Nested Microsoft 365 Groups: What You Need to Know

Nested Microsoft 365 groups refer to the practice of creating a group within another group in the Microsoft 365 ecosystem using the dynamic functionality in Azure AD. For IT admins, this practice lets them organize groups in a hierarchical manner, enabling a more structured approach to managing access, permissions, and collaboration within an organization. Membership of the dynamic group is handled by syntax in Azure AD. Instead of managing a flat list of members, dynamic rules handle that administration for you.
What is a nested Microsoft 365 group?
Nested Microsoft 365 groups are a new feature available in preview in Azure Active Directory (Azure AD), now part of Microsoft Entra. They allow admins to create Azure AD dynamic groups and administrative units that can add members from other groups using the ‘memberOf’ attribute. Apps that previously couldn’t read group-based membership in Azure Active Directory can now read the entire membership of these new groups.
These dynamic Azure AD security groups can be used for apps as well as licensing assignments. The following diagram courtesy of Microsoft explains how you can create a dynamic group with members of both Security-Group-X and Security-Group-Y, all while preventing members of the sub-groups within these two groups to members of a dynamic group.
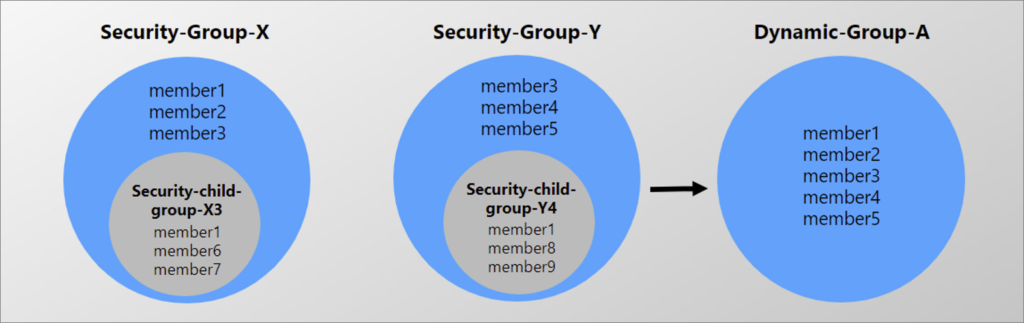
You can create a parent-child relationship by nesting groups, where the parent group contains one or more child groups. The parent group can define broad permissions and settings that apply to all child groups within it, while the child groups can have their specific settings and membership.
As this has been available in preview since around March of 2023, admins can configure dynamic groups with the memberOf attribute in the Azure portal, Microsoft Graph, and PowerShell. Security groups, Microsoft 365 groups, and other groups that are synced from on-premises Active Directory can also be added as members of these dynamic groups, and they can also all be added to a single group.
There are some best practices to take note of. User access, group reports, Azure active directory groups, and especially local groups, global groups, and universal groups can all be managed in this way. Distribution group members can be a member of another group, thus creating, in essence, dynamic distribution lists.
How do I create a nested Microsoft 365 group?
The main prerequisite for creating a nested Microsoft 365 group is permissions. The user account you plan to use to create these groups needs to be in one of the following roles: Global Administrator, Intune Administrator, or User Administrator. Also, you need to have an Azure AD Premium P1 or P2 license.
You can use the Azure portal, Microsoft Graph, and Powershell to create a nested Microsoft 365 group. Let me go through the steps in the Azure portal:
- First, I will log into my Microsoft 365 Developer tenant and access the Azure portal.
- Next, click Groups on the left and click the New group button on top.
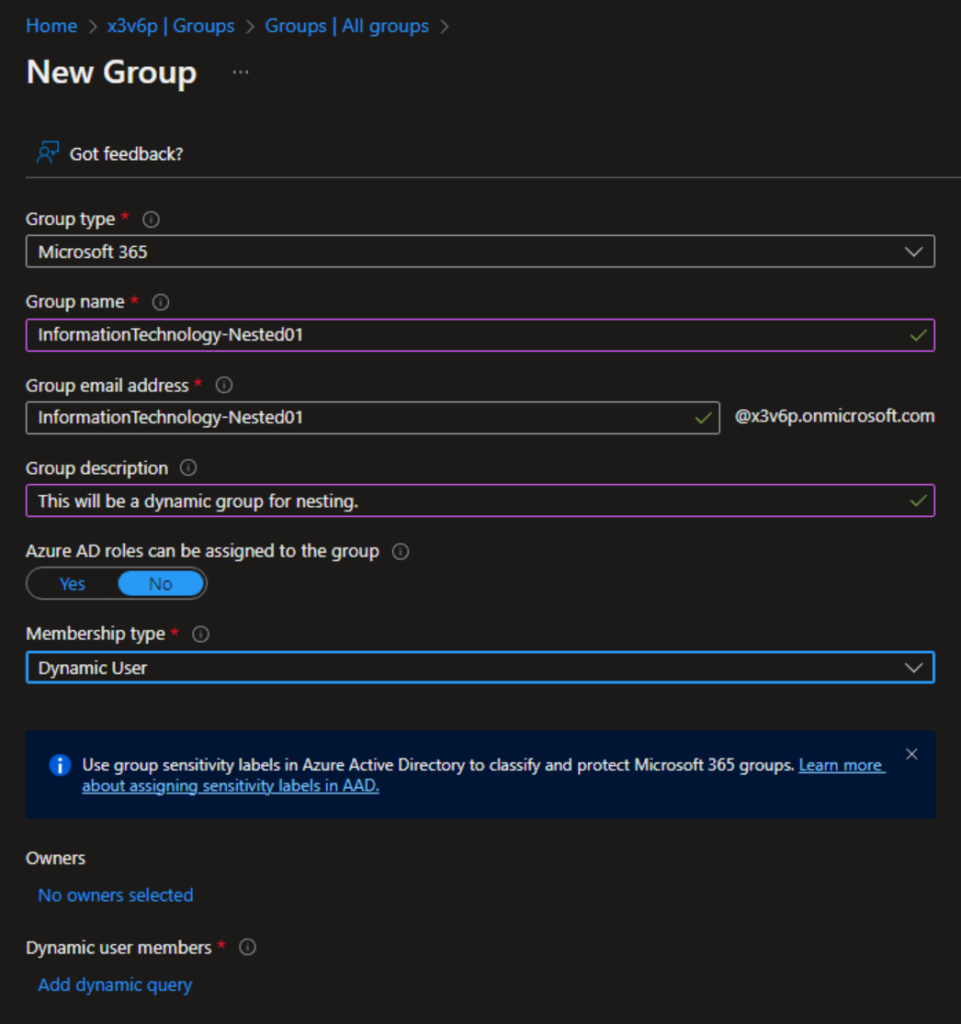
- Here, I have chosen the Microsoft 365 group type, entered a Group name, confirmed the email address is available, and entered a Group description.
- In the Membership type, I chose Dynamic User.
- Next, I will click the Add dynamic query link at the bottom.
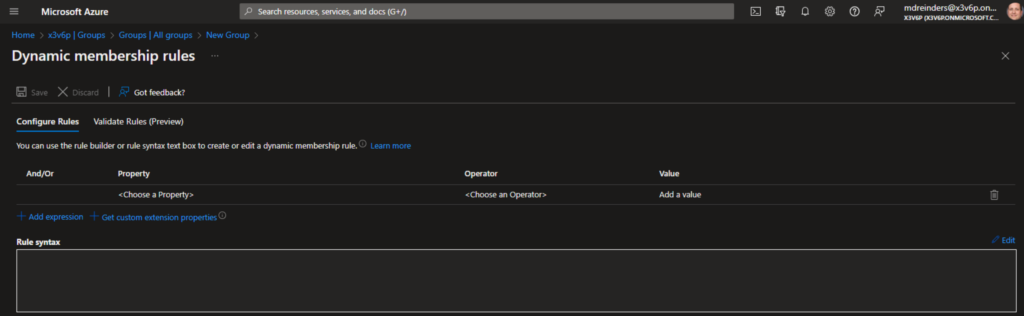
- Because the ‘MemberOf’ attribute is not yet supported, we need to click the ‘Edit‘ button in the upper right corner of the ‘Rule syntax’ field.
Note: Here is the general syntax you can add when using the ‘User’ side of things:
user.memberof -any (group.objectId -in ['groupId', 'groupId'])
- Here, I can replace the ‘groupId’ items with actual group IDs from valid existing groups. I will do that and you can see the final syntax here.
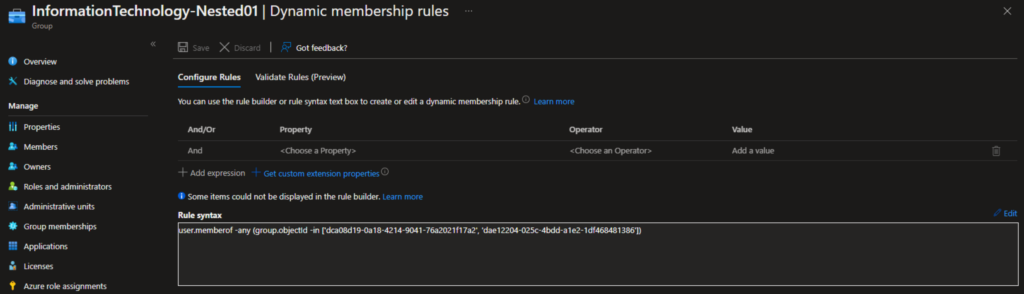
- After a few minutes – dynamic group membership processing can take many hours – I refreshed the view of the groups in my tenant. I opened our new group and went to the Members list on the left.
