What Is an Access Control List (ACL)?

An access control list (ACL) is a fundamental component of computer security. ACLs help to control and manage access permissions to organizational resources. In this article, I will explain in detail what an access control list is and how you can use them to secure access to local and networked resources.
ACLs are an integral part of enterprise cybersecurity strategies, aiding IT Administrators in not only controlling access to network and file resources but also ensuring only authorized entities gain access to specific resources. ACLs also help in maintaining the confidentiality, integrity, and availability of sensitive data and network resources.
What is an access control list?
Access control lists are made up of a set of rules used to configure and control access to resources such as files, directories, or network devices. These rules define who can access a particular resource and what operations they are then allowed to perform, usually defined as a permit or deny permission.
ACLs can be configured at various levels, including file system level, firewall level, or device level providing granular control over resource access. ACLs typically consist of access rules and permissions for different users, groups, or network addresses that define the access to system resources. This flexibility and granularity allows system administrators to enforce security policies tailored to the organizational needs.
Types of access control lists
While there are several classifications and types of access control lists, they can be broadly classified into four major types based on their working mechanism:
- Standard ACL
- Extended ACL
- Dynamic ACL
- and reflexive ACL.
1. Standard ACL
Standard ACLs represent the foundational layer of the access control mechanism and are the simplest and most straightforward type of access control list. They are primarily intended to control access based on source IP addresses or user. However, standard ACLs lack the granularity to distinguish between different types of IP traffic, such as TCP, ICMP, UDP, or specific applications. Or an Internet protocol like HTTPS.
2. Extended ACL
Extended ACLs allow more comprehensive access restrictions than standard ACLs. Extended ACLs can consider various network traffic attributes including source IP addresses, destination IP addresses, network protocols, source and destination port numbers, and even specific types of traffic.
This expanded set of criteria for extended ACLs allows for more granular access control decisions. And they enable network administrators to deploy more tailored access models.
3. Dynamic ACL
Dynamic ACLs, also known as “lock and key” access control, allow permissions to be dynamically adjusted based on organizational needs. Unlike static ACLs (standard and extended), which have fixed rules defined until someone manually changes them, you can configure dynamic ACLs using triggers that allow them to automatically adapt access permissions as needed.
For example, you can configure a dynamic ACL to automatically modify and adapt the access model based on factors such as:
- the time of day
- the user’s location
- the type of device being used
- or the security posture of the network.
4. Reflexive ACL
Reflexive access control lists (ACLs) are a type of dynamic ACL that automatically create temporary access rules in response to outbound network traffic flows. They allow you to create temporary rules dynamically, so the firewall or the router allows inbound traffic based on outbound traffic that matches specified criteria.
Implementation-based ACL types
ACLs can further be classified as network ACLs and filesystem ACLs based on their application. Note that each of these types of ACL implementation can still be configured as standard, extended, dynamic, or reflexive.
Network ACLs
Network access control lists are used to filter and control the flow of both incoming and outgoing network traffic in an enterprise network. They can help enforce security policies and access restrictions by permitting or denying traffic based on the rules specified.
You can also choose to specify access criteria based on IP addresses, destination and source port numbers, protocols, and more. Network ACLs are a common security mechanism in almost all organizations.
