Essential Guide to Mastering Get-ADGroupMember (AD User Management)

Get-ADGroupMember is a useful PowerShell cmdlet for retrieving the members of Active Directory (AD) groups. In this article, we’ll delve into the capabilities of Get-ADGroupMember, explore its common parameters, and provide practical examples to showcase its power and versatility in managing your Active Directory environment.
We’ll also touch on a related cmdlet – Get-ADGroup and how it can be used together with Get-ADGroupMember.
What does Get-ADGroupMember do?
Get-ADGroupMember is part of the Remote Server Administration Tools (RSAT) PowerShell module – a PowerShell cmdlet that belongs to the Active Directory module, which must be installed and imported to use this cmdlet. Its primary purpose is to retrieve the members of an AD group, whether they are users, other groups, or computer objects. This cmdlet offers a versatile approach to gathering information about members of the AD group and group memberships within your AD domain.
On a related note, Get-ADGroup is a PowerShell command (cmdlet) used to retrieve Active Directory group objects from your domain. You can extract a single group or multiple groups using filters and scripts.
How to use Get-AdGroupMember? – Practical examples
Let me go through some examples of what Get-AdGroupMember can do for your IT Pro needs and your organization. Just a refresher – to get PowerShell warmed up, open Windows Terminal and first run this command:
import-module ActiveDirectory
Then you can start running the commands throughout the remainder of this post.
How do I get members of an AD group?
In this example, we’ll use Get-ADGroupMember to retrieve the members of a specific AD group by specifying the group’s name using the -Identity parameter.
# Retrieve members of the "Citrix_Super_Admins" group
$members = Get-ADGroupMember -Identity "Citrix_Super_Admins"
# Display names
$members | Select-Object Name
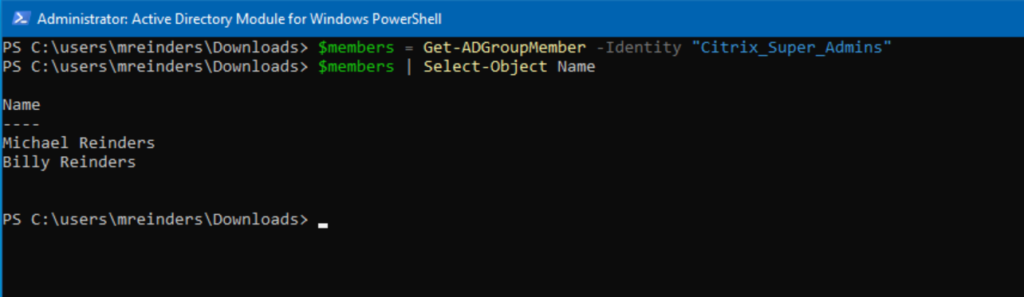
This script retrieves the members of the “Citrix_Super_Admins” group and displays their names. By the way, you can use several different attributes with the ‘-Identity’ parameter including DistinguishedName, Credential, Account Name, sAMAccountname, emailaddress, and various security identifier types.
Retrieve nested AD group members
You can use the -Recursive parameter to retrieve members from nested groups within the specified group. Let’s say you have a group called “Citrix_Super_Admins” that contains other groups representing different IT teams.
# Retrieve members of the "Citrix_Super_Admins" group, including members from nested groups
$members = Get-ADGroupMember -Identity "Citrix_Super_Admins" -Recursive
# Display member names
$members | Select-Object Name
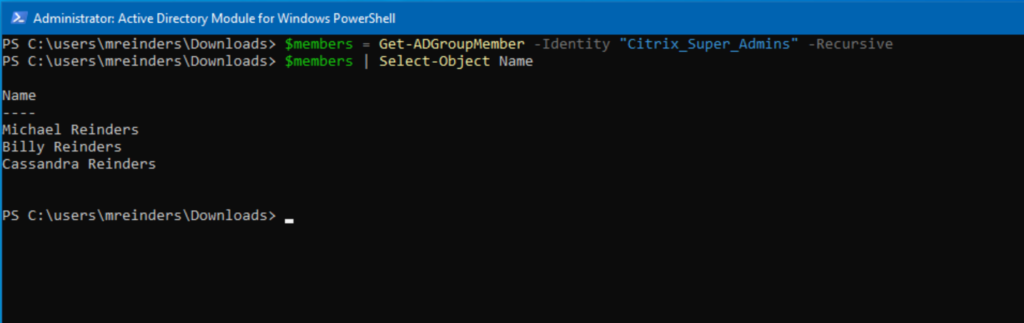
This script retrieves members from the ‘Citrix_Super_Admins’ group and includes members from any nested groups within – Cassandra is a member of ‘Citrix_Pilot_Users’, but she is NOT in the ‘Citrix_Super_Admins’ group. Kind of helpful!
