External Access for Office 365 Groups
Microsoft has put a huge amount of emphasis on Office 365 Groups as the basis for team-based collaboration for its cloud service. Collaboration often requires input from external people and that hasn’t been possible until now. The announcement of external user support for Office 365 Groups is welcome, even if it is restricted in part.
The need to support a controlled and secure mechanism to permit external people to collaborate with members of Office 365 Groups is evident. Many scenarios exist when teams come together and need the support of external expertise to accomplish tasks, such as when a team works with a supplier on the design of a new product, or when a team charged with leading the acquisition of another company needs to interact with people in that company and external lawyers and accountants.
Up until now, it has been possible for some level of interaction to occur by permitting external people to share in group conversations by email. However, they have not been able to access other group resources such as documents, the shared notebook, or an associated plan managed by Microsoft Planner. Microsoft has just announced support for external access to Office 365 Groups. I’ve been using the capability for about a month now to collaborate with people from Microsoft and other companies, notably to prepare presentations for the upcoming Ignite conference. My observations reported here are based on that experience.
Defining guest users for Office 365 Groups
Microsoft’s solution introduces a new form of Azure Active Directory object called a guest user. A guest user is defined as someone whose account and credentials are controlled outside the Office 365 tenant that owns the groups that the guest user might want to join. A guest user object is similar to the well-known mail user object, but is explicitly reserved for the purpose of controlling access for external people to the multiple types of content managed through Office 365 Groups. Guest users are identified by an email address. The email address can point to another domain within Office 365, an email domain for a company that doesn’t exist within Office 365, or a consumer email service like Gmail.com or Yahoo.com.
The sharing mechanism enabled by guest users accommodates two kinds of interaction with groups. A guest user can be allowed access to a specific file stored in a group document library or they can be granted access to the document library as a whole, in which case the guest is listed among the group membership. In this respect, sharing operates very much like the feature available in SharePoint Online. Although they don’t have direct access to the conversations held in the group mailbox, guest users can participate in those conversations via email. Because they don’t have access to the group mailbox, guest users cannot access the group shared calendar.
What you can expect to do
Table 1 summarizes the functionality that’s available in the first phase of external access to Office 365 Groups. We’re still in the early stages of the project and some of the features that you might expect are not yet available. However, the basics exist to allow guest users to be able to collaborate with files stored in group document libraries.
| Workload | Feature | Guest user can access? |
| Exchange Online | Participate in conversations in group mailbox | Yes (via email) |
| Exchange Online | Participate in group shared calendar | No direct access, but can participate via email |
| Exchange Online | Search group conversations | Yes – but only copies held in personal mailbox |
| Exchange Online | Browse Global Address List for tenant | No |
| SharePoint Online | Access a single document | Yes – via specific invitation |
| SharePoint Online | Access a complete document library | Yes |
| SharePoint Online | Search group documents | Yes |
| OneNote | Access group shared notebook | Yes |
| EXO/SPO | Access IRM-protected content | No |
| Planner | Access plan associated with Office 365 Group | No |
| Power BI | Access Power BI workspace associated with Office 365 Group | No |
| Dynamics CRM | Access CRM data associated with Office 365 Group | No |
| Groups | Browse directory for groups to join | No |
| Groups | Perform group management | No |
Table 1: Group functionality available to guest users
Some of the features listed in Table 1 might never be available. Others, like allowing guest access to Microsoft Planner, are expected to be high-priority customer requests that are more likely to appear soon. It will take time for the other Microsoft development groups that leverage Office 365 Groups to pick up the capability and update their code to support external access.
