Office 365 Audit Logging Generates Lots of Data – and Some Odd Entries
A Single Audit Mart for Everything in Office 365
About two years ago, Microsoft set out to create the unified Office 365 audit data mart. The idea was simple. Instead of every application having its own way to generate and report audit events for user and administrator actions, the audit data mart would be a common repository for Office 365. Applications continue to generate events and the pipelines ingest those events into the data mart. At the same time, transformation occurs by applying common schema application-specific data so that the audit events have common fields.
Things started slowly. Exchange and SharePoint were the first applications to generate events. Azure Active Directory joined the party followed by other applications like Teams and even Sway. Microsoft sped up ingestion processing so that events now appear within an hour (and often sooner) rather than lagging by 24 hours as happened for some sources. In short, a great deal of work over two years constructed a robust audit recording system.
As good as the progress has been, some inconsistencies and challenges still lurk. Here are some of my observations.
Some Applications Are Chatty, Some Are Not
In the world of Office 365 audit records, some applications are chatty and generate many audit records and some are terse. SharePoint is the most granular of all applications and records multiple audit records for what you might think are relatively simple operations. Take the example of applying a classification label, updating the title, and editing some of the properties for a document in a SharePoint library. You might see the first six audit records listed in Table 1 and the seventh if OneDrive for Business synchronizes the document library.
| Operation | Item | Reason |
| Accessed file | Dispform.aspx | Display document properties |
| Accessed file | Editform.aspx | Edit document properties |
| Accessed file | Upload.aspx | Upload changes |
| ComplianceSettingChanged | Document URL | Apply label to document |
| Modified file | Document name | Update document with new title. |
| FileModifiedExtended | Document URL | Update file properties. |
| Downloaded files to computer | Document name | OneDrive for Business synchronization |
Table 1: SharePoint audit records for changes to a document
It is reasonable that SharePoint is careful about recording what users do to documents. After all, many tenants use SharePoint as a document management system and want to know who did what and when. The results for other applications are less granular. Teams, for instance, records when users connect to the service, update settings, or add or change channels, but not much else. Planner does not support auditing and I have seen no trace of Yammer audit events in the log. Exchange does generate both mailbox and administrative audit events, but you must configure mailbox auditing to capture this information.
On the upside, good auditing exists for eDiscovery operations generated within the Security and Compliance Center. All this proves that Office 365 auditing is still a work in progress.
Limited Availability of Audit Data
Operating at the scale of Office 365 means the capture of truly massive amounts of audit records daily. To limit the resources needed for the audit data mart, Microsoft only keeps audit data for 90 days. This is not a hard limit and data might exist for 92 days or 93 days, but sometime soon afterwards the data are gone.
Obviously, some tenants want to be able to access audit data for longer. Microsoft’s solution is Office 365 Advanced Security Management (ASM), part of the E5 plan or available as a monthly add-on. ASM ingests audit day into its own store and keeps it for 180 days. You must license every user whose data you want ASM to manage, so at $3/user per month the cost can be considerable. On the upside, ASM does a lot more than audit management and you should evaluate ASM on that basis.
Cogmotive Discover and Audit is much cheaper than ASM and keeps audit data for much longer. Although it does not have the same kind of intelligence built into ASM to detect and highlight security anomalies, the Cogmotive product delivers very flexible search and reporting capabilities for Office 365 audit events.
Extracting to Another System
Because Office 365 keeps audit records for a limited time, some prefer to move Office 365 audit data to another system. The process to extract and format information can be challenging. A busy Office 365 tenant can generate many audit entries, especially if people make heavy use of SharePoint and OneDrive for Business. A good rule of thumb is to expect 50-200 audit records per day per active user. However, your mileage varies depending on what applications people use. Heavy users of SharePoint and Teams create more audit data than those who simply send some email. The Search-UnifiedAuditLog cmdlet (part of the Exchange Online cmdlet set) can find the records, but then you must extract the necessary information and pass it to the target system (here is a good example of the process used in one situation).
Some Odd Audit Entries
As you might expect, auditing captures both user-initiated and system-initiated events. My difficulty here is that Microsoft explains the system-initiated events poorly. For example, what does the “app@sharepoint” job do precisely? It is certainly a busy beast and accesses documents in different sites (Figure 1). It seems like this might be the user name assigned to Search Foundation activities because every time someone updates a file, an audit record for app@sharepoint appears soon afterwards, perhaps when the crawler reprocesses the file.
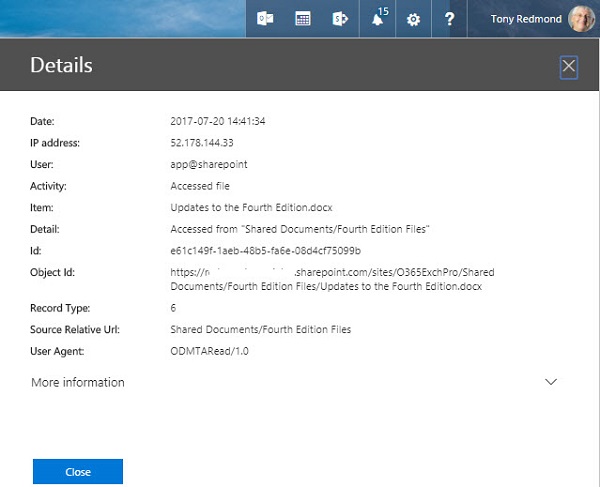
app@sharepoint also turns up elsewhere, notably after the membership of an Office 365 group changes and the change replicates to the group for the SharePoint team site.
