Understanding Microsoft Information Protection
There are a lot of compliance-based services across Microsoft 365’s licensing options. At the highest level, a Microsoft 365 E5 subscription for a tenant gives administrators a ton of toys to play with. The naming, marketing, and placement of the capabilities you get can be fuzzy. In this article, we’ll tackle Microsoft Information Protection (MIP), explaining exactly what it is and the many services, features, and capabilities that comprise it.
What is Microsoft Information Protection?
Microsoft Information Protection (MIP) is a stack, or framework, of capabilities that achieve four high-level objects for securing information:
- Know it
- Protect it
- Stop losing it
- Govern it
Think of MIP as a collection of features, services, and controls that are grouped together because combined, they work towards achieving those goals. This means MIP is not a single license, it’s not a single piece of technology, and it’s not a single service you set up: it’s the full suite of options at your fingertips for managing information compliance in Microsoft 365.
Exploring Microsoft Information Protection capabilities
Let’s get into an overview of some of the capabilities that make up Microsoft Information Protection, and how you can get started with them.
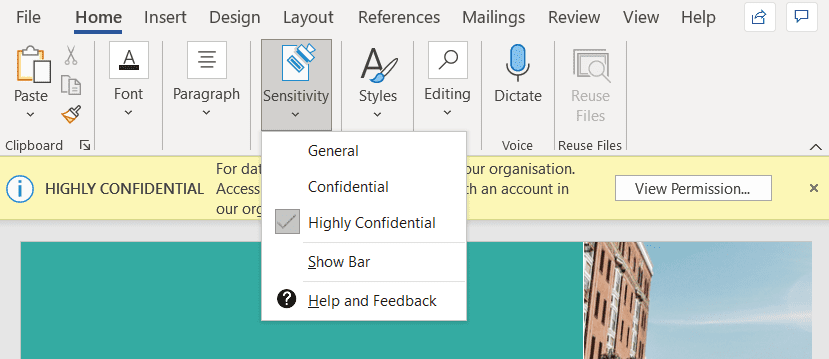
Sensitivity labels apply classification and protective controls. Originally applicable to emails and files, their scope now also includes containers such as Teams and other sources such as Azure Purview and PowerBI. License rights to assign labels are available within the Enterprise Mobility + Security license stack, or something that includes it, such as Microsoft 365 Business Premium or E3; but there are no licenses needed to consume protected data.
At the file and email level, sensitivity labels provide either only classification (akin to a physical label on a physical document, that says “Confidential”, etc) or also encryption. This encryption is controlled by a rights management service in the cloud that, effectively, enforces an access control list on files anywhere they travel.
Accidentally email an important spreadsheet to someone without that access control list? If they can’t authenticate to an allowed account, they can’t decrypt it: simple as that. For ‘containers’ such as Teams, sensitivity labels can control settings such as group privacy, external sharing settings, and access from devices without IT control. The functionality is built into modern Office apps but it can be improved with the use of a client app for Windows.
Sensitivity labels can be applied manually by users (with the option to force selection of one) or applied automatically for Microsoft 365 E5 licensees (or subsets of E5, such as E5 Compliance) if a particular type of information is identified. This brings us to perhaps the core capability of Microsoft Information Protection: data classification.
A service called the Microsoft Data Classification Service operates across Office 365 and services such as Microsoft Cloud App Security to inspect data and classify it based on what the service discovers. There are two key ways this is achieved: identification of sensitive info types or trainable classifiers.
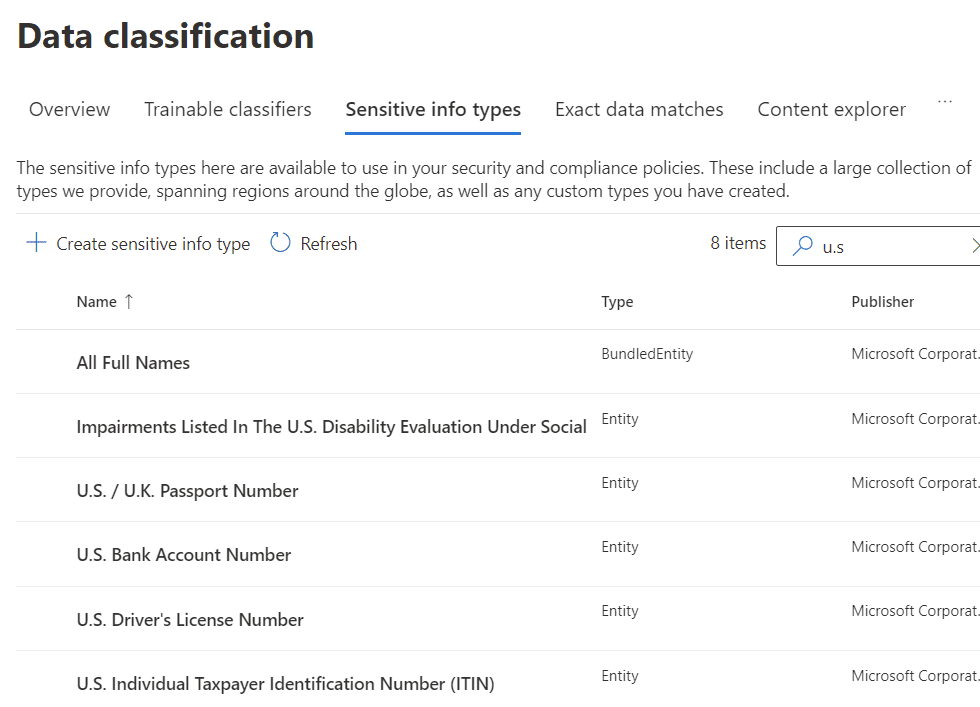
Sensitive info types are a bit self-explanatory – they are identifiable instances of information that should be considered sensitive; that is, probably deserves some kind of special protection. There are hundreds of out-the-box sensitive info types Microsoft manage for you, including credit card numbers, tax/government ID numbers, Azure resources such as storage keys, and other types of personally identifiable information. You can also create your own sensitive info types based on patterns – for example, your organisation’s employee ID format, invoice numbers, and so on.