Adding guest users to Office 365 Groups
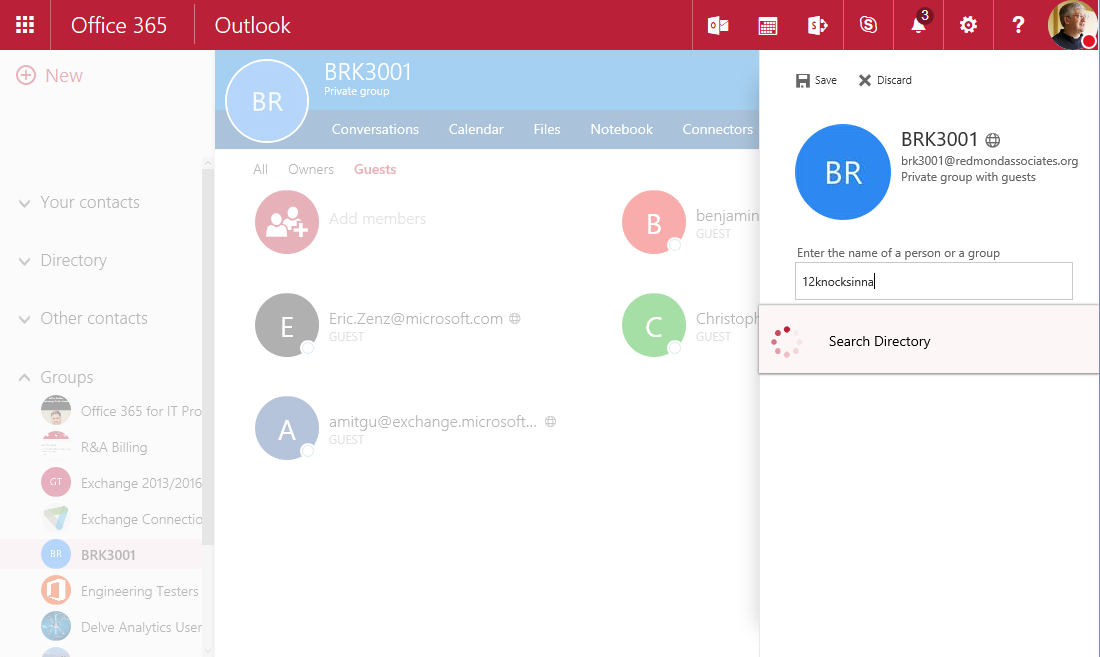
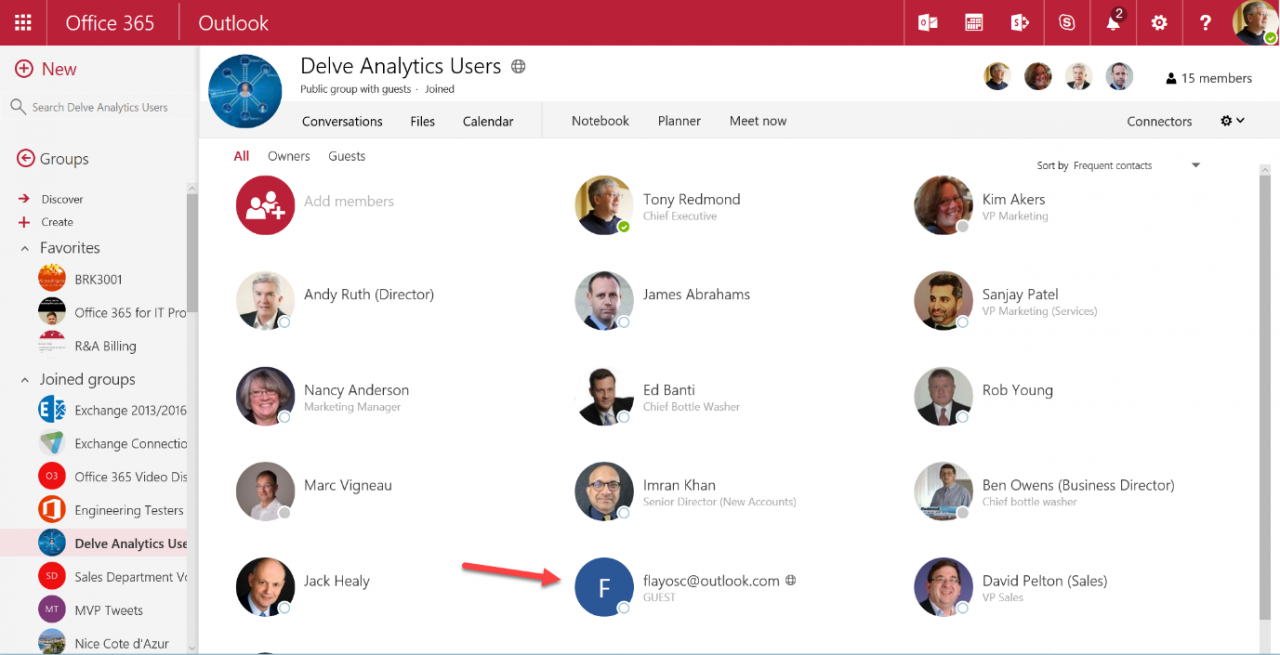
OWA is the first client to support the ability to add guest users to a group. Only group owners can invite someone from outside the tenant to become a guest user. To do so, open the group and click the ellipsis menu to the right and select Members, then Guests. Any guest users who are members of the group will be displayed. Click the Add Members icon to add a guest. Figure 1 shows the email address for a new guest being input. The address is checked against the directory and the entries in the user’s Outlook autocomplete list (shared by OWA and Outlook), but you’re not restricted to these addresses. Any valid email address is acceptable. If you input the email address of an account belonging to the tenant, they will be added as a regular member rather than a guest.
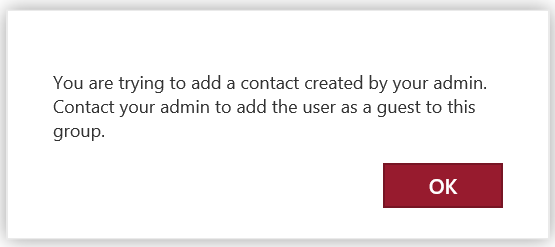
If you attempt to add an email address for a guest user that already exists for another type of mail-enabled object in the tenant directory (most likely a mail contact defined in Exchange Online), you’ll see the error message shown in Figure 2. The solution requires the administrator to remove the other mail-enabled object, after which the guest user object can be added by the group owner or by an administrator running the Add-UnifiedGroupLinks cmdlet as described later in this article.
How an invitation to an Office 365 Group guest user works
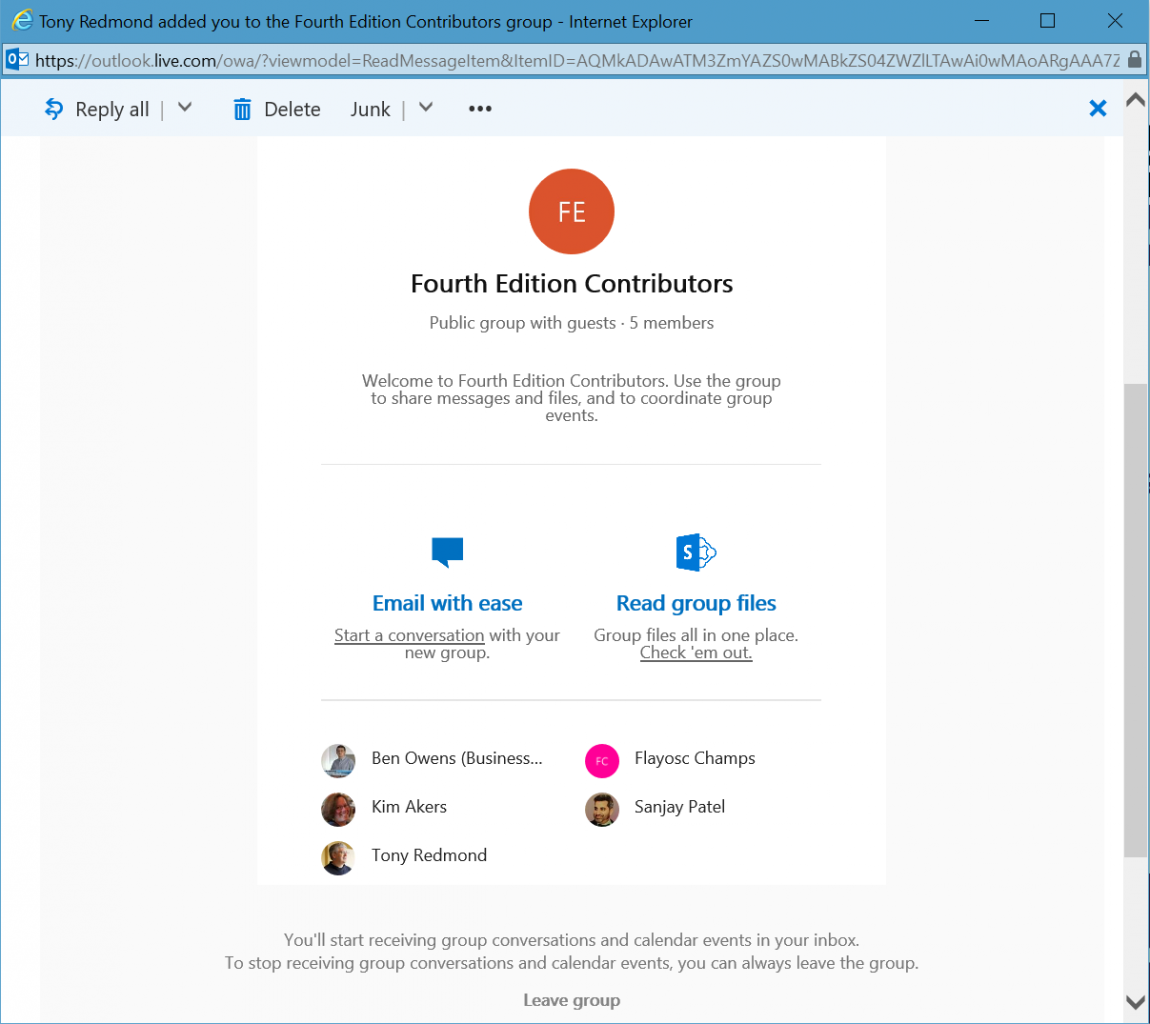
When a guest user is added to an Office 365 Group, a check is made against Azure Active Directory to establish whether the email address for the guest user is known to the tenant. If not, a new guest user object is created and a notification message (Figure 3) is sent to the guest user to let them know that they’ve been added to the group. The message contains a link to allow the guest user to leave the group if they so wish and a link to allow the user to redeem the invitation and to access the group shared document library.
A guest user can also receive an invitation to a file held in a group document library through the action of sharing a document belonging to the group as a “cloudy attachment” (one where a link is sent to the document rather than a complete copy). Clicking the attachments invokes the invitation to access the document.
If the guest user chooses to accept the invitation to access the document, two conditions can occur. First, they might already have a Microsoft account that is linked to the email address used for the invitation (including a consumer account for a service like Outlook.com). If so, they can use this account to authenticate with Office 365 and access the group files.
If they don’t have a Microsoft account, the user is redirected to invitations.microsoft.com and invited to sign-up for an account in the tenant by adding a password and a display name to their email address to create a new guest user object. A verification code is then sent to the email address and when that code is used to authenticate the address, the guest user object becomes fully active and can be used to access the Office 365 Group.
Unfortunately, guest users who have accounts in other Office 365 tenants cannot add external groups to their list of favorite groups. Instead, to ensure fast access, they have to retain a note of the URL for the group document library.
Guest user access to Office 365 Group content
Guest users see a modified version of the Files view to enable them to access documents shared with other group members. The shared notebook is also accessible. In addition, if group members circulate “cloudy attachments” (those stored in OneDrive for Business) to the group, guest users can use their credentials to see those files.
In addition to the restricted Files view, guest users are limited to the amount of information they can see about the tenant and other group members. For instance, modified Exchange address lists are used to restrict their access to the GAL and the contact cards revealed for group members don’t contain organizational information (like job titles). Guest user accounts do not appear in other Exchange address lists. Depending on customer feedback as to whether this feature is desirable, Microsoft might add the ability for an administrator to configure address lists to include guest users in the future.
The status of guest users is clearly indicted to other group members and the group type is shown as “Public group with guests” (Figure 4) or “Private group with guests”. MailTips are also used to warn users whenever they email contributions to the group. These visual indications serve as a warning that confidential material outside the boundaries of the purpose of the group should not be shared or discussed within the group. Unsurprisingly, a guest user cannot be promoted to become the owner of a group.
Apart from email interaction with a group, guest users are restricted to browser access for group resources as support currently is unavailable within Outlook 2016. The Outlook Groups mobile app is being updated to allow group owners to add guest users, but it won’t allow guest users to access the content belonging to groups from another tenant.
Guest user access to Office 365 Group conversations
Guest users can’t browse the conversations held in the group mailbox because they are not granted access to the mailbox. Instead, guest users can participate in conversations via email by being autosubscribed to the group, much in the same way that other external users can participate in conversations if the RequireSenderAuthenticationEnabled property for the group is set to False. Guest users are not governed by RequireSenderAuthenticationEnabled because they are full members of the group. The exception to this rule is where the primary SMTP address of a guest user is different than the email address used for their invitation. When this is true, any attempt to respond to a conversation will fail because the email address on the inbound item does not match any the address of a group member.
An easy workaround is to set RequireSenderAuthenticationEnabled to False, which allows any external user to email the group, Alternatively, you can create a guest user to allow the person to log in using their normal UPN and send messages to the group using their primary SMTP address.
Guest user support in Office 365 Groups for Microsoft Planner
External guest access will first be introduced for Office 365 Groups and then extended to Microsoft Planner. Testing needs to be done to establish how the task information within a plan should be presented to guest users. For instance, just because an external account is needed to assist with the costing of a specific part of a plan doesn’t mean that they should have access to all the other tasks in the plan.
Guest user access in Office 365 Groups to protected information
Information shared in groups is often quite confidential and is therefore protected with Information Rights Management (IRM). Guest users are not able to access either messages or documents protected with IRM. In fact, this can be an advantage because you can then protect ultra-confidential information with IRM and allow access to other files in the document library. Although they won’t be able to see the content of protected documents, guest users are able to see the metadata like title, author and last modified date.
Managing guest user objects for Office 365 Groups
After a guest user account is created in Azure Active Directory, it is first synchronized with Exchange Online and then with SharePoint Online. Once it exists in the Azure Active Directory instance for a tenant, the same guest user object can become a member of multiple Office 365 Groups.
You can see details of the external guest accounts through PowerShell by running the Get-MsolUser cmdlet. The first example shows how to locate the Azure Active Directory account for a specific guest account (providing you know their email address) while the second lists all known guest accounts within a tenant.
[PS] C:\> Get-MsolUser -SearchString [email protected] | Format-List [PS] C:\> Get-MsolUser -All | ? { $_.UserType -eq “Guest” } | Format-Table DisplayName, ProxyAddresses
Note the form of the user principal name assigned to a guest account to identify these accounts, which is similar to the accounts created by SharePoint Online when invitations are extended to share individual files in document libraries. If you look at the membership list for a group that contains guest users, you’ll see much the same format used to identify the guest users there.
[PS] C:\> Get-UnifiedGroupLinks -Identity BRK3001 -LinkType Members Name RecipientType ---- ------------- TRedmond UserMailbox amitgutta.microsoft.com#EXT# MailUser chris.fiessinger_microsoft.com#EXT# MailUser e.zenz_microsoft.com#EXT# MailUser benny.niaulin_share-gate.com#EXT# MailUser t.redmond_live.com#EXT# MailUser flowers_outlook.com#EXT# MailUser
In a hybrid environment where group membership is synchronized back to on-premises Active Directory via AADConnect, the guest user information is not synchronized.
There’s no way to prevent a group owner from adding a guest to a group whom you’d prefer not to be invited. If this is a problem, you could scan Azure Active Directory to locate the email address of the offending guest user and remove it whenever found using a command like the one shown below. This isn’t something to do without thinking (or testing) as removing the guest account will remove any access that user has been granted to resources in the tenant.
[PS] C:\> Get-MsolUser -All | Where { $_.UserPrincipalName -like "*Flowers_outlook.com#EXT#*" } | Remove-MsOlUser -Force
Adding guest users programmatically to Office 365 Groups
External guests can be invited by a group owner, other group members (these requests have to be approved by a group owner), or a tenant administrator. Tenant administrators can create guest user accounts through Azure B2B connections, which is a good way to set up sharing between two organizations that work together on a regular basis. Tenant administrators can also set up guest user accounts through OWA.
New guest user objects can only be added through AAD. However, once a guest user object exists in the tenant, the administrator can add that guest to any group via the Office 365 Admin Center, EAC, or by running the Add-UnifiedGroupLinks cmdlet. For example:
[PS] C:\> Add-UnifiedGroupLinks -Identity ‘Engineering Testers’ -LinkType Members -Links flayosc_outlook.com#EXT#
Note that adding a guest user to a group in this manner does not create and send a notification message to that user to tell them that they are now a member of the group. However, if the AutoSubscribeNewMembers property for the group is set to $True, they will be able to participate in group conversations immediately.