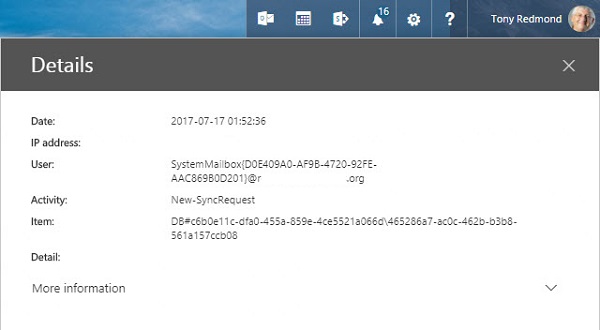
Figure 2 shows another strange audit entry. In this case, a system mailbox (presumably in Exchange Online) generates a new synchronization request audit record. Why?
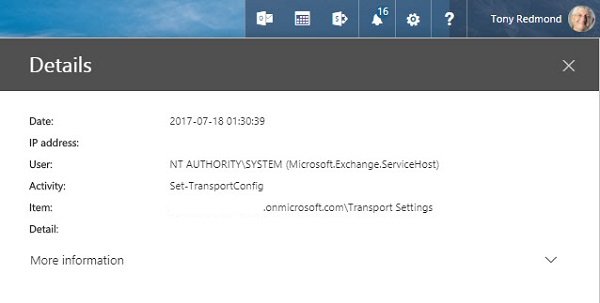
Last, Figure 3 shows an audit record that I can explain. This is an example of an Exchange administrative audit event created by an Exchange Online background process to update the transport settings for the tenant.
All these audit entries are valid and I am sure that all the actions they capture are essential. However, that is not the problem. The issue is that tenant administrators do not know that these are system events. They can guess and experienced administrators are likely to work out what events cause the capture of these events, but it would be much simpler if Microsoft labelled them as “system events.”
Connector Events
Another oddity is when you see a batch of audit events recording when someone sends a message using the SendAs permission. Usually this happens when a delegate sends a message from another user’s mailbox. But if you configure an Office 365 connector to direct a Twitter feed into a group, you will see a blizzard of audit events. It is as if someone hyper actively used their delegate permission to spam the world. In fact, Exchange logs an audit event for each tweet downloaded through the connector (Figure 4).
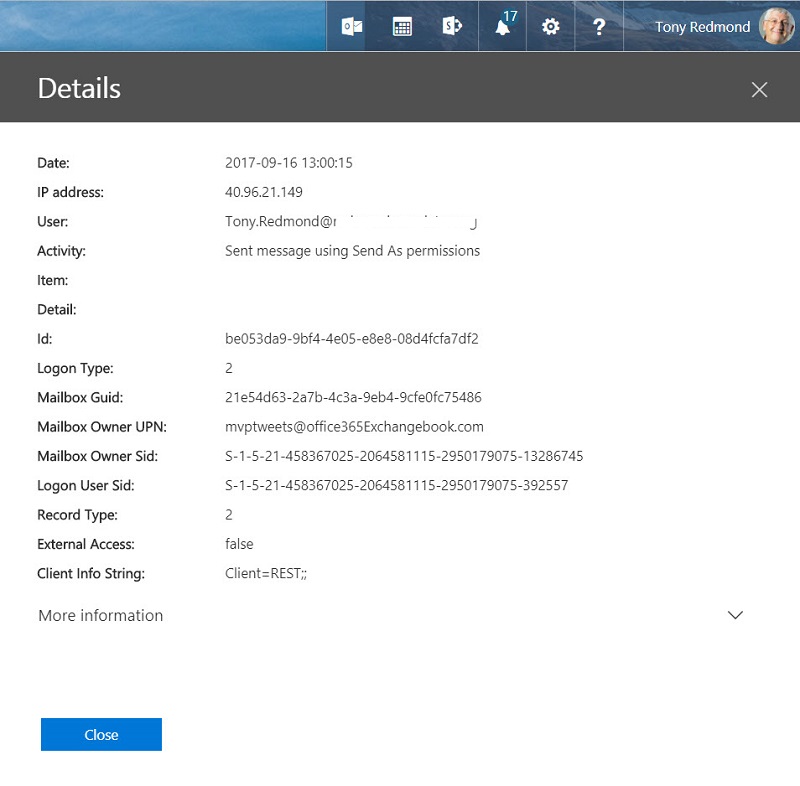
These audit events are worse than useless when it comes to tracking potential misuse of delegate permissions and are probably caused by a bug in the connector.
More Auditing to Come
Office 365 expands all the time and more applications generate audit events. That means that understanding the events captured in the audit log becomes harder because of the quantity and variety of data. Microsoft has done a good job to corral some cats to create a common audit structure for Office 365. The trick now is to make everything even smoother.
If you want more information about Office 365 audit events and you are at the Ignite conference next week, come along to the “Decoding audit events in Microsoft Office 365” session (1:15pm in Expo Theatre #5, Monday, Sept 25). Fellow MVP Alan Byrne and I will try to throw some light onto this topic.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.