Protect iOS and Android Devices with Microsoft Defender for Endpoint
Microsoft Defender for Endpoint for iOS and Android devices is a mobile threat defense solution (MTD). Most organizations are in agreement that Windows devices require some form of antivirus and antimalware solution in order to be considered secure. Very few organizations, however, consider iOS and Android as platforms that require threat protection.
Whilst iOS and Android are typically considered to be “closed” platforms, they are still vulnerable to attacks from web-based sources, for example. In this guide, we’re going to explain how Microsoft Defender for Endpoint can help to protect iOS and Android devices from various online threats.
What is mobile threat defense?
Mobile threat defense solutions monitor risk through various mechanisms like OS version, firmware, known vulnerabilities, as well as scanning for activities that could be considered malicious.
Through Microsoft Endpoint Manager and Azure AD Conditional Access, we’re able to enforce policies based on a device risk score.
Why protect iOS and Android Devices?
Whilst mobile device management platforms are designed to manage mobile devices, mobile threat defense platforms provide mobile security by preventing, detecting, and remediating cyberattacks. They use techniques on the device, network, and application-level and feed critical information to the mobile device management platform to enable features such as Conditional Access.
Do iOS and Android devices need threat protection or antivirus? Absolutely. In today’s world where sophisticated threats are ever-present, mobile threat defense is vital.
Capabilities
| Capability | Description |
| Web protection | Anti-phishing, blocking unsafe network connections, and support for custom indicators. |
| Malware protection (Android-only) | Scanning for malicious apps. |
| Jailbreak detection (iOS-only) | Detection of jailbroken devices. |
| Threat and Vulnerability Management (TVM) | Vulnerability assessment of onboarded mobile devices. Visit this page to learn more about threat and vulnerability management in Microsoft Defender for Endpoint. Note that on iOS only OS vulnerabilities are supported in this preview. |
| Unified alerting | Alerts from all platforms in the unified Microsoft 365 security console |
| Conditional access, Conditional launch | Blocking risky devices from accessing corporate resources. Defender for Endpoint risk signals can also be added to app protection policies (MAM) |
| Privacy Controls (in preview) | Configure privacy in the threat reports by controlling the data sent by Microsoft Defender for Endpoint. Note that privacy controls are currently available only for enrolled devices. Controls for unenrolled devices will be added later |
| Integration with Microsoft Tunnel | Can integrate with Microsoft Tunnel, a VPN gateway solution to enable security and connectivity in a single app. Available only on Android currently |
Licensing Requirements
Microsoft Defender for Endpoint is available standalone, and it’s also included as part of select Microsoft 365 commercial subscriptions. Two different plans are available.
Microsoft Defender for Endpoint Plan 1
This plan includes antimalware and antivirus protection, attack surface reduction, manual response actions, centralized management, security reports, and APIs. It is also included as part of Microsoft 365 E3/A3.
Microsoft Defender for Endpoint Plan 2
This plan, formerly known as Defender for Endpoint, includes all features from Plan 1 plus many more features. The list of additions includes device discovery, threat and vulnerability management, threat Analytics, automated investigation and response, advanced hunting, endpoint detection and response, and Microsoft Threat experts.
Just like Plan 1, Microsoft Defender for Endpoint Plan 2 is available as a standalone license, but it’s also included for free with the following plans:
- Windows 11 Enterprise E5/A5
- Windows 10 Enterprise E5/A5
- Microsoft 365 E5/A5/G5 (which includes Windows 10 or Windows 11 Enterprise E5)
- Microsoft 365 E5/A5/G5/F5 Security
- Microsoft 365 F5 Security & Compliance
Prerequisites
The prerequisites for enabling Microsoft Defender for Endpoint on iOS and Android devices depend on the enrollment state of the devices themselves. Defender for Endpoint can be installed and managed on both enrolled and unenrolled devices.
A Defender for Endpoint license is required for end-users of the device.
- For enrolled devices:
- The Company Portal app is required in order to deliver the Microsoft Defender app to devices and is responsible for enforcing Intune’s compliance policies. This requires the end user to be assigned a Microsoft Intune license or a license bundle that includes Intune, such as Enterprise Mobility and Security, or Microsoft 365 E3/E5.
- The device must also be registered to the organization’s Azure Active Directory. This requires the end user to be signed in to the Microsoft Authenticator app.
- For unenrolled devices:
- The only requirement for unenrolled devices is that they are registered with Azure Active Directory. This requires the end user to be signed in to the Microsoft Authenticator app.
Microsoft Endpoint Manager integration
Through integrating Defender for Endpoint with Microsoft Endpoint Manager, we’re able to share risk information between platforms, exposing the capability to dynamically determine the health and compliance state of a device.
- Open the Microsoft Defender Security Center
- Navigate to Settings > Endpoints > Advanced features
- Set Microsoft Intune Connection to On
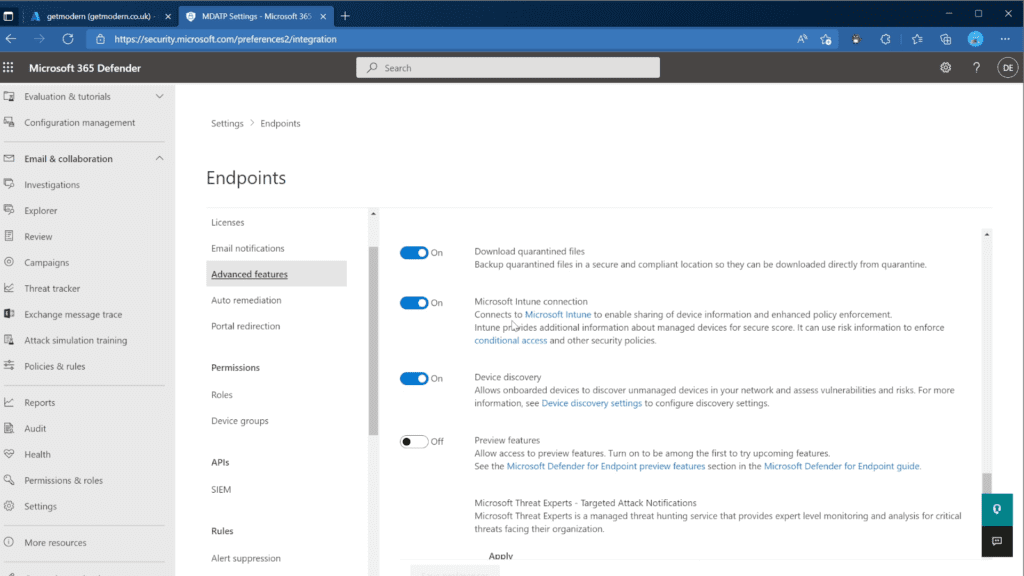
To ensure Defender for Endpoint can share compliance data with Microsoft Endpoint Manager, the feature must be enabled for iOS and/or Android devices.
- Open the Microsoft Endpoint Manager admin center
- Navigate to Endpoint Security > Microsoft Defender for Endpoint
- Set Connect iOS devices to Microsoft Defender for Endpoint to On
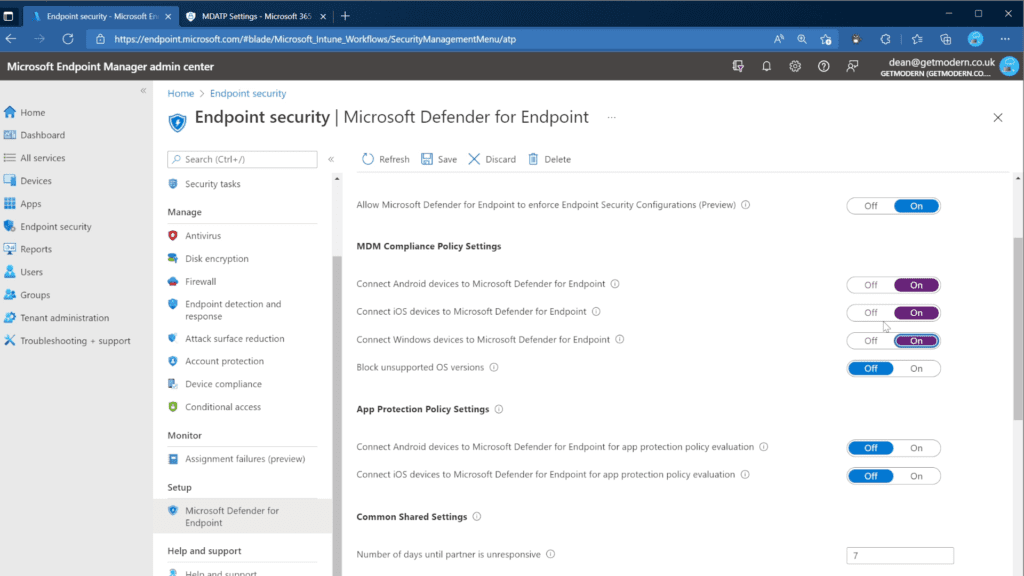
Microsoft Defender for Endpoint for iOS
The minimum system requirements for Microsoft Defender for Endpoint for iPhones and iPads is are iOS 13.0 and iPadOS 13.0 or above.
