Microsoft Launches External Access Block Policy for Groups, Teams, and Planner
A New Approach
When Microsoft introduced external guest access for Office 365 Groups in September 2016, they built the new mechanism on top of SharePoint external sharing. Both good and bad flowed from this decision. On the upside, Microsoft used something that they knew worked. External guest accounts can access files in the document library in group team sites as easily as tenant users can. The downside is that the mechanism cannot support access to other group resources. External users can communicate with other group members via email, but they have no access to the group calendar or plan.
Roll forward a year and Office 365 is a different place. The advent of Teams means that Microsoft has another application that needs external access, as does any application that depends on Groups like Planner or Stream. A SharePoint-based mechanism is unacceptable and, as I described in June, Office 365 needs a new common external access method that works for all applications.
The Teams developers said that they would support external access in mid-2017. They have acknowledged that they will not meet that date, possibly because creating an external access mechanism that satisfies the needs of multiple applications is difficult.
The External Sharing Policy
However, the first glimmer of what might be the solution appeared in a PowerShell script to control allow and block lists for external sharing to Office 365 Groups. According to a Microsoft post on the topic, “This policy works for all workloads with Guest access through O365 Groups such as Outlook, Teams & Planner in future.”
An allow list states domains that your tenant is willing to share information with, like “Microsoft.com, yourdomain.com.” A block list lists the domains that you do not want users to share information with. The policy is not retroactive and any existing sharing that is in place persists with people belonging to domains in a block list. A tenant can have either a block list or an allowed list; you cannot have both – and only one policy is available per tenant.
At first glance, the PowerShell script appears complex but it is really not. Many of the lines set out the structure that you expect in well-engineered scripts, like error and parameter handling and processing JSON-formatted content. The original script omitted a digital signature at the bottom of the script, which you would expect from Microsoft (a signed version is now available). Of course, no one ever runs unsigned scripts that they download from the web…
At the heart of the script are the New-AzureADPolicy and Set-AzureADPolicy cmdlets. To use the cmdlets to set policy, you need to run version 2.0.0.98 or later of the Azure Active Directory module for PowerShell. This is a preview version, so it is a look into the future of how the cmdlets in the module will evolve.
Creating a New External Sharing Policy
As you can see in Figure 1, running the script to create a new policy is straightforward. In this case, we create a block list comprising of the Contoso.com and Fabrikam.com domains.
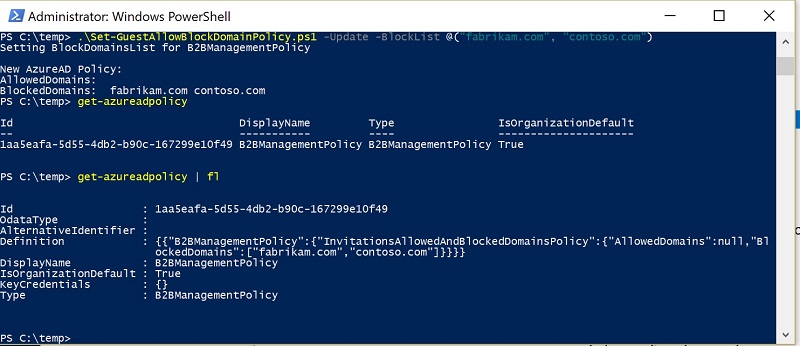
If we then run the Get-AzureADPolicy cmdlet to examine the resulting policy, we see:
Id : 1aa5eafa-5d55-4db2-b90c-167299e10f49
OdataType :
AlternativeIdentifier :
Definition : {{"B2BManagementPolicy":{"InvitationsAllowedAndBlockedDomainsPolicy":{"AllowedDomains":null,"BlockedDomains":["fabrikam.com","contoso.com"]}}}}
DisplayName : B2BManagementPolicy
IsOrganizationDefault : True
KeyCredentials : {}
Type : B2BManagementPolicy
The name of the policy is B2BManagementPolicy and it holds the blocked list as expected. It would be unsurprising if Microsoft expanded this policy in the future to include extra settings for use with applications that need to use business-to-business connections.
If you have a SharePoint sharing policy in place already, you can run the script with the MigrateFromSharepoint switch to copy the domains in that policy across to the new external sharing policy.
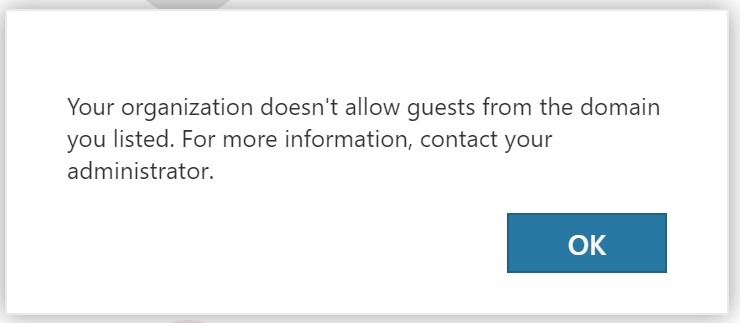
The Block in Place
With the policy in place, when group owners try to add an external guest from one of the blocked domains, they see the error shown in Figure 2.
Next Step, the Office 365 Admin Center
Office 365 is a wide and diverse universe of tenants, some of whom would never dream of running a PowerShell script to do anything. Microsoft plans to bring the block/allow list settings to the Office 365 Admin Center soon, in which case you can forget about everything you read here.
In Closing, Some Planner Updates
BTW, in other news, I recently complained that the rate of development for Planner is very slow. Well, Microsoft has refreshed the UI and upped some limits (for instance, you can assign up to 300 tasks to a user), all of which is good. What’s not so good are some complaints that the new UI erases the description field for some tasks. I have not seen the problem but it is reported by several tenants. If you use Planner, check that your task descriptions are there. If they are not, please log a call with Microsoft.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.




