Microsoft Releases Sensitive by Default Upload for SharePoint Online
Sensitive by Default Now Available for Office 365 Tenants
On January 27, the mark new files as sensitive by default feature reached general availability status. The idea is to block external access to Office files uploaded to SharePoint Online document libraries until the Office 365 Data Loss Prevention (DLP) engine has determined that no sensitive data exists in the files.
Data Loss Prevention and SharePoint Online
DLP processing for SharePoint Online is not immediate. Background jobs run periodically to detect and process policies for new files that users have created or uploaded to libraries. The period between a new file appearing in a library and DLP processing varies and could take several hours, depending on factors such as service load. During this time, the possibility exists that users might share files containing sensitive data externally and so cause data leakage.
Real-time DLP processing for SharePoint Online might be technically possible, but it would take a lot of reengineering. Unlike Exchange Online, SharePoint doesn’t have a choke point where all data must pass through before it passes out of an organization. Exchange Online uses the transport pipeline for this purpose, and transport rules ensure that policies are applied to all messages as they pass through the pipeline. By comparison, SharePoint Online applies DLP policies as new files are crawled and indexed.
Restricting Sharing
Office 365 tenants can restrict external sharing by limiting the scope of the sharing settings in the SharePoint Online Admin Center (Figure 1). These settings also affect the ability of users to share from their OneDrive for Business accounts with the rule being that the setting applied to OneDrive can only be as permissive as that applied to SharePoint Online.
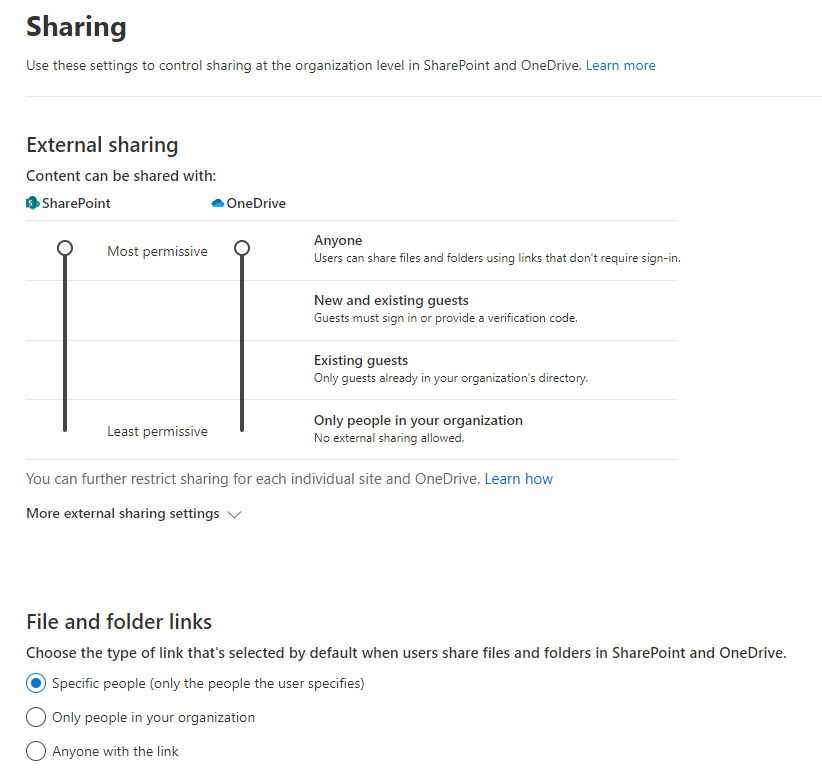
The price of restricting sharing is that it limits the ability of people to collaborate outside the company and can also remove functionality. For example, if Anyone (anonymous access) links are prohibited, the OneDrive Request Files feature isn’t available.