The deployment of Microsoft Defender for Endpoint on iOS can be done via Microsoft Endpoint Manager (MEM). Supervised, unsupervised, and even non-enrolled devices are supported.
Deploy the Defender for Endpoint app to enrolled iOS devices via Intune
- From the Microsoft Endpoint manager admin center, go to Apps > iOS/iPadOS > Add > iOS store app and choose Select.
- On the Add app page, choose Search the App Store and search for Microsoft Defender. Select Microsoft Defender.
- Select iOS 12.0 as the Minimum operating system and choose Next.
- In the Assignments tab, go to Required and select Add group. Target the assignment at a group containing users. Choose Select and then Next.
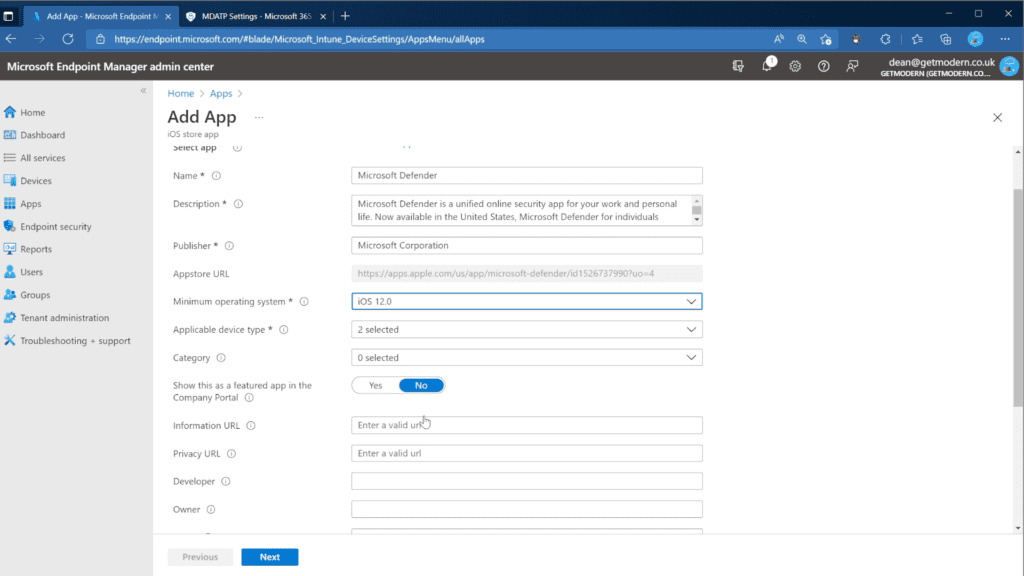
Additional steps for supervised devices via Intune
Microsoft has included additional capabilities within the Defender for Endpoint app for iOS that leverage the enhanced management capabilities exposed by supervised iOS and iPadOS devices. Through this enhanced management capability, the app can also enforce web protection without the requirement for a local VPN on the device, ensuring protection can be enabled without user interaction.
To configure the additional capability, follow these steps:
- From the Microsoft Endpoint Manager admin center, choose Apps > App configuration policies > Add, and choose Managed devices.
- In the Create app configuration policy page, provide the name, platform, and select Microsoft Defender for Endpoint from the list of targeted apps.
- Next, select Use configuration designer and set the following:
- Configuration Key: issupervised
- Value type: String
- Configuration Value: {{issupervised}}
- Select Next and configure an optional scope tag.
- On the Assignments page, assign a group – this should normally be set to All Devices. If this configuration is assigned to User groups, a user must sign in to a device before the policy applies.
Finally, we need to deploy a custom profile on a supervised device to enable enhanced anti-phishing capabilities:
- Download the configuration profile from https://aka.ms/mdeiosprofilesupervised
- From the Microsoft Endpoint Manager admin center choose Devices > iOS/iPadOS > Configuration profiles > Create profile.
- Choose to Import a configuration profile file, and import the downloaded profile.
- In the Assignment section, deploy this to All Devices, and Select Next.
Zero-touch onboarding for iOS (unsupervised devices)
This feature is currently in Public Preview.
Admins can configure Microsoft Defender for Endpoint to deploy and activate silently, even on unsupervised iOS devices.