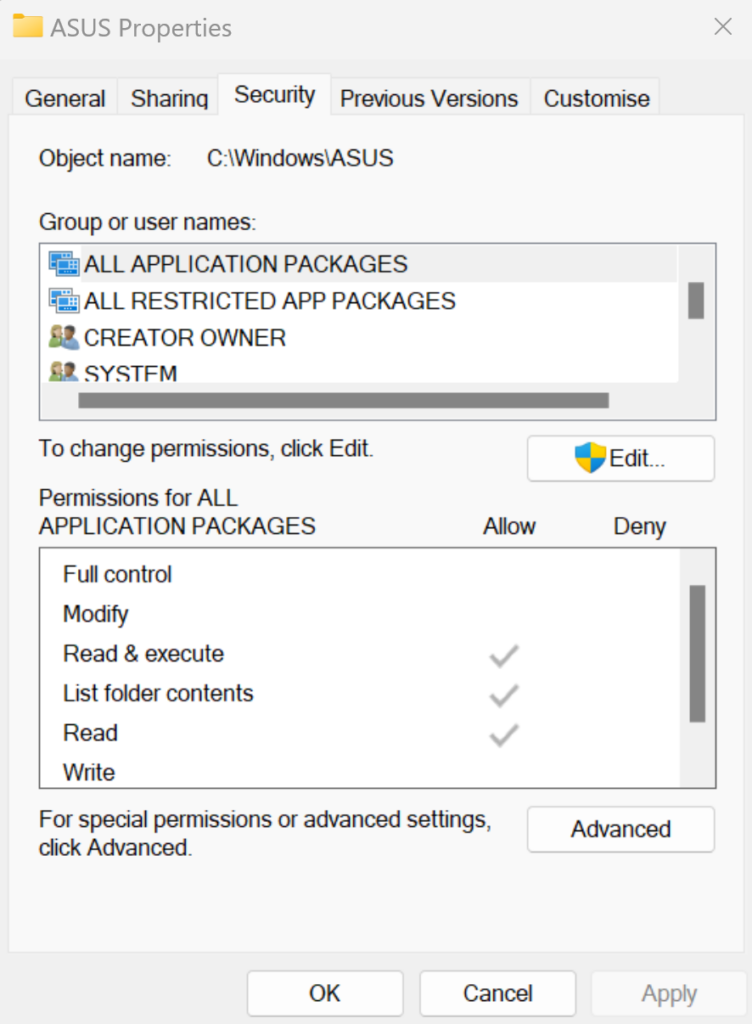
Filesystem ACLs
Filesystem ACLs are for safeguarding and controlling access to files and directories containing operating system data or user files. They define permissions for both individuals and groups. And they specify the access patterns for who can perform file operations such as read, write, and execute. Filesystem ACLs help organizations to enable the ‘principle of least privilege’ and allow fine-grained access controls.
Command-line utilities, like icacls.exe in Windows, can be used to show and manage ACLs on the filesystem and registry.
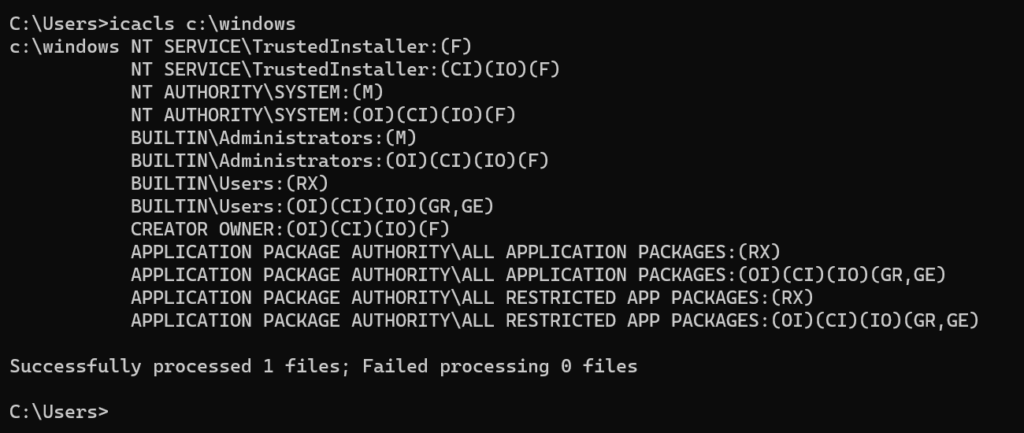
How do ACLs work?
The core working model for any type of ACL is based on a set of rules that specify who can access which resources and what actions they’re allowed to perform. Each ACL rule typically consists of one or more access control entries (ACEs) consisting of the names of the users or groups of users allowed or denied the ability to perform operations on the resource.
ACLs allow you to define access privileges in an access mask that contains a string of bits and is typically based on some criteria built on parameters like source IP addresses, destination IP addresses, protocols, and port numbers.
When a request to access a resource is made, the ACL is consulted to determine whether the request should be granted or denied based on the predefined rules. If the request matches an allowed rule, access is granted; if it matches a denied rule, access is blocked. This process controls network traffic and file access to ensure security by only permitting authorized access while blocking unauthorized attempts.
It is important to know and understand that although ACLs can be implemented and managed by specific devices such as routers, switches, web servers, Domain Name System (DNS) servers, VPNs, and firewalls, they are not limited to any particular hardware or software. Instead, ACLs are a general security concept used across different computing environments to manage access restrictions to ensure the security of systems and networks.
Benefits of using an ACL?