Run Get-AdGroupMember against a specific domain controller
In a typical Active Directory environment, you can specify a particular domain controller (DC) to query for group membership information using the -Server parameter. We will first store the member list in the ‘$members’ variable.
# Retrieve members of the "Citrix_Pilot_Users" group from a specific domain controller
$members = Get-ADGroupMember -Identity "Citrix_Pilot_Users" -Server "WS16-DC2.reinders.local"
# Display member names
$members | Select-Object Name
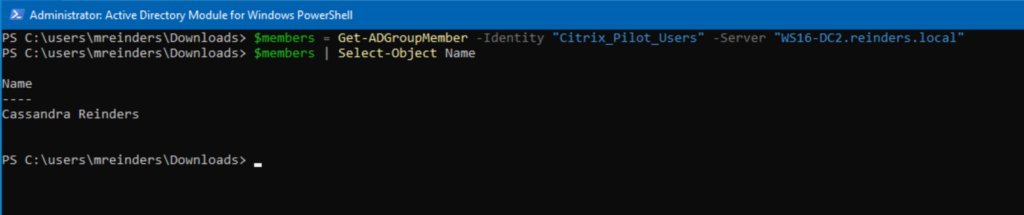
This script queries the domain controller “WS16-DC2.reinders.local” for the members of the “Citrix_Pilot_Users” group. As a reminder, you can use this to find local groups, universal groups, and even members of the administrators group on any computer object in your domain. This is useful when reconciling your Enterprise Admins or Domain Admins group, for example.
Filter AD group members based on specific criteria
We can use both Get-ADGroup and Get-ADGroupMember to filter group members based on some specific AD attributes.
Let’s go through an example or two here.
Get-ADGroup -Filter “Name -like ‘*RDS*'” | ft
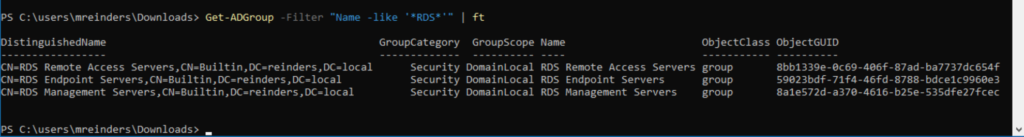
You can see here that I used the -Filter parameter to find all groups with ‘RDS’ anywhere in the distinguished Name attribute. I piped the output to ‘ft’ (Format-Table) to present the information in a more readable format. 🙂
Let’s do one more.
Get-ADGroup -Filter “MemberOf -eq ‘CN=Citrix_Super_Admins,OU=Domain Groups,DC=Reinders,DC=local'”
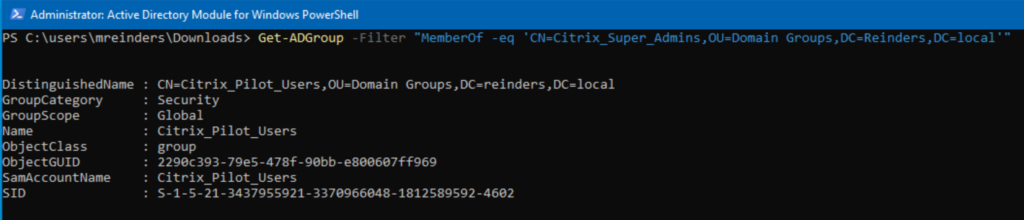
Here we are checking if any groups are members of the ‘Citrix_Super_Admins’ group. As you can see, ‘Citrix_Pilot_Users’ is a member!
Find specific AD attributes
Unfortunately, the Get-ADGroupMember cmdlet doesn’t contain the -Filter and -Properties parameters. In order to filter the results to specific object attributes, we can use Get-ADGroup again to manage our needs. Let me show you.
Get-ADGroup -Identity “Citrix_Super_Admins” -Properties *
You will see ALL of the attributes of the “Citrix_Super_Admins” group. This is very helpful when troubleshooting issues with groups. You literally get to see every attribute as part of this group.
Here is one more example.