To achieve this, a deployment profile is created by the IT admin and assigned to a User group (device groups are not supported for this workflow). Once assigned the user is notified of the installation and Defender for Endpoint is automatically installed without user interaction.
- In the Microsoft Endpoint manager admin center, go to Devices > Configuration Profiles > Create Profile.
- Choose Platform as iOS/iPadOS, Template, and Profile type as VPN. Select Create.
- Choose a name and click Next
- Select Custom VPN for Connection type and in the Base VPN section, enter the following:
- Connection Name: “Microsoft Defender for Endpoint”
- VPN server address: 127.0.0.1
- Auth method: “Username and password”
- Split Tunneling: Disable
- VPN identifier: com.microsoft.scmx
- Enter the key SilentOnboard and set the value to True.
- In the Type of automatic VPN choice, set “On-demand VPN”
- Select Add for On Demand Rules, select I want to do the following as Establish VPN, and I want to restrict to to All domains.
- Select Next and assign to a User group.
- Select Create.
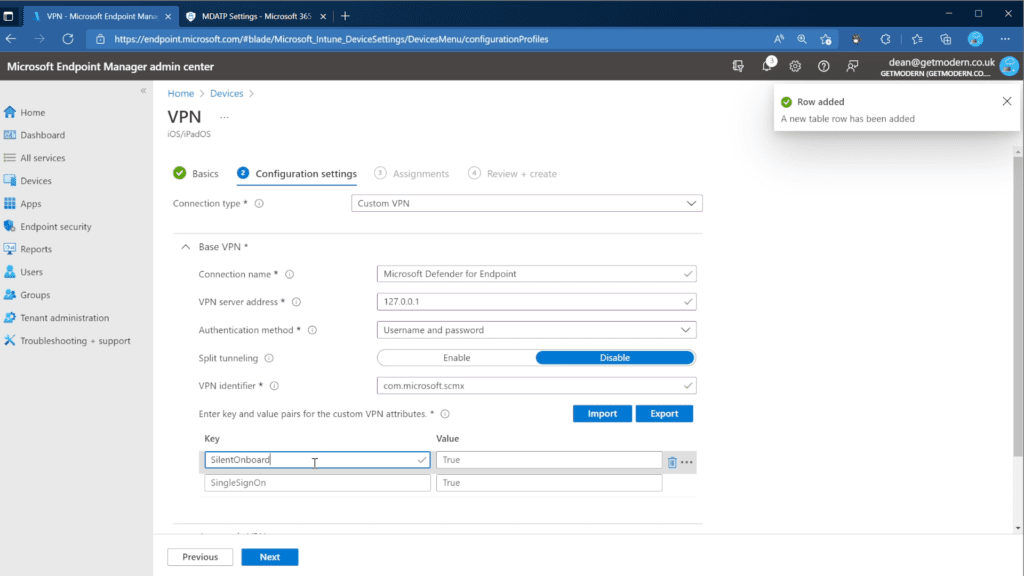
Once complete, the Microsoft Defender for Endpoint app will be deployed and silently onboarded. The device will be visible in the Microsoft Defender Security Center.
Deploy Microsoft Defender for Endpoint on unenrolled iOS Devices
Where an organization wants to permit users to access corporate resources from their personal, non-corporate and unenrolled device, Microsoft Defender for Endpoint on iOS supports this through mobile app management App Protection Policies (APP).
App Protection Policies ensure that an organization’s data is secured within a managed app by containerizing and encrypting the application data itself, separate from the OS. By leveraging Intune’s App Protection Policies, Organizations can extend their protection to all devices that can access corporate data.
If App Protection Policies for iOS devices are already in place, the feature can be enabled by completing step 4 in the following workflow:
- In Microsoft Endpoint Manager admin center, go to Apps > App Protection Policies > Create Policy > iOS.
- Add the apps that can be used to access corporate data.
- Configure the App Protection Policy for Data Protection and Access Requirements per the Microsoft Documentation.
- In Conditional Launch, scroll to Device Conditions and configure the Maximum Device Threat Level.
- Choose a Value from the available options, and decide whether to Block access or Wipe data.
Defender for Endpoint on iOS user experience for enrolled (unsupervised) devices
With enrolled devices, users will notice an additional app installed on their iOS device named “MS Defender”.
By clicking into the app, users can access various bits of information about their device.
Microsoft Defender for Endpoint for Android
The minimum system requirements for Microsoft Defender for Endpoint for Android are Android 6.0 and above, and deployment can be done via the Intune Company Portal. To support Intune Device Compliance policy enforcement, devices must be enrolled.