In the table below, I list the many benefits of using ACLs to control access to file and network resources.
| Benefits | Description |
| Security | ACLs help enable resource security by controlling access to resources |
| Granular control | ACLs allow you to establish fine-grained control over access permissions |
| Flexibility | ACLs offer great flexibility in defining and customizing access policies to fit organizational needs |
| Scalability | ACLs are scalable and can be accommodated in various environments of different sizes and complexities. They can also be configured for both on-premises and cloud-based platforms |
| Resource protection | ACLs protect business-critical and sensitive organizational resources from unauthorized access and safeguard data integrity |
| Audit and compliance | ACLs are an effective means to meet audit and compliance requirements by providing granular visibility and reporting |
| Reduced administrative overhead | The configurable nature of ACLs helps streamline access management, minimizing the administrative overhead |
What are the components of an ACL?
An access control list consists of multiple components that collectively define access permissions for organizational resources.
Sequence number
A sequence number is used to identify individual entries within the ACL and can also help in determining the order in which they are evaluated.
ACL name
This is used to store the object names and can be used to reference and manage the ACL entries.
Comment
This is an optional field that allows network administrators to include descriptive text in ACLs.
Network protocol
ACLs can filter network traffic based on specific protocols such as TCP, UDP, IPX, NetBIOS, and others. This component is used to specify the protocol being employed in the ACL.
Source and destination
These fields will contain the IP addresses to determine the origin and end target.
Log
Contains record details about incoming and outgoing network traffic affected by ACL rules.
What are the types of access controls implemented in access control lists?
Below is a table that provides a comprehensive comparison of various features and criteria that can help you choose from the different types of access controls.
| Feature | Mandatory Access Control (MAC) | Discretionary Access Control (DAC) | Role-Based Access Control (RBAC) | Attribute-Based Access Control (ABAC) | Rule-Based Access Control (RBAC) |
| Determination of access rights | System-defined access permissions | Owner-defined access permissions | Assigns permissions based on user roles | Evaluates access requests based on multiple attributes | Evaluates access decisions based on predefined rules or policies |
| Configuration flexibility | Limited | High | Moderate | High | High |
| Access granularity | High | Low | High | High | High |
| Owner’s discretion | No | Yes | No | No | No |
| Role assignment | Not applicable | Not applicable | Assign users to roles | Not applicable | Not applicable |
| Dynamic access decisions | No | No | No | Yes | No |
| Resource ownership | Determined by system | Determined by the resource owner | Not applicable | Not applicable | Not applicable |
| Administrative overhead | High | Moderate | Moderate | High | High |
| Use cases | High-security environments | General-purpose access control | Large organizations | Dynamic environments | Complex access control scenarios |
ACL best practices
Below are the top five best practices to configure and implement for both network and filesystem ACLs.
1. Principle of least privilege
It is good practice to follow the principle of least privilege in setting up access and permissions for users and other entities to network resources.
2. Regular reviews and auditing
ACLs should be periodically reviewed and audited to ensure that the access provisioned is current and meets organizational needs.
3. Logging and monitoring
Enabling logging for ACL-related events and triggers, and regularly monitoring them helps you identify and track suspicious and/or unauthorized access patterns.
4. Employee training
Proper education and training on the best practices to use for ACLs and organizational security policies are crucial to avoid security mishaps.
5. Automation
Use automation wherever possible to minimize the possibility of human error when configuring, managing, and deploying ACLs.
Examples and use cases of access control lists
ACLs can be used to configure and set several different system requirements such as securing resources, building access models, and more. Let’s look at some different use cases and examples of how ACLs can be used in a cloud provider like Microsoft Azure and an on-premises Windows-based system.
Microsoft Azure: ACL use cases
- Storage Account ACLs: These can be used to enable secure data management by allocating read, write, or delete data access within Azure Storage containers.
- Virtual Network ACLs: These are used to manage incoming and outgoing network traffic to and from Azure Virtual Machines (VM).
- Azure Key Vault ACLs: Used to safeguard sensitive information like cryptographic keys to Azure Key Vault resources.
Windows Systems: ACL use cases
- Filesystem ACLs: These are for regulating access to files and folders on Windows systems.
- Active Directory ACLs: Active Directory ACLs configure access rights to directory objects like users and groups.
- Registry ACLs: Control access to Windows Registry keys and values.
Conclusion
Access control lists (ACLs) play a vital role in organizational security, ensuring regulated access control to organizational resources. They are used to manage permissions at various levels and help maintain data confidentiality and integrity. ACLs also serve as fundamental tools for enforcing access policies and safeguarding critical IT resources.
Table of contents
- What is an access control list?
- Types of access control lists
- Implementation-based ACL types
- How do ACLs work?
- Benefits of using an ACL?
- What are the components of an ACL?
- What are the types of access controls implemented in access control lists?
- ACL best practices
- Examples and use cases of access control lists
- Conclusion