What Sensitive by Default Does
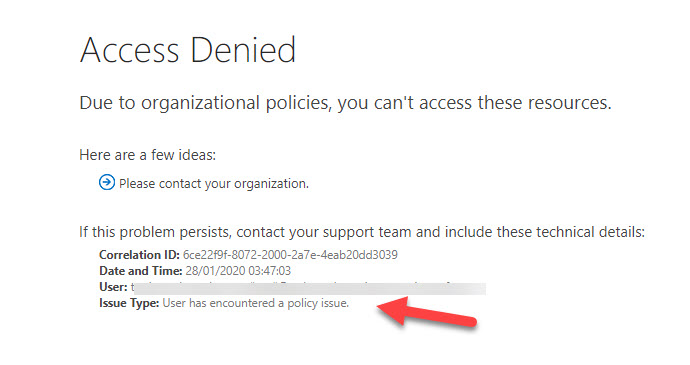
Instead of disabling external sharing completely, Microsoft’s solution is to implement a new tenant-wide setting for SharePoint Online. When set, any new file uploaded or created in SharePoint Online is deemed sensitive until it is processed by DLP. Users can share files after they are in SharePoint, but external users (including guests in Office 365 Groups) won’t be able to access the content until DLP processing is over (Figure 2), which could take several hours.
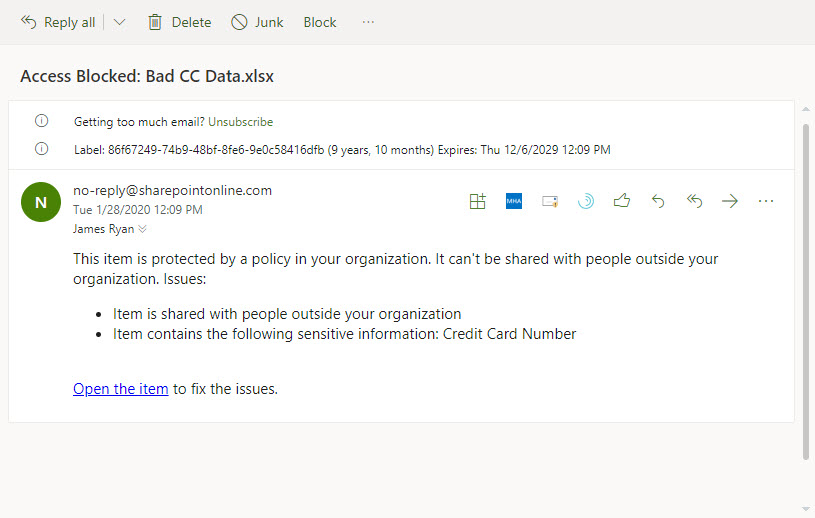
After DLP processing, the file will either be deemed sensitive and continue to be protected as per the policy settings, or not sensitive, in which case the standard SharePoint sharing settings apply and the user is notified that DLP has detected some sensitive data in a file (Figure 3).
Blocks are not applied to existing SharePoint content as DLP processing is limited to new files. Sensitive by default is covered in the Office 365 E3 and E5 plans.
Tenant-Wide Setting
The important thing is that Sensitive by Default is a tenant-wide setting. You can’t enable it for specific SharePoint sites, and you can’t enable it unless you already have at least one DLP policy configured to process all SharePoint sites. Sensitive by Default is not yet available for OneDrive for Business, but Microsoft says that they’re working on this feature and it should be available soon.
Enabling Sensitive by Default
Sensitive by Default can only be enabled by running the Set-SPOTenant cmdlet from the SharePoint Online PowerShell module. To enable Sensitive by Default, run this command:
Set-SPOTenant –MarkNewFilesSensitiveByDefault BlockExternalSharing
To disable the feature, run this command:
Set-SPOTenant -MarkNewFilesSensitiveByDefault AllowExternalSharing
It can take up to 15 minutes before a policy change is effective within a tenant.
Better Protection with Sensitivity Labels
The Sensitive by Default feature solves an immediate problem for some Office 365 tenants but it’s a crude broad brush way to block access to external people. A better approach might be is to assign Office 365 sensitivity labels to important, confidential, or sensitive content stored in SharePoint Online. The labels can encrypt the files and make sure that only people with rights to access the content can interact with it, even if files are downloaded from SharePoint.
Microsoft is doing a lot of work to make sensitivity label more useful (like the preview feature for using auto-label policies to find and protect large quantities of Office files stored at rest) and to remove some blocks for deployment that exist today (like being unable to index protected content). Anyone planning how to best protect confidential SharePoint data should focus on sensitivity labels because they are a better, more functional, and precise solution.