Android Enterprise Mode support
Personally-owned devices with work profiles and corporate-owned fully managed user device enrollments are supported in Android Enterprise.
Deploy the Microsoft Defender for Endpoint App to enrolled Android enterprise devices via Intune
- In the Microsoft Endpoint Manager admin center, go to Apps > Android Apps > Add and select Managed Google Play app.
- Search for and select Defender for Endpoint in the managed Google Play page.
- In the app page, select Approve.
- Review the approval options and choose Done.
We can also leverage app configuration policies to auto-grant applicable Android permissions so the user doesn’t need to manually approve them.
- From the Microsoft Endpoint Manager admin center, choose Apps > App configuration policies > Add, and choose Managed devices..
- In the Create app configuration policy page, enter the following details:
- Name: Microsoft Defender for Endpoint.
- Choose Android Enterprise.
- Choose Work Profile only as Profile Type.
- Click Select App, choose Microsoft Defender for Endpoint, select OK and then Next.
- In the Settings page, select Permissions and choose Add. Select the following permissions:
- External storage (read)
- External storage (write)
- Choose the Permission state drop-down, select Autogrant, and then select Next.
- Assign the configuration to the same group that the Defender for Endpoint was assigned to.
Deploy Microsoft Defender for Endpoint on unenrolled Android Devices
Microsoft Defender for Endpoint on Android supports the protection of unenrolled Android devices through mobile app management App Protect Policies, just like iOS. A single App Protect Policy can be deployed to cover both iOS and Android
If App Protection Policies for Android devices are already in place, the feature can be enabled by completing step 4 onwards in the following workflow:
- In the Microsoft Endpoint Manager admin center , go to Apps > App Protection Policies > Create Policy > Android.
- Add the apps that can be used to access corporate data.
- Configure the App Protection Policy for Data Protection and Access Requirements per the Microsoft Documentation.
- In Conditional Launch, scroll to Device Conditions and configure the Maximum Device Threat Level.
- Choose a Value from the available options, and decide whether to Block access or Wipe data.
What Data is Collected by Defender for Endpoint on Mobile Devices?
Defender for Endpoint collects information from protected devices in order to improve the platform and support the service. Data is stored in the same tenant as Microsoft Defender for Endpoint.
Required Data Collection From Android Devices
Data is key to ensuring Microsoft Defender for Endpoint works as expected. Information related to the end-user, organization, devices being used, and apps is collected and processed in order to provide the service.
For example, information related to apps considered to be malicious is collected. This includes the installation source, the location of the Android APK as well as the date and time of installation and any specific permissions granted. It’s possible to configure Microsoft Defender for Endpoint to collect information about all apps installed on a device, although this is not enabled by default.
Where Web Protection detects or blocks a malicious site, the full URL of that site and any connection information and protocol are collected.
Required Data Collection From iOS Devices
The list of data collected from protected iOS devices is quite a lot shorter than the Android equivalent. For example, no information related to apps is collected, and the service also doesn’t collect where a malicious website is detected or blocked: Only the Domain name and IP address of the site are collected.
Information related to the device itself, as well as any signed-in user information and UPN is collected, along with the Azure AD information related to both.
Known Issues
A full list of known issues for iOS and Android is provided by Microsoft.
Data Usage
Due to the VPN / loopback adapter required to deliver protection, the iOS Settings app has been shown to report 1.5/2x the amount of data transfer. It’s important to note that the amount of data being transferred is not affected, and this can be verified by contacting the mobile service provider to confirm their metrics.
Video Guide
I’ve created a video guide for the iOS process described in this article so that you can follow along as I implement the solution.
That’s it for our guide on how to set up Microsoft Defender for Endpoint for iOS and Android devices, which can really help to protect these devices from various online threats. The cybersecurity landscape is evolving constantly, and mobile threat defense is just one big perk of Microsoft’s complete endpoint security solution.
Related Article:
Table of contents
- What is mobile threat defense?
- Why protect iOS and Android Devices?
- Capabilities
- Licensing Requirements
- Prerequisites
- Microsoft Defender for Endpoint for iOS
- Deploy the Defender for Endpoint app to enrolled iOS devices via Intune
- Additional steps for supervised devices via Intune
- Zero-touch onboarding for iOS (unsupervised devices)
- Deploy Microsoft Defender for Endpoint on unenrolled iOS Devices
- Defender for Endpoint on iOS user experience for enrolled (unsupervised) devices
- Microsoft Defender for Endpoint for Android
- What Data is Collected by Defender for Endpoint on Mobile Devices?
- Known Issues
- Video Guide