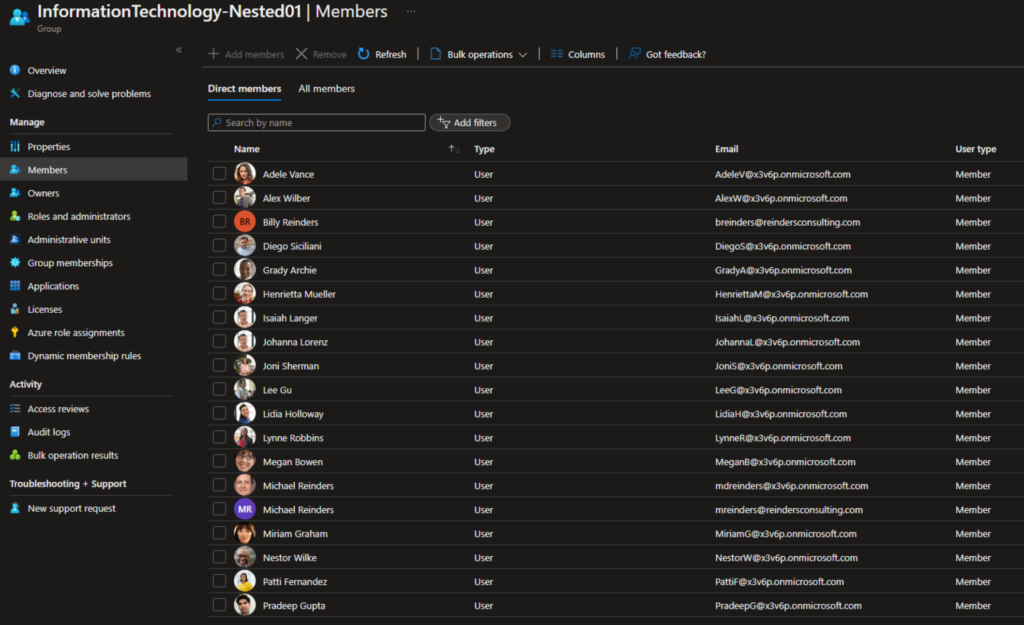
Like magic, there are 19 users in the list. There are two users in one of the groups and 17 in the other. Because the dynamic query mentions ‘OR’, all users in either of the two groups will dynamically be added to this new group. If you were to add a user to one of the two groups, they will automatically be added to our new group. And yes, this can get complicated really fast!
Current limitations of nested Microsoft 365 groups
Microsoft documentation offers some limitations IT Pros need to be aware of during the ‘Preview’ timeframe.
- Each Azure AD tenant is limited to 500 dynamic groups using the memberOf attribute. memberOf groups do count towards the total dynamic group member quota of 5,000.
- Each dynamic group can have up to 50 member groups.
- When adding members of security groups to memberOf dynamic groups, only direct members of the security group become members of the dynamic group.
- You can’t use one memberOf dynamic group to define the membership of another memberOf dynamic group. For example, Dynamic Group A, with members of groups B and C in it, can’t be a member of Dynamic Group D).
- MemberOf can’t be used with other rules. For example, a rule that states dynamic group A should contain members of group B and also should contain only users located in Redmond will fail.
- Dynamic group rule builder and validate feature can’t be used for memberOf at this time.
- MemberOf can’t be used with other operators. For example, you can’t create a rule that states “Members Of group A can’t be in Dynamic Group B.”
Nested Microsoft 365 groups offer several benefits
Dynamic groups in Azure Active Directory offer a powerful and automated approach to user access management. By leveraging user attributes and predefined rules, organizations can streamline administration, enhance security, and adapt to dynamic changes within their user base, ensuring appropriate access at all times.
Here are the four main benefits you can expect by using nested Microsoft 365 groups:
- Simplified management: Instead of configuring settings and permissions individually for each group, you can set them at the parent level and have them automatically applied to all child groups. This streamlines administration and reduces the effort required to manage multiple groups.
- Efficient collaboration: Nested groups enable better organization and segmentation of teams or departments within an organization. Members can collaborate within their specific child groups while still having access to resources and communication within the parent group.
- Flexibility and scalability: As your organization grows and evolves, nested groups provide a scalable structure for managing access and permissions. You can easily add or remove child groups as needed without disrupting the overall hierarchy or group settings.
- Consistency and security: By defining settings at the parent group level, you can ensure consistent access controls and security measures across all child groups. This helps maintain data integrity and ensures that appropriate permissions are enforced throughout the nested structure.
If you have any questions or comments about this topic, please leave one below. Thank you for reading!