Get-ADGroup -Filter “groupcategory -eq ‘Security'” -Properties Modified,ProtectedFromAccidentalDeletion | ft
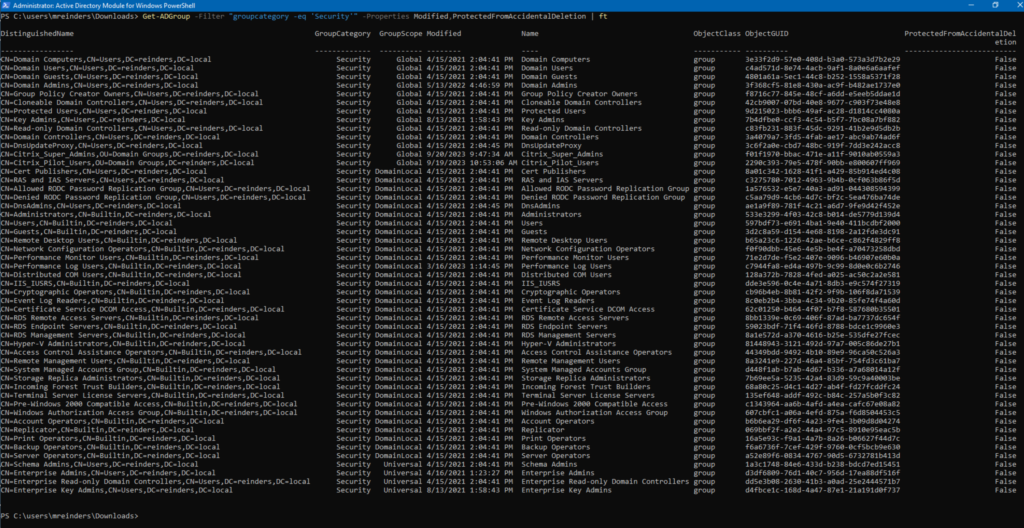
Wow! Now that is helpful. This shows all ‘Security’ groups and some useful attributes. Notice NONE of the groups are protected from accidental deletion? That should be rectified right away!
Exporting AD groups and members to a CSV or Excel file
To export AD group members, including the groups, to a CSV file using PowerShell involves a series of steps, including querying AD for group information and exporting it to a CSV file. Below is a step-by-step guide on how to do this.
We’ll use the Get-ADGroup cmdlet to retrieve a list of Active Directory groups. Optionally, you can filter groups by various criteria such as group name, Organizational Unit (OU), or specific properties.
For example, to retrieve all groups in the entire domain, we can use:
$groups = Get-ADGroup -Filter *
Iterate through the groups and retrieve members:
Loop through the list of groups obtained in the previous step and use the Get-ADGroupMember cmdlet to retrieve their members. You can also specify whether you want to retrieve users, groups, or all members.
Here’s an example that retrieves members for each group and stores the data in an array called ‘$groupmembers’.
$groupMembers = @()
foreach ($group in $groups) {
$members = Get-ADGroupMember -Identity $group | Select-Object @{Name='GroupName'; Expression={$group.Name}}, Name, SamAccountName
$groupMembers += $members
}
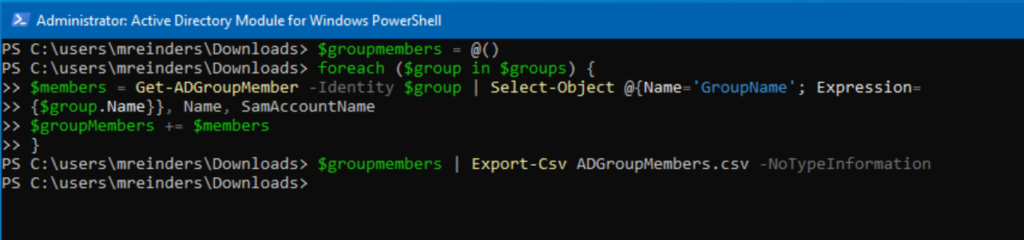
Now we just need to export the list to CSV.