Sensitive info types are graded based on confidence: low, medium, or high, and this is measured by their proximity to supporting information. For example, a Portuguese tax number is nine characters, which could lead to false positives. However, if that number is within 300 characters of “tax identification number”, for example, the odds are a bit more favorable. If you need even more accurate sensitive info types, a feature called exact data match (EDM) allows a database schema to be defined with sensitive information uploaded from, for example, a CRM or ERP system.
Trainable classifiers use machine learning where EDM or sensitive info types are not appropriate, generally because the entire document or message context must be accounted for and not just a pattern to be recognized. You can create your own custom trainable classifier, by feeding it sample data, or use Microsoft’s own prebuilt trainable classifiers such as resumes, source code, or threatening language.
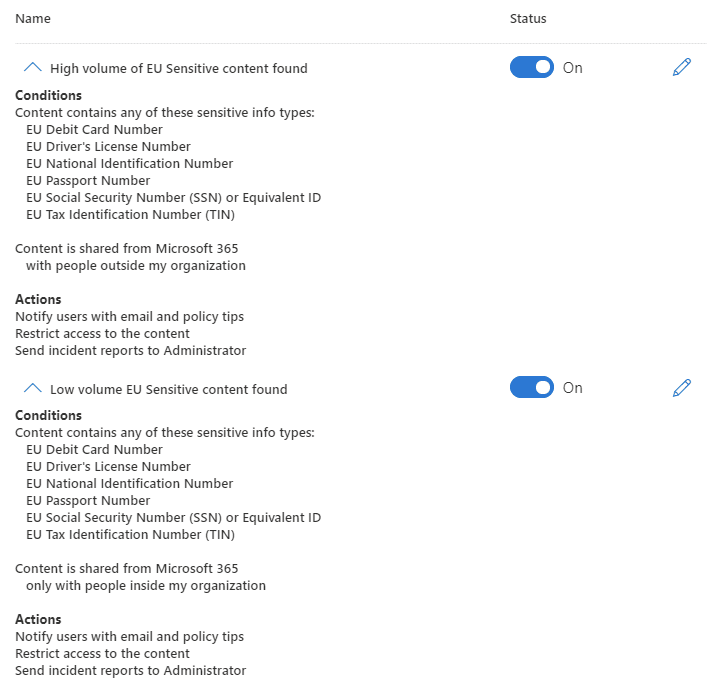
Data classification is used throughout Microsoft Information Protection. Data loss prevention (DLP) capabilities use it to control the escape or sharing of data within boundaries you allow. DLP can identify types of information transferring across services (Outlook, SharePoint, etc) and endpoints (Windows 10 USB transfers, etc; also, just announced at Ignite, macOS support) and offers administrators fine-tuned approaches to dealing with it.
This may simply be warning users or content owners, or it may block the action entirely. For example, you may block the transmission of emails with a certain volume of PII. Teams also supports DLP, but watch out – it requires E5 (or equivalent) licensing, as does endpoint DLP; though other methods only need Microsoft 365 E3. The capability for DLP even extends to third-party apps and services, like the Google Chrome browser. Using Microsoft Cloud App Security (MCAS), you can scope out non-Microsoft SaaS locations such as Box, Salesforce, or WebEx.
If you are in a highly regulated environment, Microsoft also provides advanced capabilities to control encryption. Customer Key (CK) gives organizations, rather than Microsoft, the ability to create and hold root keys for data encryption policies (DEPs) in locations like Exchange Online mailboxes and SharePoint. Double-Key encryption (DKE) is available too, wherein data is first encrypted by your key, then Microsoft’s; meaning they, as the cloud host, never have access to files with DKE sensitivity labels.
Conclusion
By now, we’ve established Microsoft Information Protection is not one thing: it’s a capability set across numerous licensed products, and it leverages background services to achieve the protection of your data. Consequently, you can really leverage those protective capabilities across the entire Microsoft 365 stack, using the whole platform’s feature set. Keep an eye on Petri.com for additional deep dives into making the most of it.
Related Article: