Active Directory Backup vs Replication (And Why You Need to Be Clear on the Difference Now)

Backup and replication are common data protection concepts, but they serve different purposes. Learn more about their differences and how they can benefit your data management strategy, especially how the backup vs replication argument relates to Active Directory (AD) and protecting it.
What are backup and replication?
Although backup and replication are both methods of protecting data and preventing data loss, there are some important differences. Everyone wants to protect their data in case of an unforeseen event or downtime. This data backup strategy forms the basis of what’s called Disaster Recovery (DR).
Backup and replication are both used to make copies of your data in an alternate location on alternate storage vs your original location. Choosing what to back up also requires design. Do you include your desktops, your production servers, virtual machines (VMs)? You must determine what should be considered a critical application, if you need to set up continuous data protection, and how often to schedule backups. I’ll cover some of these in more detail below.
Active Directory backup vs replication
How do backup and replication, and other protection strategies, apply to Active Directory (AD). There are backup and replication options available to protect AD.
- backup lets you restore Active Directory, or an object in the AD database, to a point in time.
- replication provides high availability for your domain controllers. If one DC stops responding, there should always be another on hand to process the request.
Backup
Windows Server Backup, a built-in free backup tool included with Windows Server allows you to back up AD natively. You can also use Windows Server Backup to restore AD in the event of objects being deleted or a domain controller becoming unavailable where there is no convenient replication partner.
Replication
Having at least two domain controllers (DCs) in your AD infrastructure introduces replication. The internal AD database, which houses all of your users, computers, devices, and Group Policy Objects (GPOs), etc. is replicated to the second DC. Having a third, fourth, and fifth DC enhances the overall robustness of AD as the AD database is replicated between all domain controllers, improving availability should one stop responding.
Let’s discuss in more detail the various options, then I can make some recommendations.
3 reasons why AD lag sites aren’t a replacement for backup
AD lag sites are a form of replication primarily used for disaster recovery and maintaining a read-only copy of your AD data. There is a delay or ‘lag’ in the data getting there. This delay ensures any accidental deletions or changes aren’t immediately replicated.
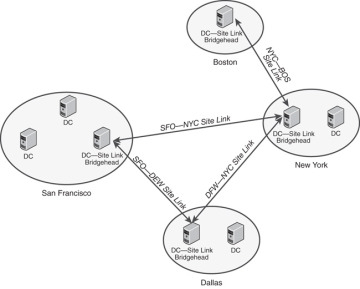
In case of a disaster or loss of your primary AD site, the lag site can be promoted to a writable domain controller. Here are reasons why you should use lag sites as an alternative to AD backup:
- Although lag sites help prevent the propagation of errors or malicious activity, they do not contain current data.
- They don’t keep historical states as backups do.
- And lag sites provide limited recovery options.
Windows Server Backup
Windows Server Backup is a free ‘Feature’ in Windows Server. You can install it using Server Manager or even Windows Admin Center. This simple utility allows you to back up the entire System State of a server, including AD.
However, there are considerations you need to take into account. Backup targets are rather limited, and not robust. The automated scheduler is not as feature-rich as other third-party enterprise-grade backup solutions.
Enterprise-level data protection options
Third-party data protection suites are where you will gain the most value and security in terms of protecting your data, enjoying your ‘well-oiled machine’ with limited admin time required (after implementation), and recovering your AD environment quickly, and sometimes, automatically.
A few options include CommVault, Cohesity, Veeam, Semperis, and Cayosoft.
What does backing up data accomplish?
Backing up data focuses on restoring data to a specific point in time. In case something happens to your ‘primary’ datastore, this ‘secondary’ location target can be used to restore your data. Answering questions like…
- how often do you make backups?
- how many locations do you back up to?
…all determine the strength, robustness, and ease of recovering your data.
The more restore points you have and the more locations you have, the faster you can ‘get back to business’ after a disaster or loss of computing infrastructure. If an on-premises fileserver goes down, you can restore those shares from a backup.
What does replication offer?
