 2017, I wrote about the refreshed Office 365 Message Encryption (OME) functionality that was just showing up around that time. I noted that new features and better client integration made it easier than ever before to protect messages, even between Office 365 tenants and other domains. Now, Microsoft has introduced a new protection policy called “Encrypt-Only” (or just Encrypt) to encourage users to protect sensitive email more than it happens today.
Simple Encryption is not Always Simple
Message encryption is a very old concept and well-regarded technologies like Pretty Good Privacy (PGP) and Secure MIME (S/MIME) have been in common use for many years. You can use S/MIME with Office 365 or find a PGP plug-in for Outlook, but in both cases the configuration can be tricky and involve several moving parts.
Although Microsoft would not say that their aim is remove the need for Office 365 tenants to use S/MIME, PGP, or other third-party encryption, it seems likely that providing an out-of-the-box solution that can encrypt messages to any email address is a powerful hint that this is their direction. And given that Microsoft controls a large percentage of the clients that access Exchange Online, they can make the encryption/decryption process much simpler and better integrated than any third-party software can.
How to Encrypt a Message
As explained in the previous article, you protect messages by applying a rights management template. The template can be one of the default set created when a tenant configures Exchange Online to support protection, or one created and customized through the Azure portal to meet a business need. Azure Information Protection is included and enabled for all tenants with the Office 365 E3 and E5 plans. Clients connected to all E3 and E5 tenants can read encrypted messages without any configuration, but the tenant IRM configuration must be right before clients can initiate an encrypted conversation.
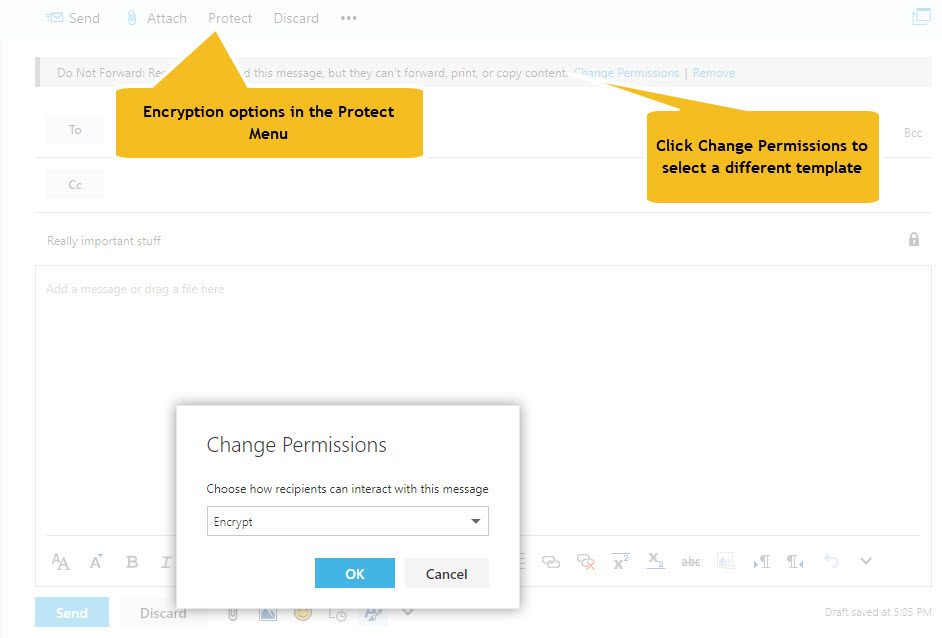
To encrypt a message with OWA, click the Protect button in the New Message window, then click Change Permissions in the message bar, and then select “Encrypt” from the set of available templates (Figure 1).
You can read encrypted messages using Outlook for iOS or Android, but you cannot create encrypted messages from these clients.
Protection with or Without Rights
Both encryption and protection use Azure Information Protection to secure messages inside encrypted wrappers. The difference is when you encrypt a message, it is solely to protect the content en route to the recipient and you don’t care what they do after they receive the message. If they like, they can print it to frame on the wall. While this isn’t protection in terms of action, the encrypt policy does enforce protection for access because the sender grants the recipient the right to decrypt the content.
When you apply a protection template to a message, it is to restrict what the recipient can do. For instance, if you apply the default Do Not Forward template to a message, it is both encrypted to ensure that anyone outside the recipient list cannot read it AND limited by the rights defined in the template. In this case, the template removes the right to forward the message. You can view the difference between the two in terms of trust. With encryption, the sender trusts the recipient and simply wants to protect the content en route to their mailbox. With protection, the sender does not trust the recipient (as much) and wants to restrict what the recipient can do after they receive a message. The important thing is that both approaches assure the sender that only authorized recipients can access a message and its attachments.