If a guest user fails to receive (or loses) the email notification to tell them that they have been added to a group, the group owner can send them the URL for the document library. The user can input the URL into a private browser session and go through the sign-in process to connect to the group. The private session makes sure that existing cached credentials don’t interfere with the process. The URL for a group document library follows this form:
https://mytenant.sharepoint.com/sites/askhr/Shared%20Documents/Forms/AllItems.aspx
Controlling the ability to add guest users to Office 365 Groups
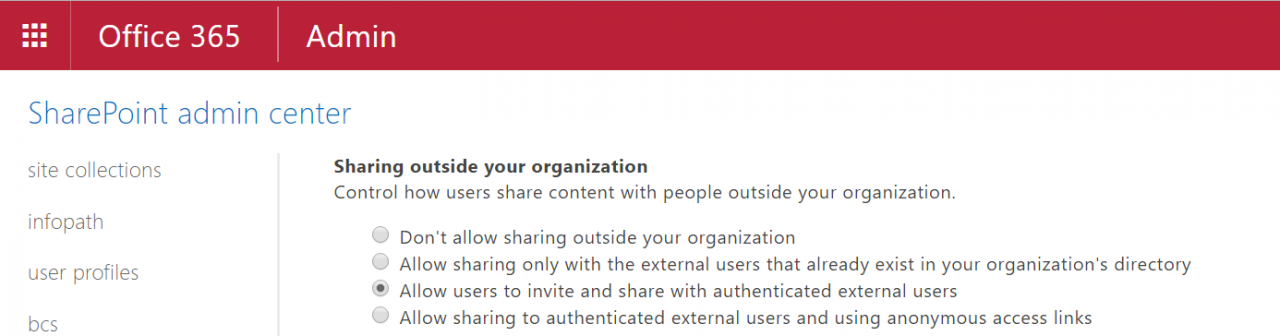
Because guest users get access to group document libraries, it follows that a prerequisite for sharing to occur is that SharePoint external sharing is enabled for the tenant. This setting is controlled in the Sharing section of the SharePoint Admin Center (Figure 5). If sharing isn’t allowed for a tenant, guest user access to Office 365 Groups won’t work.
In addition, the Azure Active Directory settings for the tenant must allow invitations to be sent to external guests. If this setting is disabled, Office 365 Groups cannot send invitations to people outside the organization. To view and configure the settings, go to the Azure Active Directory portal and select the directory instance for the tenant, then the Configure tab, and scroll down to the User Access section.
[Update: Microsoft has provided an option to control the ability to send invitations to external people in the Office 365 Admin Center. Go to Security & Privacy and select Sharing. The option should be ON to allow guest users to participate in Office 365 Groups]
Two additional levels of control are provided to allow tenant administrators to control the way that Office 365 Groups share information with guest users.
- An AAD policy is used to control group access for guest users across the tenant. This policy applies to all applications that might want to support guest users.
- Access to guest users can be selectively enabled or disabled for individual groups.
By default, the ability to add guest users to groups is enabled at a tenant level. It is controlled by the AllowToAddGuests setting stored in the same AAD directory setting object (or policy) that is also used to determine the list of users who can create new Office 365 Groups. To check that policy, you’ll need version 1.1.130 of the PowerShell module for Azure Active Directory. Once that’s installed, you can use the Get-MsolAllSettings cmdlet as follows:
[PS] C:\> Get-MsolAllSettings | ForEach Values Name Value ---- ----- AllowGuestsToBeGroupOwner False AllowGuestsToAccessGroups True GuestUsageGuidelinesUrl GroupCreationAllowedGroupId A3c13e4d-7083-4448-9224-287f10f23e10 AllowToAddGuests True UsageGuidelinesUrl Http://thoughtsofanidlemind.com ClassificationList General Usage, External Access, Internal Only, Confidential EnableGroupCreation False
- AllowToAddGuests is True, meaning that group owners are allowed to add guest users in this tenant.
- AllowGueststoAccessGroups is True, meaning that guest users can access Office 365 Groups.
The AllowGuestsToBeGroupOwner setting is not used and might be removed in the future.