$groupMembers | Export-Csv ADGroupMembers.csv -NoTypeInformation
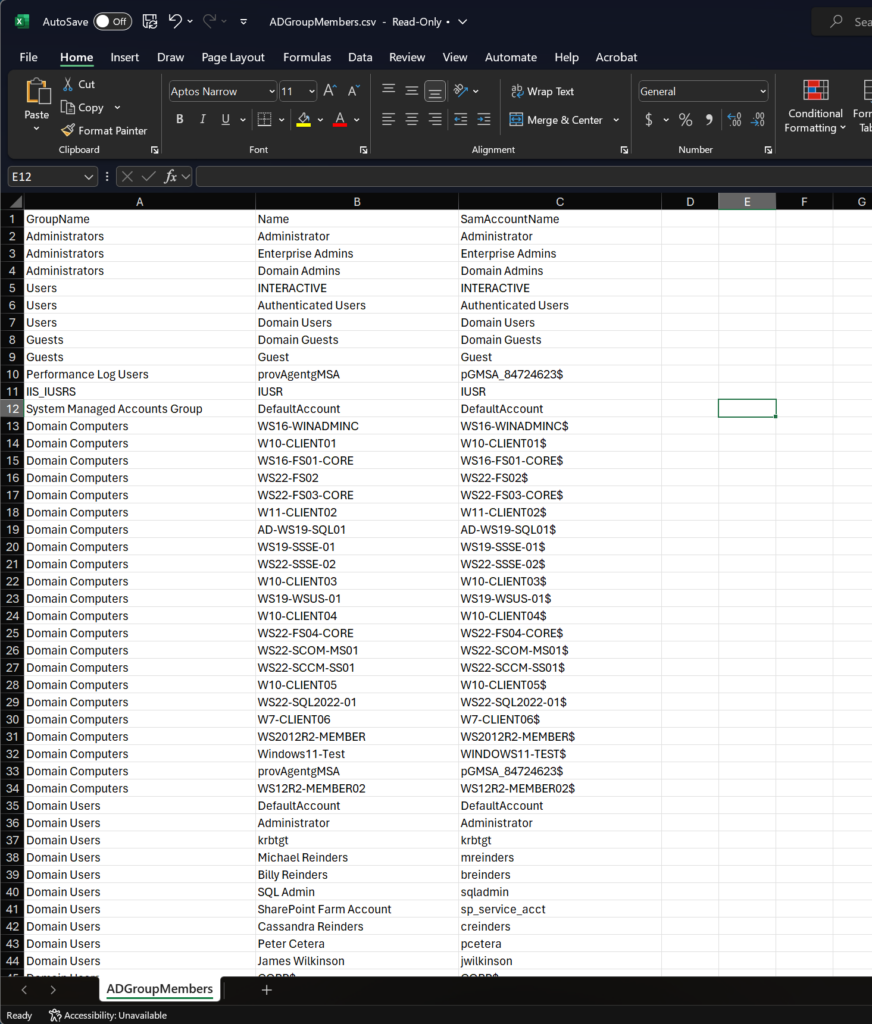
This gives us a list of all groups and their members. This can be very helpful and powerful, especially if you need to audit group memberships for security and compliance needs.
Best practices using Get-ADGroupMember
To make the most of Get-ADGroupMember (and Get-ADGroup) and ensure efficient AD management, there are a 3 best practices to consider:
1. Security
First, security. There are a lot of older scripts on the Internet that probably get the job done but may include unnecessary attributes of groups or of other AD objects. The potential interception of that data could be at risk of eavesdropping over the wire if you know what I mean.
The other aspects you should verify are credential management and access control. Make sure only the appropriate administrators in your company have access to RDP to a domain controller, install the Remote Server Administration Tools (RSAT), and things along those lines. It is very common to just let all new IT Pro hires have RDP access to your DCs. It would be much more secure to limit this access.
2. Documentation
Documentation! This is vital and will help your entire team’s productivity and efficiency in responding to requests for Active Directory management. There are a plethora of Microsoft 365 apps and services that can house all of your commands, PowerShell scripts, and FAQs surrounding this and other cmdlets. Microsoft OneNote, Microsoft Loop, and Microsoft Planner are a few to mention. Give them a try!
3. Testing
The third point I want to make here is testing! It is almost imperative that you have a testing environment to test these commands with before ‘rolling them out to production.’ Of course, the ‘Get-‘ cmdlets are essentially read-only on their own. But as soon as you use ‘Add-‘, ‘Set-‘, and ‘Remove-‘ cmdlets (or pipe your ‘Get-‘ output to these cmdlets), you are directly manipulating Active Directory. Before you accidentally delete 400 group members from 12 groups, test first…please.
Get-ADGroupMember is a versatile and powerful Active Directory PowerShell cmdlet
Get-ADGroupMember is a versatile and powerful PowerShell cmdlet that simplifies the retrieval of AD group members. By understanding its parameters and following best practices, administrators can effectively manage Active Directory, retrieve relevant information, and streamline various aspects of network administration. PowerShell, when used judiciously, can become an indispensable tool for maintaining an organized and secure AD infrastructure.