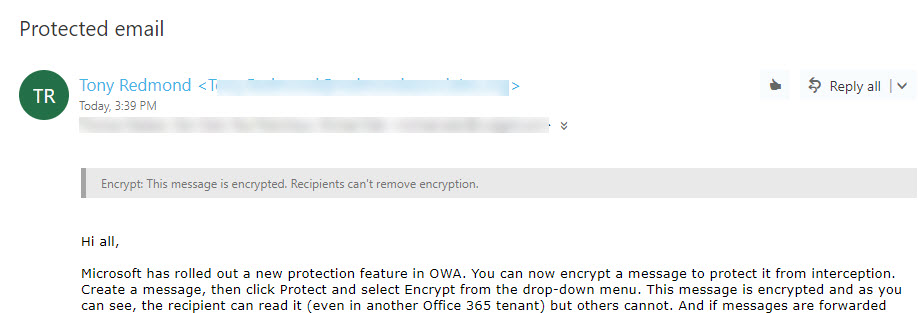
Automatic Decryption for Some Clients
Decryption is automatic if your mailbox belongs to an Office 365 tenant and you use an “enlightened” client (those that understand Azure Information Protection). The latest version of OWA and Outlook mobile handle decryption with aplomb (Figure 2).
The Outlook Experience
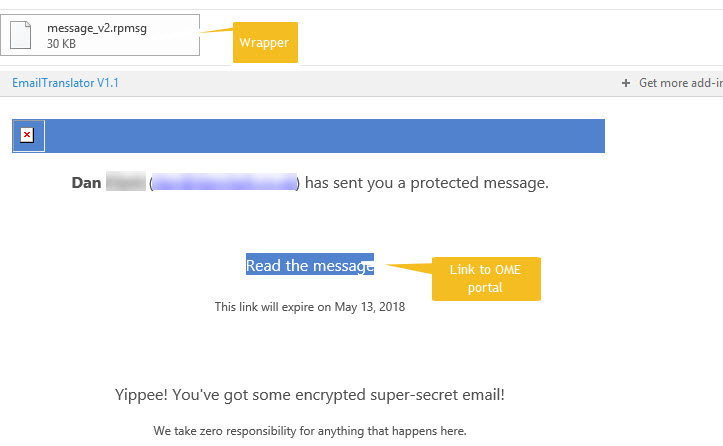
Although current versions of Outlook for Windows and Mac handle protected messages seamlessly, they need an upgrade to expose the option to encrypt messages and to be able to process encrypted messages. Until that upgrade is available, you must read encrypted messages using the Office 365 Message Encryption portal, which is the same experience as recipients outside Office 365 have.
Figure 3 shows how an unenlightened version of Outlook for Windows displays an encrypted message. Because this version of Outlook doesn’t know how to handle the file in the encrypted wrapper, it tells the recipient who sent the message and gives a link to the portal to read the message.
Stopping Auto-forwarding by Rule
Office 365 allows users to forward email to other destinations, including addresses outside the tenant. Good reasons might exist to forward email from a mailbox, but generally this is a bad habit that should only be permitted when good business reasons exist. You can check mailbox forwards with this code:
Get-Mailbox -RecipientTypeDetails UserMailbox, SharedMailbox | ? {$_.ForwardingAddress –ne $Null -or $_.ForwardingSmtpAddress -ne $Null} | Format-Table DisplayName, ForwardingAddress, ForwardingSmtpAddress, DeliverToMailboxAndForward
Even if allowed, because the forwarding address is not in the original recipient list, copies of encrypted messages forwarded by rules (either inbox rules or if a-forwarding address is set on the mailbox) are unreadable. This might not seem like a good thing, but attackers have been known to create rules to forward email from target mailboxes to learn about the normal ebb and flow of correspondence. When the attacker gains an insight into their victim, they launch a phishing attack to convince the victim to authorize a funds transfer or other payment for the attacker’s benefit.
To Encrypt or Protect, that is the Question
Given the choice to encrypt or protect messages, what should you do? Here’s a simple rule of thumb.
- Encrypt messages with confidential or sensitive data sent to recipients outside your organization.
- Protect messages with confidential or sensitive data sent to internal recipients or to recipients in domains you know respect the rights expressed in protection templates.
This rule of thumb is based on the simple fact that encryption works for all email addresses, so it is the catch-all solution when a need exists to protect content sent outside the company. Not every destination might be able to understand the limitations set by rights templates, but if a template is configured to support recipients in an external domain, it is an excellent way to protect information for the lifetime of the content.
No Great Conspiracy
Some will decry Microsoft taking steps to reduce the need for technology like S/MIME and PGP. I don’t consider this to be a grand plot for Microsoft to take over message encryption. Instead, it’s a new out-of-the-box method for users to protect sensitive information that does not need add-ons, plug-ins, or certificates. In the days of regulations like GDPR, I like anything that makes it simpler to protect sensitive data.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.