To change one of these settings, you have to update the AAD directory setting object. For example, this code stops any more guest users from being added to groups by group owners.
$CurrentSettings = Get-MsolAllSettings | ? {$_.DisplayName -eq “Group.Unified”}
$GroupSettings = Get-MsolSettings -SettingId $CurrentSettings.ObjectId
$Value = $GroupSettings.GetSettingsValue()
$Value["AllowToAddGuests"] = "False"
$Value["AllowGuestsToAccessGroups"] = "True"
Set-MsolSettings -SettingId $CurrentSettings.ObjectId -SettingsValue $Value
If the AllowGuestsToAccessGroups setting is disabled, all guest users lose access immediately to the groups to which they belong. Think of this as “flipping a switch” to turn access on or off if the need suddenly arises to limit sharing for a tenant. Access can be restored later on by updating the AAD policy. Guests will continue to have access to individual files for which they have received sharing invitations.
Blocking guest access for specific Office 365 Groups
An administrator can also selectively block or allow guest users for specific groups. In order for a group owner to be able to add a guest user to a group, both the tenant setting and the group setting must permit the action.
Because this is an Azure Active Directory setting, the Set-UnifiedGroup cmdlet is not used. Instead, the Get-MsolSettings and Set-MsolSettings cmdlets are used to retrieve and update the settings for the group that you want to control. First, retrieve the object identifier for a group and store it in a variable. This can be done by using the Get-MsolGroup cmdlet to search for the group by name. The object identifier is a GUID like 84fe8ec1-d85f-4564-a786-1f7bedd9862c that is used to locate and update the group object within Azure Active Directory. For example:
[PS] C:\> $ObjectId = (Get-MsolGroup -SearchString “TeleWorkers”).ObjectId
Now, make sure that a settings object exists for the group:
[PS] C:> $Settings = Get-MsolAllSettings -TargetObjectId $ObjectId
If the $Settings variable doesn’t contain a value, you know that the group doesn’t have a settings object and one needs to be created. This is done as follows:
[PS] C:\> $Template = Get-MsolSettingTemplate -TemplateId 08d542b9-071f-4e16-94b0-74abb372e3d9 [PS] C:\> $Setting = $Template.CreateSettingsObject() [PS] C:\> $New_setting = New-MsolSettings -SettingsObject $Setting -TargetObjectId $ObjectId
Now you can populate the setting object for the group:
[PS] C:\> $Settings = Get-MsolAllSettings -TargetObjectId $ObjectId [PS] C:\> $Value = $Settings.GetSettingsValue() [PS] C:\> $Value["AllowToAddGuests"] = "false" [PS] C:\> Set-MsolSettings -SettingId $Settings.ObjectId -SettingsValue $Value -TargetObjectId $ObjectId
Once the block is in place, any attempt to add a guest user will result in the message:
“Before you can add guests as members of the group, you need to contact your administrator.”
The sad fact is that a multi-step prone-to-error process is far too much work to block external access to a specific group. Life would be much easier if Microsoft wrote the code to allow the setting to be manipulated through PowerShell.
To check that the necessary blocks are in place, you can run this command to list the groups that aren’t allowed to have guest users.
[PS] C:\> Get-UnifiedGroup | ? {$_.AllowAddGuests -eq $False } | Format-Table DisplayName
Administrative override to add guest users to Office 365 Groups
If the AAD policy for a tenant prohibits the addition of guest users to groups, it can be overridden by accounts that hold the Global Administrator or User Management Administrator roles to add new guest users to groups.
If the guest user account already exists in Azure Active Directory, the administrator can run the Add-ADGroupMember or Add-UnifiedGroupLinks cmdlets to add the guest user to a group. If the guest user account doesn’t already exist, Azure B2B can be used to add the accounts to the tenant and the accounts can then be added to the groups. Azure B2B is the Microsoft preferred answer, but if you feel adventurous, it might be possible to add guest users through SharePoint CSOM.
Summary
Although a little restricted, Microsoft’s first steps to add access for guest users to Office 365 Groups are welcome and will address many of the needs expressed by customers. Like any first release, there are gaps to fill and uneven parts to smoothen. Given that Office 365 Groups are becoming so important to the Microsoft collaboration story, you can expect some tender loving care to be exerted in this direction in the near future.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.