Replication, another method to protect your data, focuses on business continuity. Replication, which has options for its fundamental usage (synchronous replication or asynchronous replication), allows you to keep data in sync between two or more locations or targets.
Replication allows you to restore your data from a secondary location back to your primary target if your primary target is unavailable for any reason. You can use various models to set up an ‘active/passive’, ‘active/active’, or similar formats.
Having two active data points (active/active) is more robust and allows for automated failovers. Active Directory uses a variation of active/active replication to make domain controllers highly available and available across widely-dispersed geographical locations.
When replication is setup properly, your IT Pros won’t need to do anything. But, this comes at a cost. It requires you to design your infrastructure to enable replication. For example, if an on-premises fileserver goes down, and you have Azure File Sync enabled, the data replicated to Azure will get pulled back down to your on-premises fileserver. Business goes on.
In the more cost-effective and prevalent scenario, active/passive, your primary server is available. A secondary server is also online, with up-to-date replicated information, but it is not active on the network, it is passive. Using a load balancer, or similar network device that can query the status of these servers, if the active server becomes unresponsive, it will automatically mark the passive server as active and send all network traffic to it.
Be aware of malware propagation – if you have an active/active replication setup, infected files in one location could easily infect the other. In this case, without additional replication targets isolated from your primary, you will be unable to restore the infected files to a point in time before infection.
Because of the way Active Directory is designed, Microsoft doesn’t recommend using backups (or lag sites) to restore AD if it is determined your issue was caused by malware. Instead, you should rebuild Active Directory from the ground up, and then use a ‘nonmigratory’ migration approach to restore AD objects in your new AD forest.
Prevention is always better than cure, so you should protect AD from malware. You can reduce AD’s attack surface by following some simple best practices, such as:
- Using a least-privileged security model for AD access
- Implementing an AD tiered administration model
- Use secure administrative hosts to access domain controllers
- Harden your DCs
Can AD replication replace backup?
Just in case you still weren’t sure, the answer is ‘no’. Although replication and backup serve distinct purposes and complement each other, replication can’t replace backup when protecting Active Directory. Here’s why.
- Taking periodic and scheduled backups of your data affords you the ability to go back to a specific moment in time and restore your data. Replication doesn’t directly offer that scenario. Replication does not maintain historical versions of data.
- Replicating your AD database to domain controllers creates a highly available service. If one DC becomes unavailable, AD continues pulling information from your other active DCs. This is also known as high availability.
- Replication across dispersed geographical areas helps protect your Active Directory environment from regional datacenter or network-related issues. Having two or more DCs in a single data center protects from a single DC’s point of failure. Although you can immediately fail over to a secondary replication point, you will be at the mercy of the integrity of all of your data at that single point in time.
Do I need data protection beyond replication?
Absolutely – I’ve mentioned this previously, but there are some key points as to why you should incorporate backup technologies beyond replication alone. Let’s go through them.
- Disaster Recovery – Replication alone will not cover all disaster scenarios (e.g. site-wide failures, data corruption, etc.)
- Human Error – Backups safeguard against accidental deletions or changes.
- Ransomware Attack / Malware Attack– Backups can provide a clean slate to restore to after an infection. But Microsoft doesn’t recommend restoring from backup if malware/ransomware was the cause of the outage.
- Legal and Compliance – Backups retain data for legal requirements.
- Complete Resilience – Combining replication and backups ensures a robust data recovery strategy.
Conclusion
A robust Active Directory (AD) environment relies on a comprehensive backup and replication strategy. Regular backups create copies of your AD data, ensuring a recovery point in case of accidental deletion, hardware failure, or cyberattacks.
Replication, often employed alongside backups, synchronizes directory data across domain controllers, guaranteeing consistency and availability in case of outages. Marrying these two concepts is vital to ensuring your Active Directory environment is protected from any unexpected incidents.
Committing to the capital cost of a third-party enterprise-grade data protection suite enhances your level of protection, often an order of magnitude your C-level executives will value and accept.
Please feel free to leave a comment or question below. Thank you for reading!



